This topic describes how to view service data and DDoS attack details for an instance and a domain name in the Anti-DDoS Pro and Anti-DD Premium console. This information helps you understand the DDoS protection status of your assets and promptly adjust your DDoS mitigation policies.
Overview
Anti-DDoS Pro and Anti-DDoS Premium allow you to view data from the last 30 days. You can click Traffic Relationships and Description in the upper-right corner of the Security Overview page to learn about traffic-related concepts for Anti-DDoS Pro and Anti-DDoS Premium.
Prerequisites
An Anti-DDoS Proxy (Chinese Mainland) or Anti-DDoS Proxy (Outside Chinese Mainland) instance is purchased. For more information, see Purchase an Anti-DDoS Pro or Anti-DDoS Premium instance.
A website service or non-website service is added to Anti-DDoS Proxy. For more information, see Add websites or Manage forwarding rules.
View the security overview of an instance
Anti-DDoS Pro and Anti-DDoS Premium display service information and DDoS attack details for each instance.
Log on to the Anti-DDoS Proxy console.
In the top navigation bar, select the region of your instance.
Anti-DDoS Proxy (Chinese Mainland): Choose the Chinese Mainland region.
Anti-DDoS Proxy (Outside Chinese Mainland): Choose the Outside Chinese Mainland region.
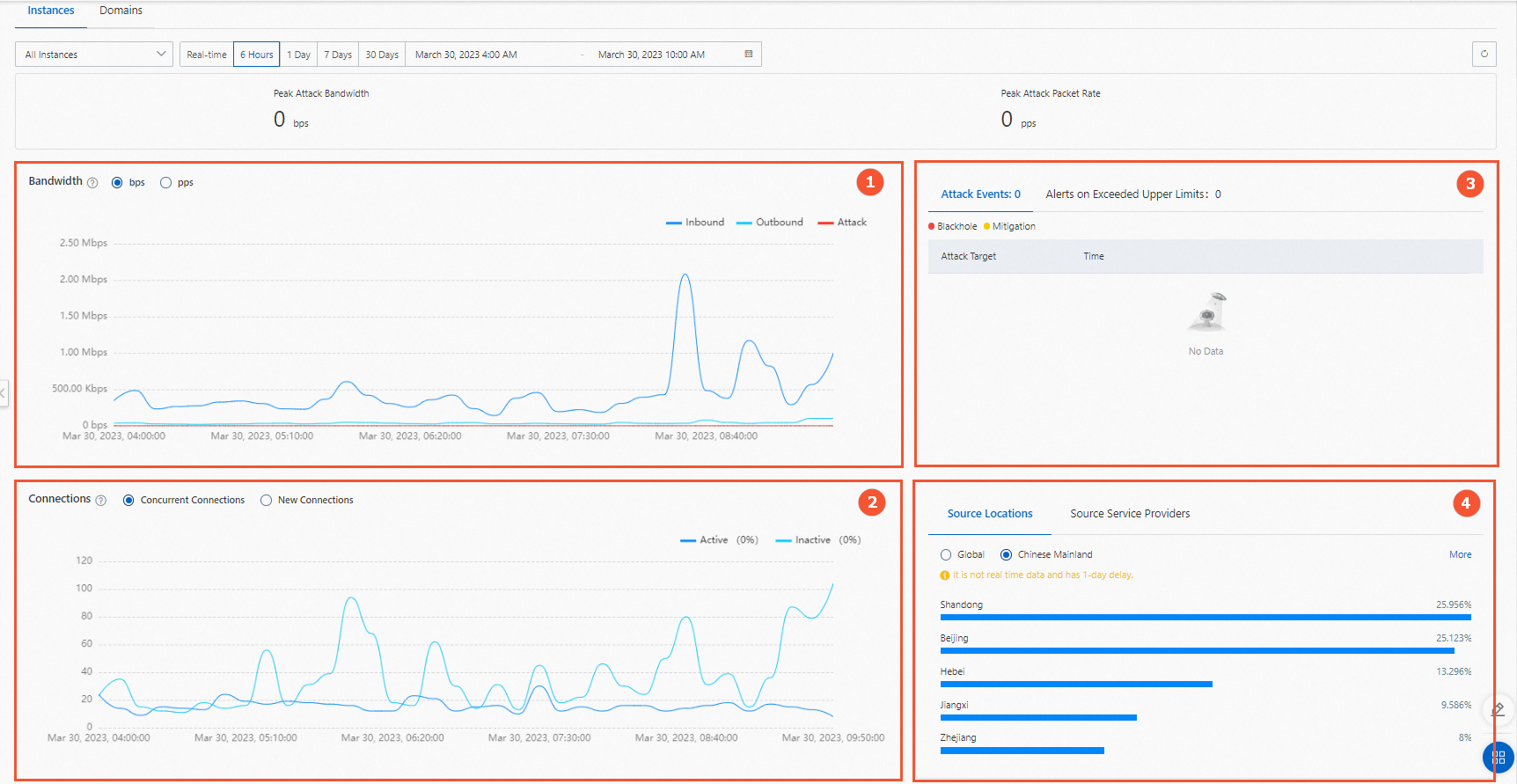
In the navigation pane on the left, click Security Overview. On the Instance tab of the Security Overview page, you can view the following information.
