By Xiao Yang (Ruanbu)
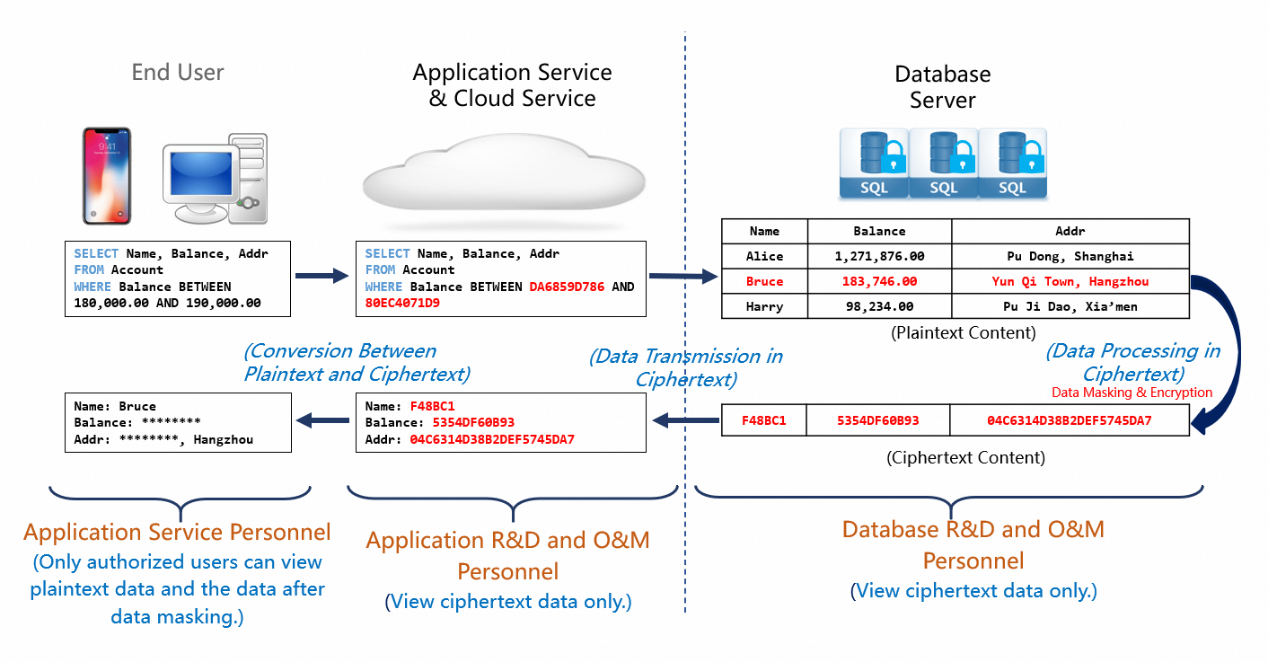
The always-confidential database feature uses confidential computing to support all database operations, such as transactions, queries, and analysis, and encrypts the query results before they are returned. The always-confidential database feature ensures that data is processed inside a secure enclave such as an application and a database but remains in ciphertext outside the enclave. This prevents cloud platform providers, unauthorized users, and management personnel such as database administrators (DBAs) from accessing your plaintext data. This also prevents developers and O&M personnel from stealing your data. The always-confidential database feature defends against external and internal threats in an efficient manner, protects your data throughout the lifecycle, and helps you privatize your cloud data.
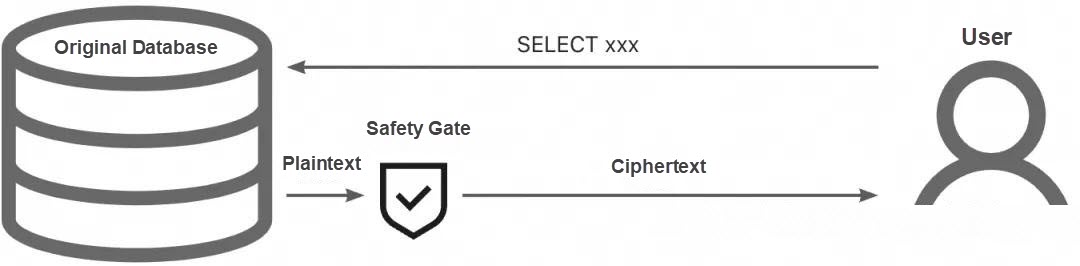
The always-confidential database itself encrypts data at the field level. From the perspective of data content, the network packet completely conforms to the communication protocol of MySQL itself, except that the data content itself is replaced, as shown in the following figure.
