By Victor Mak, Lead Solutions Architect, Alibaba Cloud Intelligence International Macau
During the pandemic, more enterprises strengthened their beliefs and quickened their paces in cloud migration and digital transformation. They actively explored the implementation of cloud-native architecture transformation. Container technologies represented by Kubernetes became a new interface for cloud computing. However, container security encountered several challenges:
Alibaba Cloud Security Center container security modules allow you to detect and prevent intrusions. The modules cover the whole container lifecycles. It ensures the security of container images during container creation. It checks container configurations during container deployment by using a baseline check. It detects and prevents intrusions during the running of containers. Please refer to the Container Security Alibaba Cloud documentation for more information.
This article focuses on two container security modules:
The section below describes how to build fine-grained security control on your container platform based on Alibaba Cloud best practices step by step:
The following figure illustrates the microservices architecture to demonstrate the container security features:
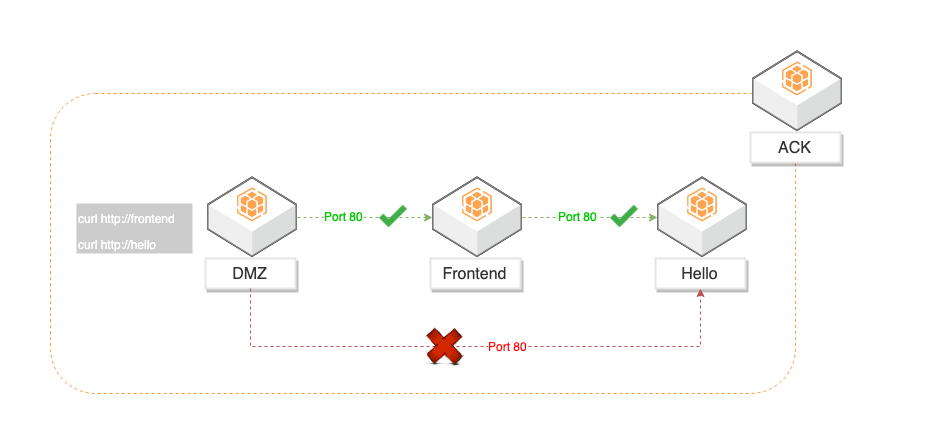
Three services were deployed in Alibaba Cloud Container Services (ACK) in this demonstration:
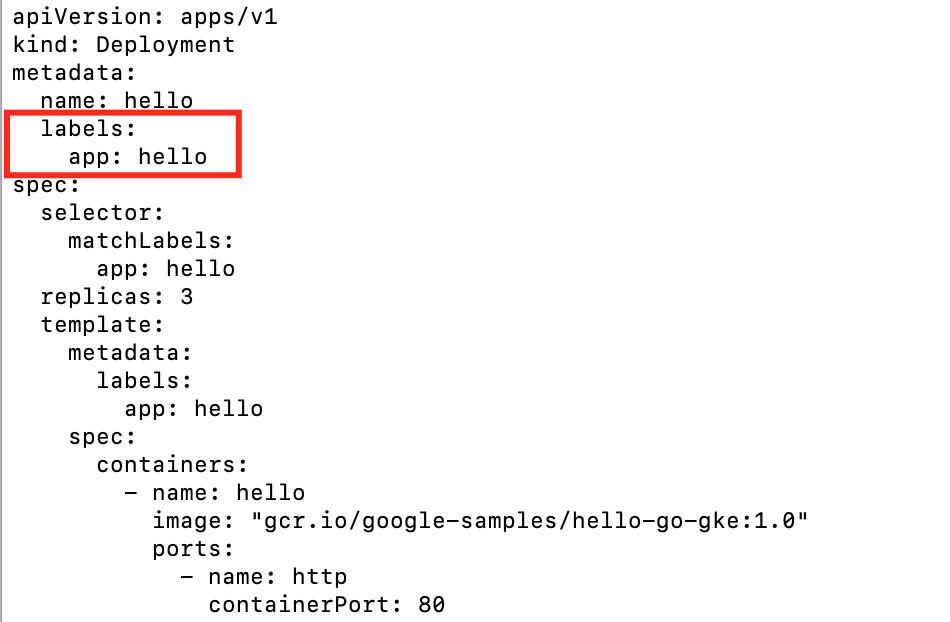
1. Hello service YAML file:
apiVersion: apps/v1
kind: Deployment
metadata:
name: hello
labels:
app: hello
spec:
selector:
matchLabels:
app: hello
replicas: 3
template:
metadata:
labels:
app: hello
spec:
containers:
- name: hello
image: "gcr.io/google-samples/hello-go-gke:1.0"
ports:
- name: http
containerPort: 802. Frontend service YAML file:
apiVersion: apps/v1
kind: Deployment
metadata:
name: frontend
labels:
app: frontend
spec:
selector:
matchLabels:
app: frontend
replicas: 1
template:
metadata:
labels:
app: frontend
spec:
containers:
- name: frontend
image: "gcr.io/google-samples/hello-frontend:1.0"
lifecycle:
preStop:
exec:
command: ["/usr/sbin/nginx","-s","quit"]3. DMZ service YAML file:
apiVersion: apps/v1
kind: Deployment
metadata:
name: dmz
labels:
app: dmz
spec:
replicas: 1
selector:
matchLabels:
app: dmz
template:
metadata:
labels:
app: dmz
spec:
containers:
- name: dmz
image: "bitnami/nginx"Before you begin, make sure:
Since Container Security is only available in Alibaba Cloud Security Center Ultimate Edition, customers need to upgrade/purchase this edition to protect their container environment:
1. Log on to the Security Center console
2. On the Overview page, click Immediate Purchase:
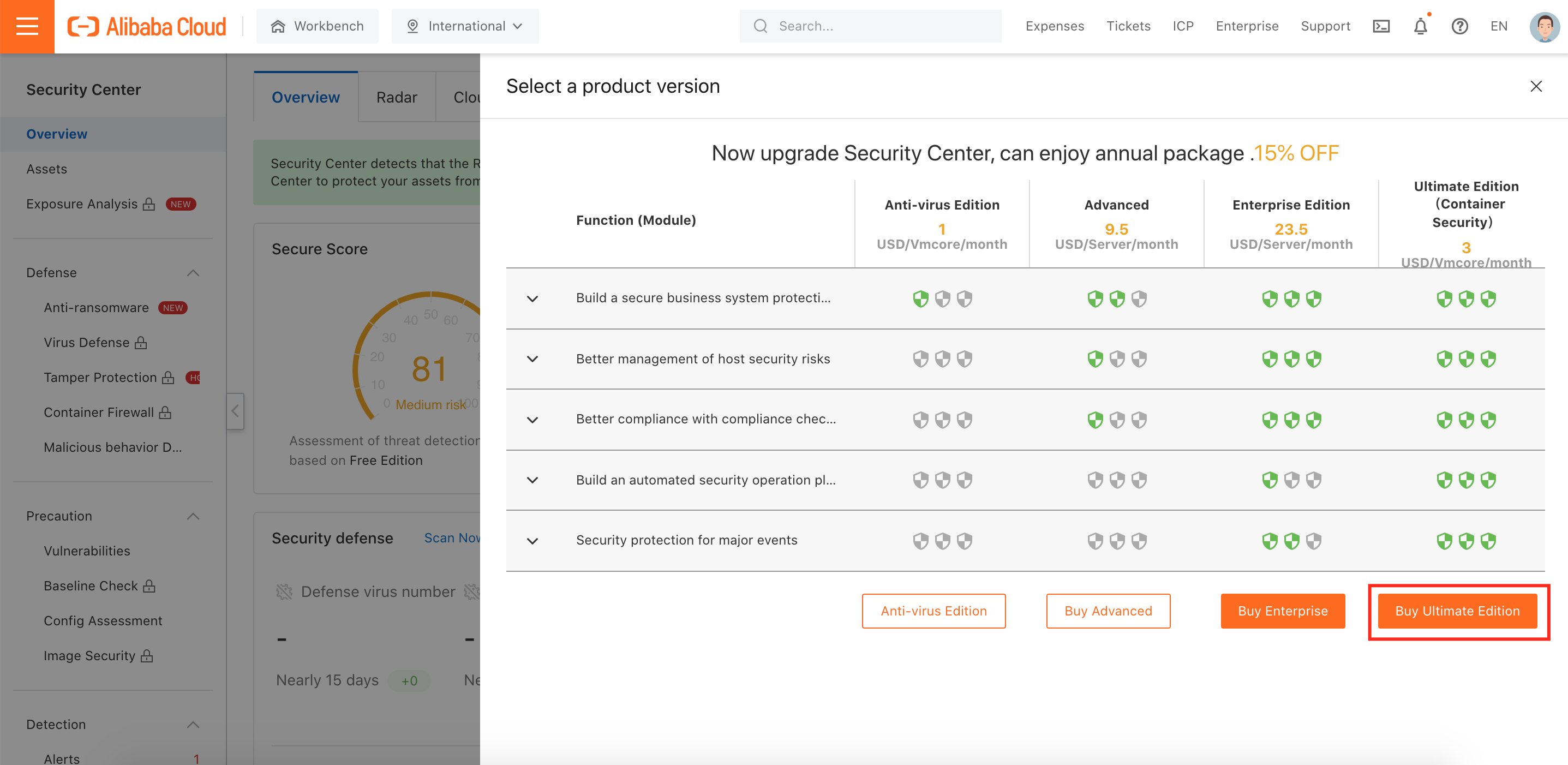
3. Select the Ultimate (Container Security) and the number of CPU Cores (vCore) and then click Buy Now:
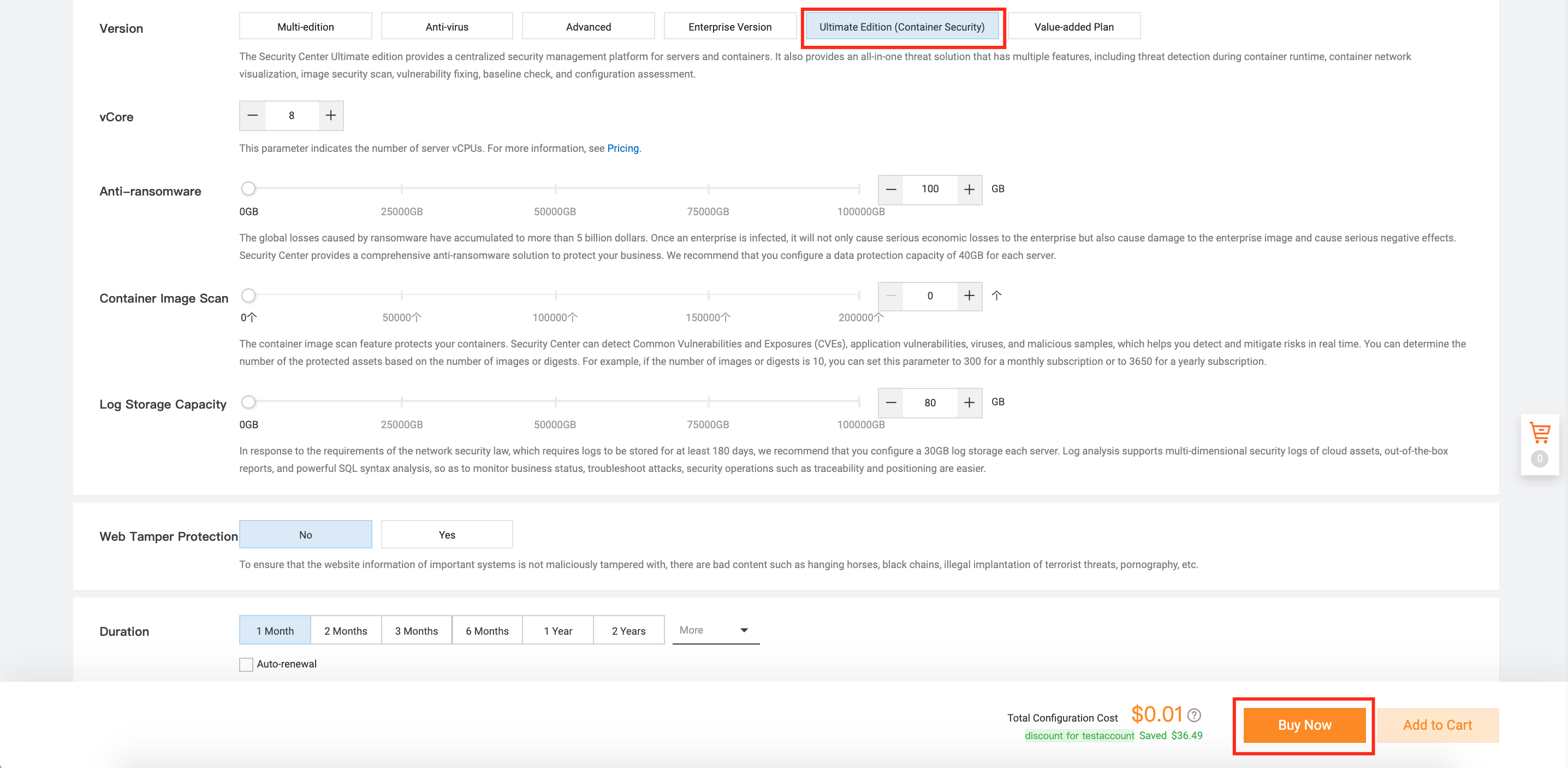
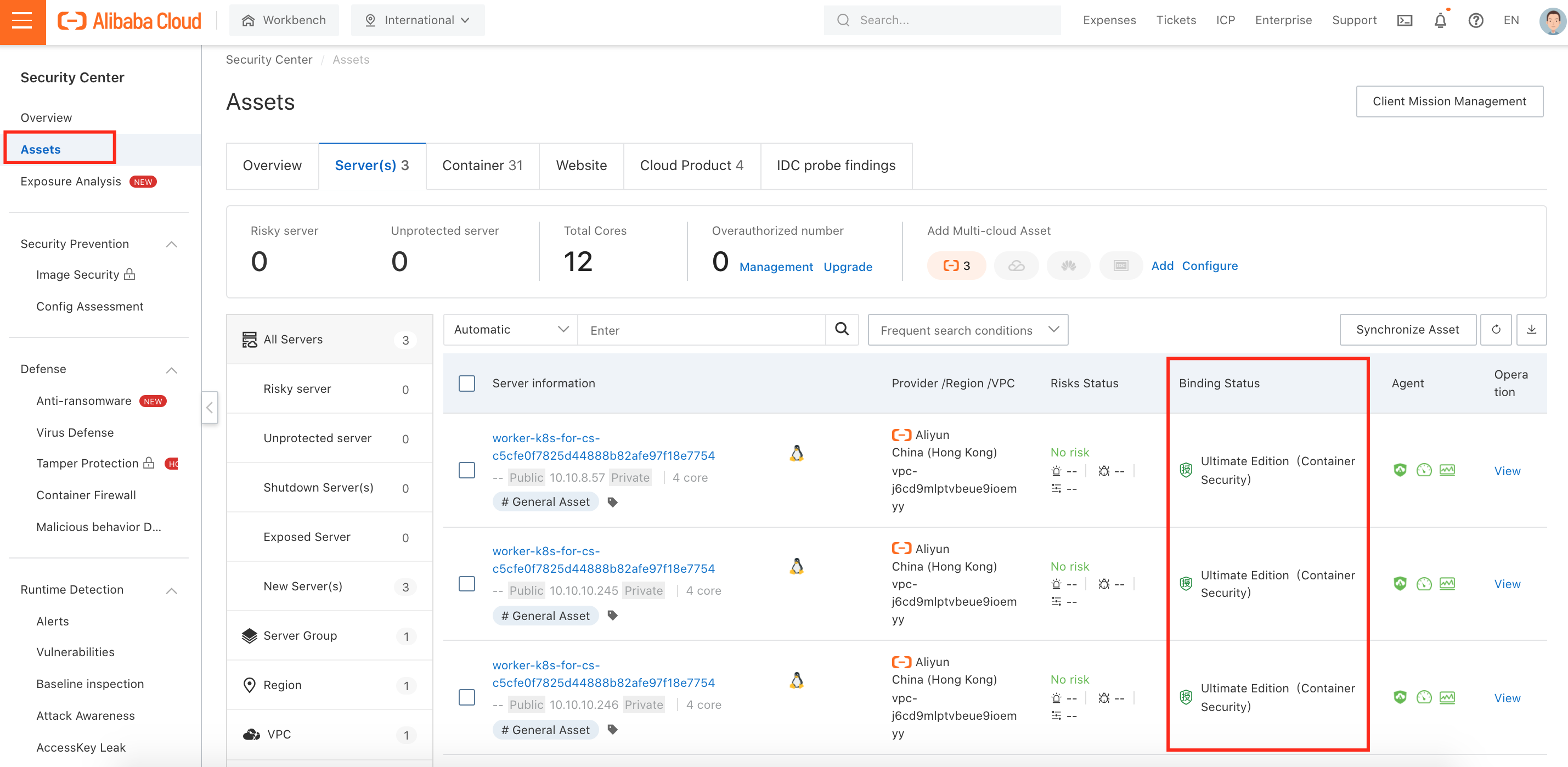
4. After enabling Security Center Ultimate Edition, make sure your Alibaba Cloud Container Service (ACK) worker nodes have already installed Security Center Agent with Ultimate Edition:
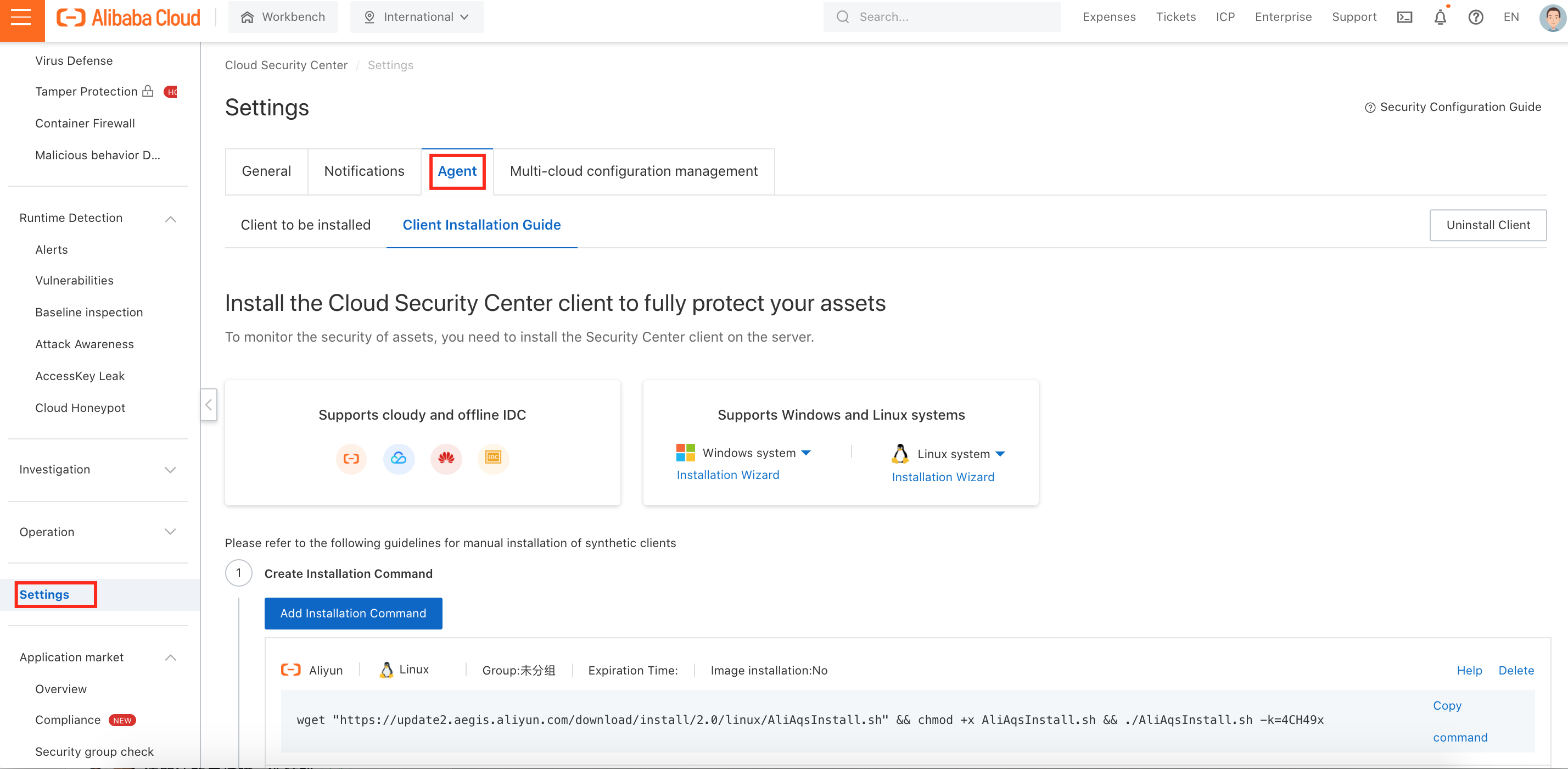
5. If you have not completed Step 4, you can follow the installation guide listed on the Agent page under Settings:
