For enterprises managing multiple Alibaba Cloud accounts, the cross-account backup feature provides a centralized data protection solution. It enables a designated management account to centrally back up and restore resources from member accounts, isolating backup data from source data at the account level. This centralized approach not only helps meet compliance and auditing requirements but also significantly reduces operational overhead. Since the management account handles all backup tasks, users in member accounts do not need to be trained on the backup system, leading to lower O&M costs and improved efficiency.
How it works
Cloud Backup supports two authorization mechanisms to add accounts for cross-account backup: one based on Resource Directory and the other based on RAM role assumption. The working principles and applicable scenarios for these two mechanisms are as follows:
Configure cross-account backup using Resource Directory: The management account and the accounts to be backed up must be in the same resource directory. The management account must be the management account of the resource directory or a delegated administrator account for the Cloud Backup service. The management account can centrally manage accounts within the resource directory to back up data from the cloud resources of these accounts. The operations are simple and visualized. This method is suitable for unified backup scenarios in enterprises that have built a multi-account architecture based on Resource Directory and for scenarios in industries, such as finance and government, that require strong compliance and centralized control.
Configure cross-account backup using RAM role assumption: Create a RAM role in the resource account and grant permissions to the management account. This allows Cloud Backup to temporarily assume the role in the resource account using the `AliyunServiceRoleForHbrCrossAccountBackup` service-linked role of the management account to obtain access permissions for the resources to be backed up. This method is applicable to scenarios where a Resource Directory is not used or where temporary or phased authorization through RAM is required to perform cross-account backups.
Both methods allow the management account to provide unified data protection for the accounts to be backed up. Unified backup policies can be used to back up data from multiple accounts and the backup data can be restored to any managed account. Backup tasks and backup data are managed within the management account. The accounts to be backed up do not need to enable or use the Cloud Backup service. Only the management account can use or delete the backup data, which isolates data at the account level.

In a cross-account backup scenario, the management account and the managed accounts to be backed up can perform the following operations:
Resource type | Operations allowed for the management account | Operations allowed for the account to be backed up |
ECS instance |
|
|
Other resource types |
|
|
Quotas and limits
Cross-account backup is supported for ECS instance backup, ECS file backup, NAS backup, OSS backup, Tablestore backup, Database Backup, and SAP HANA backup. After you perform a cross-account backup of an ECS instance, you can restore the instance only to the source Alibaba Cloud account. For information about specific supported scenarios, see the Cloud Backup console.
The backup points for an ECS instance belong to the management account, but the resulting ECS snapshots are stored in and billed to the source account. For more information, see Billing.
Cross-account backup does not affect backup performance, data deduplication, or network transfer efficiency.
When you configure cross-account backup using Resource Directory, the management account must be the management account of the resource directory or a delegated administrator account for the Cloud Backup service. You can add a maximum of three delegated administrator accounts for Cloud Backup.
For a list of supported regions, see Features available in each region.
Prerequisites
A management account and one or more accounts to be backed up are available.
If you want to configure cross-account backup based on a resource directory, make sure that the management account and the account to be backed up have been added to the same resource directory. For more information, see Enable a resource directory and Invite an Alibaba Cloud account to join a resource directory.
You have decided whether to configure cross-account backup using Resource Directory or RAM role assumption based on your scenario.
Add an account to be backed up using Resource Directory
(Optional) Step 1: Set a delegated administrator account for Cloud Backup
If you use the management account of the resource directory as the management account, skip this step.
To use a member account of a resource directory as the management account, you must set the account as the delegated administrator account for the Cloud Backup service in the trusted services of the resource directory in the Resource Management console. For more information, see Manage delegated administrator accounts.
Log on to the Resource Management console using the management account of the resource directory.
In the left navigation pane, choose .
On the Trusted Service page, in the row for the Cloud Backup service, click Manage in the Actions column.
In the Delegated Administrator Account section, click Add.
In the Add Delegated Administrator Account panel, select the management account.
Click OK.
After the account is added, the Cloud Backup service appears in the trusted services of the resource directory when you log on to the Resource Management console with the delegated administrator account.
Step 2: Add the account to be backed up in the management account
Log on to the Cloud Backup console using a management account.
In the left navigation pane, choose .
On the Cross-Account Backup page, switch to the region where the source account's resources are located.
Click Add an account to be backed up.
