This topic describes frequently asked questions about VPN gateways.
Quick Links to FAQs
Product Inquiries
What are non-cross-border connections and cross-border connections?
Can ECS instances in other zones of a VPC forward traffic through a VPN gateway instance?
Why does a VPN connection's bandwidth not meet the purchased bandwidth specifications?
Can traffic between a VPC and a public IP address be encrypted by a VPN gateway?
IPsec-VPN Features
What are the prerequisites for a data center to connect to a VPC via IPsec-VPN?
Which on-premises gateway devices can connect to Alibaba Cloud VPN gateways?
Can I configure multiple peer CIDR blocks in one IPsec connection?
How do I select an IKE version when configuring an IPsec-VPN connection?
SSL-VPN Features
What are non-cross-border connections and cross-border connections?
Alibaba Cloud VPN Gateway provides services in compliance with policies and regulations in the Chinese mainland. You can only use VPN Gateway to establish non-cross-border connections. For more information about accessing cross-border resources using a VPN connection, see How do I use VPN connections to access cross-border resources?.
Non-cross-border Connections
When you establish an IPsec-VPN connection, it is considered non-cross-border if the regions of the data center and the peer resource meet either of the following conditions:
The data center is in a region in the Chinese mainland, and the peer resource is in an Alibaba Cloud region in the Chinese mainland.
The data center is outside the Chinese mainland, and the peer resource is in an Alibaba Cloud region outside the Chinese mainland.
When you establish an SSL-VPN connection, it is considered non-cross-border if the regions of the client and the peer resource meet either of the following conditions:
The client is in the Chinese mainland, and the peer resource is in an Alibaba Cloud region in the Chinese mainland.
The client is outside the Chinese mainland, and the peer resource is in an Alibaba Cloud region outside the Chinese mainland.
Example 1 | Example 2 |
 |  |
Cross-border Connections
When you establish an IPsec-VPN connection, it is considered cross-border if the regions of the data center and the peer resource meet either of the following conditions:
The data center is in the Chinese mainland, and the peer resource is in an Alibaba Cloud region outside the Chinese mainland.
The data center is outside the Chinese mainland, and the peer resource is in an Alibaba Cloud region in the Chinese mainland.
When you establish an SSL-VPN connection, it is considered cross-border if the regions of the client and the peer resource meet either of the following conditions:
The client is in the Chinese mainland, and the peer resource is in an Alibaba Cloud region outside the Chinese mainland.
The client is outside the Chinese mainland, and the peer resource is in an Alibaba Cloud region in the Chinese mainland.
Example 1 | Example 2 |
 |  |
Regions in the Chinese mainland and regions outside the Chinese mainland
Region classification | Included regions |
The Chinese mainland | China (Qingdao), China (Beijing), China (Zhangjiakou), China (Hohhot), China (Ulanqab), China (Shenzhen), China (Heyuan), China (Guangzhou), China (Hangzhou), China (Shanghai), China (Nanjing - Local Region), China (Chengdu) |
Outside the Chinese mainland | China (Hong Kong), Singapore, Malaysia (Kuala Lumpur), Japan (Tokyo), Indonesia (Jakarta), Philippines (Manila), South Korea (Seoul), Thailand (Bangkok), Germany (Frankfurt), UK (London), UAE (Dubai), US (Silicon Valley), US (Virginia), SAU (Riyadh - Partner Region)), Mexico |
How do I use VPN connections to access cross-border resources?
To access cross-border resources using a VPN connection, use the transit router product. Transit routers provide low-latency, high-speed network transmission, enabling private network communication channels between resources across regions, including cross-border connections, and facilitating arbitrary interconnection between resources in different regions.
Network topology example:
IPsec-VPN | SSL-VPN |
 |  |
Can I use VPN gateways to access the Internet?
No.
VPN gateways only provide private network access to VPCs, but not Internet access.
What are the prerequisites for a data center to connect to a VPC via IPsec-VPN?
The gateway device at the local site must support the IKEv1 and IKEv2 protocols.