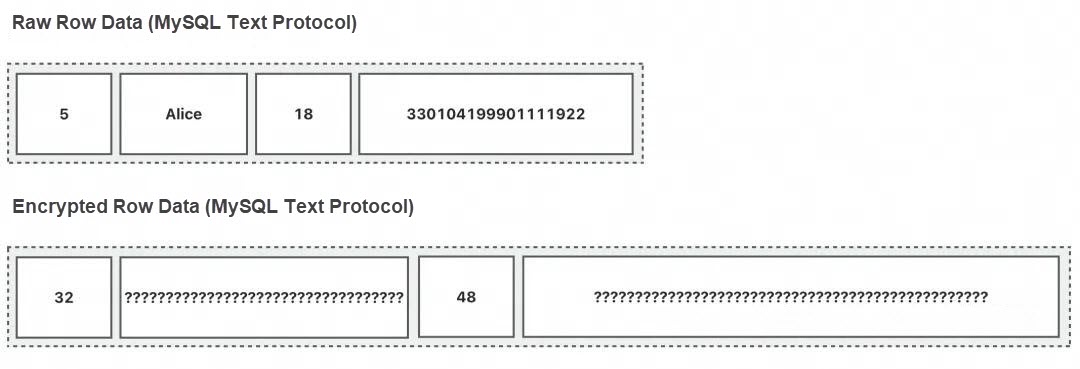
Always-confidential Database Communication Protocol
"In MySQL text communication protocol, the data of each field is stored in the form of strings, where each string is encoded in the form of length plus content. Following this principle, we organize the ciphertext in this format when returning data. We follow the MySQL communication protocol to make the always-confidential database compatible with all existing database clients in the industry. At the same time, we enable these clients to display ciphertext during queries by selectively encrypting data."
Note: MySQL has two communication mechanisms: text protocol and binary protocol. This article only selects the first one as an example.
Our client project alibabacloud-encdb-mysql-go-client is now open source. The client itself supports all SQL statements and the two MySQL communication protocols with standard Go interfaces. Therefore, you can connect to frameworks such as Gorm and Gin without business transformation.
Similar to how Java created JDBC to allow applications to connect to different databases with the same interface, GoLang created the database/sql/driver series of common interfaces. Different database drivers only need to implement a unified Driver and its derived Conn, Stmt, and Rows types, so that applications can call them with a unified interface. The MySQL community driver is used by countless users in this way. Look at the following figure. In essence, the application side calls the Next interface of the Rows type to obtain data.
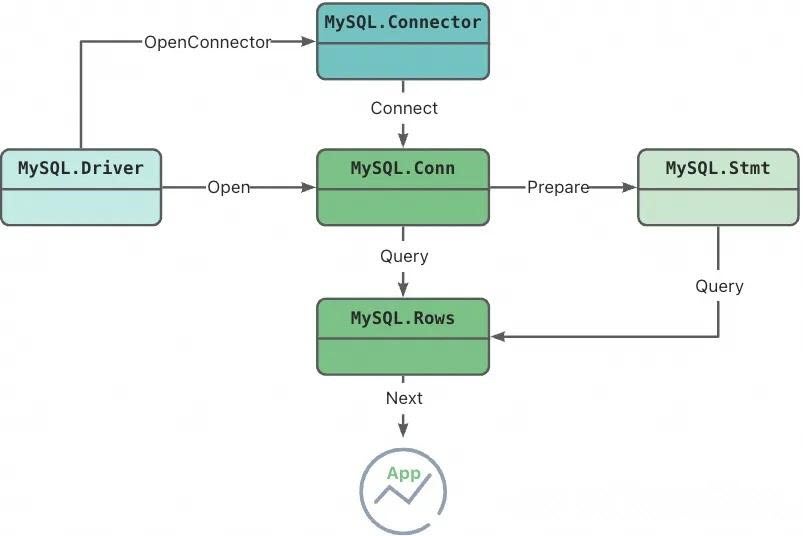
Community MySQL Go Driver UML Diagram
"Looking at the Go driver code of our always-confidential database, we can clearly see that the Driver, Conn, and other types we implemented actually have a corresponding community implementation class as a member."