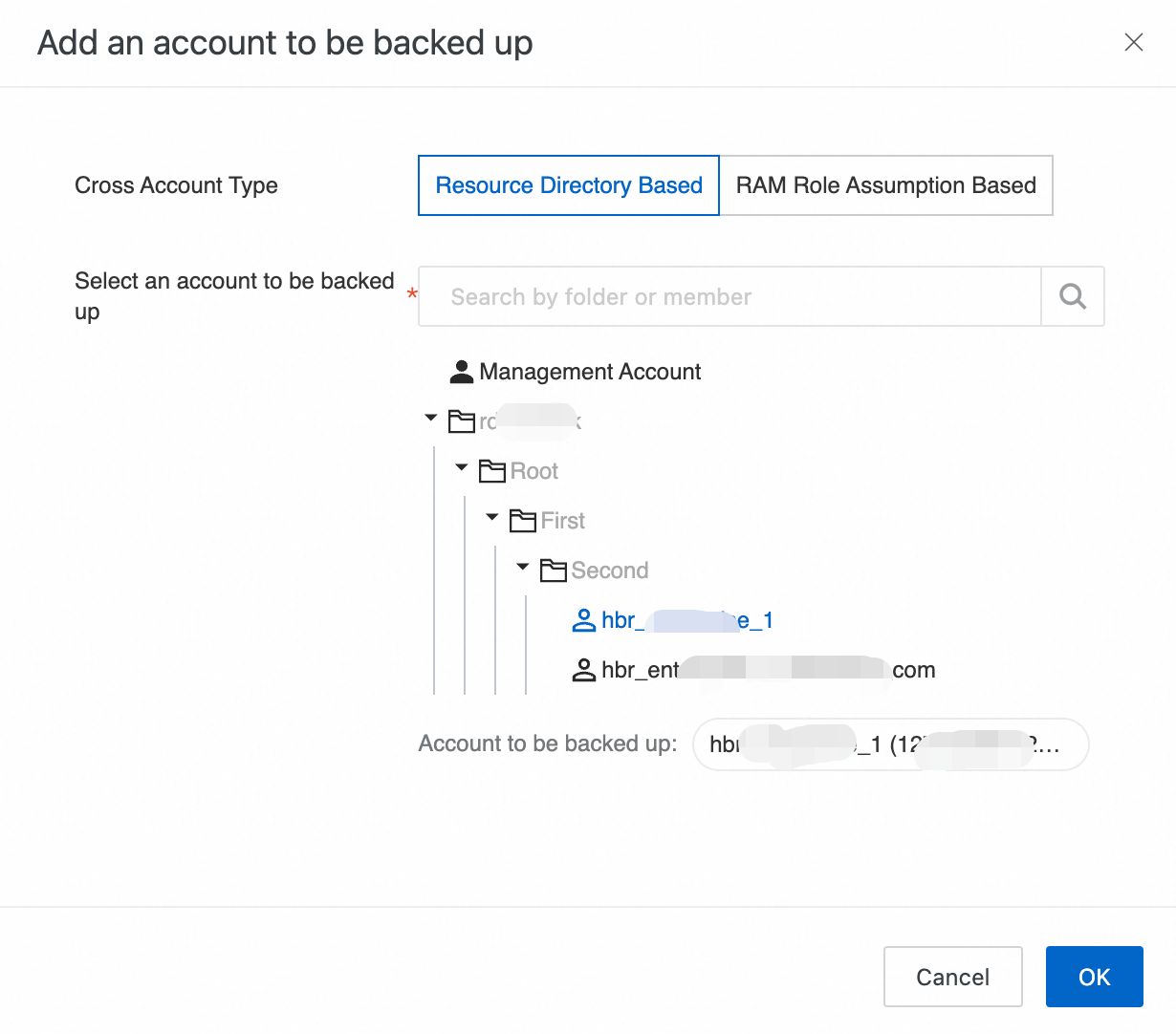
In the Add an account to be backed up panel, configure the following parameters and click OK.
Parameter
Description
Cross Account Type
Select Resource Directory Based.
Select an account to be backed up
Select the account to be backed up from the resource directory.
You can select only one account from the resource directory each time you add an account to be backed up. Enter a keyword to quickly find the desired member.
NoteFor accounts that are added to a resource directory, configure cross-account backup using the resource directory. You can also configure cross-account backup by assuming a RAM role. For more information, see Add an account to be backed up using RAM role assumption.
