Safe and Reliable Key Lifecycle Management on the Cloud
Alibaba Cloud Key Management Service (KMS) provides secure and compliant key management and cryptography services to help you encrypt and protect sensitive data assets. KMS is integrated with a wide range of Alibaba Cloud services to allow you to encrypt data across the cloud and to control its distributed environment. KMS provides key usage logs via ActionTrail, supports custom key rotation, and provides HSMs that have passed FIPS 140-2 Level 3 or other relevant validation, to help you meet your regulatory and compliance needs.
Fully Managed
KMS provides key management and cryptography services. You manage the lifecycle and permissions of keys, use them for encryption and signing while Alibaba Cloud fully manages the cryptographic infrastructure and ensures service availability, security, and reliability.
Availability, Reliability, and Elasticity
KMS processes your requests with low latency via redundant cryptographic modules across availability zones in each region and scales to meet your needs to create as many keys. You can bring your own key to KMS and keep a copy offline for more durability.
Security and Compliance
KMS ensures stringent protection of your keys on Alibaba Cloud with secure design and review. KMS helps you quickly meet regulatory and compliance requirements by offering managed HSMs that have passed FIPS 140-2 Level 3 or other relevant validation, by allowing you to configure custom key rotation policies, to manage permissions in RAM, and to track key usage in ActionTrail. You can pipe ActionTrail events to OSS or Log Service to integrate with SIEM solution for more analysis and threat detection.
Data Encryption for Integrated Cloud Services
KMS is integrated with a wide range of Alibaba Cloud services such as ECS, RDS, OSS, NAS, and MaxCompute. With minimum cost of key management, you can leverage KMS to encrypt data in these services and maintain control over their distributed compute and storage environment. With server-side encryption such as OSS SSE or database TDE, you control encryption behavior via KMS and RAM, while Alibaba Cloud handles the complication and pay for the execution of the encryption workload for you.
Custom Encryption and Digital Signatures
