By Shantanu Kaushik
In Part 1 of this 2-part series, we discussed why identity solutions are essential for organizations to begin their cloud-based setup. Then, we explained how Alibaba Cloud introduced the Identity as a Service (IDaaS) platform and how it solves the most complex identity and role management within an organization.
In this article, we will discuss the different use cases for the Alibaba Cloud IDaaS service. We will also shed some light on integration scenarios between Alibaba Cloud RAM and IDaaS.
An organization has a multi-domain authorization system for its applications. Every time a request is processed, extra resources are used for managing identity and access. This extra IT management cost can be saved by applying a centralized authority management system with Alibaba Cloud IDaaS.
The organization would be facing issues with improper authorization controls every time there is a structural change within the organization. These improper authorization scenarios can lead the organization towards impending doom. How? Data leakage or sensitive data leakage can cause irreparable harm to the organization's daily operations and reputation.
Let's analyze the architecture used by Alibaba Cloud IDaaS to manage operations in a centralized manner:
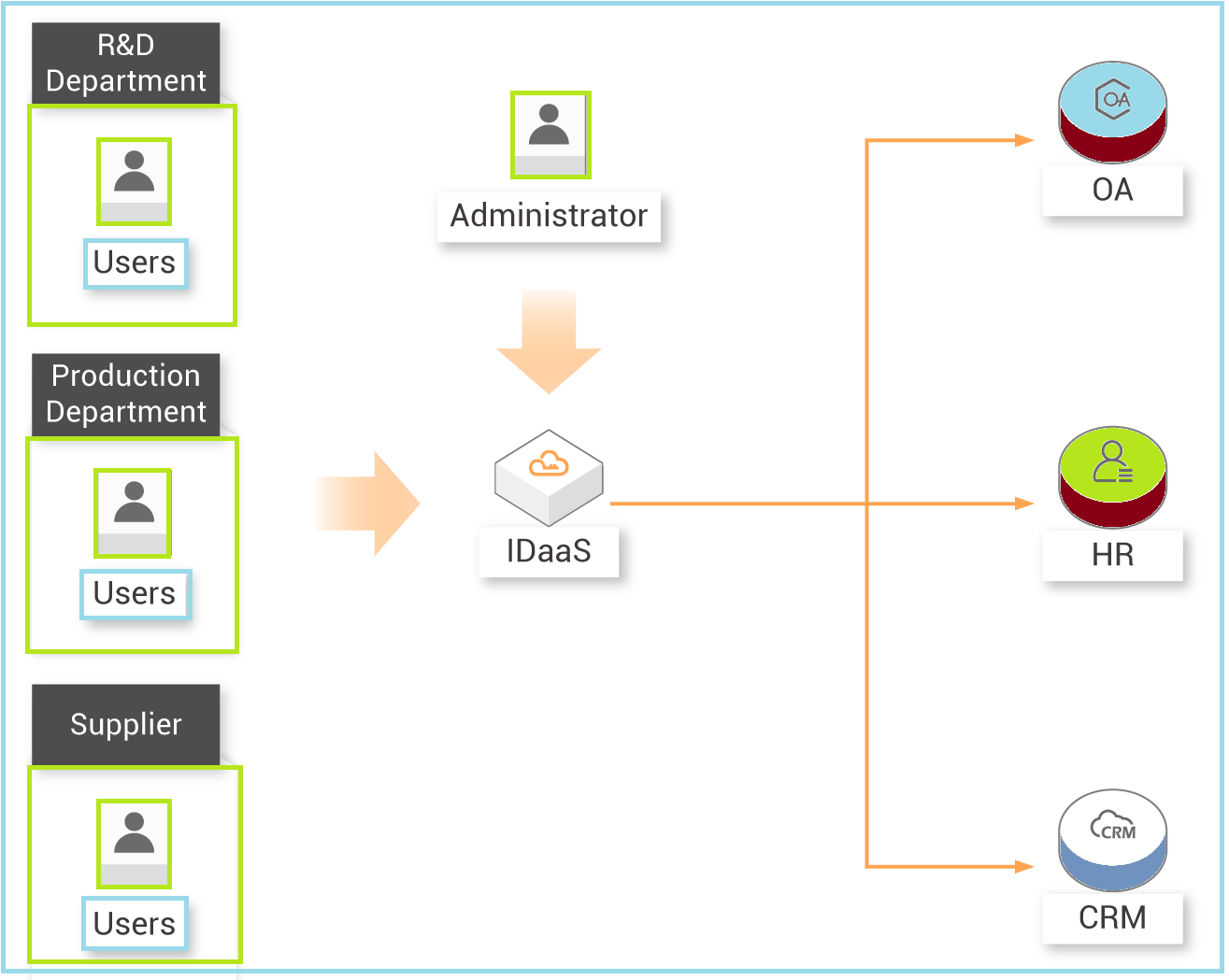
Alibaba Cloud IDaaS enables one-stop management for users. You can create or make changes to a user in the central directory maintained by IDaaS, and it will take effect globally. In the example above, different departments (user groups) have been defined, their roles and responsibilities are different, and they cannot overlap unless they are configured through IDaaS. Every user group and administrator can access IDaaS. This enables access to different systems within the organization, clearly defined and managed using IDaaS.
