Alibaba Cloud RAM(Resource Access Management)는 사용자(직원, 시스템 또는 애플리케이션 포함)를 중앙에서 관리하고 권한 수준을 통해 리소스에 대한 접속을 안전하게 제어할 수 있는 ID 및 접속 제어 서비스입니다. 따라서 RAM을 사용하면 선택한 높은 권한을 가진 사용자, 기업 직원 및 파트너에게만 Alibaba Cloud 리소스에 대한 접속 권한을 안전하게 부여할 수 있습니다. 이렇게 하면 클라우드 리소스를 안전하고 적절하게 사용될 수 있고 계정에 대한 무단 접속으로부터 보호할 수 있습니다.
장점

-
향상된 보안
MFA(다단계 인증) 기술에 따라 계정을 보호합니다.
-
유용성
웹 기반 Alibaba Cloud Management Console 또는 API를 사용하여 RAM에 간단히 접속하고 구성할 수 있습니다.

-
Alibaba Cloud 구독을 통한 무료 서비스
추가 비용 없이 중앙 집중식 관리 가능, RAM 사용자가 사용하는 다른 서비스에 대해서만 지불
하나의 엔터프라이즈 계정에 속하는 여러 계정에서 모든 사용자가 수행하는 리소스 작업으로 인해 발생하는 모든 비용에 대해 하나의 통합 청구서 제공

-
통합 관리
RAM 사용자, 그룹, 역할 생성, 관리, 이름 변경 및 삭제, 필요한 권한 부여
Alibaba Cloud 리소스에 대한 접속 권한 및 ID 자격 증명의 통합 관리 사용
필요에 따라 여러 리소스 또는 사용자 계정에서 권한 취소
기능
-

ID 관리
사용자 ID 관리
기본 계정을 사용하여 사용자 ID를 생성 및 관리 권한을 부여합니다.
MFA(다단계 인증)
사용자 암호를 안전하게 유지하고 가상 호스트 종료와 같은 특별한 권한을 할당하기 위해 TOTP 프로토콜 표준(RFC 6238)을 준수하는 MFA 디바이스를 지원합니다.
독립적인 암호 정책 관리
사용자에 대한 맞춤형 암호 강도 정책을 만들고 허용된 로그온 시도 횟수, 암호 유효 기간 및 기타 암호 정책을 설정합니다.
사용자 그룹
여러 사용자에게 동일한 권한을 할당하도록 사용자 그룹을 생성하고 관리합니다.
접속 키
콘솔을 사용하여 작업을 수행하려는 사용자의 접속 키를 설정합니다. 프로그래밍 방식 접속이 필요한 사용자를 위해 API 접속 키를 설정할 수도 있습니다.
-

SSO(Identity Federation)
사용자 기반 SSO
SAML 어설션에서 RAM 사용자를 지정하고 RAM 사용자를 이용하여 Alibaba Cloud에 접속하도록 IdP를 구성할 수 있습니다.
역할 기반 SSO
SAML 어설션에서 RAM 역할을 지정하고 RAM 역할을 이용하여 Alibaba Cloud에 접속하도록 IdP를 구성할 수 있습니다.
-

접속 관리
실행 권한
특정 조건에서 특정 리소스에 대한 특정 작업의 실행을 허용하거나 거부할 수 있는 권한을 설정합니다.
맞춤형 접속 관리
맞춤형 정책을 사용하여 사용자 권한을 효과적으로 관리합니다.
그룹 권한
그룹 권한 메커니즘을 사용하면 시나리오별 접속 관리를 통해 권한 관리와 관련된 부담을 줄일 수 있습니다.
사용자 접속 관리
본인 계정 또는 다른 Alibaba Cloud 계정에 속한 사용자에게 사용자 또는 사용자 그룹 접속 권한을 부여합니다.
-

Security Token Service
접속 권한
Security Token Service는 모바일 클라이언트에 특정 클라우드 리소스 접속 권한을 부여하여 모바일 고객이 클라우드 리소스에 직접 접속할 수 있도록 합니다.
맞춤형 유효성
보안 강화를 위해 맞춤형 토큰 유효 기간을 지원합니다.
-