Feature
Description
Bandwidth (marked 1 in the preceding figure)
For Anti-DDoS Pro (the Chinese mainland), the Bandwidth trend chart displays the trends of inbound, outbound, attack, and throttling traffic for an instance over a specified period. The traffic is measured in bps or pps.
For Anti-DDoS Pro and Anti-DDoS Premium (outside the Chinese mainland), the following tabs are provided: Overview shows bandwidth trends, Inbound Traffic Distribution shows the distribution of inbound traffic, and Outbound Traffic Distribution shows the distribution of outbound traffic.
Connections (marked 2 in the preceding figure)
Concurrent Connections: The total number of TCP connections established between clients and the instance.
Active connections: The number of TCP connections that are in the Established state.
Inactive connections: The number of TCP connections that are in any state other than Established.
New Connections: The number of new TCP connections established between clients and the instance per second.
Network Layer Attack Events, Alert on Exceeded Upper Limits, and Destination Rate Limit Events (marked 3 in the preceding figure)
Network Layer Attack Events:
Hover over an attacked IP address or port to view information about the attacked IP address and port, attack type, attack peak, and protection result.
Alerts on Exceeded Upper Limits:
Alerts are supported for the following event types: clean bandwidth, new connections, and concurrent connections. If the traffic or number of connections exceeds the purchased specification, an alert is generated. In this case, your services are not affected, but a specification upgrade is recommended. For more information, see Upgrade an instance.
You can click Details in the Status column to go to the System Logs page and view the details.
NoteData for alerts on exceeded upper limits is updated at 10:00 (UTC+8) every Monday with data from the previous day. If you have configured notifications using internal messages, text messages, or email, you will also receive a notification at 10:00 (UTC+8) every Monday that contains data from the previous day.
Destination Rate Limit Events
If metrics such as the number of new connections, concurrent connections, or service bandwidth significantly exceed the instance specifications, the corresponding throttling policy is triggered. This affects your services and generates a destination rate limit event.
If rate limiting is triggered by service traffic, we recommend that you upgrade the specifications of your instance as soon as possible. For more information, see Upgrade an instance.
If rate limiting is triggered by DDoS attacks, we recommend that you adjust your mitigation policies as soon as possible. For more information, see Configure blacklists and whitelists for IP addresses.
You can click Details in the Status column to go to the System Logs page and view detailed information.
Service Distribution by Location and Service Distribution by ISP (marked 4 in the preceding figure)
Service Distribution by Location: The distribution of source locations from which service traffic originates.
Service Distribution by ISP: The distribution of Internet service providers (ISPs) from which service traffic originates.
View the security overview of a domain name
Anti-DDoS Pro and Anti-DDoS Premium display service information and DDoS attack event details for each domain name.
Log on to the Anti-DDoS Proxy console.
In the top navigation bar, select the region of your instance.
Anti-DDoS Proxy (Chinese Mainland): Choose the Chinese Mainland region.
Anti-DDoS Proxy (Outside Chinese Mainland): Choose the Outside Chinese Mainland region.