IPsec-VPN supports the IKEv1 and IKEv2 protocols. Any gateway device that supports either the IKEv1 or IKEv2 protocol can connect to Alibaba Cloud VPN gateways. For more information, see How do I choose the IKE version when I configure an IPsec-VPN connection?.
The gateway device at the local site must have a static public IP address.
The CIDR blocks of the data center and the VPC must not overlap.
For more information about how to connect a data center to a VPC using an IPsec-VPN connection, see Connect a VPC to a data center in dual-tunnel mode.
Which on-premises gateway devices can connect to Alibaba Cloud VPN gateways?
Alibaba Cloud VPN gateways support the standard IKEv1 and IKEv2 protocols. Any gateway device that supports either the IKEv1 or IKEv2 protocol can connect to Alibaba Cloud VPN gateways. For example, gateway devices from H3C, Hillstone, Sangfor, Cisco ASA, Juniper, SonicWall, Nokia, IBM, and Ixia can connect to Alibaba Cloud VPN gateways. For more information, see Configure local gateways.
Can VPCs across regions communicate through VPN gateways?
Yes.
For more information, see Enable communication between two VPCs using an IPsec-VPN connection in dual-tunnel mode.
If you create an IPsec-VPN connection between VPCs in different regions, Internet quality affects the connection quality. We recommend using Cloud Enterprise Network (CEN) to connect VPCs in different regions. For more information, see Connect VPCs across accounts.
Does traffic between VPCs flow through the Internet?
When using VPN gateways to enable communication between VPCs:
If two VPCs are in the same region, traffic flows only through the Alibaba Cloud network, and not the Internet.
If two VPCs are in different regions, traffic flows through the Internet.
What are the differences between an IPsec server and an SSL server?
Item | IPsec server | SSL server |
Use scenario | Provides end-to-site connections. | Provides end-to-site connections. |
Client mode | Allows mobile clients that run iOS to establish IPsec-VPN connections to Alibaba Cloud. | Allows mobile clients that run Android and computers to establish SSL-VPN connections to Alibaba Cloud. |
Connection mode | Allows mobile clients that run iOS to establish IPsec-VPN connections to Alibaba Cloud by using the built-in VPN feature. | Allows mobile clients that run Android and computers to establish SSL-VPN connections to Alibaba Cloud by using OpenVPN. |
Encryption methods | IPsec | SSL certificates |
Can I configure multiple peer CIDR blocks in one IPsec connection?
Supported.
Before you configure multiple peer CIDR blocks, we recommend that you review the proposals for configuring multiple CIDR blocks. For more information, see Configuration suggestions and FAQ about enabling communication among CIDR blocks.
How many IPsec connections can each VPN gateway establish?
Each VPN gateway supports up to 10 IPsec-VPN connections by default. You can adjust this quota in the Alibaba Cloud Management Console. For more information, see Manage IPsec-VPN quotas.
How do I configure network ACL rules for a VPN gateway?
VPN Gateway Type | Configuration Rules |
IPsec-VPN | Configure rules in the outbound and inbound directions of the network ACL to allow the following CIDR blocks and IP addresses. This ensures the VPN gateway can establish IPsec-VPN connections:
|
SSL-VPN | Configure rules in the outbound and inbound directions of the network ACL to allow the following CIDR blocks and IP addresses, and open the SSL-VPN port. This ensures the VPN gateway can establish SSL-VPN connections:
|
Can I upgrade or downgrade a VPN gateway's configuration?
Yes.
To upgrade or downgrade the bandwidth of a VPN gateway, see Upgrade or downgrade a VPN gateway.
To upgrade or downgrade the quota on SSL-VPN connections for your VPN Gateway, see Modify the Maximum Number of Concurrent SSL-VPN Connections.
To enable the IPsec-VPN feature or the SSL-VPN feature for a VPN Gateway, see Enable IPsec-VPN and Enable the SSL-VPN feature.
Does VPN Gateway support viewing client connection information for SSL-VPN connections?
This is supported.
For specific operations, see View the information about an SSL client's connection.
