After you add a website service to Anti-DDoS Proxy, Anti-DDoS Proxy scrubs the traffic that is destined for the service and then forwards the traffic to the origin server. The origin server can obtain the originating IP addresses of requests from the X-Forwarded-For header or by installing the TCP Option Address (TOA) kernel module. This topic describes how to obtain the originating IP addresses of requests.
Non-website service provided by using a port
In some scenarios, you can install the TOA kernel module to obtain the originating IP addresses of requests. For more information, see Install the TOA kernel module to obtain the originating IP addresses of requests. If the TOA kernel module cannot be installed, contact technical support.
Anti-DDoS Proxy instance with an IPv4 address
TCP OPTION field usage method: After you add a non-website service at Layer 4 to Anti-DDoS Proxy, Anti-DDoS Proxy connects to the origin server by using a three-way handshake process. In the TCP Option of the last ACK packet, information such as option type 254, source port number, and source IP is inserted, occupying a total of 8 bytes. The specific position is shown in the following figure.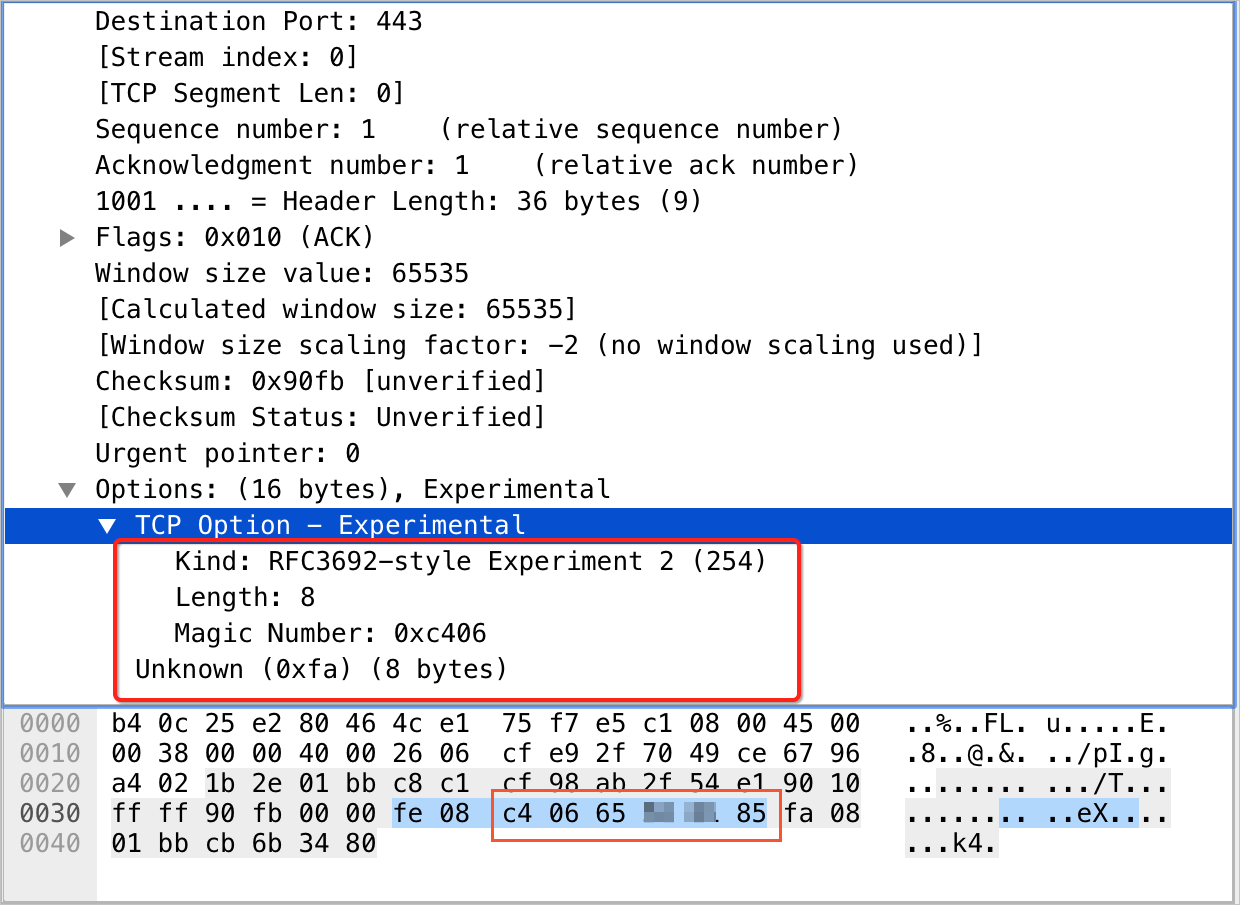
Port number: The
Magic Numberfield represents the port number in hexadecimal characters. In the example, c4 06 converts to decimal to obtain the corresponding port number 50182.Source IP address: The four consecutive bytes after the port number represent the source IP address in hexadecimal characters. In the example, 65 ** ** 85 converts to decimal to obtain the corresponding source IP address 101.***.***.133.