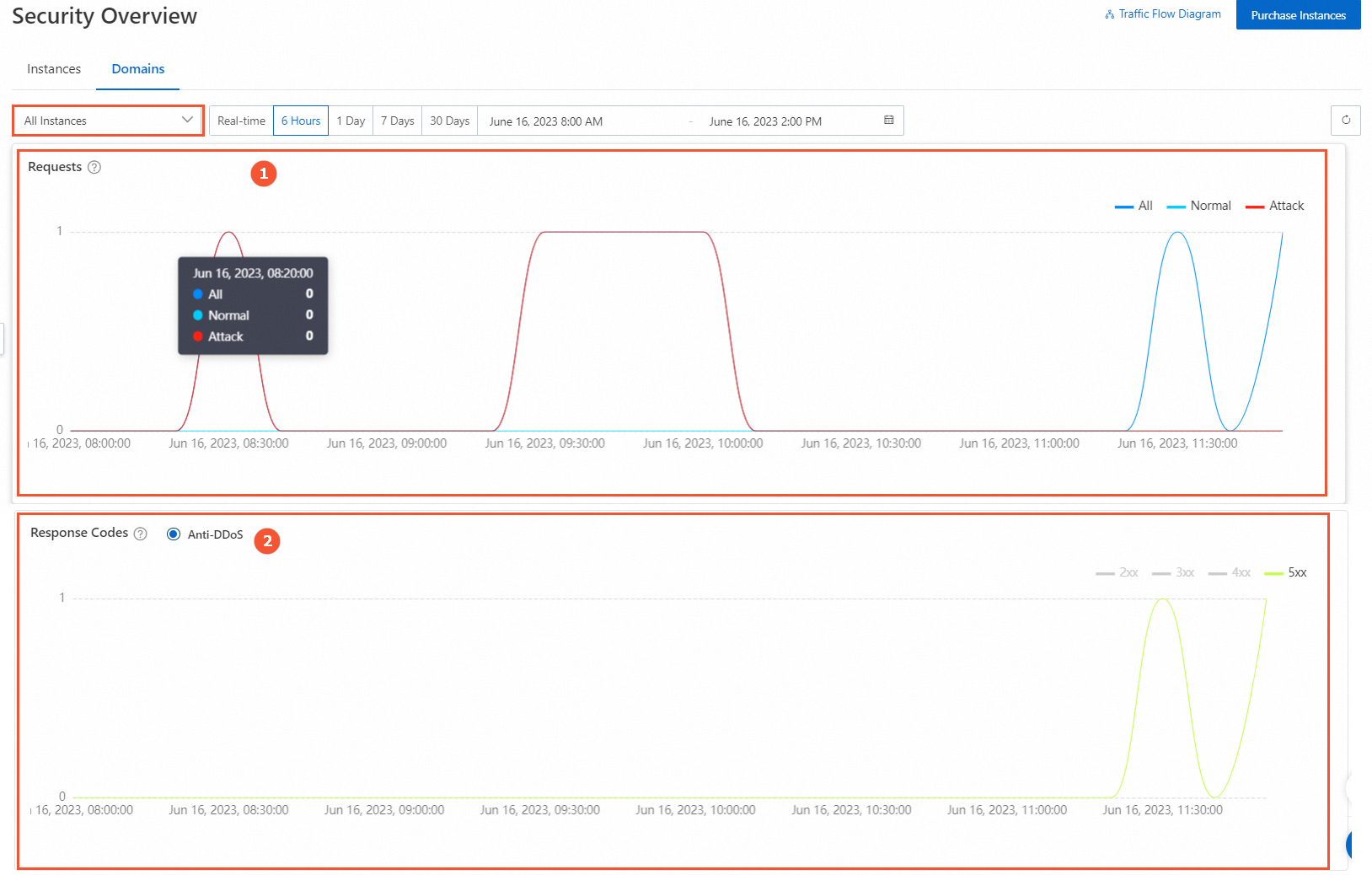
In the navigation pane on the left, click Security Overview. On the Domain Name ab of the Security Overview page, you can view the following information.
View total QPS by instance
From the Select Domain Name drop-down list, click the Total QPS by Instance tab, select the required exclusive IP addresses, and then click OK.
Feature
Description
Request Rate (QPS) (marked 1 in the preceding figure)
Displays the trend graph of the request rate for each Anti-DDoS Pro or Anti-DDoS Premium instance. The time granularity varies based on the specified time range.
Status Codes and Requests (marked 2 in the preceding figure)
Displays the response codes from Anti-DDoS Pro and Anti-DDoS Premium for each instance. The number of recorded response codes is the cumulative value within the time granularity. The following list describes the response codes:
2XX: The request was successfully received, understood, and accepted by the server.