If your VPN gateway was created after December 10, 2022, you can view the connection information about SSL clients by default.
If your VPN gateway associated with an SSL server was created before December 10, 2022, you cannot view the connection information about SSL clients by default. To view the information, you must upgrade the VPN gateway.
Can VPN gateway instances purchased before the SSL-VPN release use the SSL-VPN feature?
No.
To use this feature, you can upgrade the VPN Gateway to the latest version. For detailed instructions, see Upgrade a VPN Gateway.
How do I select an IKE version when configuring an IPsec-VPN connection?
When configuring an IPsec-VPN connection, select the IKE version based on the peer gateway device's support and whether multi-CIDR block communication is required.
Communication among multiple CIDR blocks is established if you specify multiple Local Network or Remote Network CIDR blocks when you configure an IPsec-VPN connection.
IKE Version Support for IPsec Connection Peer Gateway Devices | Is Multi-CIDR Block Communication Required? | Configuration Solution Description |
IKEv1 only | Yes |
|
No | Both the IPsec connection and the peer gateway device use IKEv1. | |
IKEv2 only | Yes |
|
No | Both the IPsec connection and the peer gateway device use IKEv2. | |
Supports both IKEv1 and IKEv2 | Yes |
|
No | Both the IPsec connection and the peer gateway device should use IKEv2. Compared to IKEv1, IKEv2 simplifies the SA negotiation process and offers better support for multi-CIDR block scenarios. Therefore, we recommend using IKEv2. |
After a data center's IP address is translated by NAT, how does it establish an IPsec-VPN connection with an Alibaba Cloud VPN gateway?
For example, if a data center plans to use 42.XX.XX.1 to establish an IPsec-VPN connection with an Alibaba Cloud VPN gateway, but the data center uses SNAT, traffic from 42.XX.XX.1 will be translated to 47.XX.XX.21. In this case, when you create a customer gateway instance in the Alibaba Cloud VPN Gateway Management Console, enter 47.XX.XX.21 as the customer gateway instance's IP address. This allows the Alibaba Cloud VPN gateway to establish an IPsec-VPN connection with the data center.