1. Add a protection object on the Container Firewall Object page under Defense:
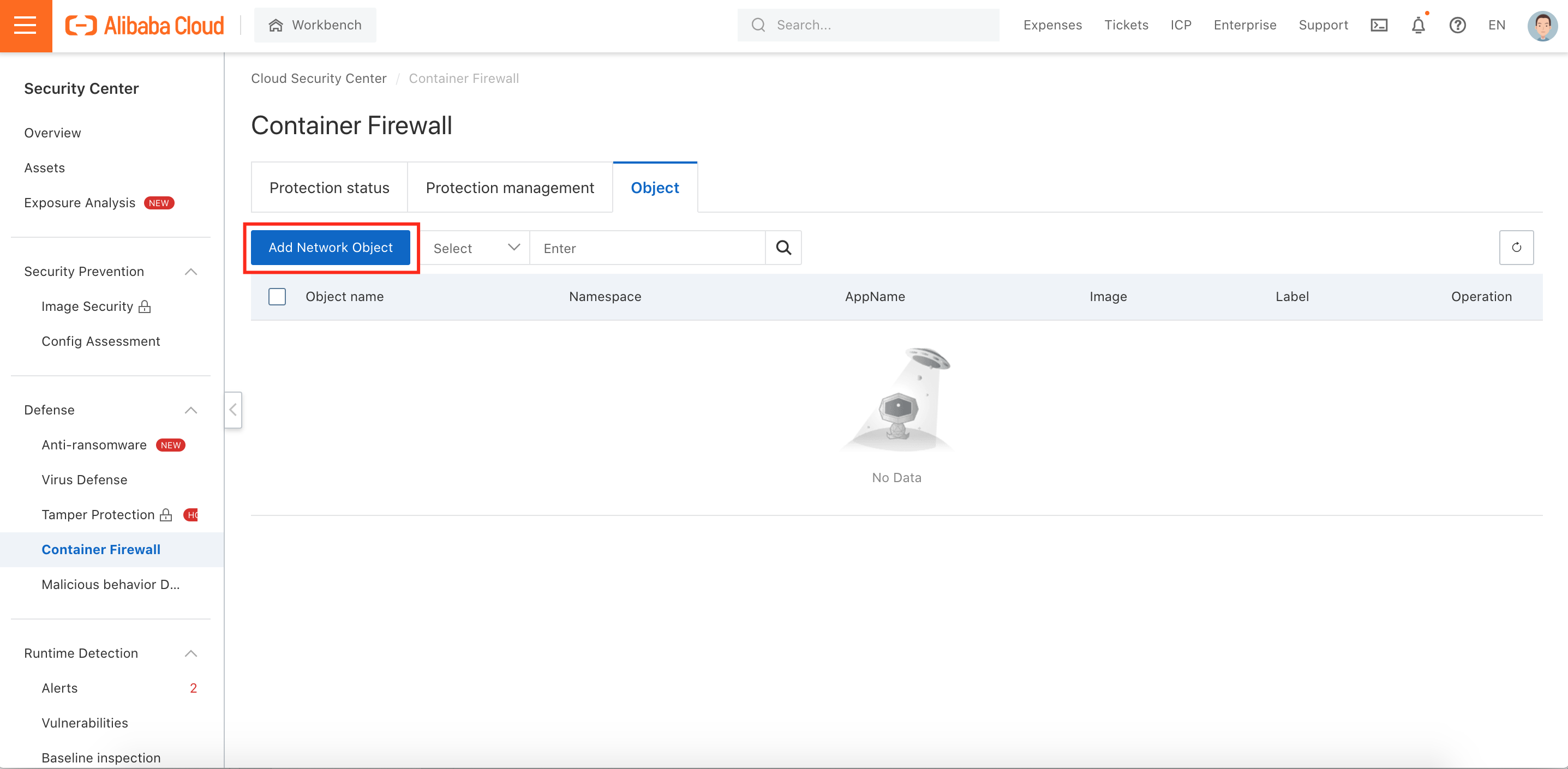
2. Configure the parameters on the Add Network Object panel. (Remark: The AppName is the tag whose tag is an app in the cluster. Fuzzy matching is supported. Example: a):
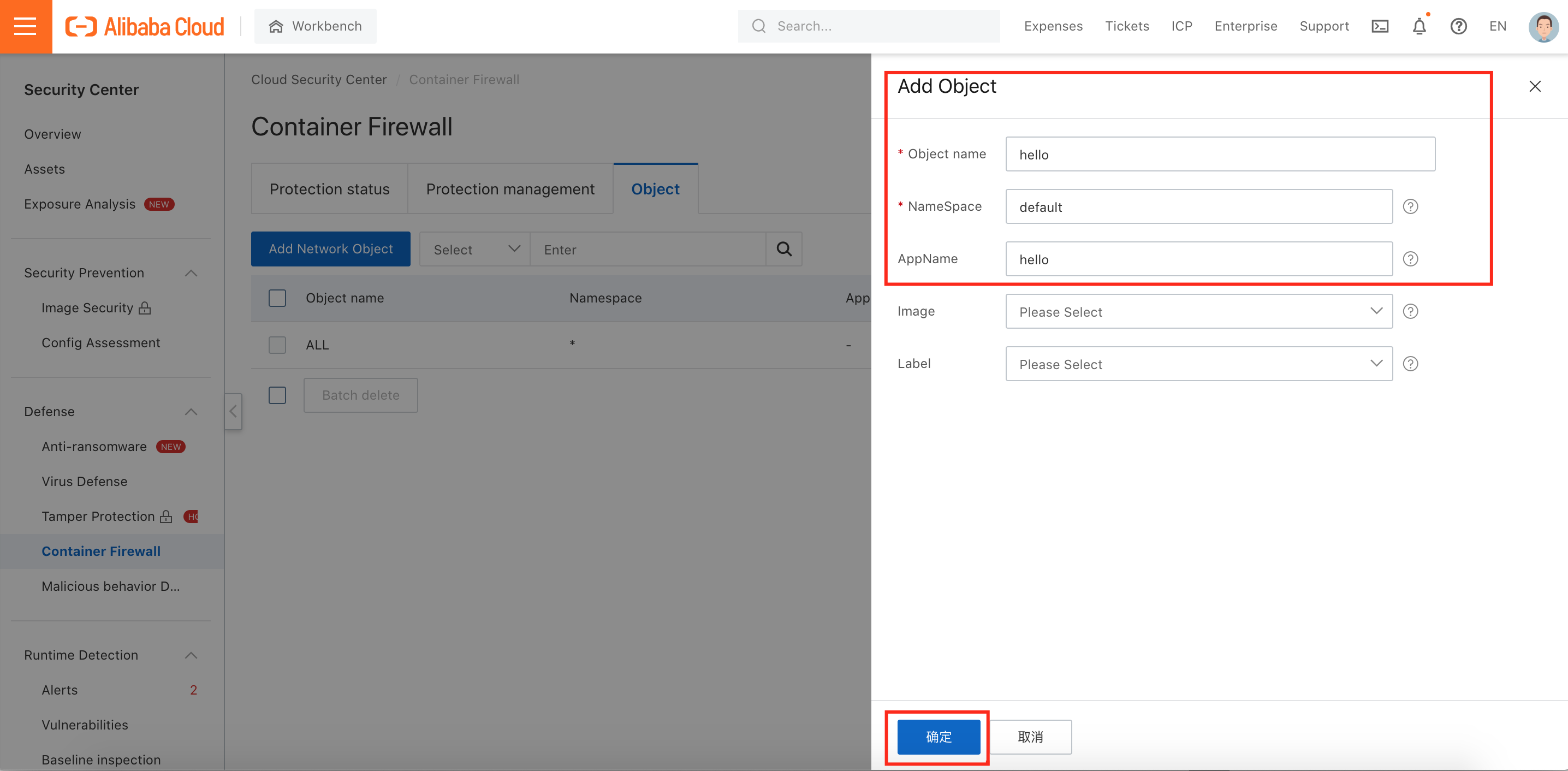
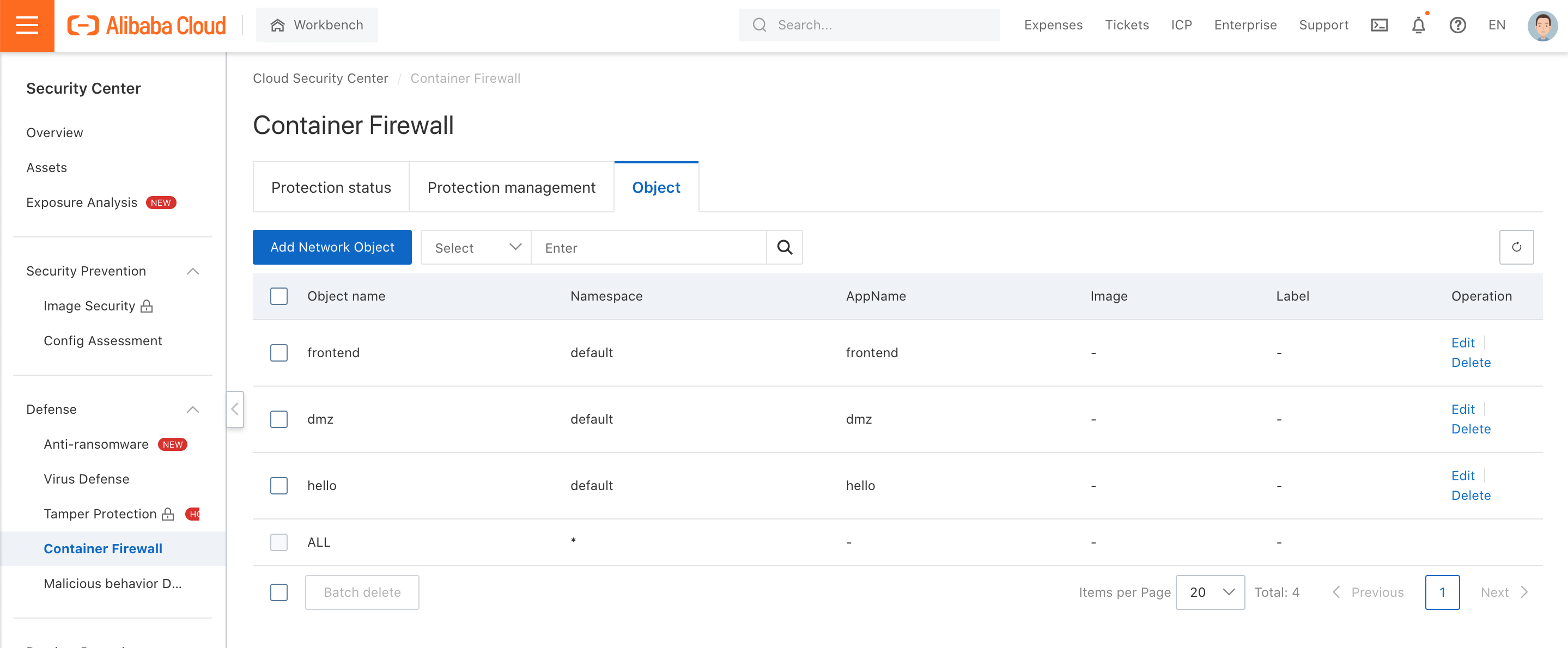
3. We added three network objects in this demonstration:
4. After you have added a protection object, you must create a defense rule to filter the traffic destined for container images. Then, click Rule Management under Protection Management:
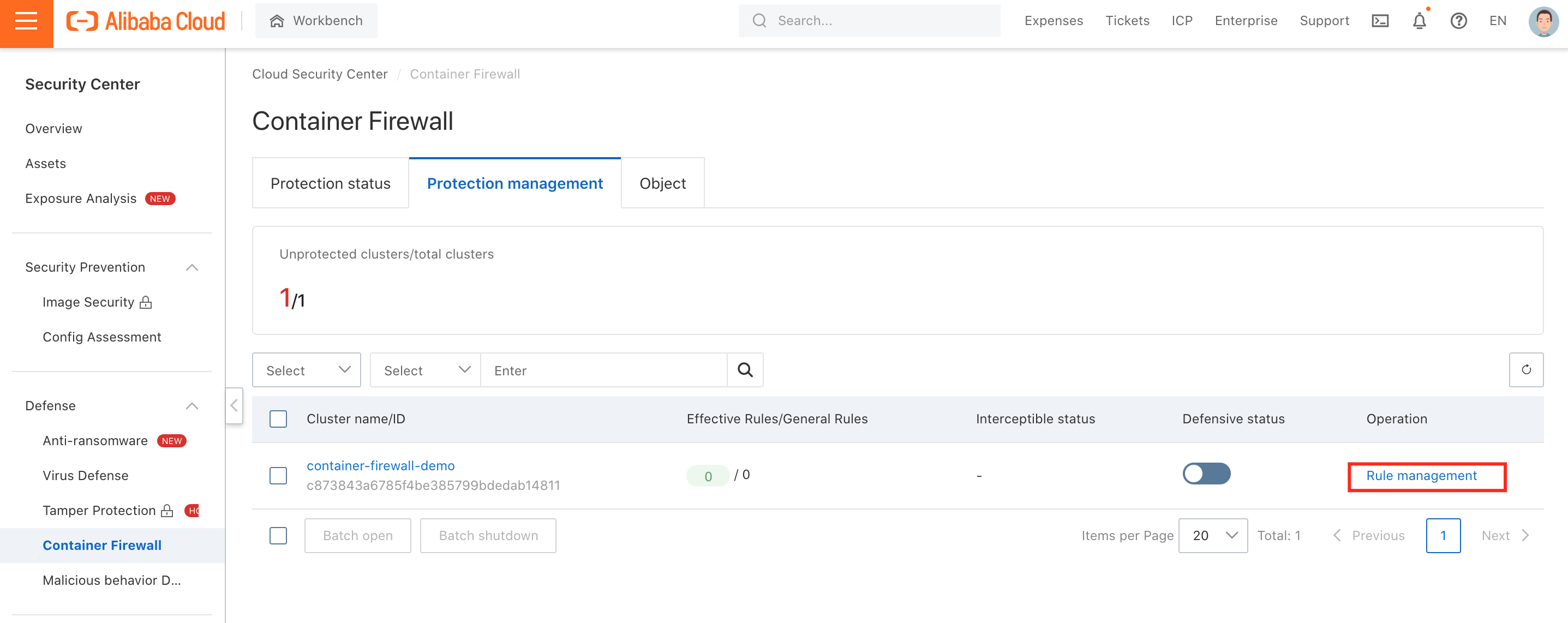
5. Click Create Rule:
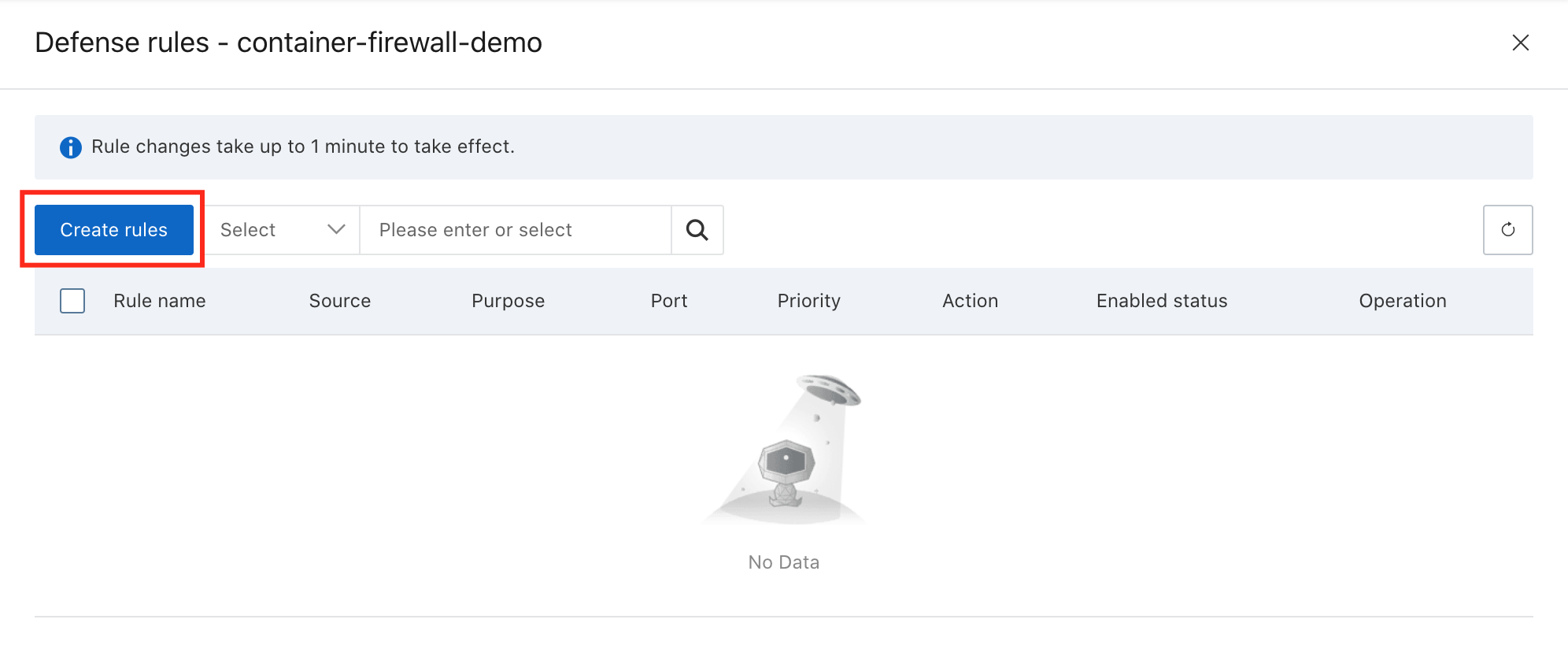
6. Define Rule name and select the source network object we created before:
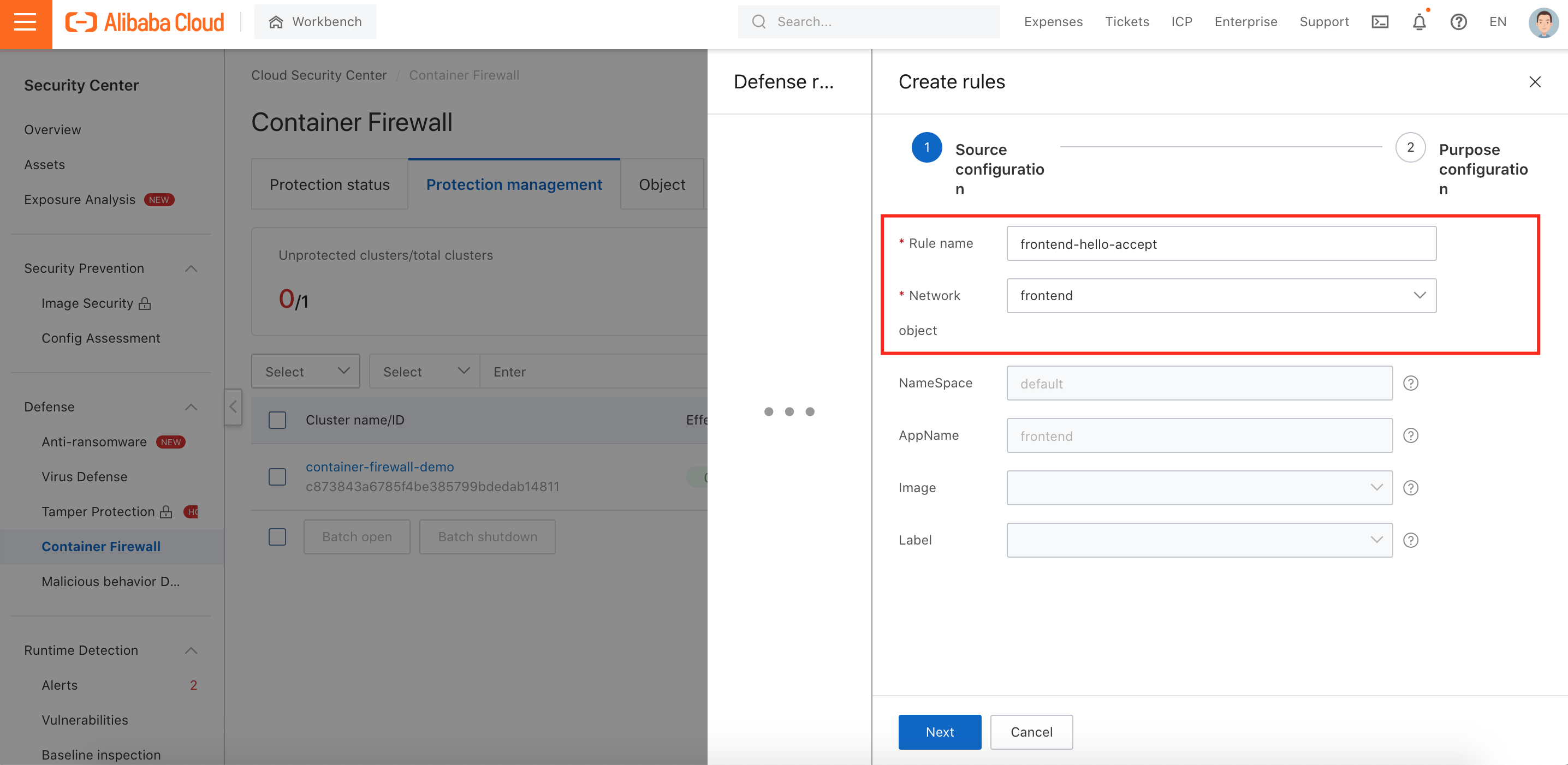
7. Select destination network object and then fill in Port, Action, Rule Status, and Priority:
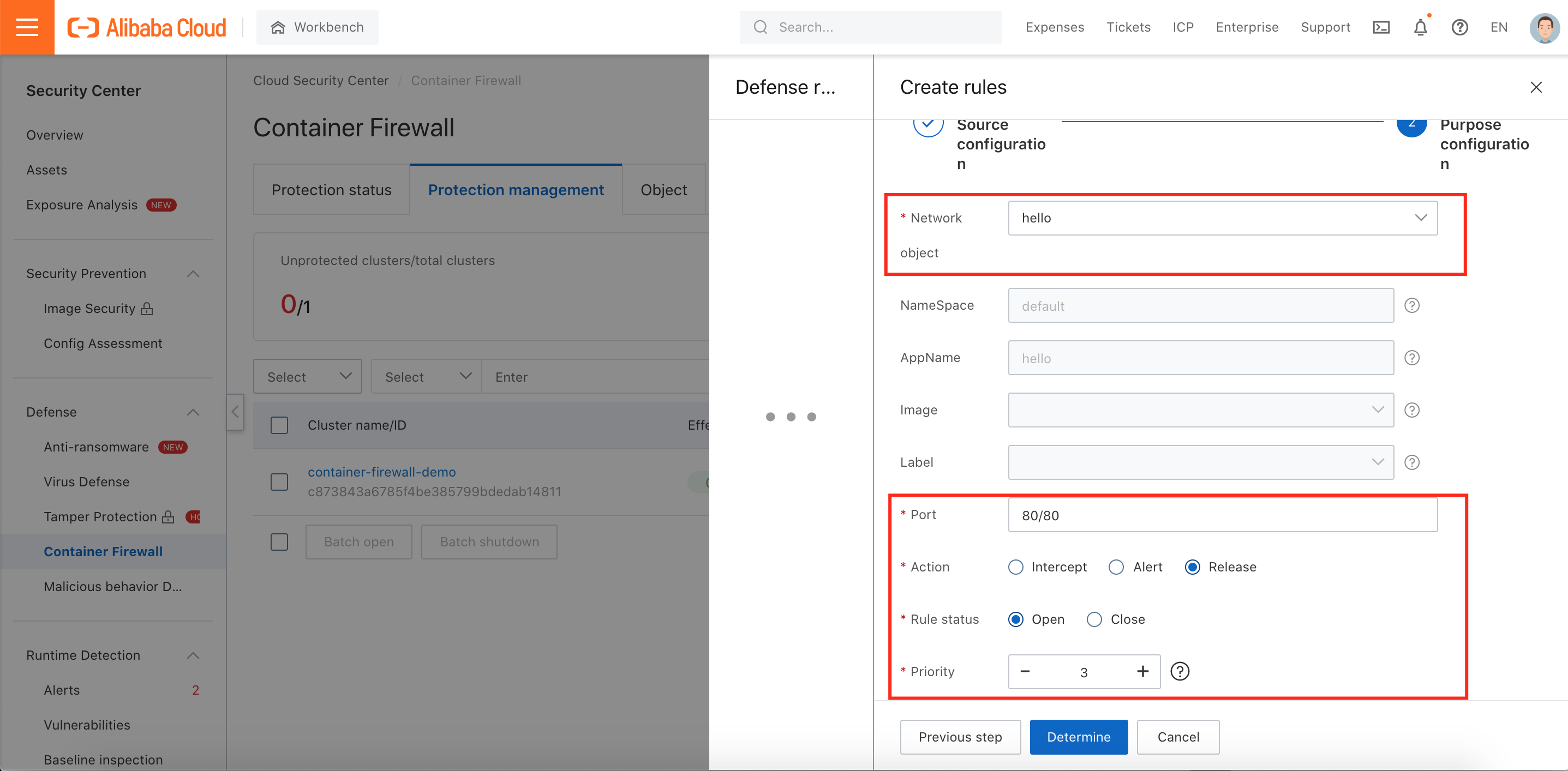
8. According to the demonstration diagram, we need to define four rules:
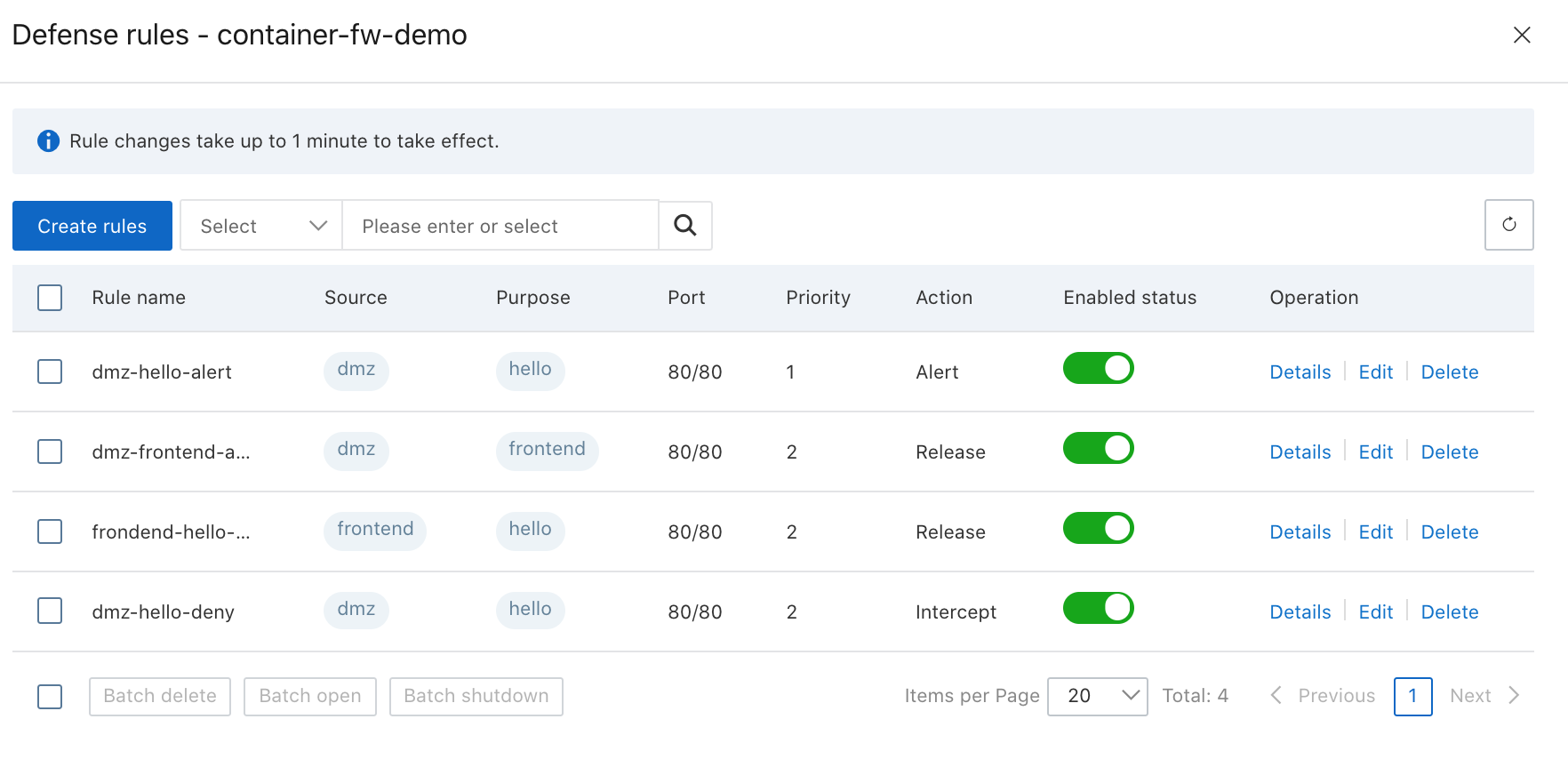
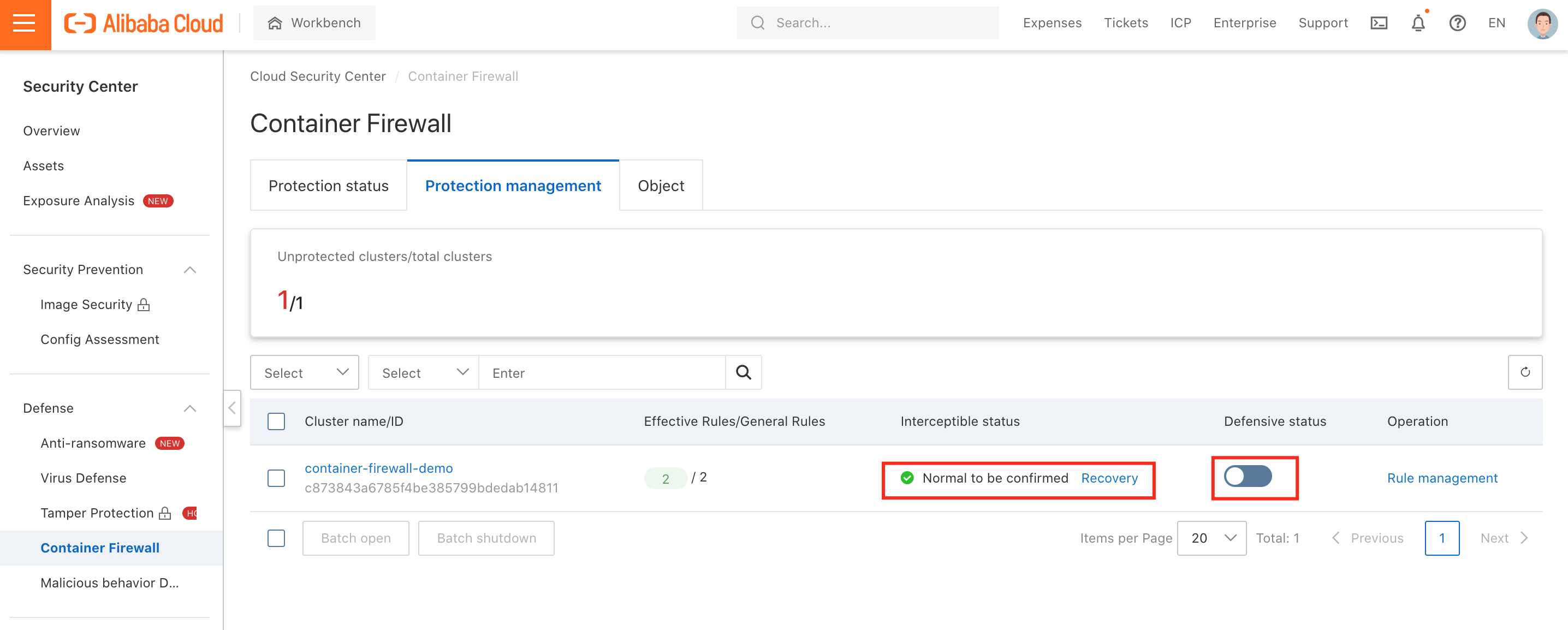
9. After configuring the security rules, enable container cluster level protection by toggling defensive status on the Protection management page:
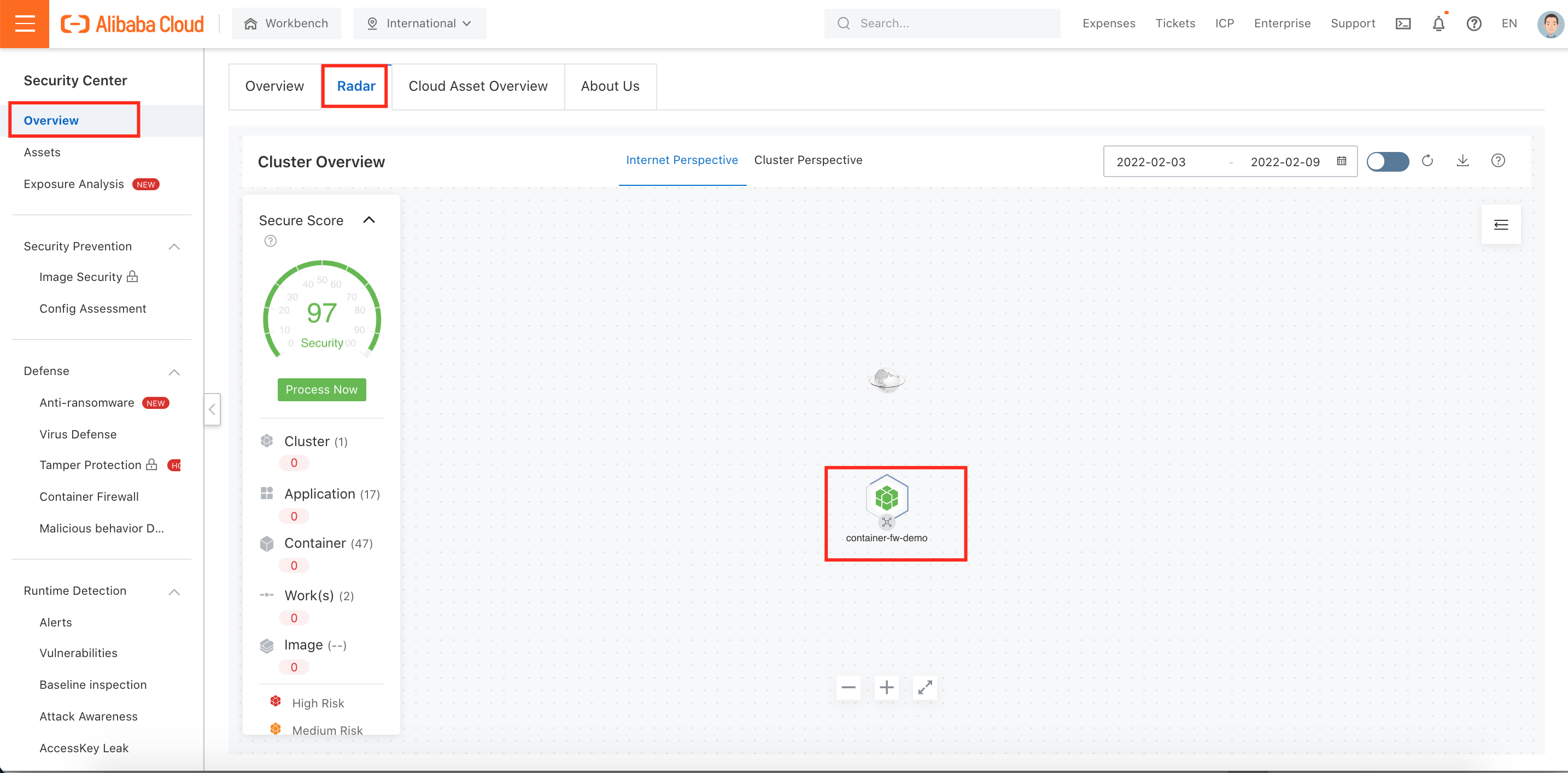
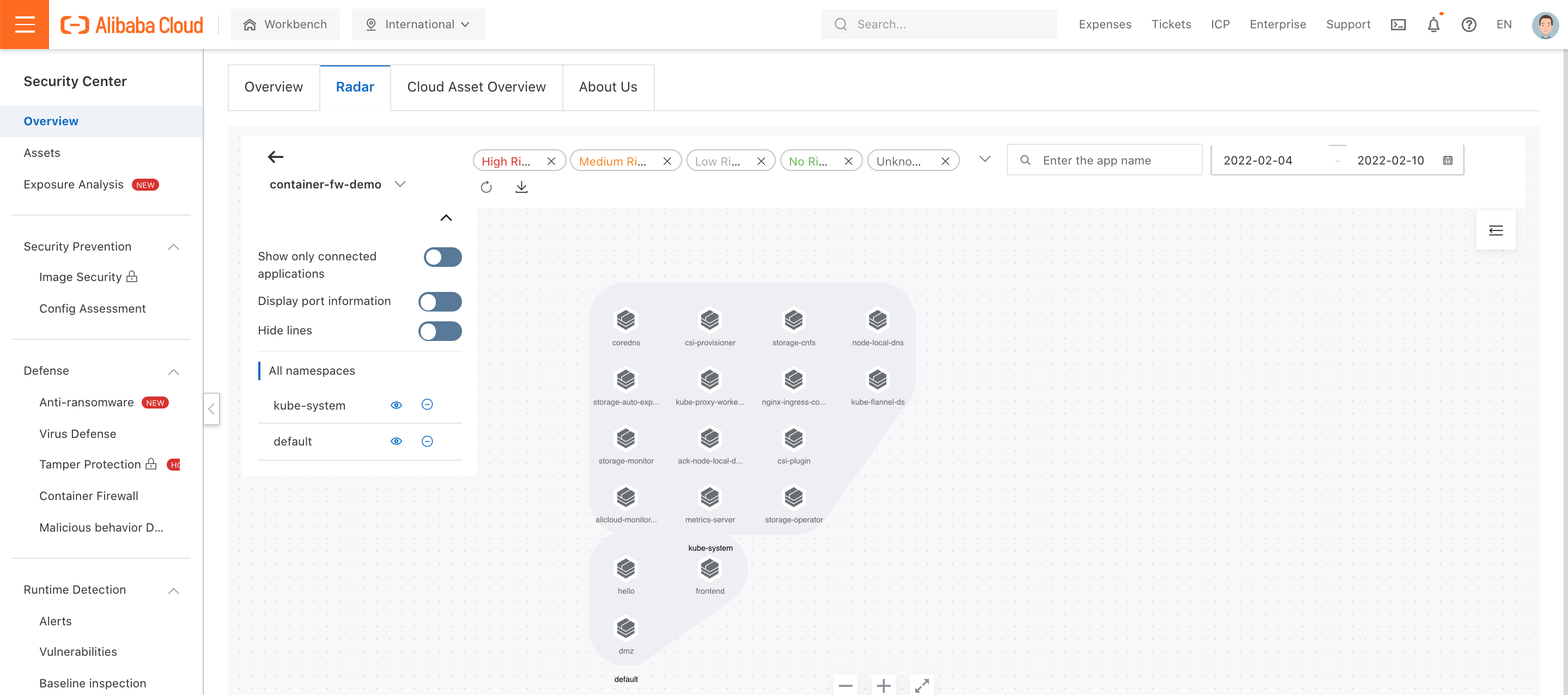
1. Navigate to the Radar page under Overview and double-check the container cluster:
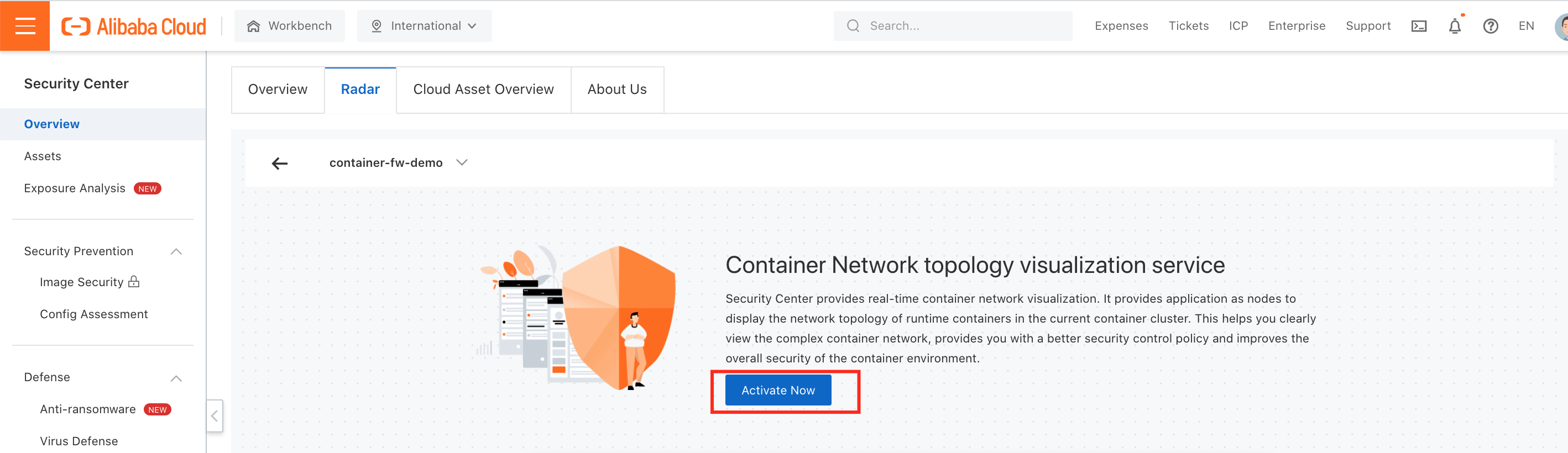
2. Select Activate Now to activate the network visualization feature:
3. After activation, you can browse container network topology in a single graphical user interface:
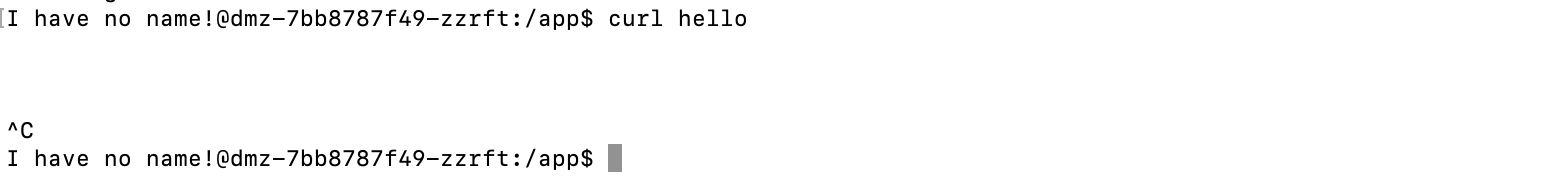
1. Log in to the DMZ container using the kubectl exec command and use curl to trigger the HTTP request:
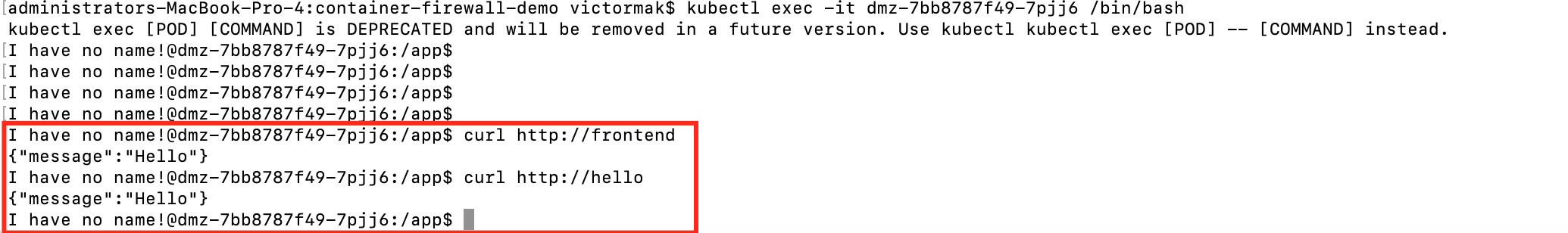
2. According to the policies we defined above, DMZ should be able to access hello. Security Center should address any related alarms.
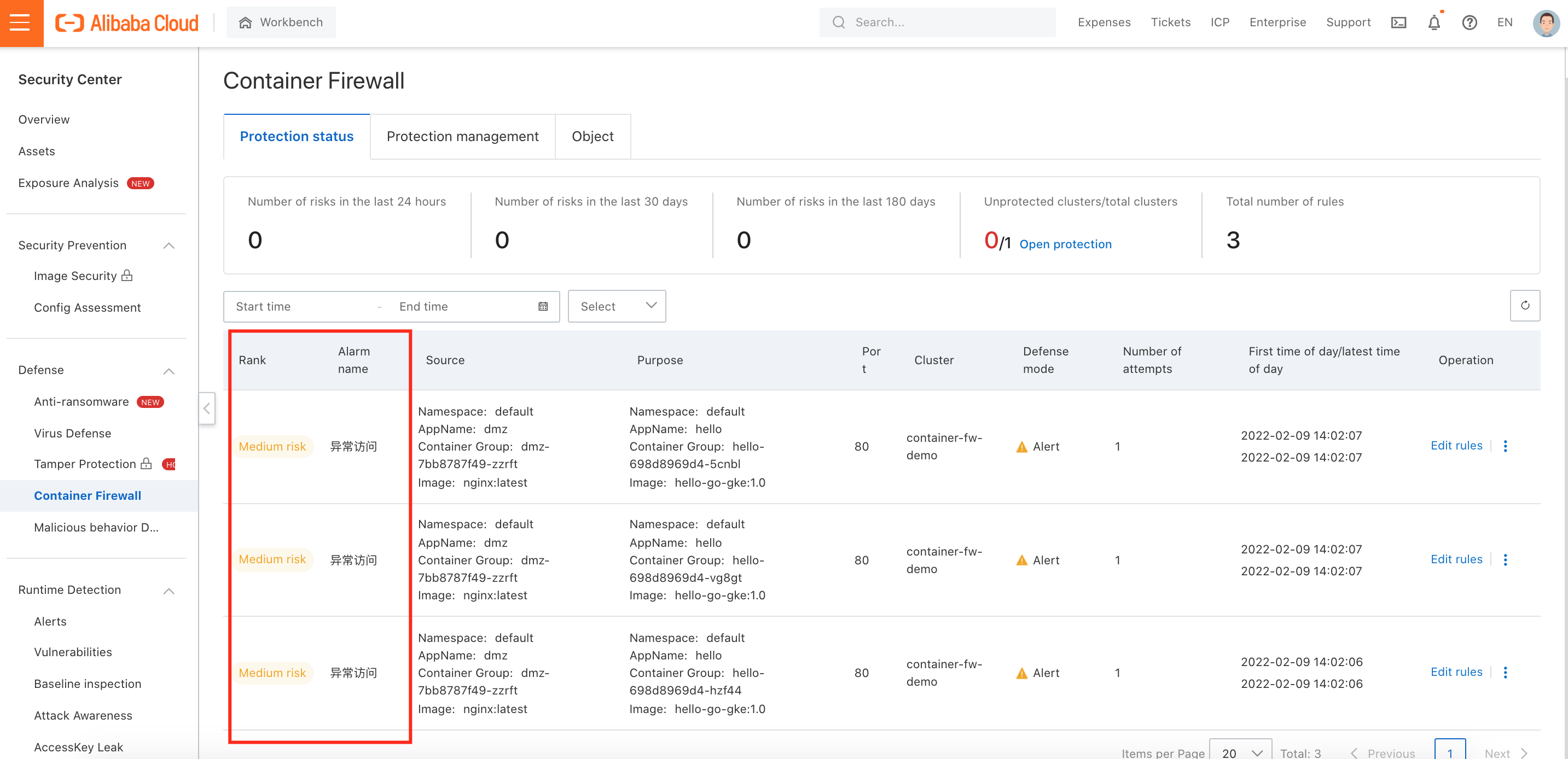
3. Change alert rule status to Disabled:
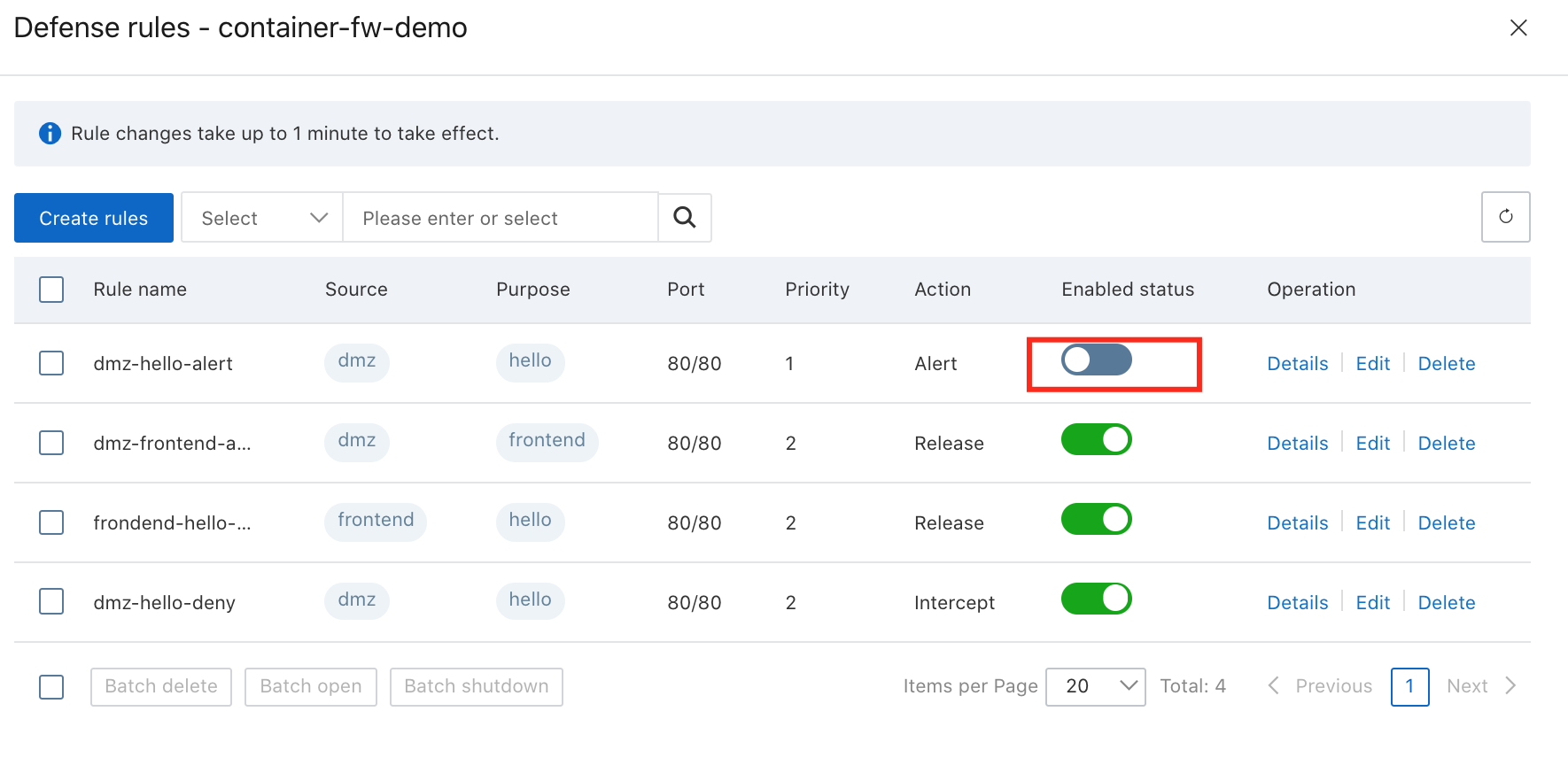
4. The DMZ container should not be able to access hello directly:
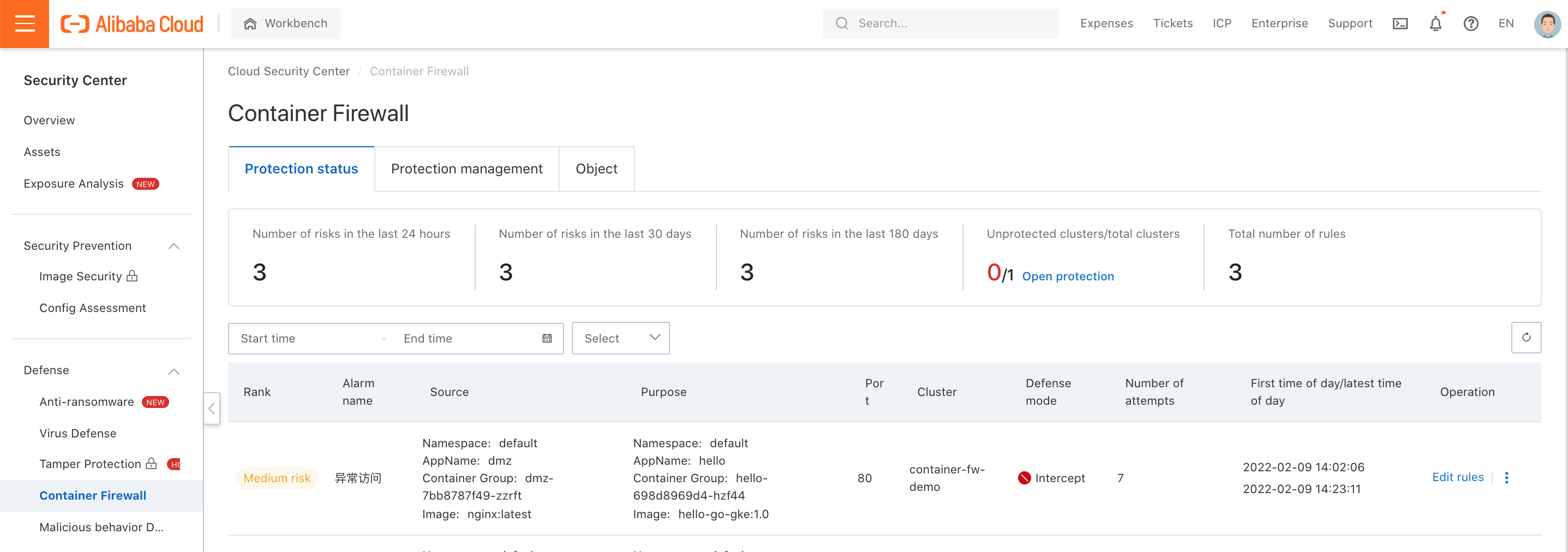
5. The alarm shows the Container Firewall should change from Alert to Intercept:
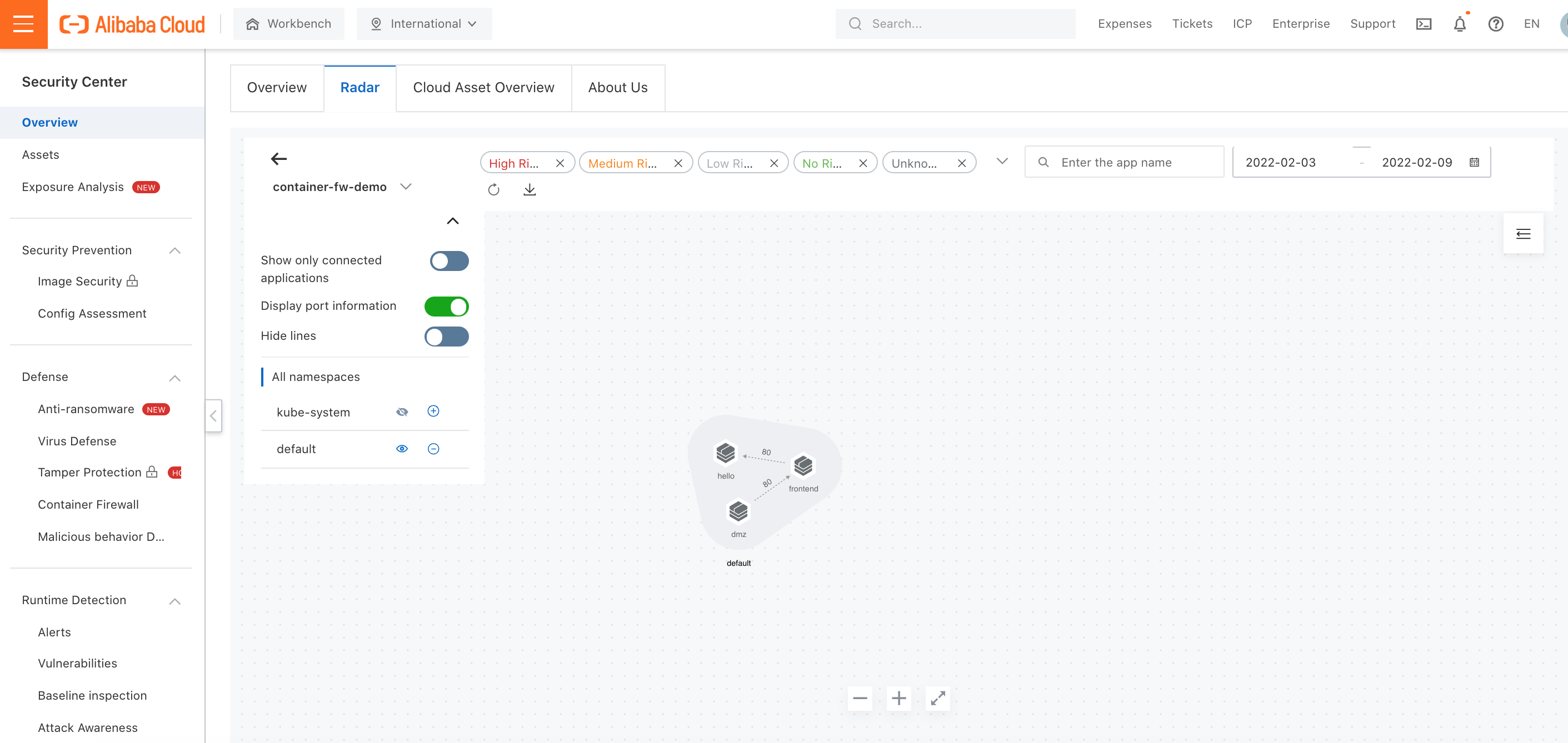
6. You can also view the container network flow between the three services on the Radar page:
What Future AML Compliance Requires: A Technology Perspective

1,353 posts | 478 followers
FollowAlibaba Cloud Indonesia - December 6, 2023
OpenAnolis - January 24, 2024
Alipay Technology - May 14, 2020
Xi Ning Wang(王夕宁) - August 6, 2020
Alibaba Cloud Community - October 17, 2025
Xi Ning Wang(王夕宁) - December 16, 2020

1,353 posts | 478 followers
Follow Microservices Engine (MSE)
Microservices Engine (MSE)
MSE provides a fully managed registration and configuration center, and gateway and microservices governance capabilities.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Apsara Stack
Apsara Stack
Apsara Stack is a full-stack cloud solution created by Alibaba Cloud for medium- and large-size enterprise-class customers.
Learn MoreMore Posts by Alibaba Cloud Community