BDRC Overview
Advantages
-

-
All-in-One Compliance & Protection
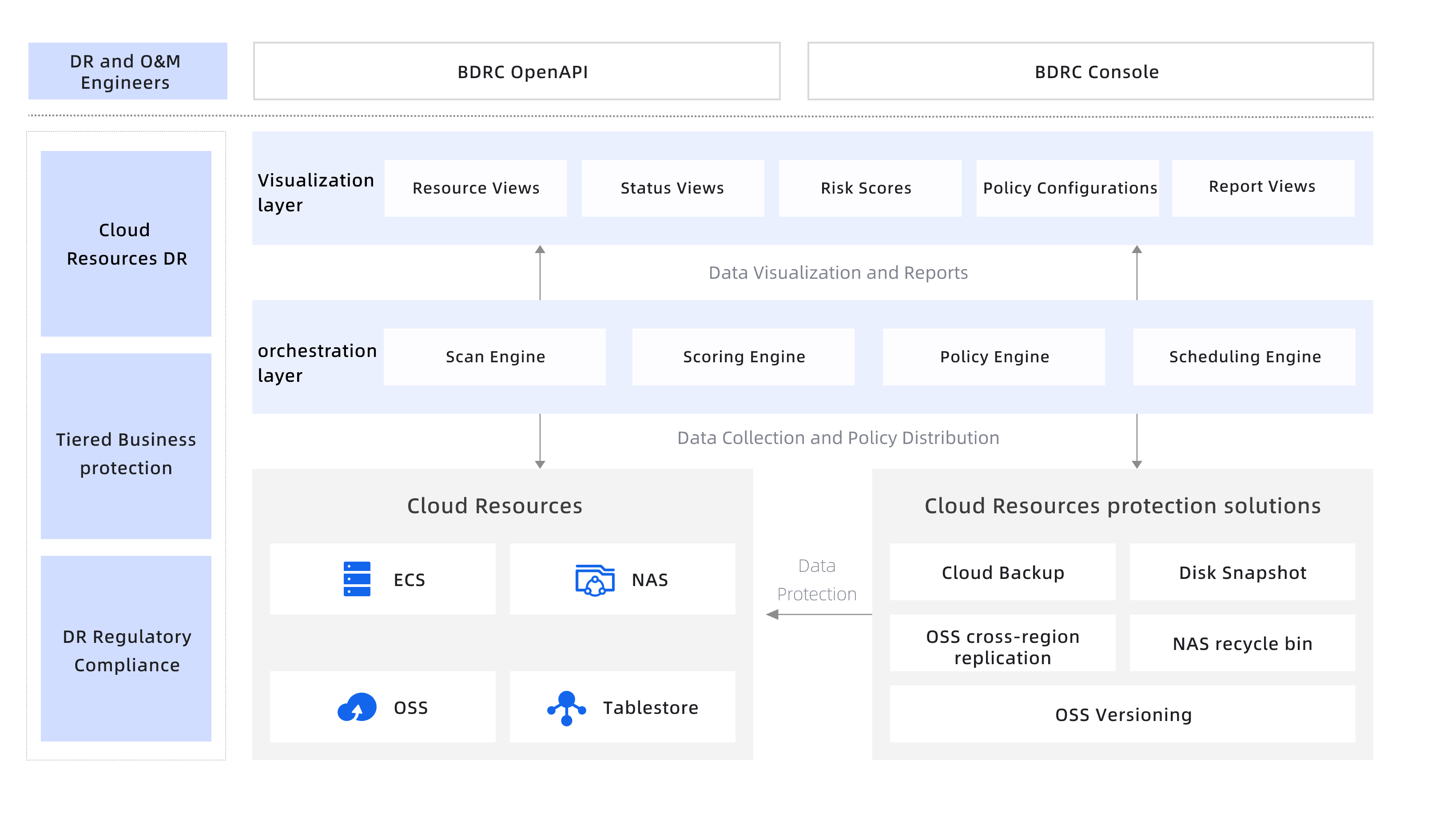
Alibaba Cloud's Native Data Storage Disaster Recovery Solution with Full Coverage
-

-
Visual Insights & Cross-Region Compliance
Multi-angled data protection view with score, star ratings and 3D visualization
-

-
Custom Policies & Centralized Control
Categorize and manage resources based on their usage to meet business needs
-

-
Ease of use
All-in-one policy center with guided configuration process to simplify the process
Use Case
-
01
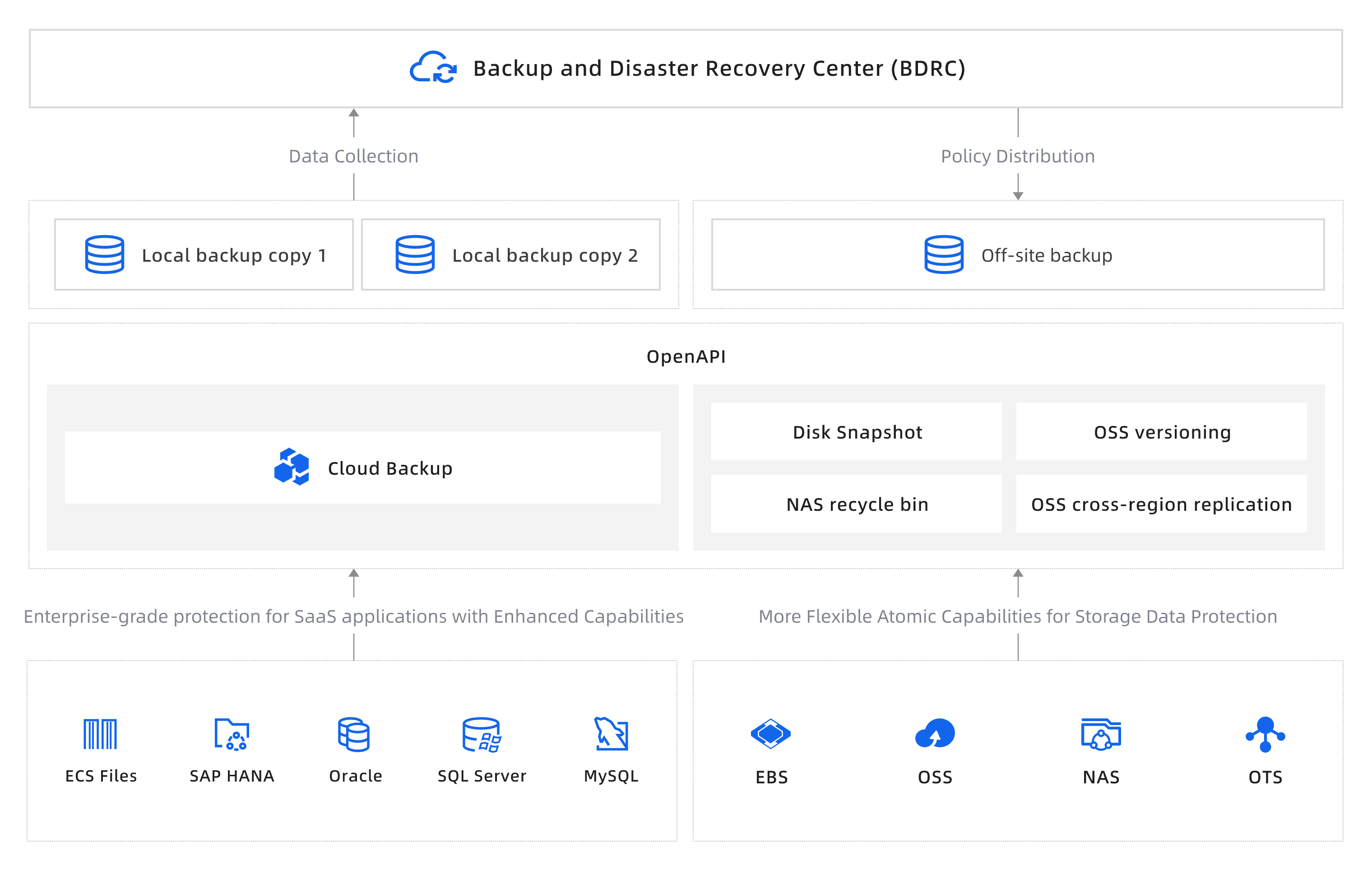
Unified Backup Management
BDRC empowers enterprises to streamline cloud resource backups with adaptive, tiered protection aligned with data criticality, ensuring compliance and operational resilience. -
02
Cloud Asset Backup
BDRC provides multi-asset protection for cloud resources (ECS, OSS), ensuring rapid recovery and data integrity with automated failover and granular retention policies, delivering resilience and business continuity. -
03
Tiered Data Protection
Organize resources into protection tiers based on importance to prioritize, assess, and monitor security levels, ensuring alignment with compliance and operational requirements across diverse scenarios. -
04
Compliance-Driven Data Protection
Assess configuration health for local and off-site backups to pinpoint gaps and implement targeted solutions, ensuring compliance readiness.
