By Zikui
Against the backdrop of frequent network security incidents, the construction of security protection has become a top priority in daily development and O&M. ZooKeeper stores sensitive system instance information and configuration data, but traditional usage does not provide ZooKeeper with a mandatory authentication mechanism, so ZooKeeper's internal data may be exposed to cyberspace. If not handled with care, any entity with network access can read and even tamper with the data in ZooKeeper, posing significant security risks.
A company that self-deploys ZooKeeper found that when using ZooKeeper, it neglected to set an appropriate Access Control List (ACL) and identity authentication capability for internally sensitive data. At the same time, it did not disable the "four-character commands" that have potential security risks. As a result, the ZooKeeper data was completely exposed to the network, and anyone who could access this network could connect and operate the data in Zookeeper. In this scenario, due to the significant security risks, the security team required rectification within a specified time.
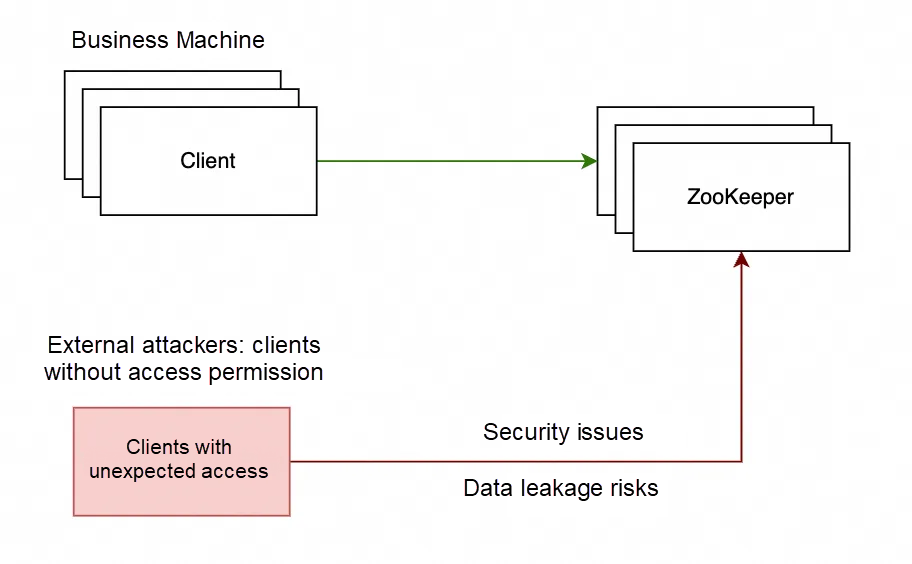
ZooKeeper inherently provides the capabilities of identity authentication and fine-grained ACL. Even with the default configuration, it can support various authentication modes, including Digest, IP, and World. Developers can provide authentication information and set the corresponding ACL for specific Znodes when initializing the connection, which can effectively limit the client access permissions to Znodes. However, although this mechanism is powerful, it is relatively complicated to use in practice. Configuring ACL separately for each Znode means that as the number of Znodes increases, especially when the business logic is complex, the management work will become extremely heavy and error-prone.
ZooKeeper also provides support for SASL (Simple Authentication and Security Layer) authentication mode which can implement an authentication mechanism based on username and password through simple server and client configurations. SASL is a protocol that supports identity authentication and secure data transmission. In Java, there has already been a set of interface implementations based on this protocol. With these interface implementations, ZooKeeper has achieved the SASL authentication function which allows developers to seamlessly integrate with the SASL authentication mechanism by dynamically reading and applying the configure file and enhance the security of ZooKeeper without modifying the existing code.
