Alibaba Cloud WAF Benefits

Professional, Stable, and End-to-end Solution to the Major Security Pain Points of Web Applications
Professional: provides Alibaba Cloud-developed rules, AI-based deep learning, and proactive protection rules, and allows you to create custom rules.
Stable: enables multi-line and multi-node disaster recovery and intelligent routing, protects services that have millions of QPS, and enables millisecond-level responses.
Timely: automatically detects and defends against the latest web vulnerabilities, including zero-day vulnerabilities first exposed by Alibaba Cloud, within hours.
Comprehensive: delivers end-to-end protection against vulnerabilities, web attacks, and bot traffic, ensures data and account security, and meets the requirements of security O&M.
Compliant: complies with the requirements of classified protection and PCI DSS, and boosts security compliance construction for enterprises.
Exclusive threat intelligence: provides exclusive network-wide threat intelligence, which is accumulated and updated from the real service scenarios of Alibaba Cloud.

The Only Chinese Vendor That Receives Full Recognition for Web Application Firewalls
Recognized by international authorities:WAF is recognized by Gartner, Forrester, IDC, and Frost & Sullivan.
Recognized by the market: A report of Frost & Sullivan shows that Alibaba Cloud WAF ranks first in the cloud WAF market in Greater China.
Extensive experience: WAF protects core services of Alibaba Cloud and accumulates a large amount of attack and defense experience from Tmall and Taobao Double 11 events over the years.
Multi-scenario Deployment and Flexible Access
Multi-scenario deployment: You can deploy WAF in the cloud or deploy protection clusters in your data centers to meet the requirements of different scenarios, such as public clouds, hybrid clouds, and data centers. Both Alibaba Cloud and third-party clouds are supported. WAF delivers the same protection capabilities for services in the cloud and in data centers.
Flexible access: You can connect Alibaba Cloud SLB, CDN, and ECS to WAF with a few clicks, and quickly configure the DNS records for your services that are deployed in data centers.
Alibaba Cloud WAF Features
Web Intrusion Prevention
Automatic Vulnerability Prevention
Automatically detects and defends against the latest web vulnerabilities, including zero-day vulnerabilities first exposed by Alibaba Cloud, within hours. You do not need to manually patch the vulnerabilities.
Multi-dimensional Dynamic Protection
Provides Alibaba Cloud-developed rules, AI-based deep learning, and proactive protection rules, and dedicated network-wide threat intelligence that is constantly updated to fully protect your services.
Anti-scanning and Anti-detection
Automatically blocks traffic based on the characteristics and behavior of scanning and detection, network-wide threat intelligence, and deep learning algorithms to prevent attackers from discovering system vulnerabilities.
Custom Protection Rules
Allows you to create custom protection rules based on your business requirements.
Traffic Control and Bot Management
Flexible Traffic Management
Supports custom combination of all HTTP headers and body characteristics to implement access control and throttling for specific scenarios.
Mitigation Against HTTP Flood Attacks
Mitigates HTTP flood attacks by using the default protection policies at different levels, custom protection policies, throttling policies, CAPTCHA verification, and blocking policies.
Accurate Bot Identification
Accurately identifies bots and automatically responds to bot mutations based on AI technology and multi-dimensional data, such as fingerprints, behavior, characteristics, and intelligence.
All-scenario Protection
Blocks web bots from accessing applications, such as websites, HTML5 pages, apps, and mini programs. This helps enterprises prevent and control service risks such as fraud and promotion abuse.
Diversified Methods to Handle Bot Traffic
Provides different methods to handle traffic based on actual scenarios. The methods include blocking, CAPTCHA verification, throttling, and spoofing.
Scenario-specific Configuration Wizard
Provides guidelines for scenario-specific configurations. This way, new users can quickly get started with Alibaba Cloud best practices.
Data Security Protection
API Security Protection
Proactively discovers APIs of the earlier versions, APIs that lack the authentication mechanism, and APIs that cause risks such as excessive data exposure and sensitive data leaks.
Data Leak Prevention
Detects and prevents sensitive data leaks. Sensitive data includes certificate numbers, bank card numbers, mobile phone numbers, and sensitive words.