An enterprise solution is made up of (n) number of systems, and multiple roles with multiple credentials can make it very hard for a user to manage everything effectively. Remembering all those passwords and addresses can be a pain. The focus shifts from productivity during workloads to remembering credentials.
Password recovery scenarios, easy to remember password strings, or repetition of passwords across systems can lead to a data breach or a user-block scenario. This is important for security and enterprise system efficiency.
Let's take a look at how Alibaba Cloud IDaaS can help enterprises overcome these issues by applying single sign-on (SSO):
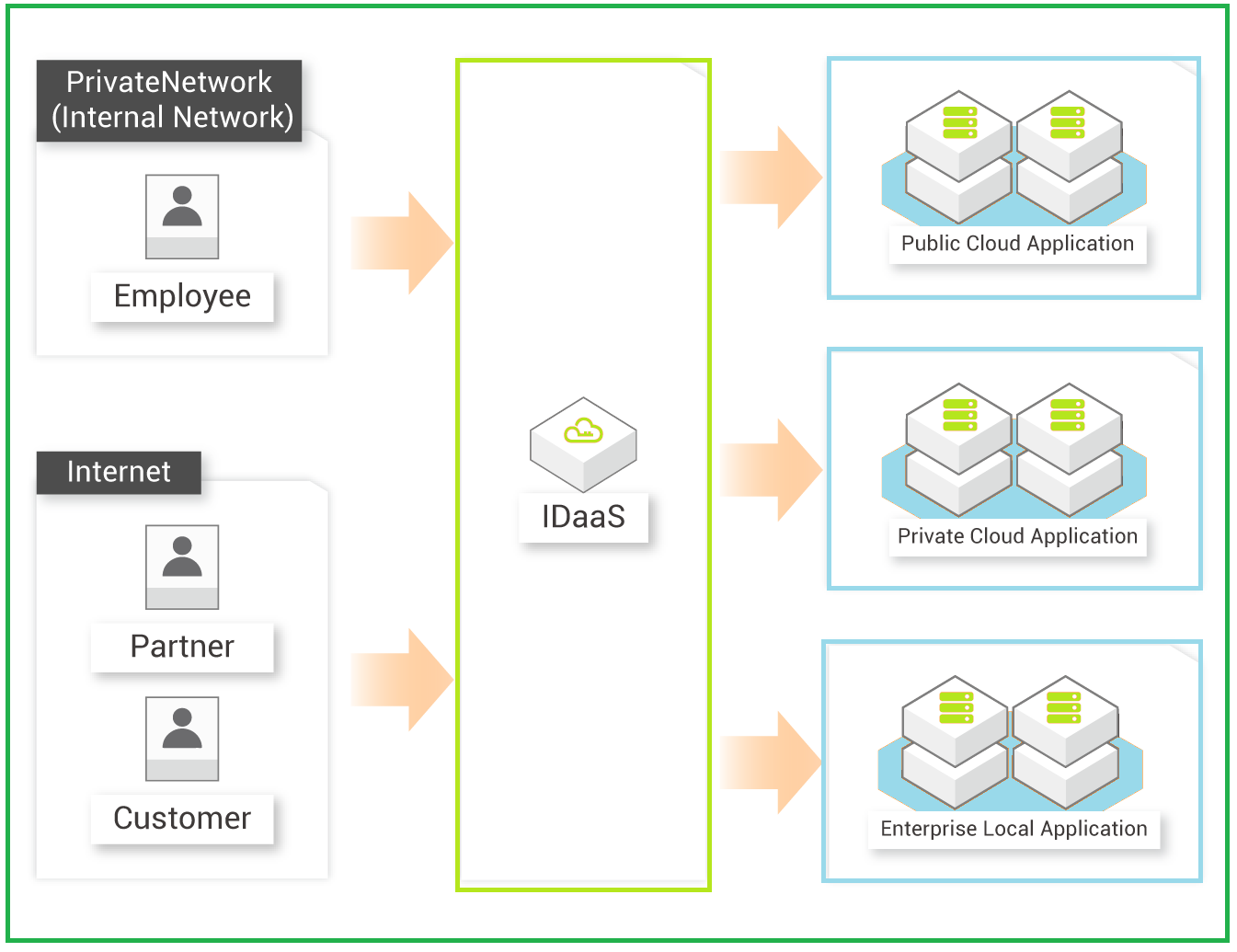
Alibaba Cloud IDaaS enables a seamless identity-based authentication using a single sign-on system. This system can incorporate any authentication system. This enables users to gain access to all authorized applications with one click.