After the account is added, the account to be backed up appears in the account list.
 When an account to be backed up is managed for the first time, Cloud Backup automatically creates the AliyunServiceRoleForHbrRd service-linked role:
When an account to be backed up is managed for the first time, Cloud Backup automatically creates the AliyunServiceRoleForHbrRd service-linked role:Role name: AliyunServiceRoleForHbrRd
Access policy: AliyunServiceRolePolicyForHbrRd
Permission description: Allows Cloud Backup to access the resources of other authorized accounts for cross-account backup and restore operations.
The following actions affect cross-account authorization and may cause cross-account backups to fail. Proceed with caution.
Deleting the account to be backed up from the cross-account backup list of the management account.
Removing the management account from the role of management account of the resource directory or the delegated administrator account for the Cloud Backup service.
The source account is no longer a member of the resource directory that is managed by the backup management account.
Deleting the AliyunServiceRoleForHbrRd service-linked role in the account to be backed up.
Existing backups are not affected. If you want to cancel a cross-account backup, see Cancel cross-account backup.
Add an account to be backed up using RAM role assumption
Step 1: Create a RAM role in the account to be backed up
Log on to the RAM console using the account that you want to back up.
In the left navigation pane, choose .
On the Roles page, click Create Role.
On the Create Role page, set Principal Type to Cloud Account. Then, set Principal Name to Other Account, enter the ID of the account, and click OK.
 Note
NoteYou can go to the Security Settings page to view your Alibaba Cloud account ID.
In the Create Role dialog box, enter a name for the RAM role, such as hbrcrossrole, and click OK.
Step 2: Grant permissions to the RAM role in the account to be backed up
After you create a RAM role, you must grant it a system policy or a custom policy. On the Precise Permissions page, RAM provides two system policies by default. Select one of the policies to grant permissions.
AdministratorAccess: Grants the permissions to manage all cloud resources of the destination account.
AliyunHBRRolePolicy: (Recommended) Grants the system permissions required by Cloud Backup.
The AliyunHBRRolePolicy system policy includes the following permissions:
{ "Version": "1", "Statement": [ { "Action": [ "nas:DescribeFileSystems", "nas:CreateMountTargetSpecial", "nas:DeleteMountTargetSpecial", "nas:DescribeMountTargets", "nas:DescribeAccessGroups" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "ecs:RunCommand", "ecs:CreateCommand", "ecs:InvokeCommand", "ecs:DeleteCommand", "ecs:DescribeCommands", "ecs:StopInvocation", "ecs:DescribeInvocationResults", "ecs:DescribeCloudAssistantStatus", "ecs:DescribeInstances", "ecs:DescribeInstanceRamRole", "ecs:DescribeInvocations", "ecs:CreateSnapshotGroup", "ecs:DescribeSnapshotGroups", "ecs:DeleteSnapshotGroup", "ecs:CopySnapshot" ], "Resource": "*", "Effect": "Allow" }, { "Action": "bssapi:QueryAvailableInstances", "Resource": "*", "Effect": "Allow" }, { "Action": [ "ecs:AttachInstanceRamRole", "ecs:DetachInstanceRamRole" ], "Resource": [ "acs:ecs:*:*:instance/*", "acs:ram:*:*:role/aliyunecsaccessinghbrrole" ], "Effect": "Allow" }, { "Action": [ "ram:PassRole", "ram:GetRole", "ram:GetPolicy", "ram:ListPoliciesForRole" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "hcs-sgw:DescribeGateways" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "oss:ListBuckets", "oss:GetBucketInventory", "oss:ListObjects", "oss:HeadBucket", "oss:GetBucket", "oss:GetBucketAcl", "oss:GetBucketLocation", "oss:GetBucketInfo", "oss:PutObject", "oss:CopyObject", "oss:GetObject", "oss:AppendObject", "oss:GetObjectMeta", "oss:PutObjectACL", "oss:GetObjectACL", "oss:PutObjectTagging", "oss:GetObjectTagging", "oss:InitiateMultipartUpload", "oss:UploadPart", "oss:UploadPartCopy", "oss:CompleteMultipartUpload", "oss:AbortMultipartUpload", "oss:ListMultipartUploads", "oss:ListParts" ], "Resource": "*", "Effect": "Allow" }, { "Effect": "Allow", "Action": [ "ots:ListInstance", "ots:GetInstance", "ots:ListTable", "ots:CreateTable", "ots:UpdateTable", "ots:DescribeTable", "ots:BatchWriteRow", "ots:CreateTunnel", "ots:DeleteTunnel", "ots:ListTunnel", "ots:DescribeTunnel", "ots:ConsumeTunnel", "ots:GetRange", "ots:ListStream", "ots:DescribeStream", "ots:CreateIndex", "ots:CreateSearchIndex", "ots:DescribeSearchIndex", "ots:ListSearchIndex" ], "Resource": "*" }, { "Effect": "Allow", "Action": [ "cms:QueryMetricList" ], "Resource": "*" }, { "Action": [ "ecs:DescribeSecurityGroups", "ecs:DescribeImages", "ecs:CreateImage", "ecs:DeleteImage", "ecs:DescribeSnapshots", "ecs:CreateSnapshot", "ecs:DeleteSnapshot", "ecs:DescribeSnapshotLinks", "ecs:DescribeAvailableResource", "ecs:ModifyInstanceAttribute", "ecs:CreateInstance", "ecs:DeleteInstance", "ecs:AllocatePublicIpAddress", "ecs:CreateDisk", "ecs:DescribeDisks", "ecs:AttachDisk", "ecs:DetachDisk", "ecs:DeleteDisk", "ecs:ResetDisk", "ecs:StartInstance", "ecs:StopInstance", "ecs:ReplaceSystemDisk", "ecs:ModifyResourceMeta" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "vpc:DescribeVpcs", "vpc:DescribeVSwitches" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "kms:ListKeys", "kms:ListAliases" ], "Resource": "*", "Effect": "Allow" } ] }
The following example shows how to grant the AliyunHBRRolePolicy permissions to the hbrcrossrole RAM role:
Log on to the Resource Access Management (RAM) console using the account to be backed up.
In the navigation pane on the left, choose .
Find the hbrcrossrole RAM role and go to the role details page.
On the Permissions tab, click Precise Permission.
In the Precise Permission page, set the Policy Type to System Policy, enter AliyunHBRRolePolicy for the Policy Name, and then click OK.
A success message is displayed, confirming the precise authorization. Click Close.
Modify the trust policy of the RAM role.
On the role details page, click the Trust Policy tab.
Click Edit Trust Policy.
On the JSON tab, copy the following code into the text box. Replace destination-account-id with the ID of the management account.
This policy allows the management account to obtain a temporary token through Cloud Backup to operate the resources of the account to be backed up.
{ "Statement": [ { "Action": "sts:AssumeRole", "Effect": "Allow", "Principal": { "RAM": [ "acs:ram::destination-account-id:role/AliyunServiceRoleForHbrCrossAccountBackup" ] } } ], "Version": "1" }Click OK.
Step 3: Add the account to be backed up in the management account
Log on to the Cloud Backup console using a management account.
In the navigation pane on the left, choose Backup > Cross-Account Backup.
On the Cross-Account Backup page, switch to the region that contains the resources you want to back up.
ImportantThe management account must add the account to be backed up in the region where the ECS files, NAS file systems, OSS buckets, Tablestore tables, databases on ECS instances, or ECS instances to be backed up are located. Otherwise, Cloud Backup cannot find the resources to be backed up, which causes backup plans or backup tasks to fail.