Security and Compliance
-
Data Security
BDRC employs a minimal-data-access architecture to ensure robust data protection.
BDRC interacts exclusively with non-sensitive metadata (e.g., instance configurations, timestamps, permissions) and does not collect, store, or process actual user data (e.g., files, databases, application content). This design aligns with GDPR, HIPAA, and PCI-DSS compliance requirements, minimizing exposure to sensitive information.
Secure, API-Driven Integration:
All interactions leverage industry-standard OpenAPIs provided by cloud platforms (e.g., AWS, Azure, GCP). These APIs enable BDRC to assess data protection status (e.g., encryption settings, backup policies) without requiring direct access to underlying data. Authentication and encryption are enforced at the API level, ensuring secure, auditable access.
Learn More > -
Access Control
BDRC adheres to security best practices by implementing strict access controls and transparent authorization mechanisms.
Principle of Least Privilege (PoLP) Minimal Permissions:
BDRC operates with only the essential permissions required to monitor data protection status (e.g., reading metadata, checking backup configurations). No Hidden Access: No additional or "hidden" permissions are utilized, ensuring full transparency and alignment with GDPR, SOC 2, and CIS benchmarks. Compliance Alignment: This approach minimizes attack surfaces and reduces the risk of privilege escalation, meeting global regulatory requirements.
RAM-Based Authorization Framework Role-Based Access Control (RBAC):
BDRC leverages Resource Access Management (RAM) identities to authenticate and authorize actions. Secure Detection & Remediation: Detecting data protection status (e.g., encryption gaps, backup failures) requires RAM-based authentication. Implementing countermeasures (e.g., enabling encryption, configuring backups) also demands explicit RAM permissions, ensuring accountability and audit-ability. Temporary Credentials: Access is granted via short-lived tokens or temporary credentials, reducing long-term exposure risks.
Learn More > -
Logging and auditing
BDRC ensures full traceability of all activities through detailed logging and auditing mechanisms. This provides end-to-end visibility into cloud resource monitoring, risk management, and policy enforcement.
Scan Auditing Cloud Resource Scans:
Every scan performed by BDRC on cloud resources (e.g., instances, storage, databases) is automatically logged, including timestamps, scope, and results. Audit Trail: Logs capture metadata such as scan triggers, configurations, and detected risks, enabling forensic analysis and compliance validation.
Integration:
Logs are stored in a structured format (e.g., JSON) and can be exported for integration with SIEM tools (e.g., Splunk, ELK Stack). Operation Auditing User Actions: All operations, including score queries, risk resolution workflows, policy creation, and configuration changes, are recorded with user identity, timestamp, and action details.
Transparency:
Logs provide a complete audit trail for governance teams to verify compliance with internal policies and external regulations (e.g., GDPR, SOC 2). Access Control: Audit logs are protected by role-based access controls (RBAC) to ensure only authorized personnel can view or modify them.
Learn More >
Pricing
BDRC is free to use! Enhancing data protection scores or resolving risks may require paid services like ECS snapshots or Cloud Backup, depending on your implementation needs.
For more information about other costs that may arise, see Relevant Pricing.




