By Wang Xining
This is the third edition in the ASM Extended Capabilities series, a collection of articles that describes some extended capabilities of Alibaba Cloud Service Mesh (ASM).
OPA, a CNCF-managed incubation project, is a policy engine that implements fine-grained access control for applications. For example, you can use OPA for cross-microservice authorization.
As shown in the following figure, as a common policy engine, you may deploy OPA as an independent service with microservices. To protect applications, each request to microservices must be authorized before being processed. To check whether a request is authorized, microservices call OPA APIs.
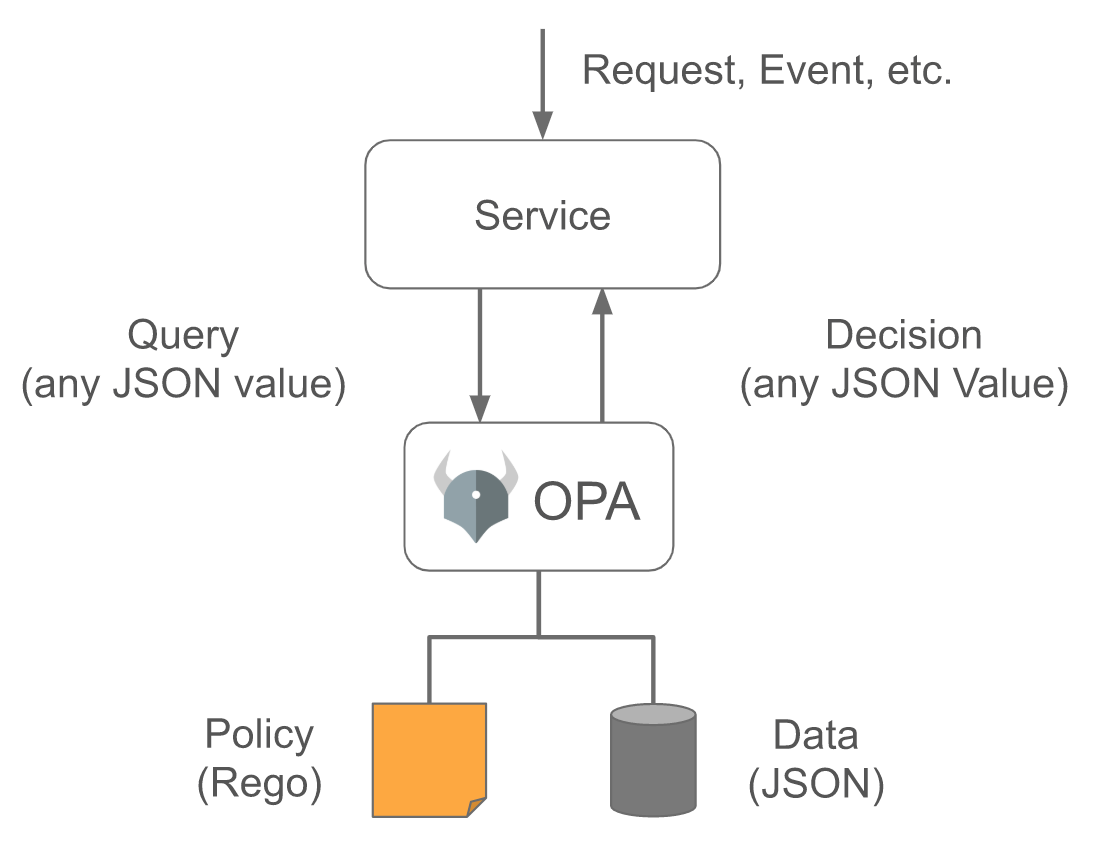
ASM integrates OPA to implement fine-grained access control for the applications. For example, you can use OPA for cross-microservice authorization. After OPA is enabled, just like the Istio Envoy proxy container, the OPA container will also be injected to the business pod. Then, OPA helps to define access control policies in ASM to provide the out-of-the-box capability for distributed application developers and help them quickly define use policies and improve the development efficiency.
