When implementing various security services provided by public cloud services, you may have the question: Can I really prevent security attacks from the outside?
In this article, we will use Alibaba Cloud Web Application Firewall (WAF) to verify security. WAF can identify and block web attacks and malicious web requests in real-time. We will launch attacks on the website service to test whether Alibaba Cloud WAF can prevent them. The following section will describe the steps.
The configuration steps are simple. WAF is placed in front of a web server to prevent the exposed web server. In this example, we will use an Elastic Compute Service (ECS) server. All access to the web server will be verified using WAF. The fully qualified domain name (FQDN) of the web server and the CNAME of WAF are registered in Domain Name System (DNS).
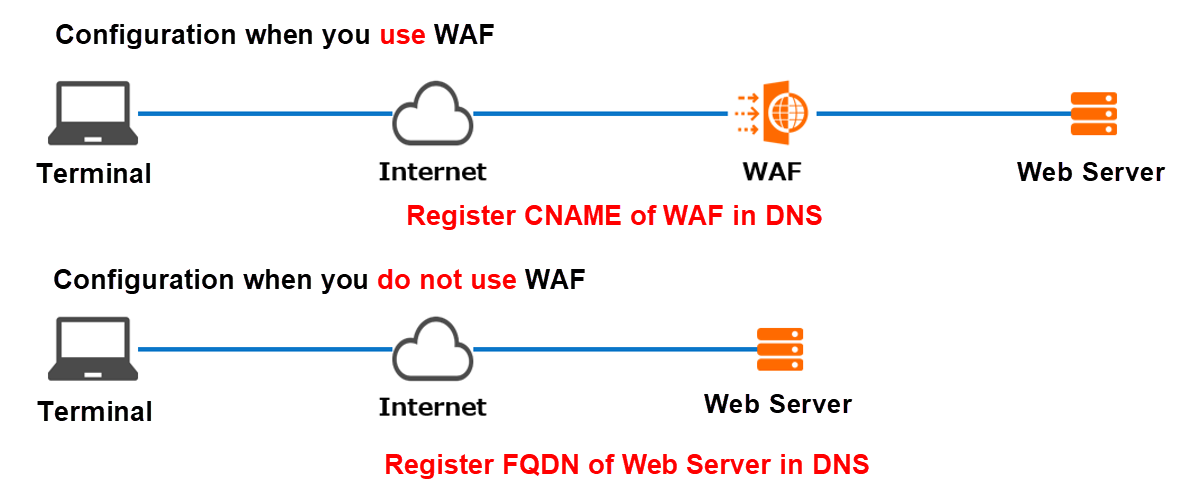
The web server has a global IP address. As a result, the web server can check accesses that are not verified by using WAF.
Note: The following section describes the definition of IP address, CNAME, and FQDN:
In this example, we will use an Alibaba Cloud Elastic Compute Service (ECS) server. The operating system of the ECS server is CentOS.
# yum -y update
# yum -y install httpd# yum -y install certbot
# systemctl enable httpd
# systemctl start httpd
# certbot certonly --webroot -w /var/www/html -d <Web server FQDN>Note: Resolve DNS records before you create an encryption certificate.
Run the following commands to create a certificate:
/etc/letsencrypt/live/<Web server FQDN>/fullchain.pem
/etc/letsencrypt/live/<Web server FQDN>/privkey.pem# yum -y install mod_ssl# vi /etc/httpd/conf.d/ssl.confRun the vi commands to add the following files:
SSLCertificateFile /etc/letsencrypt/live/<Web server FQDN>/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/<Web server FQDN>/privkey.pem# systemctl restart httpd# yum install �Cy php# cd /var/www/html/
# vi index.htmlUsing the vi command to create HTML source code.
<!DOCTYPE html>
<html lang="ja">
<head>
<meta charset="utf-8">
<title> Getting started with HTML: Create a text box</title>
</head>
<body>
<form action="//sbc-nextcloud.sbcicp1.net/index.php" method="post">
<p> Username:<br>
<input type="text" name="name"></p>
<p><input type="button" value="Check" id="button2"></p>
</form>
</body>
</html># vi index.phpUsing the vi command to create PHP source code.