Anti-DDoS Proxy instance with an IPv6 address
V6tov4 mode
TCP OPTION field usage method: After you add a non-website service at Layer 4 to Anti-DDoS Proxy, the Anti-DDoS node and the origin server complete a three-way handshake. In the TCP Option of the last ACK packet, option type 249, source port number, source IP, Anti-DDoS IP, and other information are inserted, occupying a total of 40 bytes. The specific position is shown in the following figure.
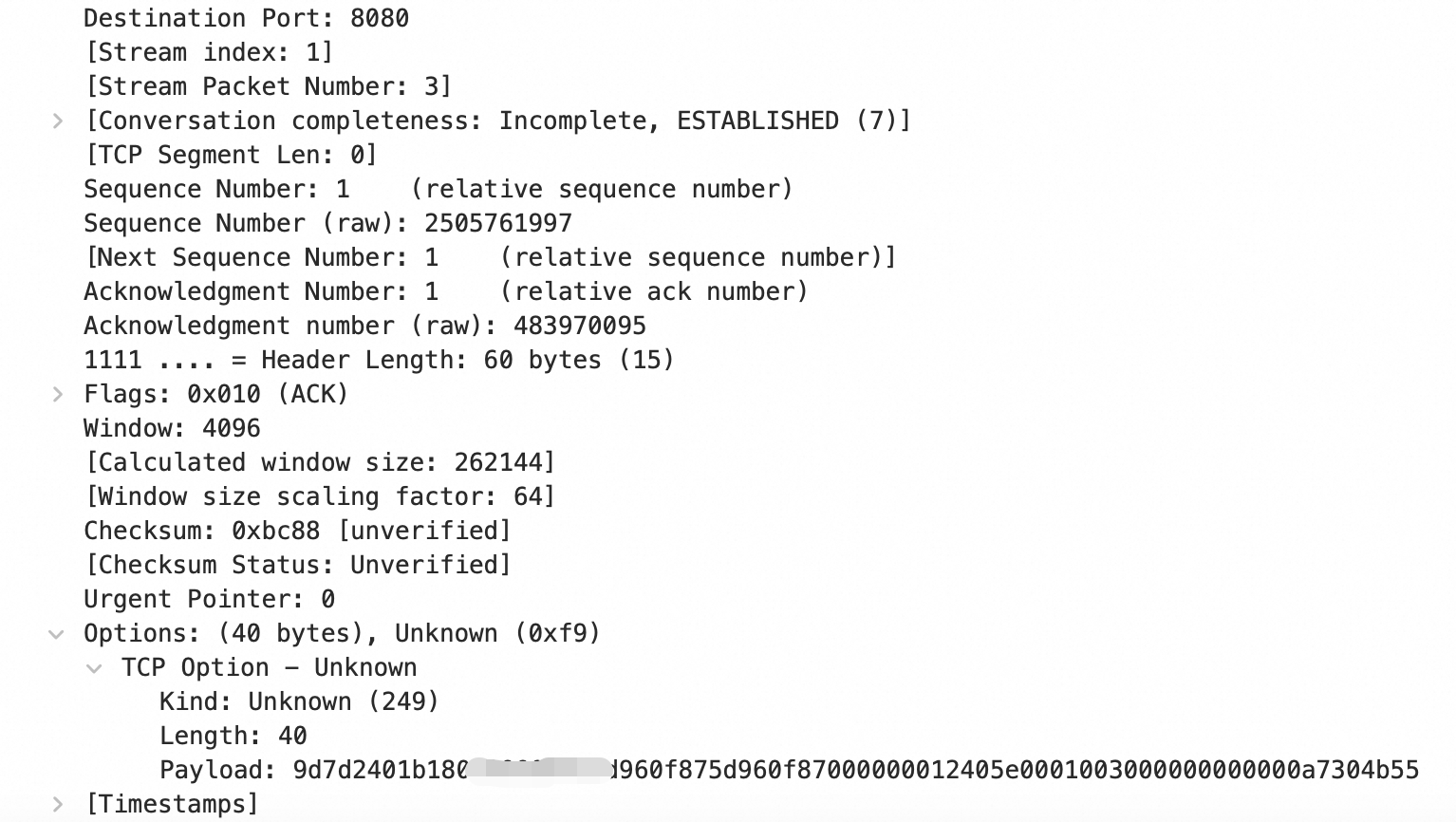
Port number: The first two bytes in the
Payloadrepresent the port number in hexadecimal characters. In the example, it is 9d7d, which converts to decimal to obtain the corresponding port number 40317.Source IP address: The consecutive sixteen bytes after the port number represent the source IP address in hexadecimal characters, directly corresponding to the IPv6 address. In the example, it is 2401*****0f87, which means the source IP address is 2401:b180:100*:*:*:f87:5d96:f87.
