After you add a service to an Anti-DDoS Pro or Anti-DDoS Premium instance, attack traffic is redirected to the instance. This prevents service unavailability during volumetric DDoS attacks and ensures that your origin server remains stable and reliable. This topic describes best practices for onboarding configurations and protection policies to help you protect your services in various scenarios.
Overview of the onboarding process
Scenario | Onboarding process |
Onboard a service in normal scenarios | |
Onboard a service in an emergency | Before you follow the onboarding process for normal scenarios, read Precautions for emergency onboarding. |
Step 1: Analyze your service
First, perform a comprehensive analysis of the service that you want to protect with Anti-DDoS Pro or Anti-DDoS Premium. This helps you understand the current status and data of your service. The information provides guidance for using the protection features of Anti-DDoS Pro and Anti-DDoS Premium.
Item | Description | Suggestion |
Website and service information | ||
Daily peak traffic of the website or application, including bandwidth in Mbps and queries per second (QPS) | This helps you determine when risks may occur. | Use this information to select the Clean Bandwidth and Clean QPS specifications for your Anti-DDoS Pro or Anti-DDoS Premium instance. |
The main user groups of your service, such as the primary locations of your users | This helps you determine the source of illegitimate attacks. | You can use this information to configure the Location Blacklist policy after you add the service. For more information, see Configure a location blacklist for a domain name. |
Whether your service uses a client/server (C/S) architecture | If a C/S architecture is used, determine whether you have app clients, Windows clients, Linux clients, clients for code callbacks, or clients in other environments. | None. |
Whether the origin server is deployed in a region outside the Chinese mainland | This helps you determine whether the configured instance fits the optimal network architecture. | If the origin server is deployed outside the Chinese mainland, you must purchase an Anti-DDoS Pro or Anti-DDoS Premium (Outside Chinese Mainland) instance. For more information, see What is Anti-DDoS Pro and Anti-DDoS Premium? |
The operating system of the origin server, such as Linux or Windows, and the web service middleware used, such as Apache, Nginx, or IIS | This helps you determine whether an access control policy is configured for the origin server. This prevents the origin server from blocking traffic that is forwarded from the back-to-origin IP addresses of Anti-DDoS Pro and Anti-DDoS Premium. | If a policy is configured, you must add the back-to-origin IP addresses of Anti-DDoS Pro and Anti-DDoS Premium to the whitelist of the origin server. For more information, see Add the back-to-origin IP addresses of Anti-DDoS Pro or Anti-DDoS Premium to a whitelist. |
Whether the service needs to support the IPv6 protocol | None. | If your service needs to support the IPv6 protocol, you must use Anti-DDoS Origin. For more information, see What is Anti-DDoS Origin? |
The protocol type that is used by the service | None. | This information is required to select a protocol when you add website information to your Anti-DDoS Pro or Anti-DDoS Premium instance. |
Service ports | None. | This helps you determine whether the service ports of the origin server are supported by Anti-DDoS Pro and Anti-DDoS Premium. For more information, see Custom server ports. |
Whether the request header (HTTP Header) contains custom fields and whether the server has a corresponding verification mechanism | This helps you determine whether Anti-DDoS Pro or Anti-DDoS Premium affects custom fields and causes verification failures on the server. | None. |
Whether the service has a mechanism to obtain and verify originating IP addresses | After you add the service to Anti-DDoS Pro or Anti-DDoS Premium, the originating IP addresses change. You must confirm whether to adjust the configuration for obtaining originating IP addresses on the origin server to prevent service interruptions. | For more information, see Obtain the originating IP addresses of requests after you configure Anti-DDoS Pro or Anti-DDoS Premium. |
Whether the service uses TLS 1.0 or a weak cipher suite | This helps you determine whether the cipher suite that is used by your service is supported. | After you add the service, you can set the TLS security policy as needed. For more information, see Customize the TLS security policy for an HTTPS certificate of a server. |
(For HTTPS services) Whether the server uses mutual authentication | None. | If you require mutual authentication, see Deploy HTTPS mutual authentication using Anti-DDoS Pro or Anti-DDoS Premium. |
(For HTTPS services) Whether the client supports the Server Name Indication (SNI) standard | None. | For domain names that support the HTTPS protocol, both the client and the server must support the SNI standard after the domain name is added to Anti-DDoS Pro or Anti-DDoS Premium. |