Web Tamper Proofing
Locks and caches the content of important pages. This way, users can view the original content of pages regardless of whether the pages are tampered with.
Account Risk Detection
Automatically identifies common account risks such as dictionary attacks, brute-force attacks, and weak passwords.
Security O&M and Compliance
Secure Access
Enables you to protect HTTPS services with a few clicks, provides end-to-end IPv6 support, and ensures intelligent load balancing, high availability in and off the cloud, and fast disaster recovery.
Full Access Logs
Records and stores full web access logs. You can execute SQL statements to query and analyze the logs in real time. You can also create custom alert rules.
Automatic Asset Identification
Discovers unprotected domain names based on the big data in the cloud. This helps shrink the attack surface.
Hybrid Cloud Deployment
Provides protection for services that are deployed in data centers.
Compliance with Classified Protection Requirements
Complies with the requirements of classified protection in various industries.
WAF Editions
* PayPal is not supported for Alibaba Cloud Pay-as-you-go Free Trial. Learn more>








Alibaba Cloud WAF Scenarios
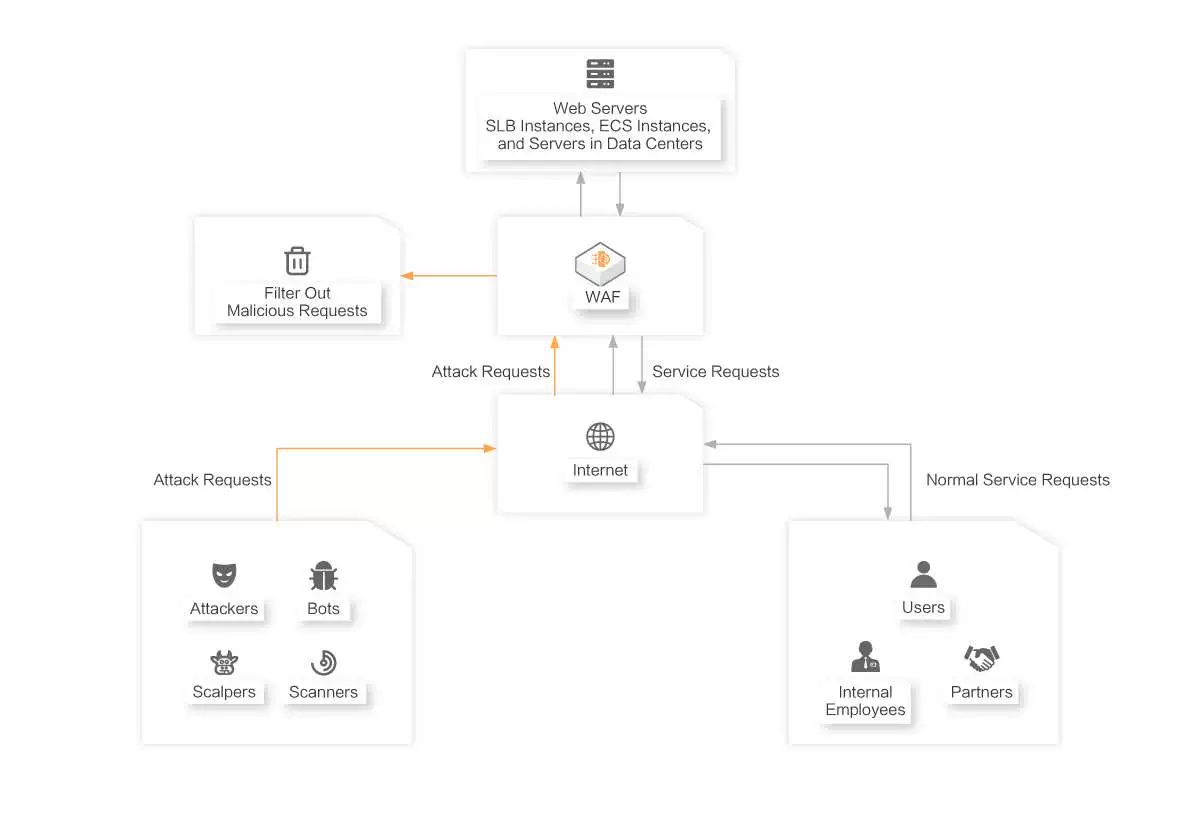
Security Capabilities Required for Migrating Web Applications to the Cloud
Automatically fixes zero-day vulnerabilities on your web applications. You do not need to manually patch and fix the vulnerabilities. WAF prevents your web applications such as websites, HTML5 pages, apps, and mini programs from being attacked and against virus intrusion in an efficient manner. WAF mitigates attacks such as trojans, web tampering, malicious bots, data leaks, and HTTP flood attacks.