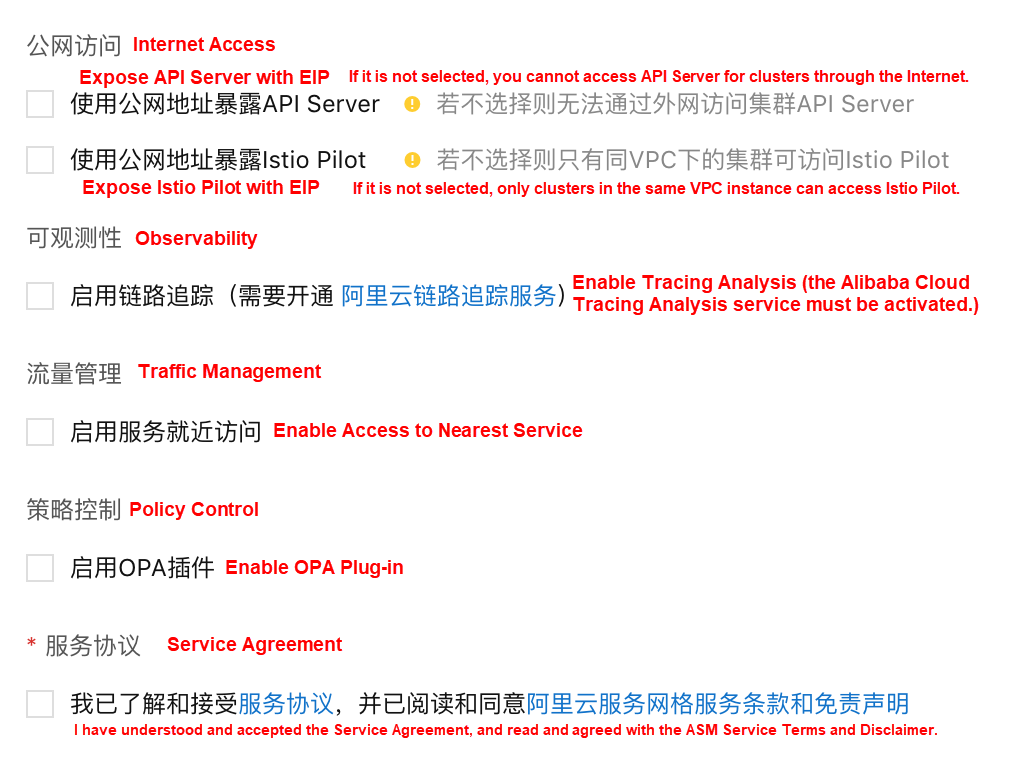
As shown in the figure, it allows determining whether to enable the OPA plug-in while creating an ASM instance.
If you did not select Enable OPA Plug-in while creating an ASM instance, use the following method to enable the OPA plug-in.
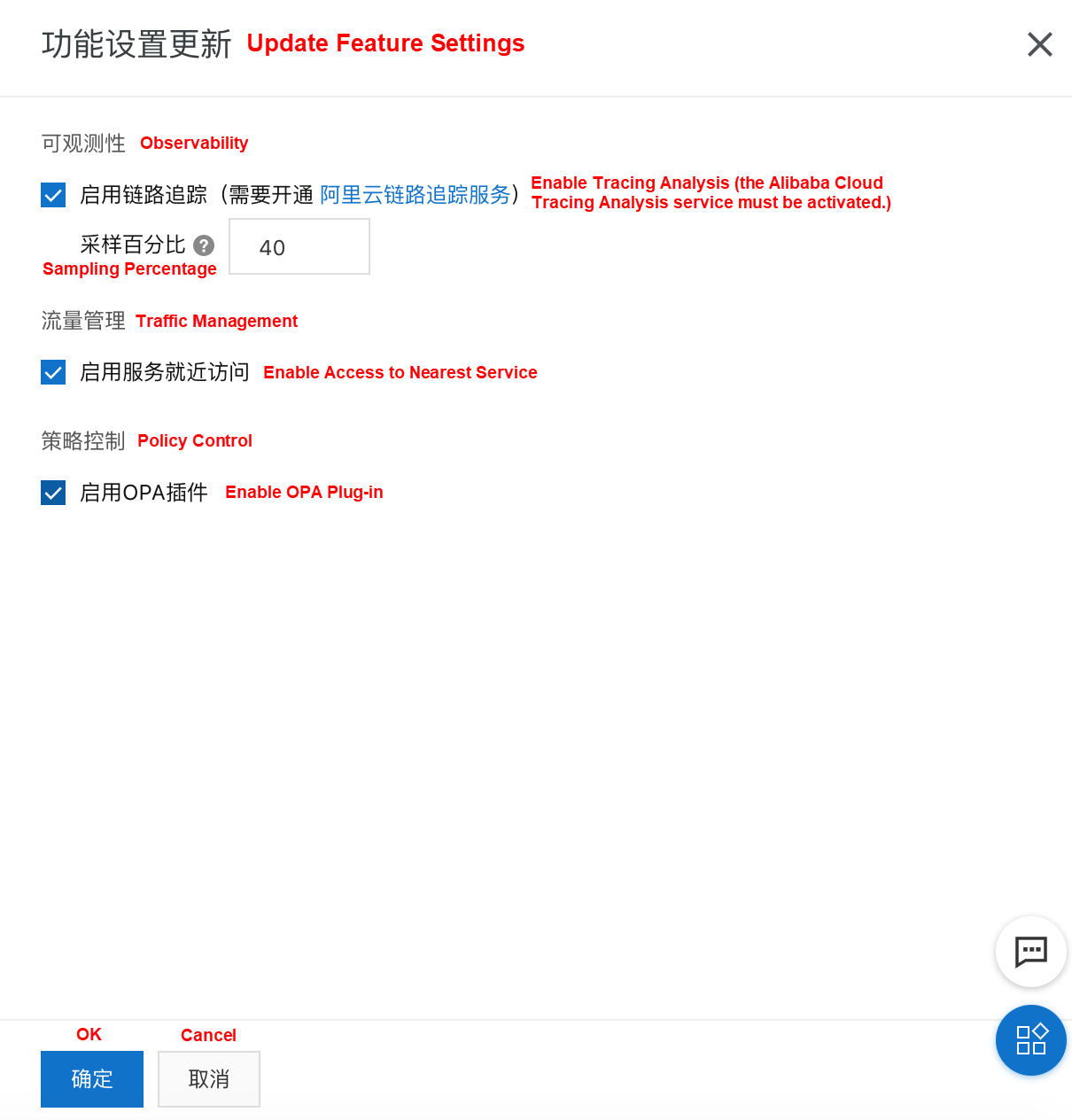
Note: Before deploying the business pod, ensure configuring the OPA configuration file and policy configuration item Configmap. The following sections describe how to deploy the OPA configuration and policy.