KMS encapsulates simplified cryptography and HSM APIs for you to easily encrypt data in your application for integrated security and compliance, further reducing the attack surface to sensitive data from adversaries. You can also use asymmetric keys for digital signing to ensure integrity of critical data.
Cost-effectiveness
With KMS, you only pay for the resources that you use, eliminating the need for HSM purchase and associated cost of continuous hardware operation, patching and replacements. KMS helps you reduce the cost of building and maintaining your own key management infrastructure.
Features
Comprehensive Management Features
KMS provides rich key management features to meet all your needs.
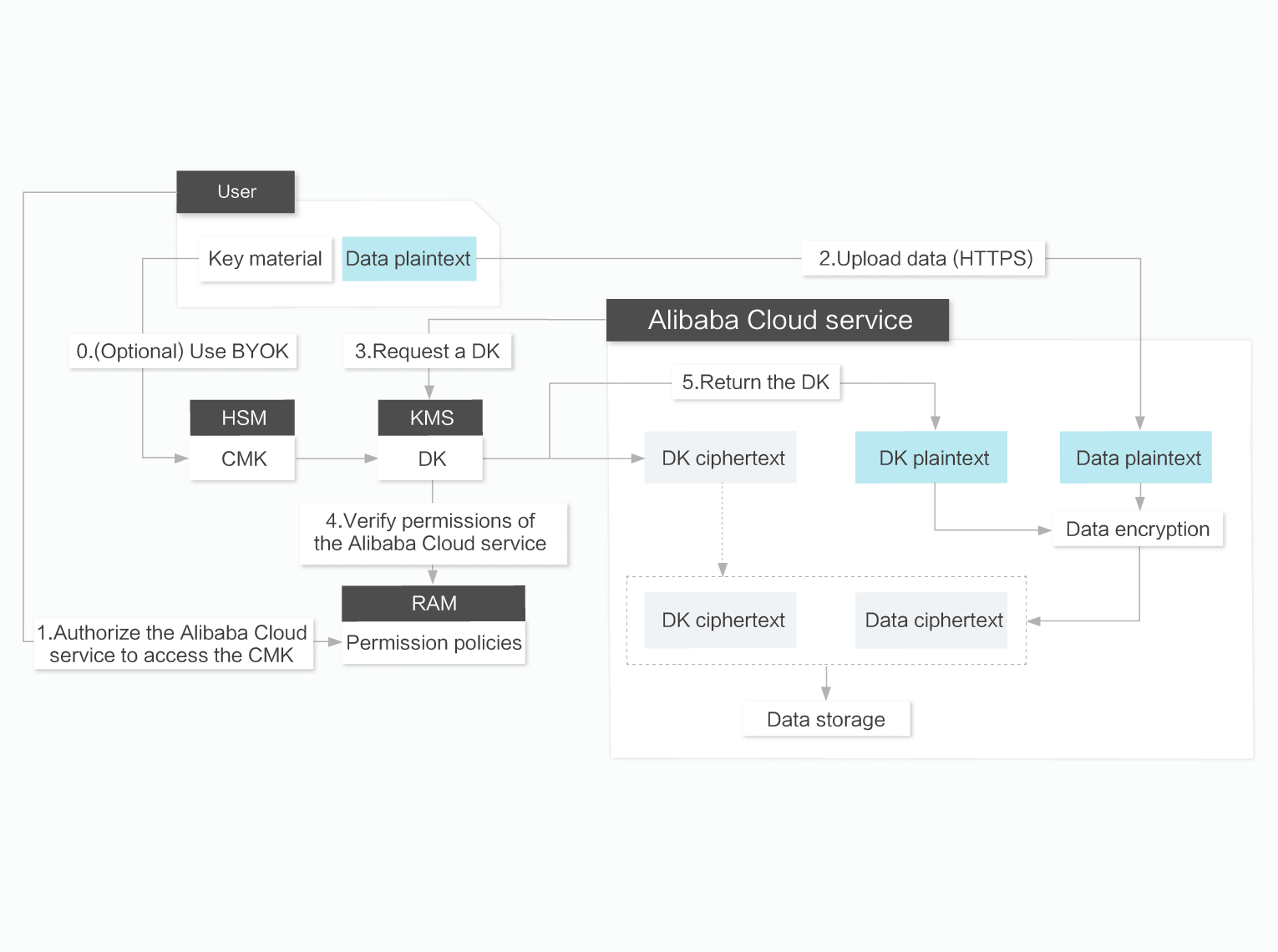
Keys Generated in KMS or Imported from External Sources
You can generate keys in KMS or import Bring Your Own Keys (BYOKs) to managed HSMs. BYOKs allow you to keep additional offline key copies. Managed HSMs ensure that imported keys will not be exported.
Key Lifecycle Management and Automatic Key Rotation
You can enable or disable keys, or schedule a regular cycle to delete keys. For BYOK, you can delete keys at any time, or specify an automatic expiration policy. KMS allows you to configure custom rotation policies to automatically rotate encryption keys periodically and therefore enhance the security of keys.
Authentication, Authorization, and Auditing (AAA)
You can manage KMS user authentication and authorization policies through RAM. You can track and audit key usage through ActionTrail, or store key usage logs in OSS or Log Service for diverse scenarios such as long-term storage, data analysis, and SIEM integration.
Fully Managed HSMs
Managed HSMs provide a high security protection mechanism for keys.
HSM Certification and Compliance
KMS provides HSMs that have passed FIPS 140-2 Level 3 validation, running under FIPS-approved Level 3 mode of operation, or offers HSMs that have passed relevant validation to comply with local regulatory requirements.
Secure Generation of Keys
Managed HSMs use a secure and licensed random number generation algorithm. The algorithm uses high entropy seeds to generate key materials. This protects keys from being recovered or anticipated by malicious parties.