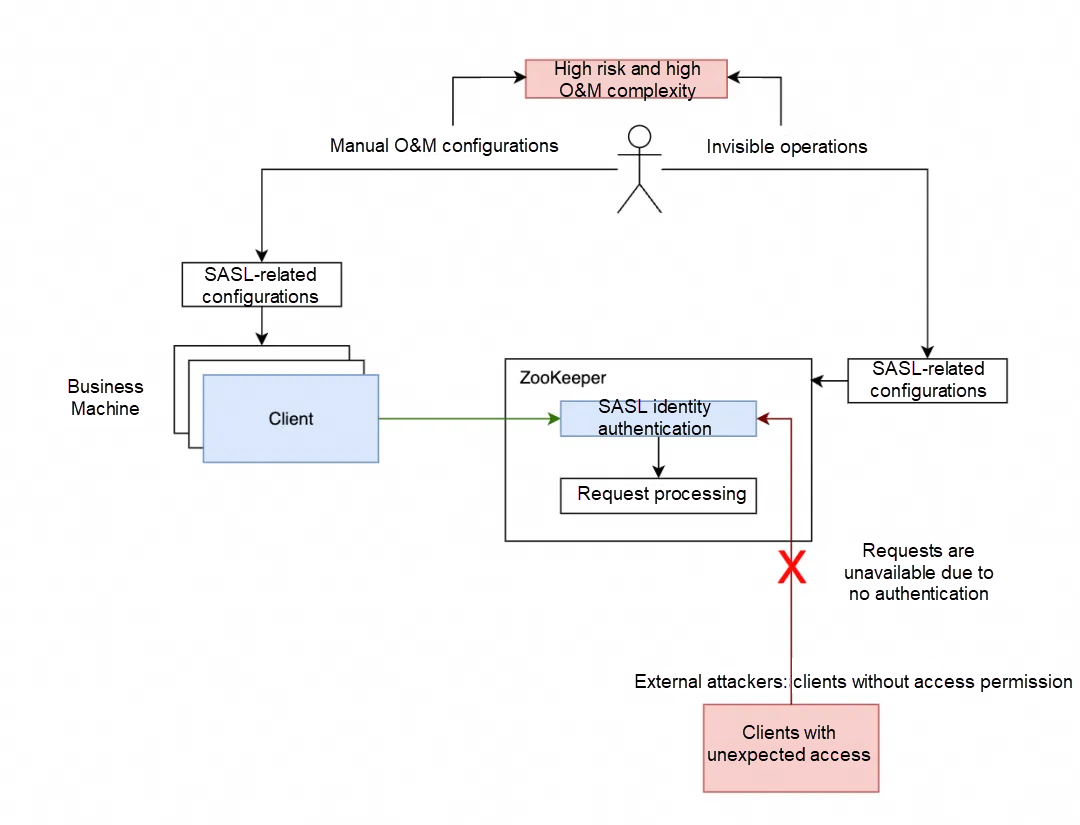
When using the SASL authentication mode, the client and server establish a secure connection through related configurations: only clients with valid authentication information are allowed to connect to the ZooKeeper server and perform data operations. This effectively enhances data security and avoids exposing data in ZooKeeper to the entire network.
However, the actual deployment of the SASL authentication mechanism requires manual server-side configuration work, and its configuration rules are quite complex, which can easily lead to errors during the setup process and cause node exceptions. In addition, the configuration of identity information for SASL authentication also requires continuous manual maintenance, which increases the difficulty and complexity of O&M.
MSE integrates with SASL configuration management capabilities through a standardized process, shielding the complexity of underlying clusters and client configuration. This allows users to access SASL authentication capabilities simply by visualized configurations and client configurations.
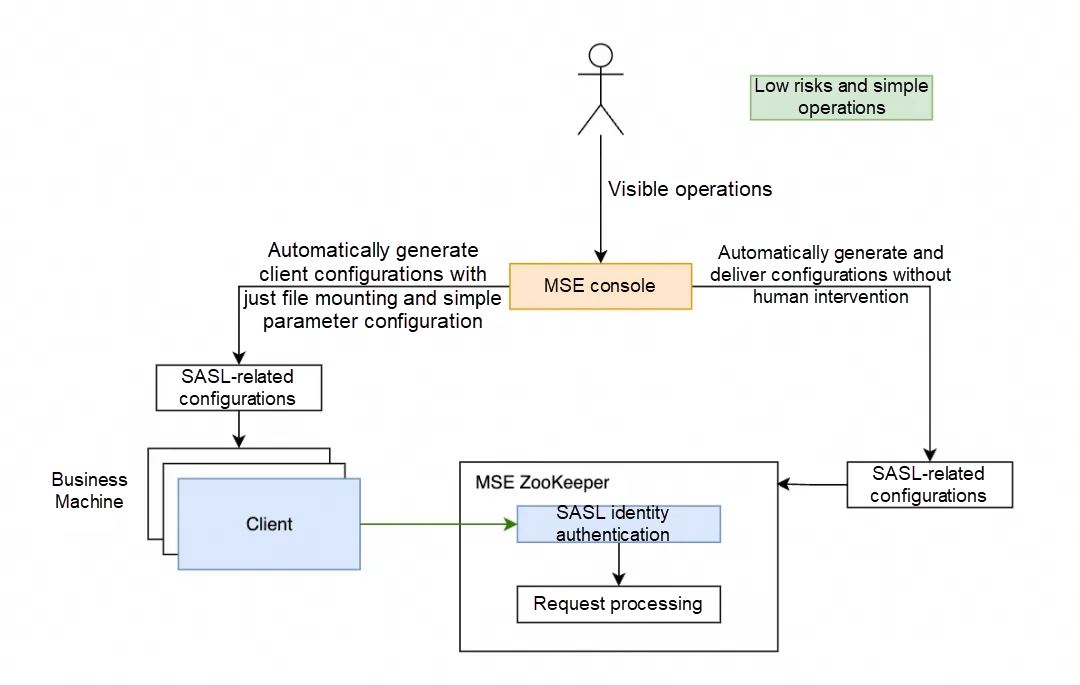
To make it easier for users to utilize the SASL authentication, MSE simplifies the complex server configuration steps and abstracts them into simple visible operations. Users only need to perform a few steps on the MSE console to easily activate the server's SASL authentication feature. At the same time, the MSE console will automatically generate client configurations and guide users to simply set parameters, allowing applications to access SASL capabilities without delving into tedious technical details, thereby enhancing the security capabilities of ZooKeeper.

Configure SASL user information with one click on the MSE console to mask the complex configurations of ZooKeeper

Enable mandatory SASL identity verification and disable four-character commands for sensitive information with one click through parameter configurations
After enabling the mandatory SASL authentication on both the server and client sides, clients without user information configuration or those that have incorrect user information cannot connect to the ZooKeeper Server. At the same time, MSE provides user management and password rotation capabilities, allowing for quick rotation and user deactivation when necessary.
With the above configurations, the cluster will force SASL identity authentication for clients, and clients who can’t pass the authentication cannot initiate requests to the server. This effectively reduces the risk of internal data leakage in the Zookeeper instance and also lowers the risk and complexity of manual operations.