Scenarios
-
 Prevents common web attacks, such as SQL injections, XSS attacks, webshell uploads, directory traversals, and backdoors.
Prevents common web attacks, such as SQL injections, XSS attacks, webshell uploads, directory traversals, and backdoors. Prevents attackers from using zombie servers to launch HTTP flood attacks.
Prevents attackers from using zombie servers to launch HTTP flood attacks. Automatically fixes zero-day vulnerabilities at the earliest opportunity by using virtual patching. This avoids code rewrite, which is difficult and time-consuming.
Automatically fixes zero-day vulnerabilities at the earliest opportunity by using virtual patching. This avoids code rewrite, which is difficult and time-consuming. Proactively discovers APIs of the earlier versions, and APIs that lack the authentication mechanism and throttling policies. This helps reduce data leak risks.
Proactively discovers APIs of the earlier versions, and APIs that lack the authentication mechanism and throttling policies. This helps reduce data leak risks. Automatically blocks unauthorized scanning and detection activities.
Automatically blocks unauthorized scanning and detection activities.
Related Services
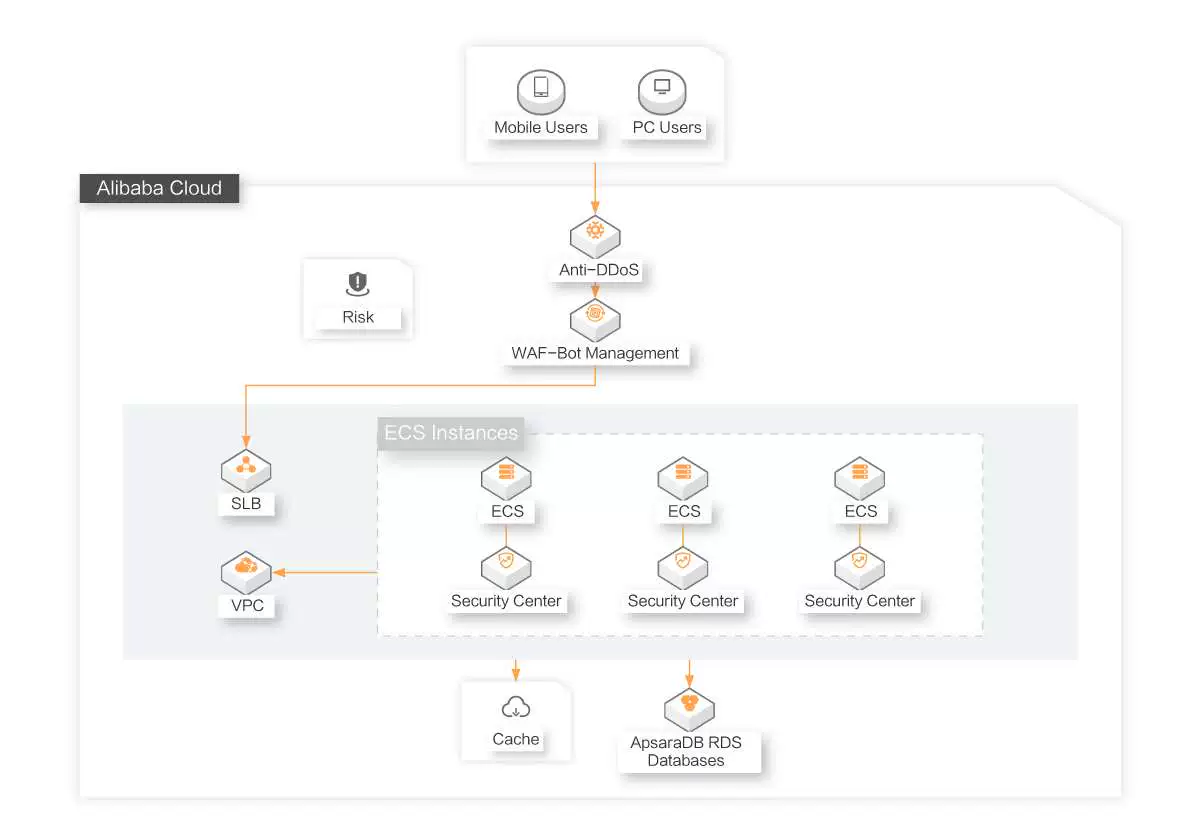
Prevention of Fraud and Promotion Abuse
Business operations may generate volumetric traffic, which affects system availability. In addition, promotion abuses always occur. These all affect and even have negative impacts on the business operations. Alibaba Cloud provides you with a complete solution to handle risks on business operations. The solution is based on years of experience on business operations.
