Latest News
Positioned as a Challenger in the Gartner® Magic Quadrant™ for Network Firewalls for two consecutive years
Learn more >Pay-as-you-go savings plans for Cloud Firewall are available
Learn more >Cloud Firewall obtained IPS certification from ICSA Labs
Learn more >Product Introduction
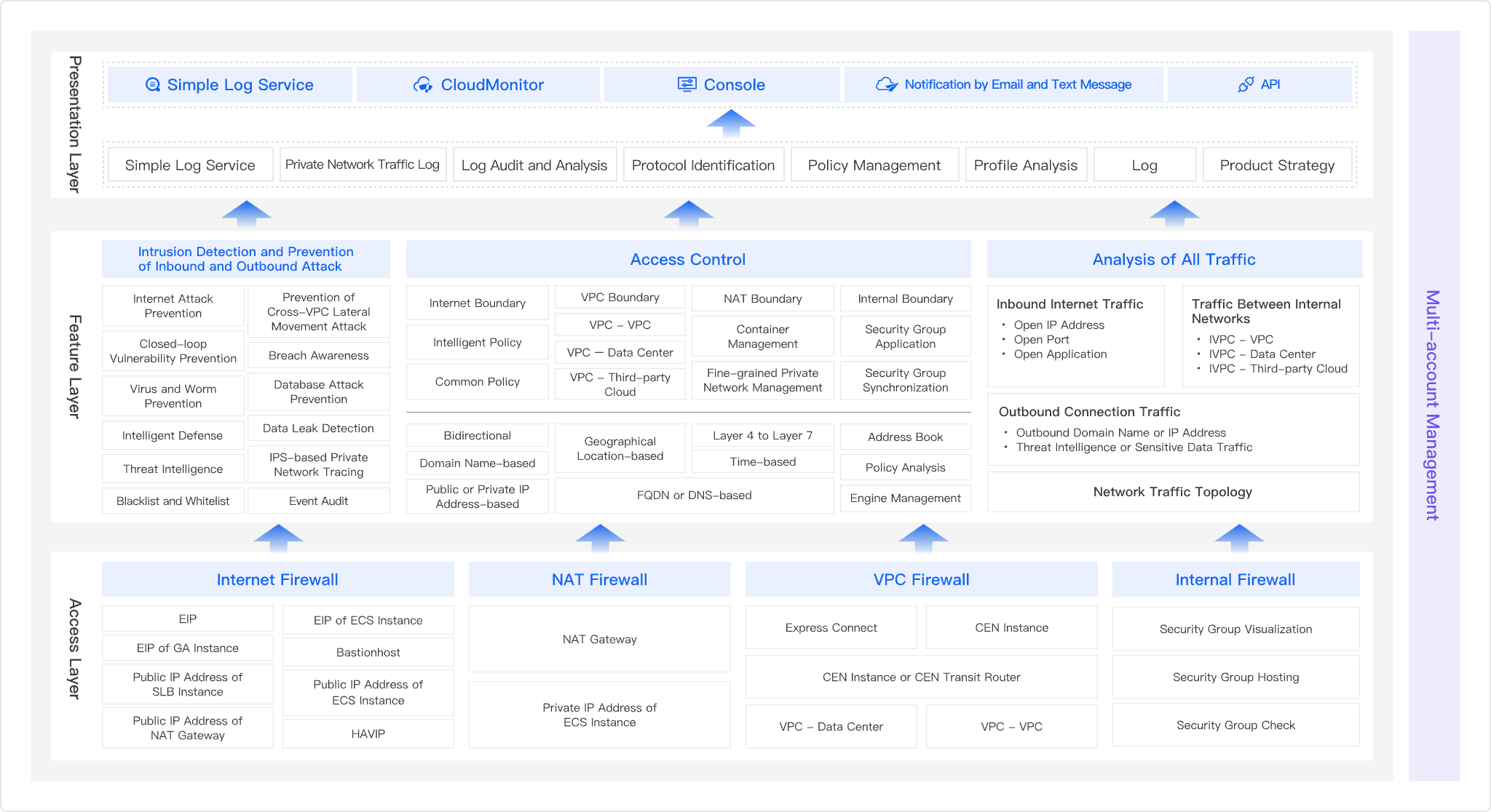
Alibaba Cloud Cloud Firewall is a SaaS-based firewall solution. It delivers unified security isolation and control across multiple dimensions, including the Internet Border, VPC Border, NAT Border, Host Border, and DNS Border. As your primary network defense, it integrates the Internet firewall, VPC firewall, NAT firewalls, Host firewall, and DNS firewall to provide comprehensive protection for your internet, virtual network, and host assets.
Cloud Firewall Editions