(For HTTPS services) Whether a session persistence mechanism exists | The default connection timeout period for HTTP and HTTPS in Anti-DDoS Pro and Anti-DDoS Premium is 120 seconds. | If your service has long-session requirements, such as for uploads or logons, you can use the Layer 7 cookie-based session persistence feature. |
Whether the service has empty connections | For example, a server may proactively send packets to prevent session interruption. In this case, adding the service to Anti-DDoS Pro or Anti-DDoS Premium may affect normal service traffic. | None. |
Service interaction process | This helps you understand the service interaction process and business logic to configure targeted protection policies. | None. |
Number of active users | This helps you determine the severity of emergency attack events and take low-risk emergency measures. | None. |
Service and attack information | ||
Service type and features, such as game, card game, website, or app services | This helps you analyze attack features during the attack and defense process. | None. |
Service traffic (inbound) | This helps you determine whether malicious traffic is included. For example, if the average daily access traffic is 100 Mbps, traffic that exceeds 100 Mbps may indicate an attack. | None. |
Service traffic (outbound) | This helps you determine whether an attack has occurred and serves as a reference for whether to expand the clean bandwidth. | None. |
Inbound traffic range and connection status for a single user or IP address | This helps you determine whether a throttling policy can be created for a single IP address. | For more information, see Set frequency control. |
User group properties | For example, individual users, users in internet cafes, or users who access the service through a proxy. | This helps you determine whether there is a risk of false positives caused by concentrated concurrent access from a single egress IP address. |
Whether the service has experienced volumetric attacks and the attack types | This helps you set targeted DDoS mitigation policies based on the types of historical attacks. | None. |
The peak throughput of attacks that the service has experienced | This helps you select the specifications of the Anti-DDoS Pro or Anti-DDoS Premium instance based on the peak attack throughput. | For more information, see Purchase an Anti-DDoS Pro or Anti-DDoS Premium instance. |
Whether the service has experienced CC attacks (HTTP Flood) | This helps you analyze historical attack features to configure preventive policies. | None. |
The peak QPS of CC attacks that the service has experienced | This helps you analyze historical attack features to configure preventive policies. | None. |
Whether the service provides a Web API service | None. | If a Web API service is provided, do not use the Emergency protection mode of Frequency Control. You must analyze API access features to configure custom CC attack protection policies and prevent normal API requests from being blocked. |
Whether a stress test has been completed for the service | This helps you evaluate the request processing performance of the origin server and determine whether a service exception is caused by an attack. | None. |
Step 2: Preparations
Before you add your service to Anti-DDoS Pro or Anti-DDoS Premium, you must test the service in a test environment. After the test is passed, you can add the service to the production environment.
Before you add a service to Anti-DDoS Pro or Anti-DDoS Premium, you must complete the preparations that are described in the following table.
Service type | Preparation |
Website services |
|
Non-website services |
|
Step 3: Add the service and configure protection
Onboard your service.
NoteIf your service is under attack before you add it to Anti-DDoS Pro or Anti-DDoS Premium, you must change the IP address of the origin server. Before you change the IP address, check whether the code of the client or app directly points to the origin IP address. If it does, you must update the client or app code before you change the origin IP address to prevent service interruptions. For more information, see Change the public IP address of an origin ECS instance.
Based on your business scenario and the Anti-DDoS Pro or Anti-DDoS Premium instance that you purchased, you can refer to the following onboarding guides to add your service:
Configure origin server protection.
To prevent attackers from bypassing Anti-DDoS Pro or Anti-DDoS Premium to directly attack the origin server, you must configure origin server protection. For more information, see Configure origin server protection.
Configure protection policies.
Website services
CC attack protection
When the service is normal: After you add the website service to Anti-DDoS Pro or Anti-DDoS Premium, let it run for a period, such as two or three days. Then, you can analyze the application log data, including URLs and the average access QPS from a single source IP address. Evaluate the request QPS from a single source IP address under normal conditions and configure a custom frequency control rule for throttling. This helps avoid a passive response after an attack occurs.