높은 유연성
세분화된 접속 관리
단일 리소스에 대한 하나 혹은 여러 작업에 대한 권한을 부여할 수 있습니다. 예를 들어 리소스 소유자는 리소스 생성, 작업 수행 또는 삭제 권한을 부여할 수 있습니다.
다차원 접속 관리
IP, 시간 및 기타 요인에 따라 접속 권한을 제한합니다.
버전 관리 메커니즘
원치 않게 정책이 삭제되는 리스크를 방지하기 위해 각 권한 부여 정책의 여러 버전을 유지합니다.
-


사용 및 청구
무료
RAM은 추가 비용 없이 제공됩니다. RAM 사용자/역할이 사용하는 다른 Alibaba 제품/서비스에 대해서만 요금이 청구됩니다.
통합 청구서
계정에는 모든 RAM 사용자/역할이 수행한 리소스 작업으로 인해 발생하는 모든 비용에 대한 통합 청구서가 발급됩니다.
작동 원리
-
기업 사용자 계정 관리 및 권한 할당

-
모바일 앱에 대한 임시 접속 관리

-
기업 간 리소스 운영 및 접속 관리

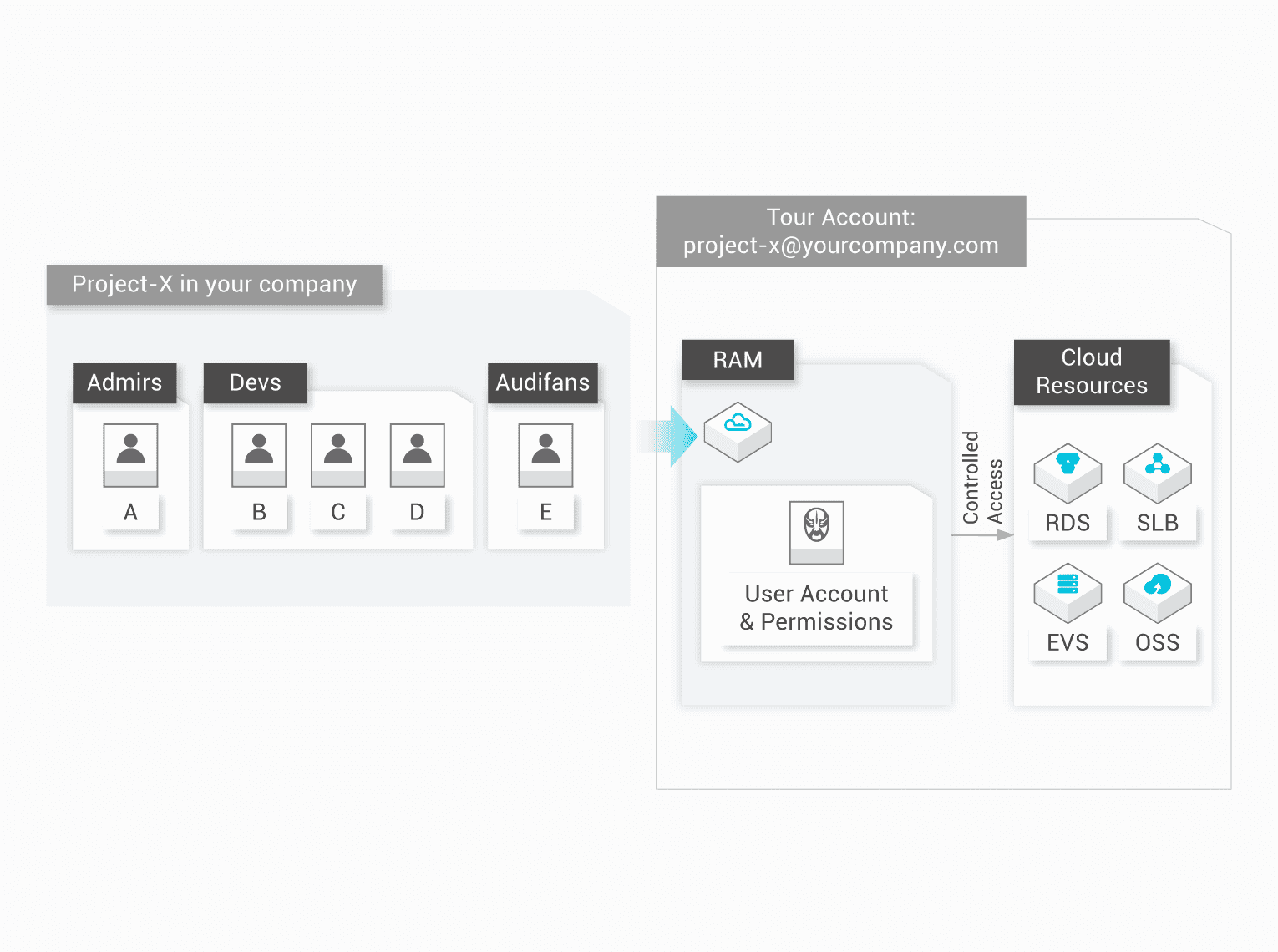
기업 사용자 계정 관리 및 권한 할당
한 기업에 ECS/RDS/SLB 인스턴스 및 OSS 버킷과 같은 여러 클라우드 리소스를 구매한 프로젝트가 있습니다. 서로 다른 책임과 권한을 가진 직원들은 다양한 작업을 수행해야 합니다. 권한이 있는 리소스 작업만 수행하도록 독립적인 사용자 또는 운영자 계정을 할당할 수 있습니다. 