NoteStatistics for 2XX response codes include statistics for the 200 response code.
3XX: The client must perform further operations to complete the request. These status codes are usually used for redirection.
4XX: An error may have occurred on the client, which prevents the server from processing the request.
5XX: An error or exception occurred while the server was processing the request.
View QPS by domain name
From the Select Domain Name drop-down list, click the QPS by Domain tab, select the domain names, and then click OK.
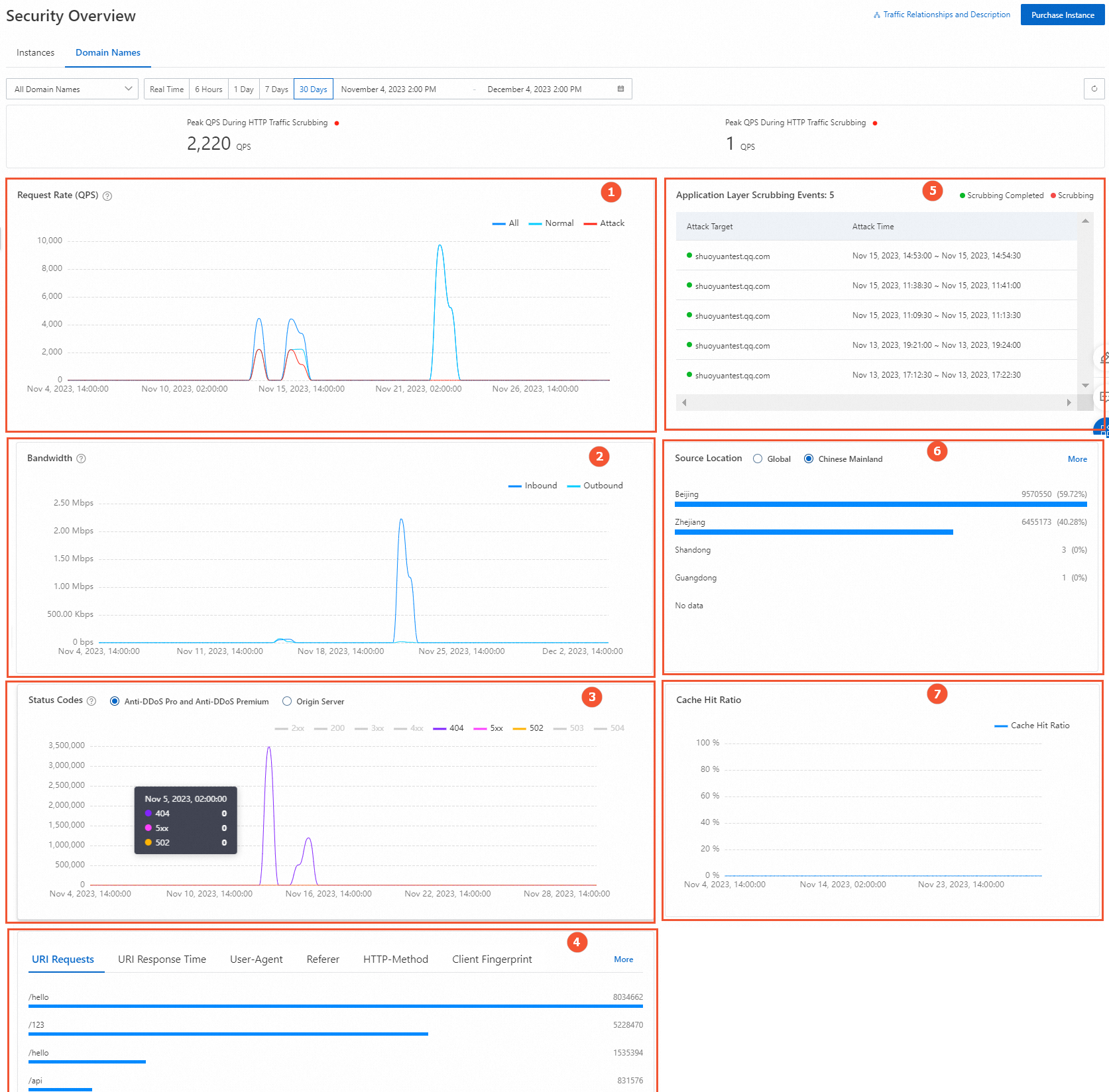
Feature
Description
Request Rate (QPS) (marked 1 in the preceding figure)
Displays the trend graph of the request rate for each domain name. The time granularity varies based on the specified time range.