When a CC attack is in progress: You can view the Security Overview report in the Anti-DDoS Pro and Anti-DDoS Premium console to obtain parameters such as Top URLs by Request, IP addresses, source IP addresses, and User-agent. For more information, see Security Overview. You can create a custom frequency control rule based on the actual situation and observe the protection effect. For more information, see Custom frequency control rules.
(For website services) Intelligent protection
The Strict mode of the intelligent protection policy may cause false positives. Website services already have inherent protection against common Layer 4 attacks after they are added. Do not use the Strict mode of intelligent protection for website services. You can use the default Normal mode. For more information, see Set intelligent protection.
Enable full logs
You can enable the log analysis feature. For more information, see Quickly use the log analysis feature. When your service is under a Layer 7 attack, you can use the full logs feature to analyze attack behavior and create targeted protection policies.
NoteEnabling the log analysis service may incur additional fees. You must confirm the fees before you enable the service.
Non-website services
In most cases, after you add a non-website service to Anti-DDoS Pro or Anti-DDoS Premium, you can use the default protection configuration. After the service runs for a period, such as two or three days, you can adjust the mode of Layer 4 intelligent protection based on your service conditions. For more information, see Set Layer 4 intelligent protection. This can effectively improve the protection against Layer 4 CC attacks.
NoteIf your service is an API type or has concentrated access from a single IP address, such as from an office network egress, a single server IP address, or a high-frequency API calling service, do not enable the Strict mode of the intelligent protection policy for non-website services. If you must use the Strict protection mode, you must contact Alibaba Cloud technical support to confirm the situation before you enable it. This prevents service unavailability that is caused by false positives.
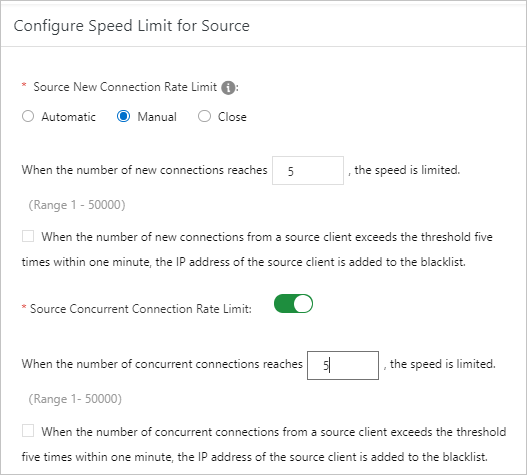
If you find that attack traffic is passed through to the origin server, you can enable the source and destination connection throttling policies in the DDoS mitigation policies. For more information, see Configure a single DDoS mitigation policy. If you are not completely clear about your service conditions, you can set both the maximum number of new connections from a source IP address and the maximum number of concurrent connections from a source IP address to 5. If you find false positives, you can adjust the values to relax the throttling policies.
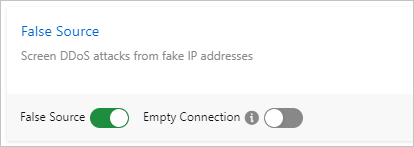
If your service has a scenario where the server proactively sends data packets, you must disable the Empty Connection protection policy to prevent the normal service from being affected. For more information, see Configure a single DDoS mitigation policy.
Perform local tests.
After you complete the preceding configurations for Anti-DDoS Pro or Anti-DDoS Premium, you must check the configuration accuracy and perform verification tests.
NoteYou can modify the local system hosts file to perform local tests.
Table 1. Configuration accuracy checklist
Number
Check item
Checklist For Onboarding Website Services (required)
1
Check whether the domain name in the onboarding configuration is correct.
2
Check whether the domain name has an ICP filing.
3
Check whether the protocol in the onboarding configuration is consistent with the actual protocol.
4
Check whether the port in the onboarding configuration is consistent with the actual service port.
5
Check whether the IP address specified for the origin server is the real server IP address, not the IP address of the Anti-DDoS Pro or Anti-DDoS Premium instance or another service.