• Outbound abnormal traffic defense and access controls
• Inbound Internet attack defense and access controls

• Basic Firewall Capability
• Provide North-South Flow Control
• Provide Network IPS for N-S Traffic
• Traffic analysis and log management

• Traffic topology
• Security Group Centralized Mgmt.
• Multi-Account Centralized Mgmt.
• Support custom protection rules

• All features provided by the Enterprise edition
• Protect traffic between multi-accounts' VPCs connected by a CEN instance

• Outbound abnormal traffic defense and access controls
• Inbound Internet attack defense and access controls

• Basic Firewall Capability
• Provide North-South Flow Control
• Provide Network IPS for N-S Traffic
• Traffic analysis and log management

• Traffic topology
• Security Group Centralized Mgmt.
• Multi-Account Centralized Mgmt.
• Support custom protection rules

• All features provided by the Enterprise edition
• Protect traffic between multi-accounts' VPCs connected by a CEN instance
Benefits
Alibaba Cloud Cloud Firewall is easy to use, stable, and reliable. Deployed across the Internet, VPC, and NAT Borders, it allows you to easily build a cloud security system with the following advantages
Cloud-native
The product supports one-click protection for public assets, including public IP addresses of ECS instances, SLB public IPs, HAVIPs, EIPs, and NAT EIPs. It also supports automatic protection for newly added assets. You can enable it instantly without altering your network architecture. This ensures immediate defense with no complex configuration, significantly reducing O&M efforts.
Elasticity and Stability
Cloud Firewall scales smoothly with your business needs, ensuring zero interruption. It also features built-in HA to guarantee superior stability.
Deep Threat Defense
It proactively detects and blocks malicious traffic in real time, including hacker attacks, vulnerability exploits, brute-force attacks, worms, mining programs, backdoor trojans, and DoS attacks. This protects your enterprise information systems and network architecture on the cloud, preventing unauthorized access and data breaches.
Flexible Billing
Small and medium-sized businesses can choose the pay-as-you-go model, while larger enterprises can opt for a subscription plan. Our billing methods are diverse and flexible.
Features
Fine-Grained Access Control
Cloud Firewall allows you to centrally manage access control policies from the Internet to services and microsegmentation policies between services. Cloud Firewall supports fine-grained access control from Layer 4 to Layer 7, including access control based on IP addresses, ports, applications, domains, and locations.
Detection and Protection of Outbound Connections
Cloud Firewall can detect and analyze the outbound connection traffic of cloud resources to help distinguish malicious requests. Cloud Firewall can display outbound connection traffic mirror sessions for your assets in real-time, helping detect suspicious hosts and breaches at the earliest opportunity.
VPC Isolation-and Control
VPC firewalls help detect and control the traffic between VPCs and the traffic between VPCs and data centers. This way, you can implement fine-grained control over the traffic between VPCs, the traffic between VPCs and data centers, and the protection against internal lateral movement attacks.
Real-Time Intrusion Detection and Protection
Cloud Firewall uses the built-in threat detection engine and threat intelligence to block and intercept malicious traffic intrusions and common attacks on the Internet in real-time, including command executions, reverse shells, database attacks, mining and trojan programs, viruses, and worms.
Virtual Patch Protection for Vulnerabilities
Cloud Firewall can integrate with Security Center to detect vulnerabilities exploited by hackers to launch attacks on your Internet-facing assets. Cloud Firewall also provides virtual patches to defend against these vulnerabilities, including zero-day vulnerabilities. This way, you can prevent your assets from being intruded using vulnerabilities.
Control of Asset Exposure Risks
Cloud Firewall allows you to centrally manage and analyze assets exposed to the Internet (such as EIPs, public IP addresses of ECS instances, SLB instances, and ENIs). Cloud Firewall also supports fine-grained access control and Internet risk defense, helping reduce the network attack surface.
Multi-Account Management
Cloud Firewall supports the Resource Management features to help implement centralized security control over resources of multiple accounts (such as resource protection integration, security policy configurations, attack protections, and viewing log statistics). This helps improve the efficiency of security O&M.
Visualized Traffic Analysis
Cloud Firewall can display the traffic information in a visualized manner (such as the traffic information and traffic trend charts of all public IP addresses, statistics on top inbound and outbound traffic, and the trend charts and distribution of traffic across VPCs), helping monitor the outbound traffic for your Internet-facing assets and internal assets.
Network Log Audit and Analysis
Cloud Firewall supports the log audit feature for log records (including traffic logs, event logs, and operation logs) to help audit network traffic in real-time. For example, you can audit and track attack defense logs and hit results of access control rules.
Feature Comparison
| Feature | Alibaba Cloud | Vendor F |
|---|---|---|
| Cloud Network Asset Protection | ||
| Internet Traffic | ✔ | ✔ |
| VPC-to-VPC Traffic | ✔ | ✔ |
| NAT Gateway Traffic | ✔ | ✔ |
| Auto-sync and Protection for Public Assets | ✔ | ✖ |
| Elastic High Availability | ✔ | Requires separate deployment of HA components |
| Multi-account Management | ✔ | Requires separate purchase of a Manager component |
| Intrusion Prevention & Access Control | ||
| IPS Basic Protection | ✔ | ✔ |
| Threat Intelligence | ✔ | ✔ |
| Emergency Vulnerability Patching | 3 hours | 24+ hours |
| Intelligent Defense | ✔ | ✖ |
| Outbound Sensitive Data Detection | ✔ | ✖ |
| Intelligent Address Book | ✔ | ✖ |
| Traffic Visualization & Analysis | ||
| Anomaly Detection for Traffic Trends | ✔ | ✔ |
| Public Exposure Analysis | ✔ | ✔ |
| Proactive Outbound Connection Analysis | ✔ | ✖ |
| VPC Inter-Access Analysis | ✔ | ✖ |
| AI Tool Access Traffic Analysis | ✔ | ✖ |
Scenarios

