
IDaaS Identity and Permission Management Platform
IDaaS is a cloud-based Identity and Access Management (IAM) service that provides comprehensive identity and permission management features.
Provides enterprise-level unified identity services: IDaaS is the core of an enterprise's identity management. It eliminates identity silos and allows users to access all applications with a single account. We continuously adopt the latest technologies to make identity management a frictionless experience while improving identity security and management efficiency.
Eliminates redundant passwords for all users: IDaaS supports all mainstream standard SSO protocols. You can use these protocols to integrate all mature enterprise services. By eliminating passwords, IDaaS significantly reduces security risks. Users no longer need to worry about how to store or remember an average of a dozen sets of accounts and passwords.
Cross-cloud platform identity connection: IDaaS can act as a bridge to connect identities from other cloud platforms to Alibaba Cloud. A cloud identity management solution is usually a basic requirement for enterprises that use cloud services. IDaaS can build identity bridges between Alibaba Cloud and private environments, and between multiple public cloud providers.
Cloud-Based Identity Security Platform
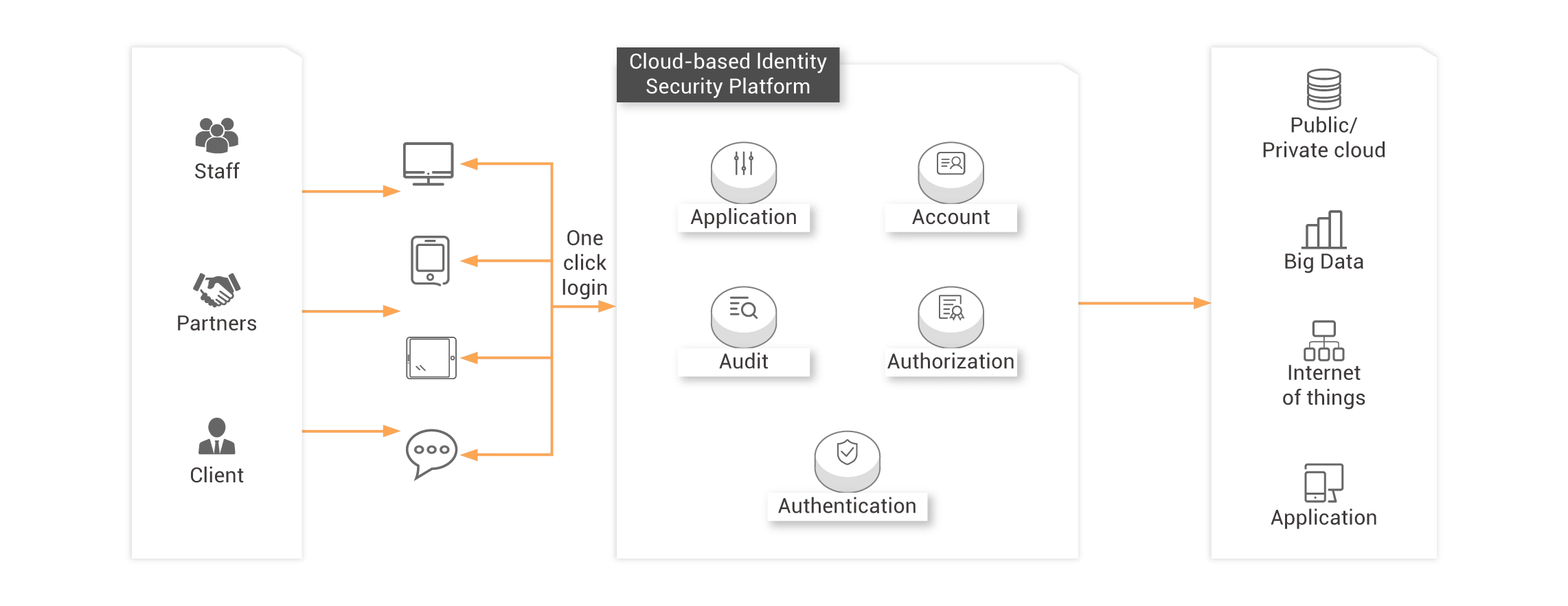
5A Unified Authentication Platform
Application
Docking web applications, mobile applications, desktop applications, and IoT devices provide users with integrated services that include access control, single sign-on, and application portals.
Authorization
According to the department or role of the user, the accessible range can be managed easily. Authorization or revocation can be centralized to achieve one configuration and take effect globally.
Account
Provide unique user identity data for enterprise information construction with complete account life cycle management.
Audit
Trace user behaviors and provide real-time audit reports to keep managers informed about the efficiency of the company’s digital assets.
Authentication
Centrally verify user identity, configure multi-factor authentication (MFA), and support third-party authentication sources.
Use Scenarios
-
Single Sign-On for Enterprise Applications