Hardware Protection of Keys
Managed HSMs protect keys in KMS through hardware mechanisms. The plaintext of keys is only processed inside HSMs for key operations. It is kept within the hardware security boundary of HSMs.
Integration with Other Alibaba Cloud Services
KMS can be integrated with multiple Alibaba Cloud services to provide native encryption experience and advanced security capabilities.
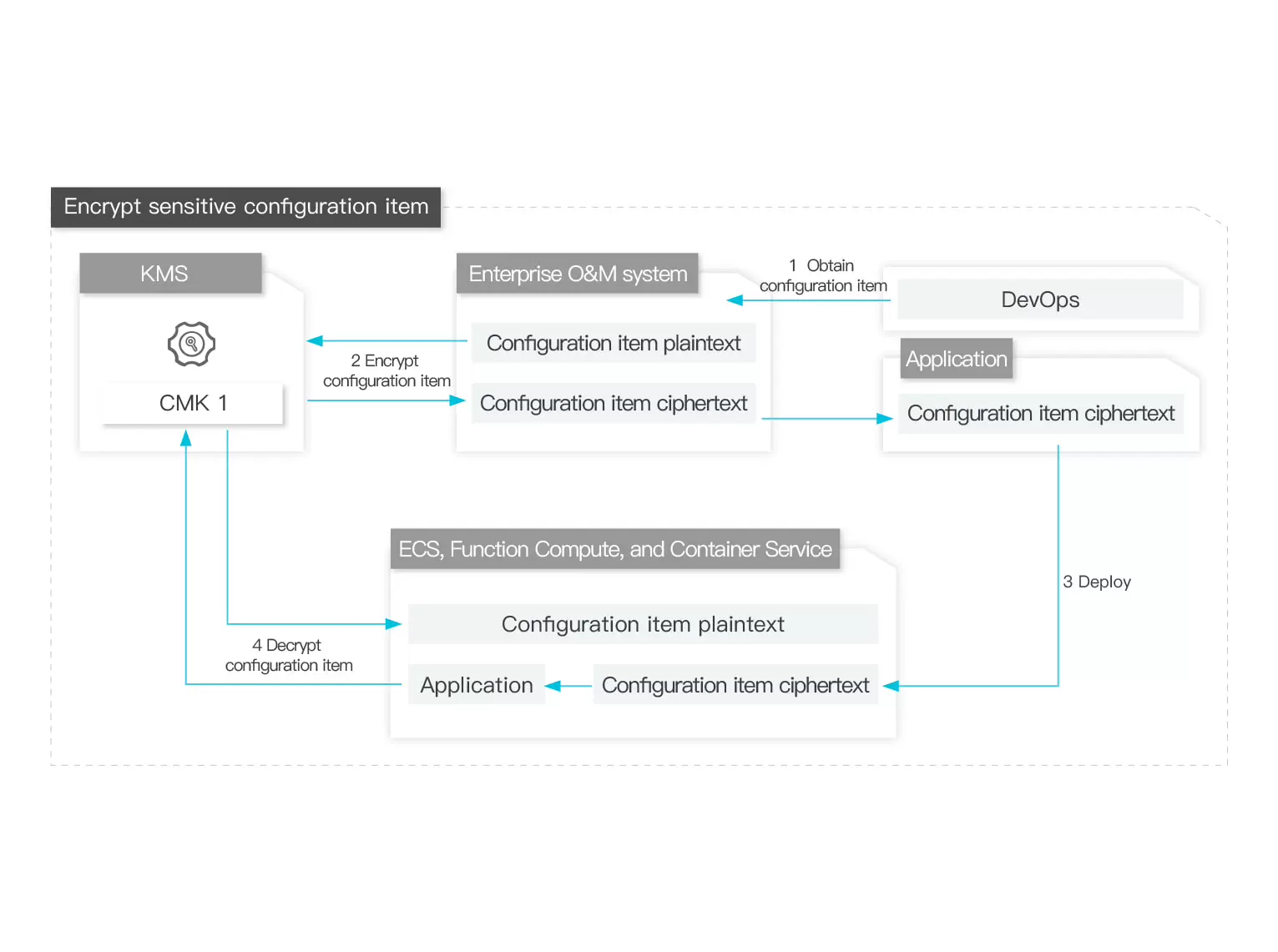
Entry-level Default Encryption
KMS allows each cloud service to automatically manage a dedicated encryption key. By default, cloud services can use this key without caring about its lifecycle and authorization policies.