<?php
foreach (getallheaders() as $name => $value) {
echo "$name: $value\n";
}
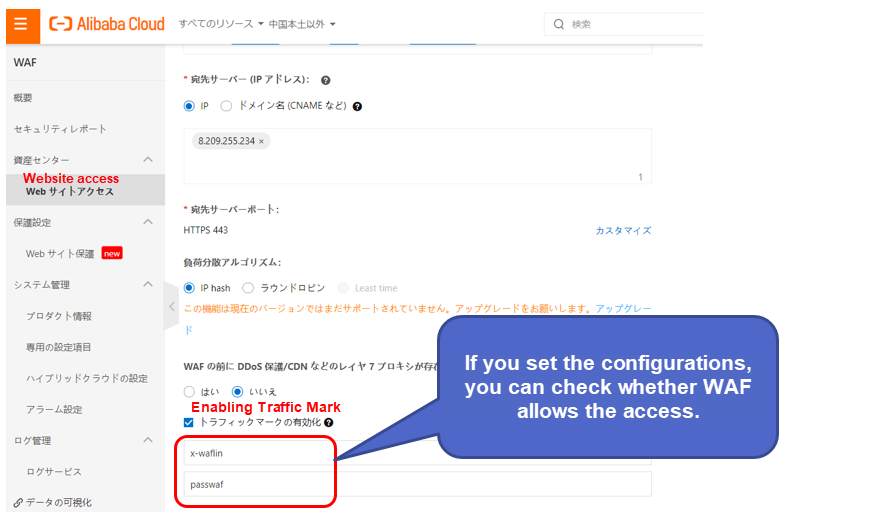
?>
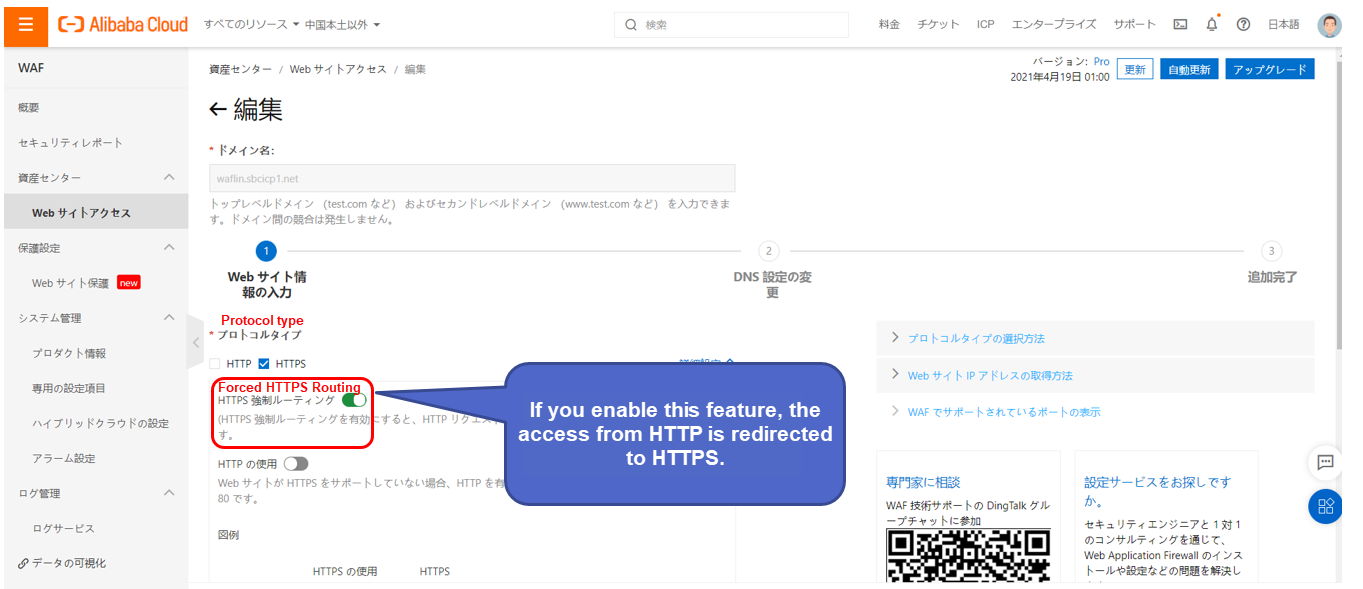
Access https://<Web Server FQDN>/index.php to check the access results.
If the configuration in the following figure exists, WAF is used for access.