An enterprise in today's world needs to configure its system ends to maintain security and authorization. The most important thing to remember is an organization cannot only have internal members accessing the system. External users and customers will get access to the information within your organization at some point.
Vulnerabilities in the system can cause enterprises to come under massive security risks. This can expose the database and applications to cyber-attacks. This sort of issue isn't common and can cause irreversible economic issues.
Alibaba Cloud IDaaS helps you implement multi-factor authentication (MFA) in a more unified manner to maintain an added security layer for data protection.
Let's take a look at the architectural flow of this scenario on the chart below:
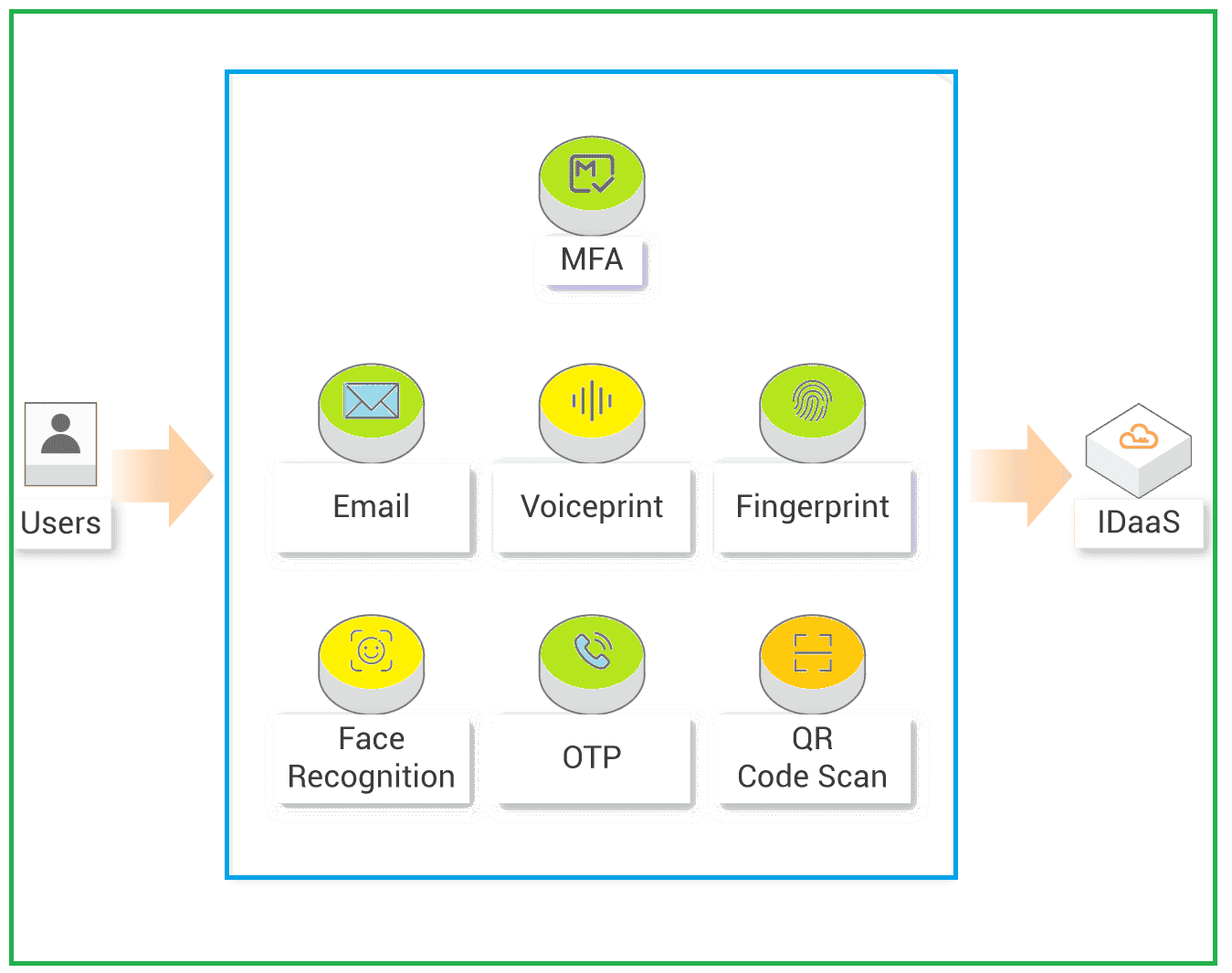
Alibaba Cloud IDaaS can configure authentication factors in a centralized manner. It overcomes the multiple password scenario and implements systems, such as dynamic tokens, face, fingerprint, retinal scan, and other biometric authentication methods. It can also implement QR scanning, SMS auth, tokens, and certificates for authentication.