With Dubbo, you can configure SASL identity authentication capabilities in this way. In the usage scenario of Dubbo, it is necessary to ensure that the ZooKeeper dependency version is 3.4.x or above. The configuration process is the same as the general method of using the ZooKeeper client.
By default, all versions of the spring-cloud-starter-zookeeper-discovery dependency used by SpringCloud are supported. The configuration process is the same as the general method of using the ZooKeeper client.
SASL authentication is supported by Zookeeper clients of all Kafka versions. The configuration process is the same as the general method of using the ZooKeeper client.
Big data components that depend on ZooKeeper, such as Hadoop, HBase, and Hive are supported. (The version of ZooKeeper that these components depend on must be 3.4.x or above.)
Access to SASL is supported in other scenarios where ZooKeeper java SDK is used in the application. (The ZooKeeper dependency version is 3.4. X or above.)
As the core middleware of applications, ZooKeeper stores sensitive data in business processes and plays a critical role. Correct and standardized usage is essential to ensure data security. Otherwise, it may cause internal data leakage due to improper operation, which will pose serious security risks. Therefore, in the daily O&M and use of ZooKeeper, a standardized and secure operation is particularly critical to strengthen enterprise security protection and capacities. To achieve this goal, MSE provides a set of standardized processes to help users utilize ZooKeeper more safely and easily. This accelerates the improvement of enterprise security capabilities and minimizes the risks that may occur during the change process.

635 posts | 55 followers
FollowAlibaba Clouder - March 20, 2018
Whybert - January 10, 2019
Apache Flink Community China - January 9, 2020
Alibaba Cloud Community - January 30, 2024
tianyin - November 8, 2019
Alibaba Cloud Native Community - June 29, 2023

635 posts | 55 followers
Follow Secure Access Service Edge
Secure Access Service Edge
An office security management platform that integrates zero trust network access, office data protection, and terminal management.
Learn More Microservices Engine (MSE)
Microservices Engine (MSE)
MSE provides a fully managed registration and configuration center, and gateway and microservices governance capabilities.
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Global Internet Access Solution
Global Internet Access Solution
Migrate your Internet Data Center’s (IDC) Internet gateway to the cloud securely through Alibaba Cloud’s high-quality Internet bandwidth and premium Mainland China route.
Learn MoreMore Posts by Alibaba Cloud Native Community