-
Unified User Directory

-
Unified Identity Authentication

-
Centralized Access Authorization

-
Unified Behavior Audit

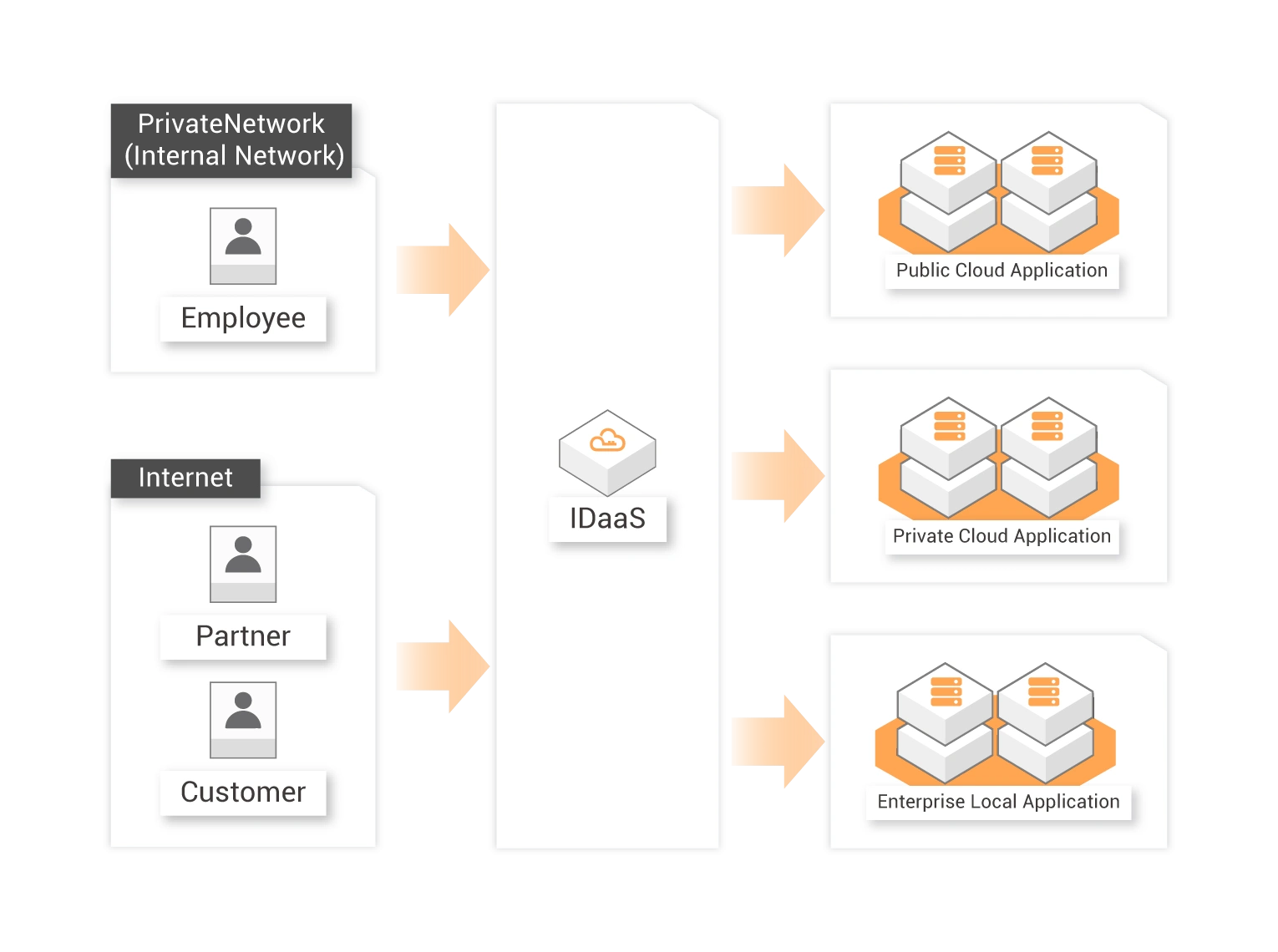
Help companies build proprietary portals
Employees, partners and customers of the enterprise can access all authorized applications with one click through the unified portal provided by IDaaS.
Help to solve
-
Decentralized login address and password management issues
The application systems introduced by enterprises are increasing year after year, and users need to remember more addresses and passwords. This can easily lead to problems, such as reduced work efficiency and difficulty in promoting new applications.
At the same time, some countermeasures commonly used by users when managing multiple passwords, such as simple passwords and the same passwords, also bring more security risks that allow attackers to access your system easily.