이러한 방식으로 기업은 보안을 손상시키지 않으며 언제든지 모든 사용자 계정에 대한 권한을 부여/취소할 수 있습니다. 또한 리소스 운영에 대한 비용은 기본 계정인 기업에 일괄적으로 청구됩니다.
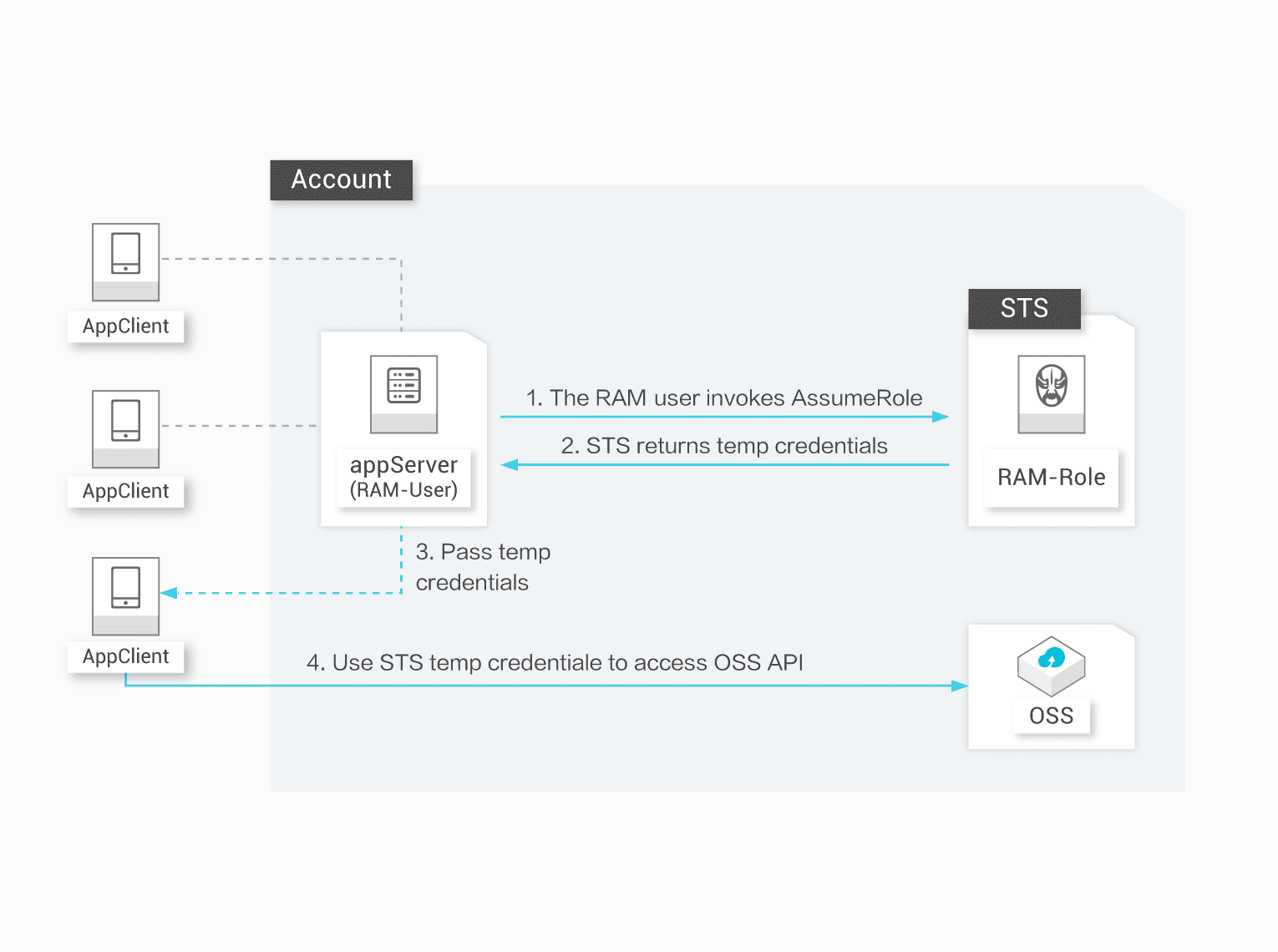
모바일 앱에 대한 임시 접속 관리
기업은 모든 앱이 AppServer를 사용하여 데이터를 전송하는 것을 원하지 않습니다. 그러나 모바일 앱은 모바일 디바이스에서 실행되여 이러한 디바이스를 제어하는 것은 불가능합니다. 기업은 또한 최소한의 권한으로 각 앱에 접속 토큰을 제공하고 접속 기간을 줄여 보안 위험을 최소화하고자 합니다.