We recommend that the data center use the default IPsec protocol ports (500 and 4500) to establish IPsec-VPN connections with the VPN gateway. Do not convert port numbers.
On the Alibaba Cloud side, if a public VPN gateway is associated with a VPC instance that also has NAT Gateway enabled, the public VPN gateway instance's IP address remains unchanged and is not translated by NAT Gateway.
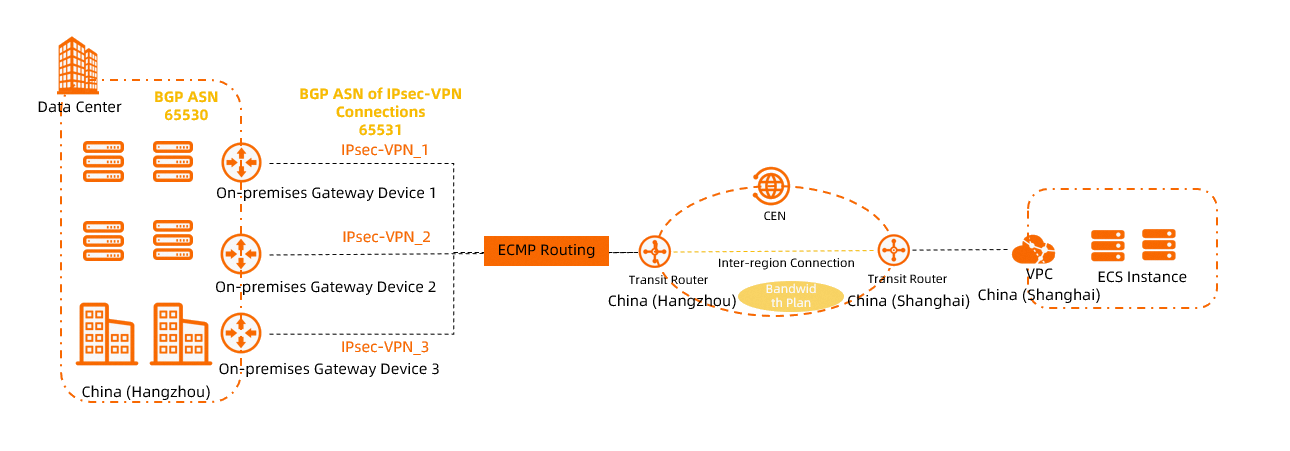
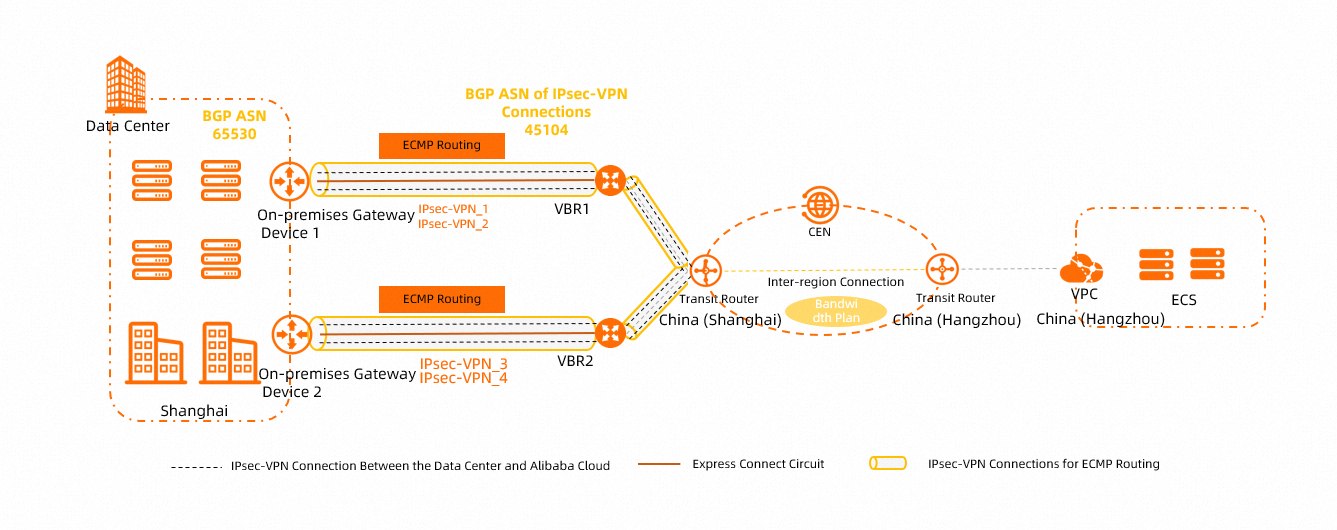
How do I increase the bandwidth of an IPsec-VPN connection?
When an IPsec connection is bound to a VPN gateway instance, the maximum bandwidth of the VPN gateway instance is 1,000 Mbps (the maximum bandwidth is 500 Mbps in some regions). To increase the IPsec-VPN connection's bandwidth, we recommend that you bind the IPsec connection to a transit router instance to connect your data center to Alibaba Cloud. The transit router enables network communication between your data center and the VPC.
After an IPsec connection is associated with a transit router, the maximum bandwidth of the IPsec-VPN connection is 1,000 Mbit/s. To increase the maximum bandwidth, you can establish multiple IPsec-VPN connections between the transit router and your data center. This way, network traffic is transmitted between your data center and Alibaba Cloud over multiple IPsec-VPN connections, as shown in the following figure. For more information, see Create multiple IPsec-VPN connections over the Internet for load balancing and Create multiple private IPsec-VPN connections to implement load balancing.
Scenario where the IPsec connection's network type is public:
Scenario where the IPsec connection's network type is private:
Can ECS instances in other zones of a VPC forward traffic through a VPN gateway instance?
Yes.
When you create a VPN gateway instance, specify a vSwitch. The system deploys the VPN gateway in the zone where the specified vSwitch resides. After creation, the VPN gateway instance can forward traffic for ECS instances in all zones of the VPC instance.