NoteThe remaining twenty bytes in the
Payloadbesides the port number and source IP address contain the Anti-DDoS Proxy IP information.
V6tov6 scenario
TCP OPTION field usage method: After adding a non-website service at Layer 4 to Anti-DDoS Proxy, the Anti-DDoS node and the origin server complete a three-way handshake. In the TCP Option of the last ACK packet, option type 253, source port number, and source IP information are inserted, occupying a total of 20 bytes. The specific position is shown in the following figure.

Port number: The
Experiment Identifierfield represents the port number in hexadecimal characters. In the example, it is eb98, which converts to decimal to obtain the corresponding port number 60312.Source IP address: The
Datafield represents the source IP address in hexadecimal characters, directly corresponding to the IPv6 address. In the example, it is 2401*****0f87, which means the source IP address is 2401:b180:100*:*:*:f87:5d96:f87.
To prevent the traffic from the back-to-origin CIDR blocks of your Anti-DDoS Proxy instance from being blocked, we recommend that you add the back-to-origin CIDR blocks of the instance to the whitelist of the origin server. For more information about how to query back-to-origin CIDR blocks of an Anti-DDoS Proxy instance, see Allow back-to-origin CIDR blocks to access the origin server.
If your origin server is an Elastic Compute Service (ECS) instance, add the back-to-origin CIDR blocks of your Anti-DDoS Proxy instance to the security group of the ECS instance. For more information, see Add a security group rule.
If your origin server is an ECS instance that is deployed after a Server Load Balancer (SLB) instance, add the back-to-origin CIDR blocks of your Anti-DDoS Proxy instance to the whitelist of the SLB instance. For more information, see Enable access control.
Website service provided by using a domain name
If service requests are forwarded to the origin server by a Layer 7 proxy server, such as an Anti-DDoS Proxy instance, the originating IP addresses obtained by the origin server are the back-to-origin IP addresses of the Anti-DDoS Proxy instance. The originating IP addresses are recorded in the X-Forwarded-For header. The format is X-Forwarded-For: Originating IP address, Back-to-origin IP address of Anti-DDoS Proxy.
If the requests pass through more than one proxy server, the X-Forwarded-For header records the originating IP addresses and the IP addresses of all proxy servers. The format is X-Forwarded-For: Originating IP address, IP address of Proxy server 1, IP address of Proxy server 2, IP address of Proxy server 3, .... The proxy server can be a Web Application Firewall (WAF) instance or an Alibaba Cloud CDN (CDN) instance.
A common web application server can use the X-Forwarded-For header to obtain the originating IP addresses of requests.
You can use the following methods to obtain the value of the X-Forwarded-For header in different programming languages:
ASP
Request.ServerVariables("HTTP_X_FORWARDED_FOR")ASP.NET (C#)
Request.ServerVariables["HTTP_X_FORWARDED_FOR"]PHP
`$_SERVER["HTTP_X_FORWARDED_FOR"]JSP
request.getHeader("HTTP_X_FORWARDED_FOR")
In the X-Forwarded-For header, the IP address before the first comma (,) is the originating IP address of a request.
You can also configure common web servers, such as NGINX, IIS 6, IIS 7, Apache, and Tomcat, to obtain the originating IP addresses. For more information, see Retrieve the originating IP addresses of clients.