driver.go file
// Driver implementation: Contains the MySQL implementation class
type EncMySQLDriver struct {
mysqlDriver *mysql.MySQLDriver
}"We implement most of the standard interfaces using these internal community implementation classes. For example, for the Conn.Begin interface required by the community, we directly call the function of the same name of the internal community class member."
connection.go file
func (c *encmysqlConn) Begin() (driver.Tx, error) {
return c.conn.Begin()
}"This design allows us to focus on the encryption and decryption processing itself without caring about MySQL's connection, transaction, SQL, and other mechanisms. As mentioned before, our always-confidential database fully complies with the MySQL communication protocol. Therefore, within our client, we can use the community driver to call the Rows.Next interface to directly read the ciphertext content. What we need to do is to parse the ciphertext in our Rows.Next interface and return the plaintext to the application side."
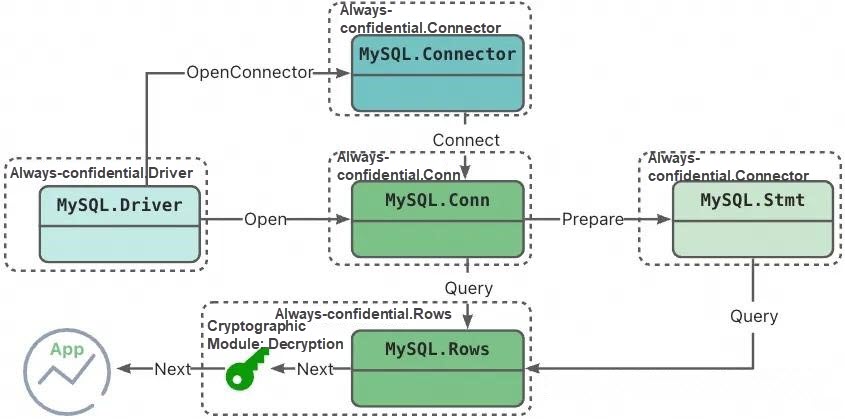
Always-confidential MySQL Go client UML diagram
"For the application side, you do not need to worry about the underlying driver implementation, but introduce our open source package."
Obtain the always-confidential mysql go client
go get github.com/aliyun/alibabacloud-encdb-mysql-go-client@latest"Referring to our README.md, you will soon be able to run a demo. Since we have implemented the standard interface of Go language, the client itself can connect to GoLang common Web frameworks such as Gorm and Gin with one click, whose stability and usability have been verified by customers."
As a cloud service provider, when we provide security products to users, the spirit of open source, transparency, and openness can enhance users' trust in us. By reading our open-source code, users can be more confident about the security, reliability, and stability of our products.
In addition, in the Go world, closed-source projects cannot be directly exposed through Go's package management mechanism. Previously, the always-confidential database placed the compressed package on the document interface to output data to customers, which increased the complexity of the customer integration package and the difficulty of deploying online businesses. For the value of the customer first, we finally chose open source.
Best Practices for Migrating SQL Server Instance-Level Databases to the Cloud
Core Technology of PolarDB-X Storage Engine | Lizard B+tree Optimization
ApsaraDB - January 12, 2023
Alibaba Cloud Community - September 2, 2025
Alibaba Clouder - April 26, 2019
Balaban - March 17, 2021
ApsaraDB - July 3, 2019
Neel_Shah - August 1, 2025
 PolarDB for MySQL
PolarDB for MySQL
Alibaba Cloud PolarDB for MySQL is a cloud-native relational database service 100% compatible with MySQL.
Learn More Time Series Database (TSDB)
Time Series Database (TSDB)
TSDB is a stable, reliable, and cost-effective online high-performance time series database service.
Learn More AnalyticDB for MySQL
AnalyticDB for MySQL
AnalyticDB for MySQL is a real-time data warehousing service that can process petabytes of data with high concurrency and low latency.
Learn More Cloud Hardware Security Module (HSM)
Cloud Hardware Security Module (HSM)
Industry-standard hardware security modules (HSMs) deployed on Alibaba Cloud.
Learn MoreMore Posts by ApsaraDB