At the same time, IDaaS allows for other third-party authentication systems to be integrated. Developers building a scenario from the core up can use the IDaaS API to enable support for other applications using IDaaS identity and authentication capabilities.
Enterprise-level directory services account for a large amount of operation and maintenance (O&M) resources. There is a recurring demand for O&M while enabling capacity expansion for directory services. The scenario above and account management scenarios for new additions can incur more O&M and R&D costs.
However, this isn't the only problem. The development isolation causes severe issues with the information system. Multiple application systems within an enterprise can throw data and authorization demands off during the employee onboarding or relieving process.
Alibaba Cloud IDaaS provides a solution to overcome this scenario on the chart below:
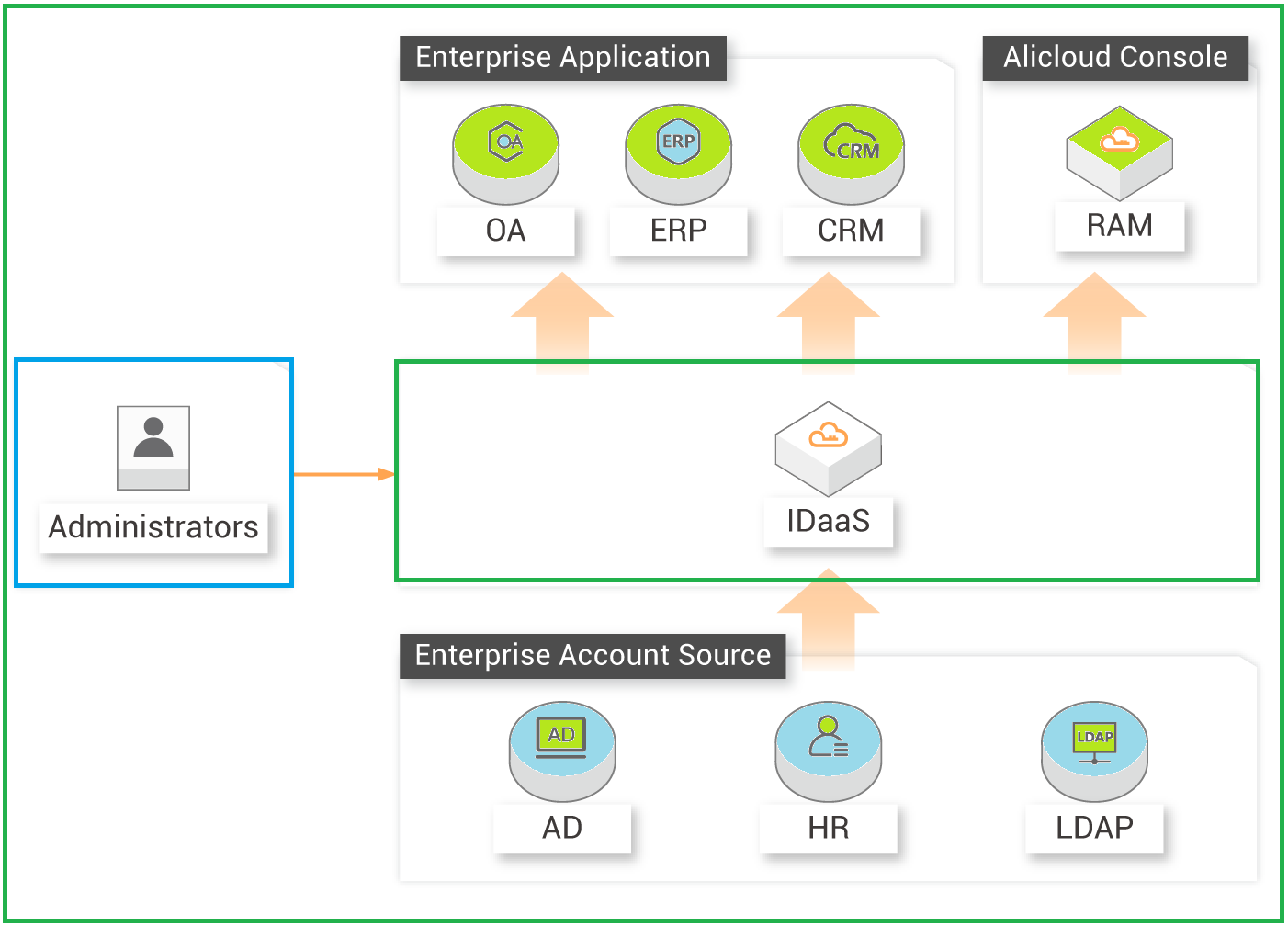
Alibaba Cloud IDaaS enables a unified user-directory system for easy user authentication and management across multiple application systems within an enterprise. It provides unique user identities to enable an enterprise-based information construction scenario.
Alibaba Cloud IDaaS provides automatic updates with synchronized downstream to manage an account lifecycle in a centralized manner with a permanent online system that provides unlimited expansion capabilities. IDaaS enables a unified account to provide features like:
Let's take a look at the information flow architecture for this use case scenario on the chart below:
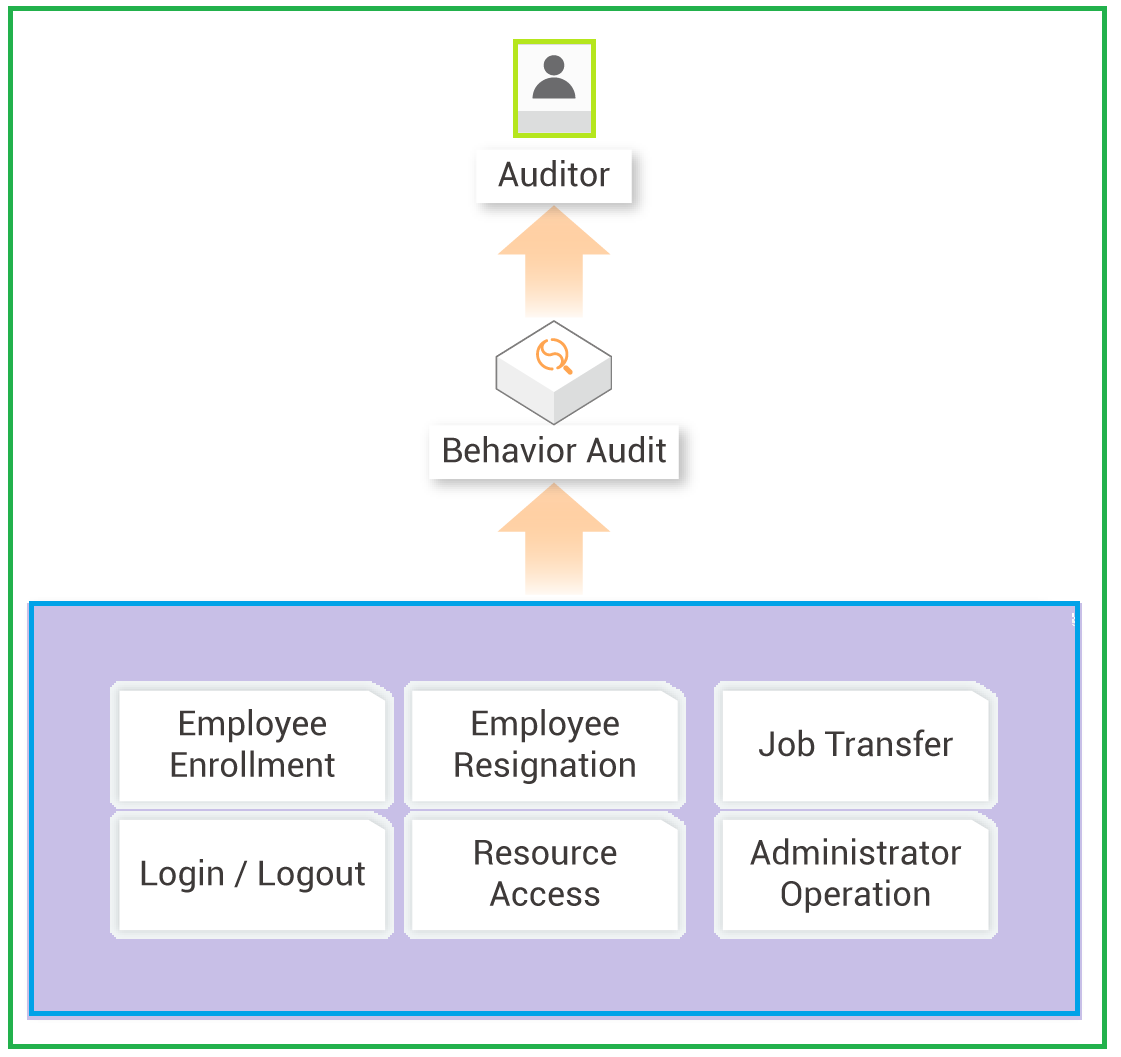