기업 간 리소스 운영 및 접속 관리
기업 A는 여러 클라우드 리소스를 구매하고 클라우드 리소스 O&M, 모니터링 관리 및 기타 작업을 기업 B에 부여했습니다. 기업 B는 A의 리소스에 대한 접속 권한을 직원 중 한 명 혹은 여러 명에게 할당할 수 있습니다. B는 직원이 A의 리소스에 대해 수행할 수 있는 작업을 정확하게 제어해야 합니다. O&M 위탁계약이 해지되면 A는 B의 권한을 임의로 취소할 수 있습니다.
FAQ
1. Alibaba Cloud RAM을 시작하려면 어떻게 하나요?
Alibaba Cloud에 가입하면 웹 기반 Alibaba Cloud Management Console 또는 RAM API(프로그래밍 방식 접속)를 사용하여 사용자 및 그룹을 생성하고 다른 리소스에 접속할 수 있는 권한을 할당할 수 있습니다.
2. 하위 사용자가 Alibaba Cloud Management Console에 로그인하려면 어떻게 하나요?
로그온 페이지를 방문하거나 Management Console 대시보드에 연결되는 링크를 참조하세요.
3. RAM 통합을 지원하는 Alibaba Cloud 제품 및 서비스에는 어떤 것이 있나요?
RAM을 지원하는 Alibaba Cloud 서비스 문서를 참조하세요.
4. RAM 역할이란 무엇인가요?
RAM-Role은 가상 사용자(섀도우 계정) 또는 RAM 사용자 유형입니다. 이 사용자는 고정된 ID를 가지고 있으며 정책을 부여할 수 있습니다. 그러나 RAM-Role은 인증된 실제 사용자가 맡아야야 합니다.
5. 신규 RAM 사용자에게 부여되는 작업 권한은 무엇인가요?
기본적으로 새 RAM 사용자에게는 작업 권한이 없습니다. RAM 사용자는 운영자를 대표하여 어떤 작업을 수행하려면 명시적으로 권한을 부여받아야 합니다. 사용자는 권한이 부여된 후에만 RAM 콘솔 또는 API를 통해 리소스 작업을 수행할 수 있습니다.
6. 정책이란 무엇인가요?
정책은 정책 언어를 사용하여 설명된 권한 그룹입니다. 권한 부여 조건은 물론 권한 부여된 리소스 집합 및 작업 집합을 정확하게 정의할 수 있습니다.
7. Alibaba Cloud에서 지원하는 모든 시스템 정책을 보려면 어떻게 하나요?
Alibaba Cloud에서 지원하는 모든 시스템 정책을 보려면 RAM 콘솔에 로그온하고 정책 페이지로 이동하여 모든 시스템 정책 목록을 확인하세요.
8. RoleARN이란 무엇인가요?
RoleARN은 역할을 지정하는 글로벌 리소스 설명자입니다. RoleARN은 Alibaba Cloud의 ARN 명명 규칙을 따릅니다.
예를 들어 Alibaba Cloud 계정의 "devops" 역할에 대한 RoleARN은 acs:ram::1234567890123456:role/devops입니다.
9. 여러 버전이 있는 정책을 삭제하려면 어떻게 하나요?
여러 번 편집 및 저장한 정책에는 여러 "버전"이 첨부됩니다. RAM 콘솔에서 이러한 정책이 삭제되면 나머지 "기본" 정책을 삭제할 수 있습니다. 그러면 Alibaba Cloud 계정에서 정책이 완전히 제거됩니다.
10. 일반적으로 사용되는 권한을 할당하려면 어떻게 하나요?
Alibaba Cloud는 RAM 사용자, 그룹, 역할에 연결할 수 있는 일반적으로 사용되는 권한 집합인 시스템 정책을 제공합니다. 이러한 정책은 ECS에 대한 읽기 전용 권한 또는 ECS에 대한 전체 권한과 같이 Alibaba Cloud에서 생성 및 관리하는 포괄적인 권한 집합의 그룹입니다. 이러한 정책을 사용할 수는 있지만 수정할 수는 없습니다.
11. 맞춤형 정책을 생성하려면 어떻게 하나요?
1. RAM 콘솔에 접속하여 정책을 선택합니다.
2. "정책 생성"을 클릭합니다.
3. 목록에서 템플릿을 선택합니다(예: AliyunOSSReadOnlyAccess).
4. 필요에 따라 정책의 이름, 비고, 내용을 편집할 수 있습니다.
5. 필요한 변경을 수행한 후 "확인"을 클릭하여 사용자 지정 정책을 생성합니다.
12. 그룹에 정책을 연결하려면 어떻게 하나요?
1. RAM 콘솔에 로그인하고 ID > 그룹을 선택합니다.
2. 그룹을 선택하고 "권한 추가"를 클릭하여 권한 추가 페이지로 이동합니다.
3. 그룹에 권한을 부여할 관련 정책의 이름을 선택합니다.
13. 여러 RAM 사용자에게 동일한 권한을 할당하려면 어떻게 하나요?
RAM 그룹에 정책을 연결할 수 있습니다. 그룹의 모든 사용자에게 그룹과 연결된 권한이 부여됩니다.
14. RAM 사용자는 어떤 종류의 보안 자격 증명을 가질 수 있나요?
RAM 사용자는 API를 통해 또는 접속 키의 도움으로 Alibaba Cloud Management 콘솔에 로그인하여 클라우드 서비스에 접속할 수 있습니다. 사용자 이름과 암호를 입력한 후 다른 인증 코드(사용자의 MFA 디바이스에서 제공하는 두 번째 보안 요소)가 필요한 다중 요소 인증(MFA)을 활성화합니다. 이것은 계정에 또 다른 보안 계층을 제공합니다.