Optional Sources for Encryption Keys
You can create keys in KMS or import external key materials, and authorize cloud services to employ user-managed keys for data encryption protection. Therefore, you obtain full control over keys by managing their permissions and lifecycle.
Auditing Key Usage by Cloud Services
Regardless of service-managed keys or user-managed keys, you can audit key usage by cloud services by calling KMS API operations on your behalf.
Simple and Effective Cryptographic Operations
KMS uses abstract cryptographic concepts and provides simple cryptographic operation APIs.
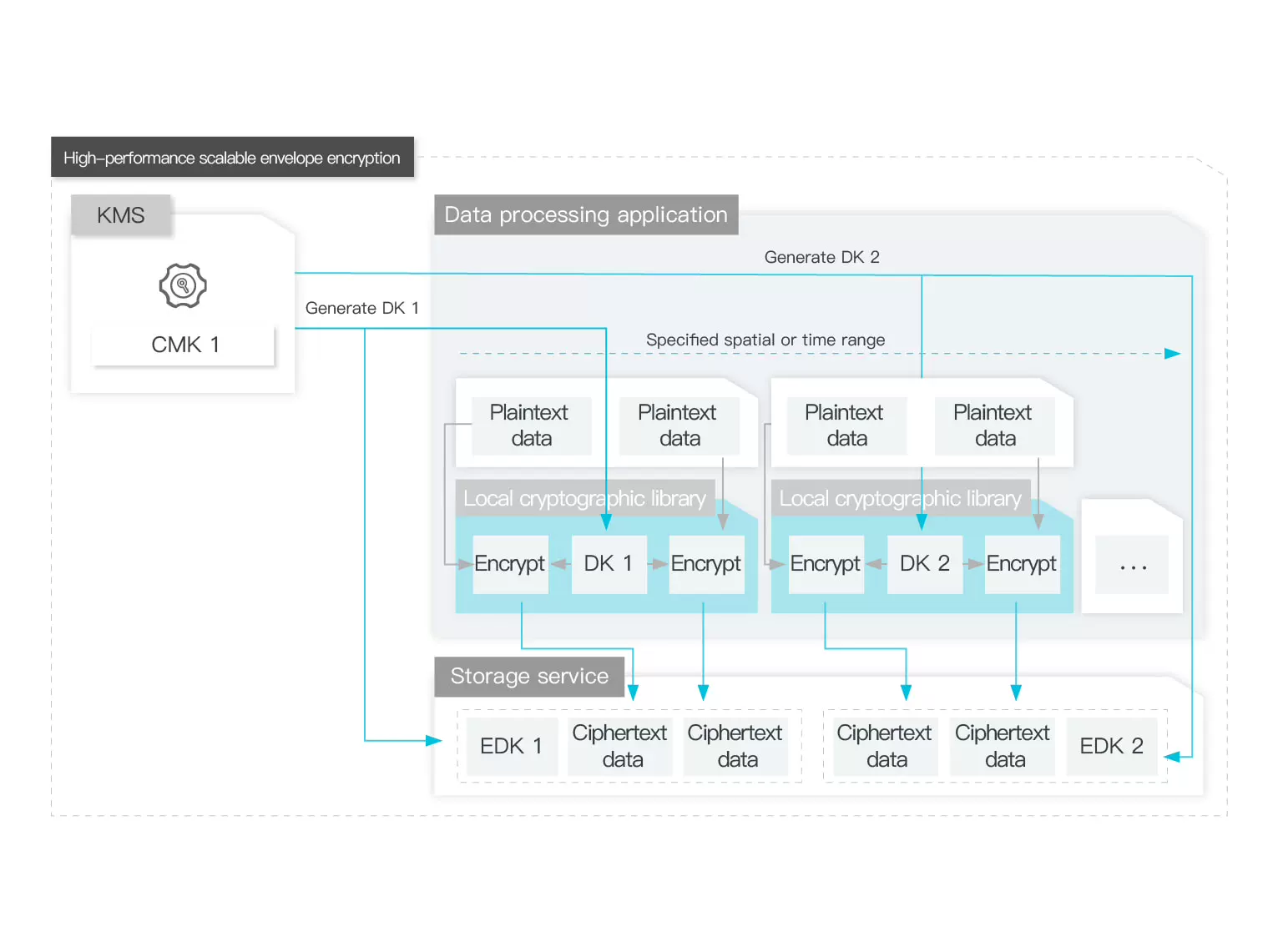
Envelope Encryption
With envelope encryption built in KMS, you can generate a secondary key and encrypt the CMK through a single API call.
