To allow Realtime Compute for Apache Flink to access your Kerberized Hive cluster, you must register it in the console. This topic describes how to register a Kerberized Hive cluster.
Background
Kerberos is a computer-network authentication protocol that is used for identity authentication to ensure the security of communication. If your Flink jobs need to access a Kerberized Hive cluster, you must register it in the console and then configure it for your Flink jobs.
Usage notes
Only Kerberized Hive clusters of Hadoop 2.x and Hadoop 3.x are supported.
NoteOnly Realtime Compute for Apache Flink that uses Ververica Runtime (VVR) 8.0.7 or later supports Hadoop 2.x.
One or more Kerberized Hive clusters can be registered in a namespace.
One or more Kerberos principles and keytab files can be created for each Kerberized Hive cluster.
Only a single Kerberos principle of a Kerberized Hive cluster is supported per job.
Session clusters do not support accessing Kerberized Hive clusters.
Register a Kerberized Hive cluster
Go to the registration page.
Log on to the Realtime Compute for Apache Flink console.
Find the target workspace and click Console in the Actions column.
In the left-side navigation pane, choose .
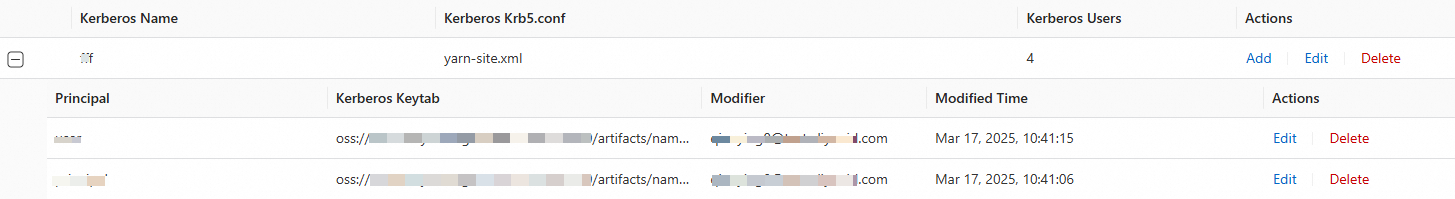
On the Hive Kerberos tab, click Add Kerberos.
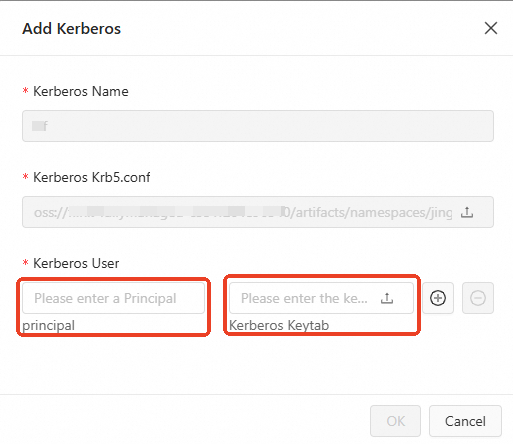
In the Add Kerberos dialog box, configure the parameters as follows:
Configuration item
Description
Kerberos Name
Enter the name of your Kerberized Hive cluster.
Kerberos Krb5.conf
Enter the path of the Krb5.conf file. You can click the
 button to upload the Krb5.conf file.
button to upload the Krb5.conf file. Krb5.conf is a configuration file in the Kerberos authentication environment. The file is used to specify the connection mode and security parameters between Kerberos clients and servers. The file is also used to specify the locations of Kerberos components.
principal
Enter a principal name.
Kerberos Keytab
Enter the path of the keytab file. You can click the
 button to select and upload the Krb5.conf file.
button to select and upload the Krb5.conf file. A keytab stores keys for Kerberos principals. It can be used by services to authenticate to Kerberos securely.
To obtain the configuration file, see Basic operations on Kerberos.
Click OK.
When a Kerberized cluster is no longer needed, you can click Delete in the Actions column to disassociate it from the current namespace. Affected jobs will fail, so perform this operation with caution.
Add principals
You can add one or more principals for a Kerberized cluster.
Find the target cluster and click Add in the Actions column.
In the Add Kerberos dialog box that appears, enter a principal name and add a Keytab file.
Click the
 icon to view newly added principals.
icon to view newly added principals.