6
Check whether the certificate information is correctly uploaded.
7
Check whether the certificate is valid. For example, the encryption algorithm may be non-compliant, or the certificate of another domain name may be uploaded by mistake.
8
Check whether the certificate chain is complete.
9
Check whether you understand the billing method of burstable protection for Anti-DDoS Pro or Anti-DDoS Premium (Chinese Mainland) instances.
10
Check whether the Websocket and Websockets protocols are enabled for the protocol type.
11
Check whether the Emergency and Strict modes of Frequency Control are enabled.
Checklist For Onboarding Non-website Services (required)
1
Check whether the service port can be accessed normally.
2
Check whether the protocol in the onboarding configuration is consistent with the actual protocol. Confirm that a UDP protocol rule is not mistakenly configured for a TCP protocol service.
3
Check whether the IP address specified for the origin server is the real server IP address, not the IP address of the Anti-DDoS Pro or Anti-DDoS Premium instance or another service.
4
Check whether you understand the billing method of burstable protection for Anti-DDoS Pro or Anti-DDoS Premium (Chinese Mainland) instances.
5
Check whether the Strict mode of Layer 4 intelligent protection is enabled.
Table 2. Service availability checklist
Number
Check item
1 (Required)
Test whether the service can be accessed normally.
2 (Required)
Test whether the session persistence feature for service logons works normally.
3 (Required)
(For website services) Observe the number of 4xx and 5xx response codes returned by the service to ensure that the back-to-origin IP addresses are not blocked.
4 (Required)
(For website services) For app services, test whether HTTPS link access is normal. Check for SNI issues.
5 (Recommended)
Check whether the backend server is configured to obtain the real source IP address for access.
6 (Recommended)
(For website services) Check whether origin server protection is configured to prevent attackers from bypassing Anti-DDoS Pro or Anti-DDoS Premium to directly attack the origin server.
7 (Required)
Test whether the port of the TCP service can be accessed normally.
Formally switch the service traffic.
After all required checks are passed, you can use a grayscale approach to modify the DNS records one by one. This switches the website service traffic to Anti-DDoS Pro or Anti-DDoS Premium and avoids service exceptions that are caused by batch operations. If an exception occurs during the traffic switch, you must quickly restore the DNS records.
NoteAfter you modify a DNS record, the change takes about 10 minutes to take effect.
After the real service traffic is switched, you must test the service again based on the preceding service availability checklist to ensure that the service runs normally.
Configure monitoring and alerts.
You can use CloudMonitor to monitor the domain names, ports, and origin server ports that are protected by Anti-DDoS Pro or Anti-DDoS Premium. For more information, see Configure alert rules for Anti-DDoS Pro and Anti-DDoS Premium. You can monitor their availability, HTTP response status codes such as 5xx and 4xx, and other metrics in real time to promptly detect service exceptions.
Perform routine O&M.
Pay-as-you-go burstable protection and advanced mitigation sessions for the Insurance plan:
The first time you purchase an Anti-DDoS Pro or Anti-DDoS Premium instance in the Chinese mainland, you receive one free Anti-DDoS plan of the 300 Gbps specification. For more information, see Anti-DDoS plans. You must bind the plan to your instance and set the burstable protection threshold to 300 Gbps as soon as possible. After the plan is bound, you are not charged burstable protection fees for mitigated attacks that have a peak throughput of less than 300 Gbps within the current calendar day.
NoteIf you do not want to enable the burstable protection feature of Anti-DDoS Pro or Anti-DDoS Premium after the Anti-DDoS plan is exhausted or expires, you must promptly adjust the burstable protection threshold to the basic protection bandwidth of the instance.
To enable the burstable protection feature of Anti-DDoS Pro or Anti-DDoS Premium (Chinese Mainland), you must first check the billing methods of Anti-DDoS Pro and Anti-DDoS Premium (Chinese Mainland). For more information, see Billing of Anti-DDoS Pro and Anti-DDoS Premium (Chinese Mainland). This prevents the actual burstable protection fees from exceeding your budget.
For an Insurance plan instance of Anti-DDoS Pro or Anti-DDoS Premium (Outside Chinese Mainland), you receive two free advanced mitigation sessions per month. You can select a plan edition as needed.