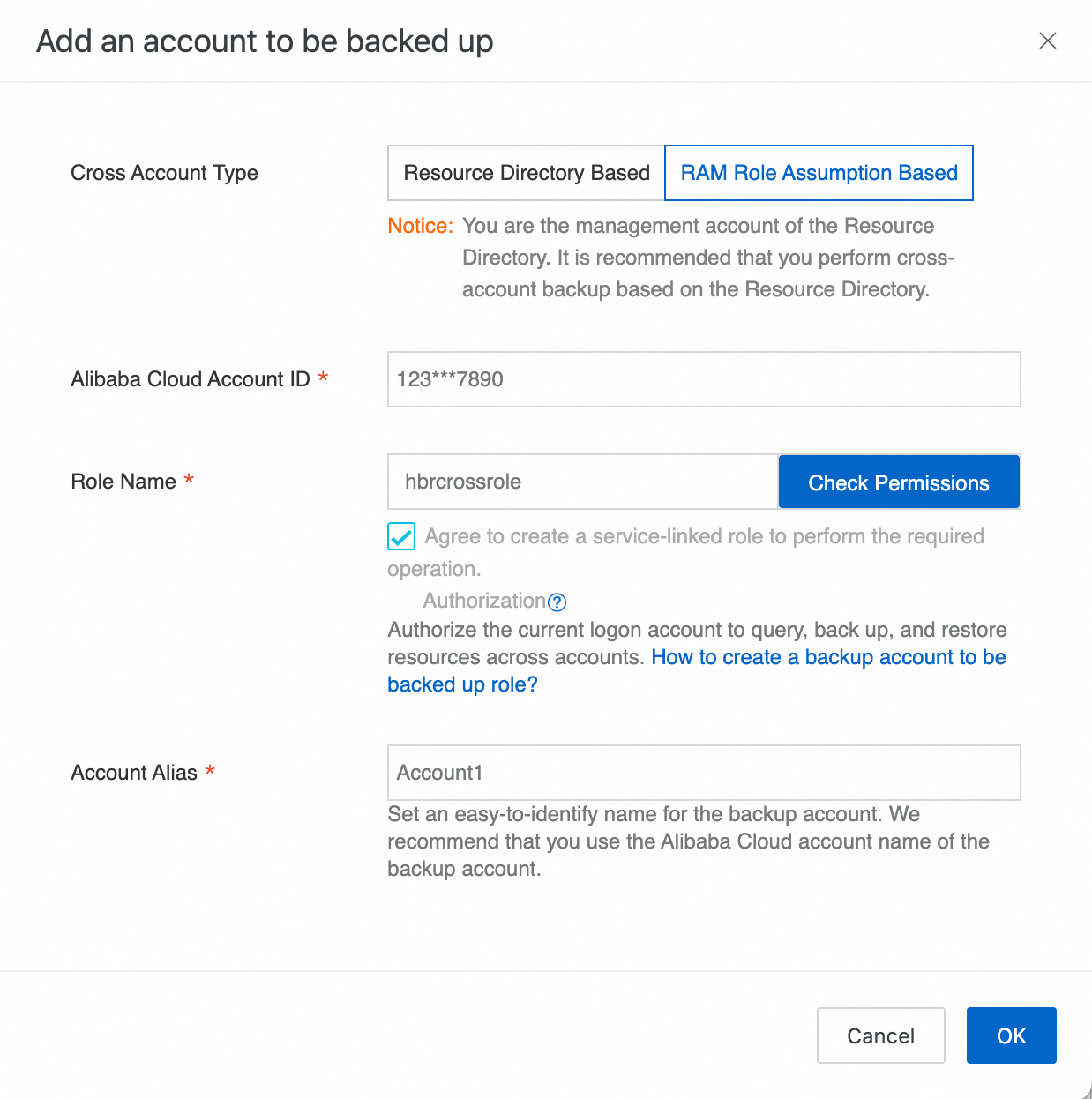
Click Add an account to be backed up. In the displayed panel, configure the following parameters and then click OK.
Parameter
Description
Cross Account Type
Select the option to assume a RAM role. If the backup management account is a Resource Directory Cloud Backup service administrator, see Add accounts from a resource directory.
Alibaba Cloud Account ID
Enter the Alibaba Cloud account ID. In this case, enter the ID of the account to be backed up.
Role Name
Enter the name of the RAM role created in the account to be backed up, such as hbrcrossrole.
When the management account adds an account to be backed up for the first time, you must authorize the service-linked role AliyunServiceRoleForHbrCrossAccountBackup. After the authorization is complete, you do not need to repeat it.
Role name: AliyunServiceRoleForHbrCrossAccountBackup
Access policy: AliyunServiceRolePolicyForHbrCrossAccountBackup
Permission description: Allows the backup service to access the resources of other authorized accounts for cross-account backup and restoration.
ImportantClick Check Permissions to check whether the previous authorization configuration is correct. If an error is reported, check the configuration and try again. If the check is successful, the message You are authorized to access the resources of this role. appears.
Account Alias
Set an easy-to-identify name for the backup account. We recommend using the Alibaba Cloud account name of the account to be backed up.
After the account is added, the account to be backed up appears in the account list.
The following actions affect cross-account authorization and may cause cross-account backups to fail. Proceed with caution:
Deleting the account to be backed up from the cross-account backup list of the management account.