You may need to add routing configurations as needed to enable the VPN gateway instance to forward ECS instance traffic. For example, if a vSwitch in a zone is associated with the VPC instance's custom route table, you must add a custom route pointing to the VPN gateway instance in that custom route table.
What do I do if the system reports a route overlap error when adding a route to a VPN gateway instance?
When you add a route to a VPN gateway instance, system errors typically occur for two reasons:
The destination CIDR block of the route you add is the same as a route in the VPC instance. Check the routing configuration in the VPC instance's route table to resolve the route conflict.
The route you add conflicts with a route in the VPN gateway instance. Check the routing configurations in the VPN gateway instance's policy-based route table and destination-based route table to resolve the route conflict.
If you add a destination-based route whose destination CIDR block and next hop are the same as an existing destination-based route in the VPN gateway instance, a route conflict occurs.
If you add a policy-based route whose source CIDR block, destination CIDR block, and next hop are the same as an existing policy-based route in the VPN gateway instance, a route conflict occurs.
Why does a VPN connection's bandwidth not meet the purchased bandwidth specifications?
After you purchase a VPN gateway, it provides the purchased bandwidth capacity. However, the following factors can affect your bandwidth experience during traffic transmission:
The functions of the device associated with the customer gateway instance, connection capacity, average packet size, and protocols used (TCP and UDP).
Network latency between the customer gateway instance's associated device and the VPN gateway.
NoteIf you purchase a public network type VPN gateway instance or use a public network type IPsec connection, public bandwidth capacity and public network latency may affect your bandwidth experience.
If you want to test the bandwidth of your VPN gateway, we recommend using iPerf3. The rate of transferring files by running commands, such as scp, ftp, and cp commands, cannot reflect the actual bandwidth due to the impact of disk read and write speeds. For more information about how to use iPerf3, see Use iPerf3 to test the bandwidth of an Express Connect circuit.
If you require higher transmission quality, we recommend using the CEN product.
Can traffic between a VPC and a public IP address be encrypted by a VPN gateway?
Yes.
If your client or data center is connected to a VPC using a VPN gateway and needs to access resources in the VPC using a public IP address, you must perform the following operations:
Add the public IP address's CIDR block to the VPN Gateway:
If you use an IPsec-VPN connection, add the public CIDR block to the Remote Network of the IPsec-VPN connection.
If you use an SSL-VPN connection, add the public CIDR block to the Client CIDR Block of the SSL server.
You must set the public CIDR block as a user CIDR block for the virtual private cloud (VPC). This ensures that the VPC can access the public CIDR block. For more information about user CIDR blocks, see VPC FAQ and VPC FAQ.
What do I do if the number of routes exceeds the limit?
If the number of routes exceeds the limit when using policy-based routes, destination-based routes, or BGP dynamic routing, preventing you from adding new routes or preventing IPsec connections from learning BGP routes, you can resolve the issue using these two methods:
Increase the route quota.
You can increase the quota of policy-based routes, destination-based routes, or BGP routes. For more information, see IPsec-VPN quotas.
Configure an aggregated route.
Aggregate multiple configured routes into a single route without affecting your business.
For example, if you configured three destination-based routes with destination CIDR blocks 10.10.1.0/24, 10.10.2.0/24, and 10.10.3.0/24, all pointing to the same IPsec connection (e.g., IPsec connection 1), you can add a new destination-based route with destination CIDR block 10.10.0.0/22 and a next hop pointing to IPsec connection 1. Then, delete the original three destination-based routes to save destination route quota.
If VPN bandwidth is full or utilization is high, how do I find the top source and destination IP addresses?
You can enable VPC flow logs to collect and analyze VPN Elastic Network Interface (ENI) traffic. For details, see Query and analyze traffic transmitted by VPN gateway instances using ENI flow logs.
What type of public IP address does a VPN gateway use?
A VPN gateway's public IP address type is Multi-line BGP . This type connects to multiple ISP lines and automatically selects the optimal path, providing users with a fast and stable access experience.