Determine the attack type:
When an Anti-DDoS Pro or Anti-DDoS Premium instance is under both CC attacks and DDoS attacks, you can view the Security Overview report in the Anti-DDoS Pro and Anti-DDoS Premium console. For more information, see Security Overview. You can determine the attack type based on the attack traffic information:
DDoS attack type: The protection report on the Instances tab shows that attack traffic fluctuates and traffic scrubbing has been triggered, but there are no associated fluctuations in the protection report on the Domain Name tab.
CC attack type: The protection report on the Instances tab shows that attack traffic fluctuates and traffic scrubbing has been triggered. The protection report on the Domain Name tab also shows associated fluctuations.
For more information, see How do I determine the type of attack on an Anti-DDoS Pro or Anti-DDoS Premium instance?
Service access latency or packet loss:
If the origin server is in a region outside the Chinese mainland and the main users are from the Chinese mainland, users may experience high latency and packet loss when they access the website. This may be because of unstable access links that are caused by cross-carrier networks. You can use an Anti-DDoS Pro or Anti-DDoS Premium (Outside Chinese Mainland) instance with an acceleration line.
Delete a domain name or port forwarding configuration:
To delete a protected domain name or port forwarding configuration record, you must confirm whether the service has been formally added to Anti-DDoS Pro or Anti-DDoS Premium.
If the service traffic has not been formally switched, you can delete the domain name or port forwarding configuration record in the Anti-DDoS Pro and Anti-DDoS Premium console.
If the service traffic has been switched, you must go to the DNS console of your domain name service to modify the DNS record. You must switch the service traffic back to the origin server before you delete the domain name or port forwarding configuration.
NoteBefore you delete a forwarding configuration, you must make sure that the DNS record or service access of the domain name has been switched back to the origin server.
After you delete a domain name configuration, Anti-DDoS Pro and Anti-DDoS Premium can no longer provide professional security protection for your service.
Precautions for emergency onboarding
If your service is already under attack, note the following when you add the service to Anti-DDoS Pro or Anti-DDoS Premium:
The service is under a DDoS attack
In most cases, after you add the service to Anti-DDoS Pro or Anti-DDoS Premium, you can use the default protection configuration.
If you find that Layer 4 CC attack traffic is passed through to the origin server, you can enable the source and destination connection throttling policies in the DDoS mitigation policies. For more information, see Configure a single DDoS mitigation policy.
The origin IP address is throttled by blackhole filtering
If the origin server of your service is attacked and the blackhole filtering policy is triggered before you add the service to Anti-DDoS Pro or Anti-DDoS Premium, you must promptly change the origin ECS IP address. If the origin server is an SLB instance, you must change the public IP address of the SLB instance. For more information, see Change the public IP address of an origin ECS instance. After you change the origin IP address, you must add the service to Anti-DDoS Pro or Anti-DDoS Premium for protection as soon as possible to prevent the origin IP address from being exposed.
If you do not want to change the origin IP address, or if the origin IP address has been changed but is still exposed, you can deploy an SLB instance in front of the origin ECS server. Then, you can use the public IP address of the SLB instance as the origin IP address to add to Anti-DDoS Pro or Anti-DDoS Premium.
NoteIf your origin server is not deployed on Alibaba Cloud and is under attack, you need to urgently add the service to Anti-DDoS Pro or Anti-DDoS Premium for protection. You must make sure that the domain name that is used by your service has an ICP filing from the Ministry of Industry and Information Technology (MIIT). Before you add the service to Anti-DDoS Pro or Anti-DDoS Premium, you must contact Alibaba Cloud technical support to perform special processing on the domain name. This prevents service unavailability that is caused because you have not added Alibaba Cloud to the ICP filing information of the domain name
The service is under a CC attack or crawler attack
When your service is under a CC attack or crawler attack, you can add the service to Anti-DDoS Pro or Anti-DDoS Premium. Then, you can analyze HTTP access logs to determine attack features and set corresponding protection policies. For example, you can analyze whether request fields such as the source IP address, URL, Referer, User Agent, Params, and Header are legitimate.