Deleting the AliyunServiceRoleForHbrCrossAccountBackup service-linked role in the management account.
Deleting the RAM role used for cross-account backup in the account to be backed up.
Failing to grant the necessary permissions to the RAM role used for cross-account backup in the account to be backed up.
Existing backups are not affected. If you want to cancel a cross-account backup, see Cancel cross-account backup.
Configure cross-account backup
After you add an account to be backed up, log on to the console with the management account and switch to the account to be backed up from the cross-account list. This lets you configure a cross-account backup for the resources of that account.
Log on to the Cloud Backup console using your management account.
In the top menu bar, select the region where the resources to be backed up are located.
Click Logon Account and select the account to back up.
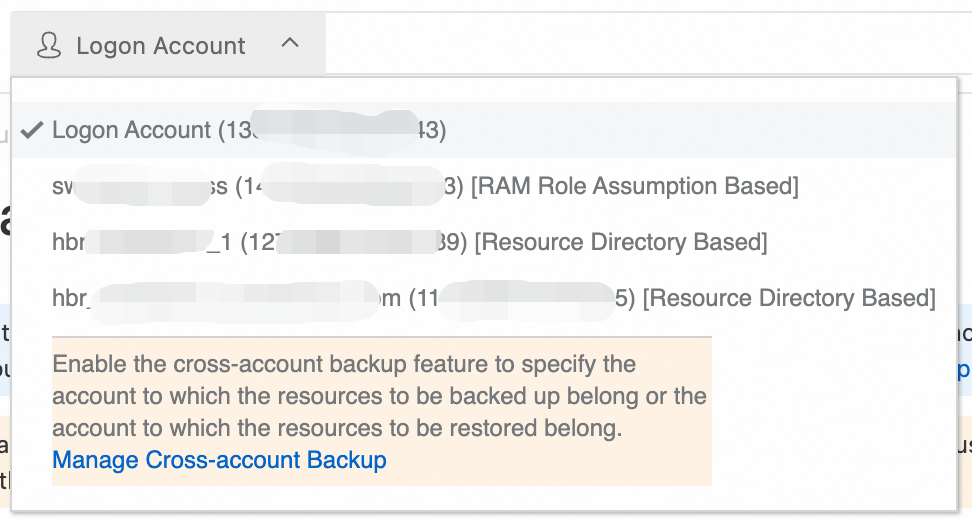
In the navigation pane on the left, select a backup feature to perform a cross-account backup.
ImportantCross-account backup is supported for ECS file backup, ECS instance backup, NAS backup, OSS backup, Tablestore backup, Database Backup, and SAP HANA backup. After you perform a cross-account backup of an ECS instance, you can restore the instance only to the source Alibaba Cloud account. For information about specific supported scenarios, see the Cloud Backup console.
For example, to back up ECS files, first switch to the account where the ECS instance is located in the upper-left corner. Then, select the ECS instance from the instance list. Create a backup policy or select an existing one and attach it to the ECS instance of the account to be backed up to complete the backup plan configuration. After the backup task is complete, the ECS file data of the account to be backed up is backed up to the backup vault of the management account.
ImportantA backup vault can store backup data from different accounts at the same time. A backup policy can be attached to data sources from different accounts at the same time to achieve unified data protection for various types of resources across multiple accounts. Before you configure a cross-account backup plan, make sure that all prerequisites are met.
Cross-account restore
The backup vault of the management account stores the backup data of that account and the accounts to be backed up. You can restore data from any historical backup point in the backup vault to the management account or any account to be backed up as needed. The following example shows how to restore data to an account to be backed up:
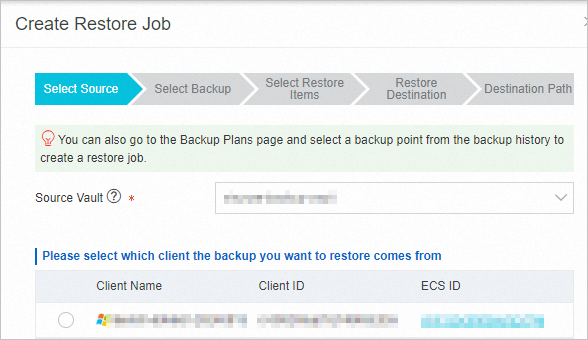
Switch to the destination account to which you want to restore the backup data.
Create a restore job. The steps to create a restore job are the same as the restore steps for each data source.