Enterprises often face challenges while trying to set up a log-based auditing system. Traditionally, the logging system presented tedious management approaches and caused more issues than it solved at the enterprise-level. It also incurred large management costs.
Alibaba Cloud IDaaS enables a centralized system to set up an identification system to detect any unauthorized access or any potential risk by analyzing the user-behavior logs by log-auditing.
Alibaba Cloud IDaaS helps enterprises set up systems that record all user behaviors in detail along with administrator operations. These visual reports can be accessed by managers to maintain and keep track of corporate digital assets.
Alibaba Cloud IDaaS helps you integrate RAM features, such as Account Management, Permission Management, Authentication Management, and audits for logon.
The integration of features from RAM and IDaaS enables the enterprises that have shifted their applications to the cloud and use Alibaba Cloud RAM to manage cloud resources. This integration scenario overcomes issues with account lifecycle management for individual systems, helps maintain separate users and user groups for individual systems, and helps employees, administrators, and managers with their credentials issues.
Facilities provided by RAM Integration with IDaaS:
1. Single Sign-On (SSO)
RAM user roles and users are associated with IDaaS to provide the SSO service.
2. AD/LDAP User Data Provisioning
IDaaS provides this functionality to RAM and enables the system to access AD or LDAP data.
3. QR Code Access
The integration of RAM with IDaaS enables the functionality for users to logon to RAM by scanning QR codes with AD or DingTalk accounts.