Scenarios
-
 Ensures system stability during business operations and prevents issues such as website freezing and system failures caused by bot traffic.
Ensures system stability during business operations and prevents issues such as website freezing and system failures caused by bot traffic. Prevents promotion abuse and fraud to ensure that real customers benefit from promotions.
Prevents promotion abuse and fraud to ensure that real customers benefit from promotions. Mitigates data crawling and avoids excessive bandwidth fees caused by data crawling.
Mitigates data crawling and avoids excessive bandwidth fees caused by data crawling.
Related Services
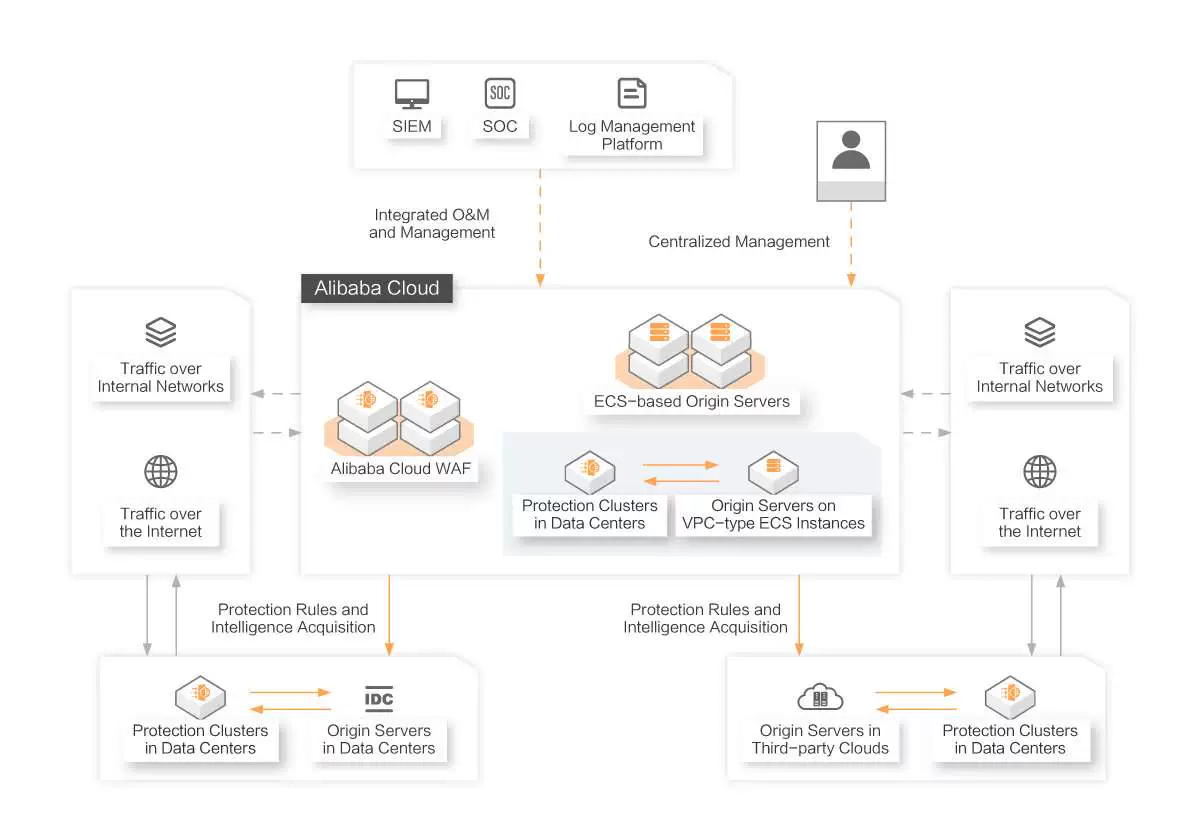
Hybrid Cloud WAF Solution
Deploys protection clusters in data centers to protect web services that are deployed across public clouds and data centers. Both Alibaba Cloud and third-party clouds are supported. You can use the Alibaba Cloud WAF console to control and perform O&M on the services.