Restore databases on ECS instances (Restore a MySQL database, Restore an Oracle database, and Restore an SQL Server database)
Best practices
Cross-account type selection: Choose a suitable cross-account configuration method based on your enterprise's account structure. For multi-account scenarios that are not in a resource directory or for cross-enterprise collaboration, configure cross-account backup based on RAM role assumption. For enterprise multi-account architectures that are already in a resource directory, configure cross-account backup based on the resource directory for unified control and permission management.
Least privilege configuration: Use the AliyunHBRRolePolicy system policy instead of AdministratorAccess to avoid security risks from excessive permissions. Grant only the minimum set of permissions required for backup and restore operations. Regularly review the cross-account backup permission configuration and promptly revoke any cross-account access permissions that are no longer needed.
Region planning: Add cross-account configurations based on the region where the resources to be backed up are located to ensure backup performance and data transfer efficiency. Prioritize configuring cross-account backup capabilities in regions with a high concentration of resources.
Cost control: The cross-account backup feature is free of charge. For more information about other fees, see Billing. Plan your backup policies and retention periods to control storage costs.
Cancel cross-account backup
After you cancel a cross-account backup, the management account can no longer back up data from the account to be backed up. Evaluate the impact before you proceed.
If the management account adds an account to be backed up but does not perform any backup or restore operations, no fees are incurred.
After you cancel the cross-account backup feature, the backed-up data is retained in the backup vaults of the management account and can be restored to the current account or other managed accounts. This data continues to consume storage capacity, and Cloud Backup continues to charge you for the storage capacity. For more information about how to stop being billed, see How do I stop being billed for Cloud Backup?. Note that data cannot be recovered after its backup is deleted.
Switch to the account to be backed up. On the corresponding data source page, delete the backup plan, uninstall the backup client (if applicable), unregister the instance, and delete the backup vault. For more information, see How do I stop being billed for Cloud Backup?.
Switch to the management account. On the Cross-Account Backup page in the Cloud Backup console, delete the account to be backed up.
If you configured cross-account backup using Resource Directory, delete the AliyunServiceRoleForHbrRd service-linked role for the account to be backed up.
Log on to the RAM console using the account that you want to back up.
In the navigation pane on the left, choose .
Find the AliyunServiceRoleForHbrRd service-linked role for the account that you want to back up. In the Actions column, click Delete Role and confirm the deletion.
If you configured cross-account backup using RAM role assumption, delete the RAM role created for the account to be backed up.
Log on to the Resource Access Management (RAM) console using the account to be backed up.
In the left navigation pane, choose .
Find the RAM role for the account that you want to back up, such as hbrcrossrole. In the Actions column, click Delete Role and confirm the deletion.
Billing
You are not charged for using the cross-account backup feature of Cloud Backup. However, charges apply to backup and recovery operations, as described in the following table. For more information, see Billing methods and billable items.
Resources in the account to be backed up | Billable items for the management account | Billable items for the account to be backed up |
ECS instance |
|
|
ECS file |
| Fees for resources, such as disks, that are used after you restore from a backup point |
NAS |
|
|
OSS |
|
|
Tablestore |
|
|
Database on ECS |
| Fees for resources, such as disks, that are used after you restore from a backup point |
SAP HANA |
| Fees for resources, such as disks, that are used after you restore from a backup point |
FAQ
Is the cross-account backup feature free?
Yes, the feature is free of charge. Associated costs that are generated during backup and recovery are borne by the management account. However, snapshot service fees for ECS instance backups and OSS request fees are still borne by the account to be backed up. For more information, see Billing.
What is the difference between cross-account backup vault replication and cross-account backup? In what scenarios are they used?
Cross-account replication of backup vaults: The source account has already performed a backup and generated backup data. The source account copies the data from its backup vault to another Alibaba Cloud account. As a result, both accounts store a copy of the backup data to achieve data redundancy or enable cross-account use.
Cross-account backup: The management account uniformly issues backup policies to the accounts to be backed up. The backup data from these accounts is stored in the management account. The management account can use this backup data for on-demand restoration, which achieves unified management of backup data. The accounts to be backed up cannot view or manage the backed-up data.
Both methods are widely used in enterprise data security and compliance scenarios. Both support account-level data isolation and storage for accounts both within and outside a resource directory. Choose a method as needed. You can also combine both methods to achieve both unified management and redundancy of backup data.