Deploy the OPA configuration file using kubectl to connect to the ACK cluster added to the ASM instance and run the following command:
kubectl apply -n {Actual namespace} -f - <<EOF
apiVersion: v1
kind: ConfigMap
metadata:
name: opa-istio-config
data:
config.yaml: |
plugins:
envoy_ext_authz_grpc:
addr: :9191
path: istio/authz/allow
EOF ASM currently supports OPA policies defined by Rego. In the future, it will additionally support WebAssembly-based OPA extended capabilities.
Use kubectl to connect to the ACK cluster added to the ASM instance, replace the policy definition with the actual policy definition, and run the following command:
kubectl apply -n {Actual namespace} -f - <<EOF
apiVersion: v1
kind: ConfigMap
metadata:
name: opa-policy
data:
policy.rego: | ### The following is a sample policy definition, which must be replaced by the actual one.
package istio.authz
import input.attributes.request.http as http_request
default allow = false
allow {
roles_for_user[r]
required_roles[r]
}
roles_for_user[r] {
r := user_roles[user_name][_]
}
required_roles[r] {
perm := role_perms[r][_]
perm.method = http_request.method
perm.path = http_request.path
}
user_name = parsed {
[_, encoded] := split(http_request.headers.authorization, " ")
[parsed, _] := split(base64url.decode(encoded), ":")
}
user_roles = {
"guest1": ["guest"],
"admin1": ["admin"]
}
role_perms = {
"guest": [
{"method": "GET", "path": "/productpage"},
],
"admin": [
{"method": "GET", "path": "/productpage"},
{"method": "GET", "path": "/api/v1/products"},
],
}
EOF Deploy the sample application to the ASM instance by referring to Deploy Applications to an ASM Instance and define the corresponding Istio virtual services and ingress gateway. For more information, see Manage Istio Resource Definitions.
The preceding policy restricts access to the Bookinfo application and is defined as follows:
/productpage but not /v1/api/products./productpage and /v1/api/products.curl -i --user guest1:password http:// {IP address of the ingress gateway service}/productpage
HTTP/1.1 200 OK
......
curl -i --user guest1: password http://{IP address of the ingress gateway service}/api/v1/products
HTTP/1.1 403 Forbidden
......
curl -i --user admin1:password http://{IP address of the ingress gateway service}/productpage
HTTP/1.1 200 OK
......
curl -i --user admin1: password http://{IP address of the ingress gateway service}/api/v1/products
HTTP/1.1 200 OK
......ASM Extended Capabilities 2 - Customize External Authorization in ASM

56 posts | 8 followers
FollowAlibaba Cloud Native - September 8, 2022
Alibaba Cloud Native - November 3, 2022
Xi Ning Wang(王夕宁) - June 10, 2020
Xi Ning Wang(王夕宁) - July 21, 2023
Alibaba Cloud Community - May 19, 2022
Xi Ning Wang(王夕宁) - July 28, 2020

56 posts | 8 followers
Follow Cloud-Native Applications Management Solution
Cloud-Native Applications Management Solution
Accelerate and secure the development, deployment, and management of containerized applications cost-effectively.
Learn More Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Microservices Engine (MSE)
Microservices Engine (MSE)
MSE provides a fully managed registration and configuration center, and gateway and microservices governance capabilities.
Learn MoreMore Posts by Xi Ning Wang(王夕宁)