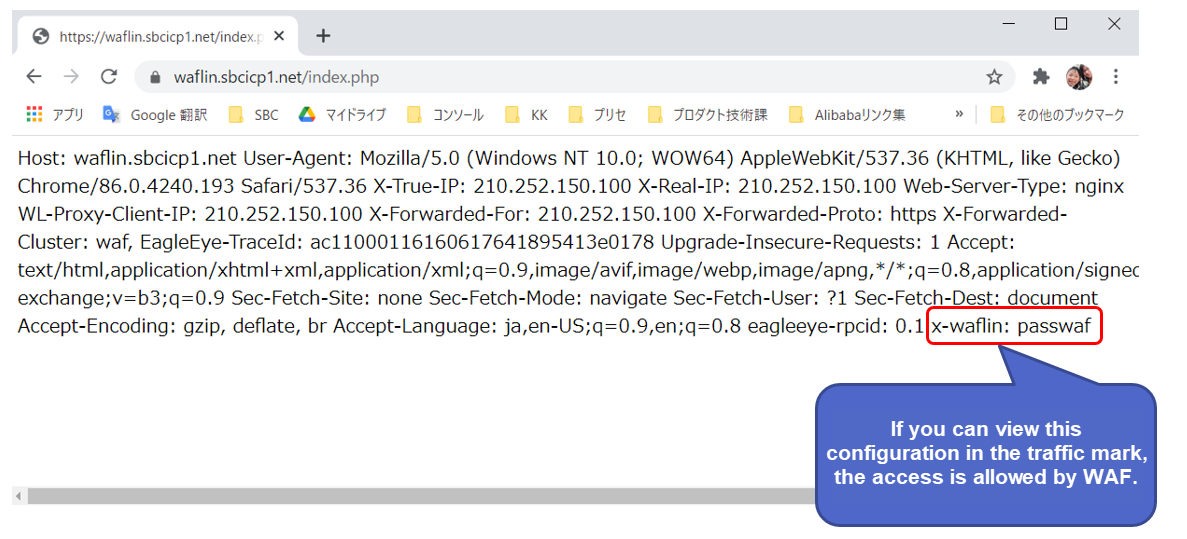
We will launch attacks by tampering with the URL parameters while WAF is enabled.
The website can be accessed normally if the URL parameters are not tampered with.
However, after launching attacks, the website will become inaccessible, demonstrating the effectiveness of WAF.
To launch attacks, please tamper with the following URL parameter:
https://<Web server FQDN>/index.html?q=SELECT id,pass FROM login_user WHERE id='1' or '1' = '1'-- AND pass=";The following figure shows that the access request is denied by WAF.
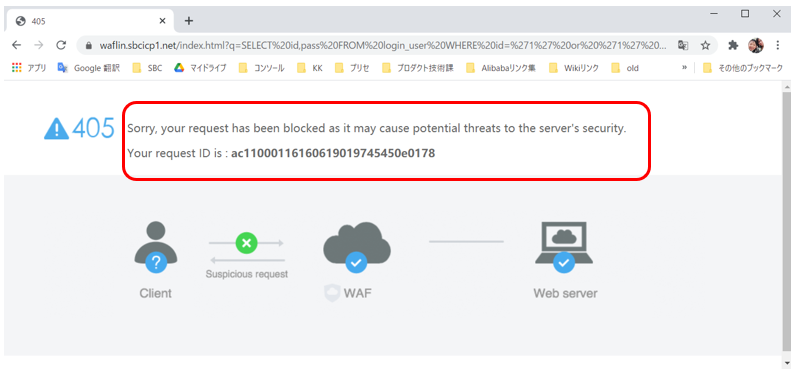
Next, we will launch attacks with WAF disabled.
To do so, please tamper with the following URL parameter and use a global IP address if you have not registered the CNAME.
https://8.209.255.234/index.html?q=SELECT id,pass FROM login_user WHERE id='1' or '1' = '1'-- AND pass=";The following figure shows the page displayed when accessing an ECS server without WAF.
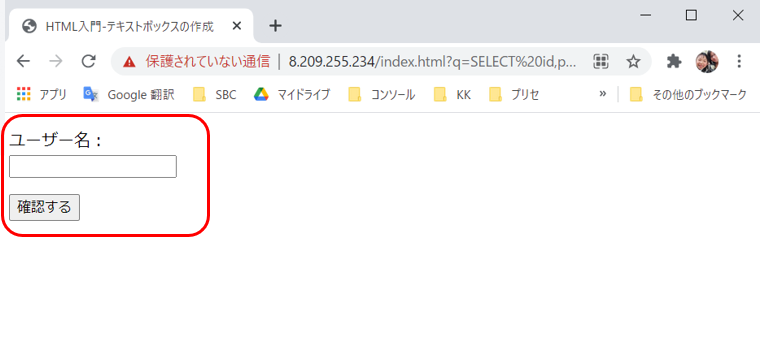
In this example, you can check whether Alibaba Cloud WAF can prevent web servers from malicious attacks. The biggest benefit of Alibaba Cloud WAF is that you can use WAF not only in Alibaba Cloud servers but also web servers of other cloud providers.
This article is a translated piece of work from SoftBank: https://www.softbank.jp/biz/blog/cloud-technology/articles/202208/alibaba-cloud-waf/
Disclaimer: The views expressed herein are for reference only and don't necessarily represent the official views of Alibaba Cloud.
Alibaba Cloud Community - March 24, 2023
Alibaba Cloud Community - August 4, 2023
Alibaba Clouder - November 19, 2019
Alibaba Clouder - December 19, 2019
Alibaba Clouder - December 21, 2017
Alibaba Cloud Community - December 4, 2023
 Web Hosting Solution
Web Hosting Solution
Explore Web Hosting solutions that can power your personal website or empower your online business.
Learn More WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn MoreMore Posts by H Ohara