Scenarios
-
 Services that are latency-sensitive, require high availability, and demand zone-disaster recovery, geo-disaster recovery, and centralized protection across multiple network environments.
Services that are latency-sensitive, require high availability, and demand zone-disaster recovery, geo-disaster recovery, and centralized protection across multiple network environments. Web services that cannot be deployed on Alibaba Cloud or protected by WAF.
Web services that cannot be deployed on Alibaba Cloud or protected by WAF. Web services that are deployed in the private network of the cloud or data centers.
Web services that are deployed in the private network of the cloud or data centers.
Related Services
Feature Comparison
| Feature | Alibaba Cloud | Vendor C | |
|---|---|---|---|
| Web Basic Protection | |||
| OWASP TOP 10 Protection | ✔ | ✔ | |
| Zero-day Vulnerability Protection | ✔ | ✔ | |
| Intelligent Adaptive Engine | ✔ | ✖ | |
| Scan Protection | ✔ | ✖ | |
| Website Tamper-proofing | ✔ | ✖ | |
| Bot Management | |||
| Client Environment Adaptation & Client Feature Recognition | Web, H5, Native Apps (iOS/Android/HarmonyOS), Mini Program(Wechat, Alipay) | Web, H5 | |
| Traffic Fingerprint Recognition | ✔ | ✔ | |
| Intelligent Behavior Analysis | ✔ | ✔ | |
| Actions | Monitor, Block, JavaScript Validation, Captcha, Back-to-Origin Tagging | Monitor, Block, JavaScript Validation, Captcha, Back-to-Origin Tagging | |
| Asynchronous Interface Auto-Compatibility | ✔ | ✖ | |
| API Security | |||
| API Interface Auto-Discovery | ✔ | ✔ | |
| Detection Timeliness | 1 Minute | 24 Hours | |
| Request/Response Sensitive Data Detection | ✔ | ✔ | |
| Risk Detection | ✔ | ✖ | |
| Attack Monitoring | ✔ | ✖ | |
Related Resource
Cloud Native Mode
Enable WAF protection for an ALB instance
Enable WAF protection for your ALB instance with one click. ALB is deeply integrated with WAF 3.0, which provides all-in-one security services that can detect malicious requests. WAF-enabled ALB instances are resistant to intrusions, provide more stable performance, and support high security for services and data.
Solution
Cloud Security Solution
Safeguard business security, application security, data security, infrastructure security, and account security with Alibaba Cloud's powerful security toolset.
Blog
Alibaba Cloud Provides Proven Data Security Solution to Empower UAE E-Commerce Platform
Leading UAE-based Asian supermarket chain WEMART taps Alibaba Cloud’s trusted security solution against cyber threats.
End-to-end Enterprise Security in the Cloud
Meets the requirements of data security, platform security, and the security of your new applications or migrated applications. WAF allows you to view and understand the security posture of your services in a convenient manner.

Delivering Global Cloud Training Excellence
Alibaba Cloud Academy, the training and certification division of Alibaba Cloud, provides more than 300 online and in-person training courses, empowering clients, partners, and developers to enhance their cloud skills and credibility. Our online training programs, which include Clouder courses, Specialty courses, and free short video courses, cater to the evolving needs of learners seeking flexible, on-demand educational resources.
Download Academy Catalog