Bandwidth (marked 2 in the preceding figure)
Displays the trend graphs of the peak outbound and inbound bandwidth for the domain name.
NoteOnly the payload field is counted. This may cause a drift from the instance-level bps trend graph.
Status Codes and Requests (marked 3 in the preceding figure)
Includes response codes from Anti-DDoS Pro and Anti-DDoS Premium and response codes from the origin server. The number of recorded response codes is the cumulative value within the time granularity. The following list describes the response codes:
2XX: The request was successfully received, understood, and accepted by the server.
Note2XX includes all status codes from 200 to 299.
200: The request succeeded.
3XX: The client must perform further operations to complete the request. These status codes are usually used for redirection.
4XX: An error may have occurred on the client, which prevents the server from processing the request.
Note4XX includes all status codes from 400 to 499.
403: The server understood the client's request but refused to fulfill it.
404: The server could not find the resource requested by the client.
405: The server understood the resource path of the client's request, but the HTTP method used in the request, such as GET, POST, PUT, or DELETE, is not allowed for that resource.
410: The resource has been deleted from the server.
499: The client canceled the request before the server finished processing it.
5XX: An error or exception occurred while the server was processing the request.
Note5XX includes all status codes from 500 to 599.
502: Anti-DDoS Pro and Anti-DDoS Premium, acting as a proxy server, received an invalid response from the upstream server when attempting to fulfill the request.
503: The server is currently unable to handle the request, possibly due to temporary server maintenance or overload.
504: Anti-DDoS Pro and Anti-DDoS Premium, acting as a proxy server, did not receive a timely response from the upstream server when attempting to fulfill the request.
URI Requests and URI Response Time (marked 4 in the preceding figure)
This section displays the Top 5 data for the following metrics: URI Requests, URI Response Time, User-Agent, Referer, HTTP-Method, Client Fingerprint, HTTP/2 Fingerprint, JA3 Fingerprint, and JA4 Fingerprint. You can click More to view more data. For more information about these metrics, see Appendix 1: Supported HTTP request fields.
NoteThe URI response time is the time elapsed from when Anti-DDoS Pro and Anti-DDoS Premium receives a client request until it finishes processing and returns a response. This is measured in milliseconds. If a URI has multiple response times, the maximum value is used.
Application Layer Scrubbing Events (marked 5 in the preceding figure)
Displays scrubbing events that occurred at the application layer. You can hover over a domain name to view information about the attacked domain name, attack peak, and attack type.
Source Location (marked 6 in the preceding figure)
The distribution of access source locations.
Cache Hit Ratio (marked 7 in the preceding figure)
This applies to scenarios with the static page cache feature enabled. For more information, see Anti-DDoS Lab.
Set an alert threshold
For volumetric attacks, the default policy of Anti-DDoS Pro and Anti-DDoS Premium is designed to prevent an excessive number of alerts. By default, a flood attack alert event is generated only if the inbound traffic is 500 Mbps or higher and the scrubbing traffic is greater than 100 Mbps. If your normal service traffic is low, you may not receive alerts for smaller attacks. To address this, you can configure a custom alert threshold. This ensures that an attack event is generated even when scrubbing traffic is visible in the console for attacks that do not meet the default threshold.
Log on to the Anti-DDoS Proxy console.
In the top navigation bar, select the region of your instance.
Anti-DDoS Proxy (Chinese Mainland): Choose the Chinese Mainland region.
Anti-DDoS Proxy (Outside Chinese Mainland): Choose the Outside Chinese Mainland region.
In the navigation pane on the left, click Security Overview. On the Security Overview page, in the Set Alert Threshold area, you can configure a custom attack alert threshold.
 As shown in the figure, you can configure the inbound bandwidth threshold based on the following points:
As shown in the figure, you can configure the inbound bandwidth threshold based on the following points: The threshold applies to the total inbound bandwidth received by a single IP address of the Anti-DDoS instance.
Inbound traffic includes attack traffic and service traffic.
An alert event is generated if the inbound traffic is greater than or equal to the custom threshold and the scrubbing traffic is greater than 100 Mbps.
This setting applies to all IPv4 addresses of the Anti-DDoS instance. Custom adjustments for IPv6 addresses are not supported.