Security Capabilities Required for Internet-Facing Asset Protection and Control
Cloud Firewall provides automatic protection for your Internet-facing assets. It combines network-wide threat intelligence and virtual patch features to protect your Internet-facing assets against attacks. In addition, Cloud Firewall allows you to sort your Internet-facing assets and control access to your Internet-facing assets.
Highlights
-
 Prevention of Risks Introduced by the Exposure of on-Cloud Assets to the Internet
Prevention of Risks Introduced by the Exposure of on-Cloud Assets to the InternetYou can easily handle the security issues caused by the exposure of cloud assets.
-
 Access Policy and Security Specification Management
Access Policy and Security Specification ManagementCloud Firewall helps check the access policies for inbound and outbound traffic.
Related Service

Cloud Firewall Solutions in Hybrid Cloud Scenarios
You can deploy a cloud firewall among multiple VPCs or between a VPC and a data center to isolate VPCs and defend against lateral movement attacks. You can also deploy Cloud Firewall to protect leased line connections between a VPC and a data center in hybrid cloud scenarios.
Highlights
-
 Traffic Security between VPCs
Traffic Security between VPCsCloud Firewall can help you detect and control the traffic between multiple VPCs.
-
 Prevention of Risks Introduced by Access between VPCs and Data Centers
Prevention of Risks Introduced by Access between VPCs and Data CentersThe control and protection feature for the traffic between VPCs also applies to the traffic between VPCs and data centers.
Related Service

Meeting the Requirements of Classified Protection of Cybersecurity
You can deploy Cloud Firewall to meet the level 2 and level 3 requirements of Classified Protection of Cybersecurity 2.0 (such as requirements for border protection, access control, intrusion prevention, malicious code prevention, spam prevention, and security audit).
Highlights
-
 Classified Protection of Cybersecurity
Classified Protection of CybersecurityYou can deploy Cloud Firewall to meet the requirements of Classified Protection of Cybersecurity 2.0 (such as requirements for zone border protection, network access control, network intrusion prevention, and traffic security audit).