4. RAM Access Logs Auditing
As we discussed above, IDaaS provides a seamless user behavior log audit feature. Integration organizations using Alibaba Cloud RAM for identity and access control can leverage the behavior log audit for RAM users.
Identity is essential for an organization to work and flourish. Alibaba Cloud has forwarded solutions, such as Alibaba Cloud Resource and Access Management (RAM) and the Identity as a Service (IDaaS). These services help organizations take care of issues with access, authorization, and authentication using centralized management and single sign-on systems that work flawlessly to provide a seamless user experience.

2,593 posts | 793 followers
FollowAlibaba Clouder - January 29, 2021
5544031433091282 - April 8, 2025
Alibaba Clouder - April 2, 2021
CloudSecurity - December 9, 2025
Alibaba Clouder - September 10, 2020
Alibaba Cloud Community - September 27, 2021

2,593 posts | 793 followers
Follow Bastionhost
Bastionhost
A unified, efficient, and secure platform that provides cloud-based O&M, access control, and operation audit.
Learn More Managed Service for Grafana
Managed Service for Grafana
Managed Service for Grafana displays a large amount of data in real time to provide an overview of business and O&M monitoring.
Learn More IDaaS
IDaaS
Make identity management a painless experience and eliminate Identity Silos
Learn More RAM(Resource Access Management)
RAM(Resource Access Management)
Secure your cloud resources with Resource Access Management to define fine-grained access permissions for users and groups
Learn MoreMore Posts by Alibaba Clouder