AEAD
KMS encapsulates authenticated encryption with associated data (AEAD). You can use encryption context to provide additional integrity and authenticity for encrypted data.
Digital Signature Verification
KMS can host asymmetric keys and provide digital signature verification algorithms based on asymmetric keys. KMS can be used in a wide range of scenarios such as identity verification, code signature, and blockchain.
Usage Suggestions
|
Encryption of Data Stored in Alibaba Cloud Services/Transparent Data Encryption
|
Data Field Encryption
|
AK/SK Secret Management
|
Key Backup and Restoration
|
Hardware KMS
|
|
|---|---|---|---|---|---|
| Use Scenario | Applicable to over 90 Alibaba Cloud services, including Elastic Compute Service (ECS), ApsaraDB RDS, and Object Storage Service (OSS) | Applicable to encryption of files, data fields, and certificate chains | Applicable to the management of AK and SK secrets, tokens, passwords of database accounts, and other secrets | Applicable to the backup of keys and secrets in regions across the world | Applicable to hardware key management service validated by Federal Information Processing Standards (FIPS) 140-2 Level 3 |
| Encryption Method | Encryption of data stored in Alibaba Cloud services or transparent data encryption | Application encryption | Application encryption | N/A | Application encryption, encryption of data stored in Alibaba Cloud services, or transparent data encryption |
| Data Access Characteristics | Real-time access, called by cloud services | Real-time access, cache access | Real-time access | Real-time access after archiving | Real-time access |
| Processing Performance | No limit | Over 100,000 QPS | Over 100,000 QPS | N/A | Over 100,000 QPS |
| Whether the SDK needs to be integrated | No | Yes | Yes | No | Yes |
| Supported SDK Development Languages | N/A | Java, Go, PHP, Python... | Java, Go、PHP、Python... | N/A | Java, Go、PHP、Python... |
| Support for Terraform | Yes | Yes | Yes | No | No |
| SLA | Subject to the service-level agreements (SLAs) of specific cloud services | 99.95% | 99.95% | 99.9999% | 99.95% |
| Billable Item | Free of charge | QPS, number of keys, number of VPCs... | Charged based on the number of secrets and QPS after encryption based on the customer master key (CMK) | Backup duration | QPS, the number of VPCs, the number of hardware security modules (HSMs)... |
| Pricing | USD 0.0 per month | From USD 500.0 per month | From USD 550.0 per month |
Free of charge for 0-6 days From USD 12.5 per month for 7 days or more |
From USD 1,799.00 per month |
| Purchase Link | Free to Use | Software Key | Credential Butler | Key Backup | Hardware Key Management |
Upgraded Support For You
1 on 1 Presale Consultation, 24/7 Technical Support, Faster Response, and More Free Tickets.
1 on 1 Presale Consultation
24/7 Technical Support
6 Free Tickets per Quarter