Cloud-native directory service
Provide unique user identity data for enterprise information construction, and centralized account lifecycle management, with updates automatically synchronized downstream, unlimited expansion, and permanent online.
Help to solve
-
Solve the problem of employee account information silos and management omissions
Due to the information solis problem caused by development isolation between multiple application systems of the enterprise, the process of employee onboarding and transfer is complicated and time-consuming, and the account permissions are not completely recovered after leaving the job.
-
Additional R&D and O&M costs
The local deployment of directory services by an enterprise requires a large amount of operation and maintenance resources and requires periodic application for authorization for capacity expansion. At the same time, the repeated construction of account management by each application system brings new R&D and maintenance costs.

Provide a unified multi-factor certification center
It can centrally configure authentication factors other than multiple passwords, including biometrics such as dynamic tokens, certificates, faces, and fingerprints. A variety of common third-party certification sources can be integrated. At the same time, it provides a developer API to support other applications to use IDaaS's identity authentication capabilities.
Help to solve
-
Security issues caused by password vulnerability
Easy password settings places enterprise IT system under huge security risks causing system vulnerability of both database and application from illegal cyber activities. It has been proved countless incidents of credentials leakage and even customer digit assets lost that had caused irreversible economic results.

Provide visual centralized authorization capabilities
According to the user name or the department where the user is authorized to access it, it can be configured once and take effect globally.
Help to solve
-
Decentralized authorization management issues
When dealing with requirement of various applications authorization distributed over multiple domains, extra resources are required and is therefore placing enterprise subjected to additional IT management cost.
Whenever there occurs organization structure change that causes possible improper authorization operations there would always trigger risky interruption to daily enterprise operation.

Help managers understand user behavior and asset usage at any time
Detailed records of all user behaviors and administrator operations, and the formation of visual reports, allowing managers to keep track of the use of corporate digital assets at any time.
Help to solve
-
Decentralized audit log issues
Traditional logging systems is not regarded as management friendly and to build up from ground a centralized log-based auditing system normally introduces increased IT development cost.
Meanwhile setup of identifying system of malicious access or other potential risky behaviors by users’ historical behaviors would not be possible with current decentralized logging systems.
Feature comparison
| Feature | Vendor O | Alibaba Cloud IDaaS |
|---|---|---|
| Domestic applications such as Wecom and Lark | ✖ | ✔ |
| Official services in the Chinese mainland | ✖ | ✔ |
| Standard protocols OIDC, SAML, and Oauth2.0 | ✔ | ✔ |
| MFA | ✔ | ✔ |
| Custom password policy | ✔ | ✔ |
| Roles permissions | ✔ | ✔ |
| Machine-to-Machine(M2M) authentication | ✔ | ✔ |
| Single Sign-On(SSO) | ✔ | ✔ |
Upgraded Support For You
1 on 1 Presale Consultation, 24/7 Technical Support, Faster Response, and More Free Tickets.
1 on 1 Presale Consultation
24/7 Technical Support
6 Free Tickets per Quarter










