By Shantanu Kaushik
The traditional IT practices led us towards the path of derived evolution. However, certain practices had to be migrated to evolve and account for the necessary paradigm shifts.
These paradigm happened when developers and other IT teams found solutions to the challenges presented by the changing times and technology. Some ideas include strong security and authorization services that ensure any system can work after the credentials are applied to it. Collectively, these ideas are known as access control. Identity Management has solved a lot of clogs in the chain of productivity due to unauthorized access and breach violations.
Traditionally, any breach was handled using network-layer control, and using tools to ward-off such malicious attempts is a task that still requires a lot of expertise to handle. While cloud computing has led to revolutionary practices in security and authorization, identity and access management is something that every organization thrives on.
Jack of all trades, but a master of none is a saying to avoid with a cloud data center or any data center. If one team can execute tasks for everybody, we would need a hierarchy. Hierarchy is the most important aspect of any organization of life scenario, especially when you want to maintain decorum in services and require results. Technologists can relate it to the OSI model; every layer has a task that helps it work efficiently.
Identity and Access Management works on the same principle. A user of a user group could be tasked to ensure that resources are properly managed for the development team to leverage. Here, a user or user group from the operations team will get credentials that will enable them to manage the operations tasked to them. They cannot execute anything else, only what the system has granted them.
Identity as a Service (IDaaS) is a term that defines cloud-based identity and access management services. IDaaS is a solution that helps enterprises control resource access by defining roles and assigning access levels to users and user groups. Let’s take a look at how the cloud-based identity security system works using Alibaba Cloud IDaaS on the chart below:
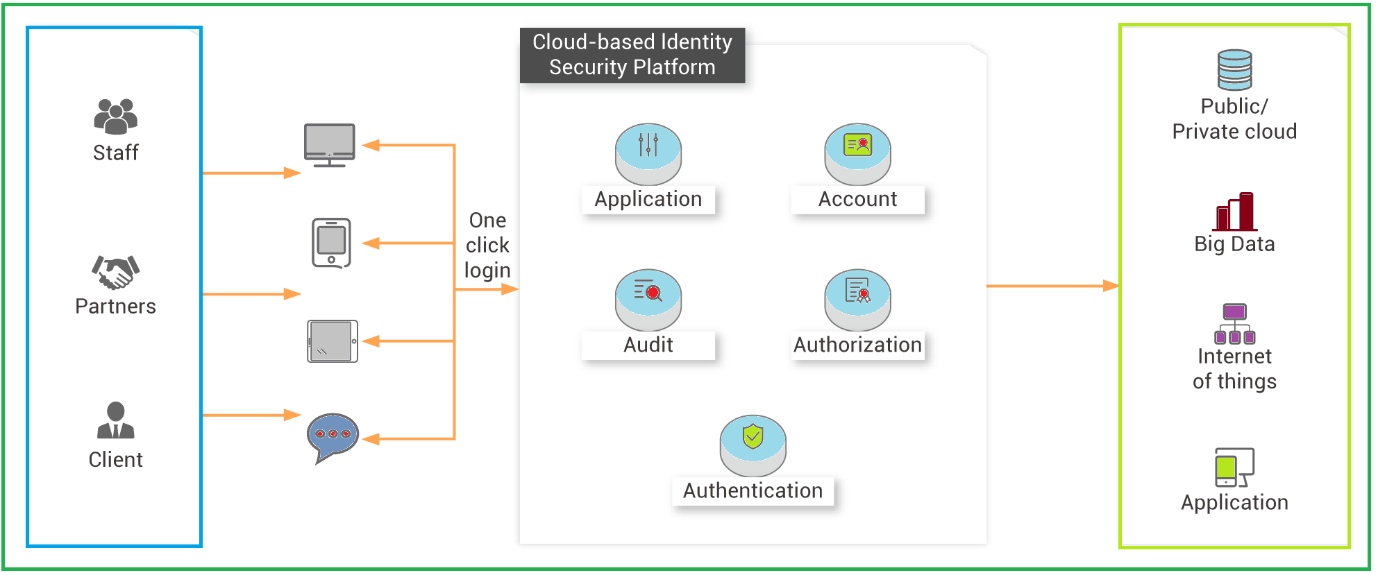
Alibaba Cloud introduced the Identity as a Service (IDaaS) as a centralized platform that helps you work with Identity Management, Permission Management, and Application Management.
Alibaba Cloud IDaaS helps you access all applications and services with one account. You can use the IDaaS service to manage identities for third-party SaaS systems, business systems, and office administration.
Alibaba Cloud Identity as a Service (IDaaS) works with the 5A’s:
IDaaS gives enterprises unique user identities to use enterprise information construction and manage the complete account lifecycle.
As a centralized service, you can easily verify user identity, enable support for third-party authentication sources, and configure multi-factor authentication (MFA).
The accessibility range of a user can be easily managed depending on their department or role. Since the system is centrally-managed, granting or revoking authorization is a one-click process.
Integrated services, such as single sign-on, access control, and application portals, can be accessed by the users when using any application or devices, such as desktop applications, IoT devices, mobile applications, or web applications.
You can easily use the Alibaba Cloud IDaaS service to trace user behavior and generate a real-time audit report that can be accessed by the administrators.
Some of the most important benefits of IDaaS are listed below:
Alibaba Cloud IDaaS helps you connect identities from sources across cloud platforms, making it an efficient choice in a multi-cloud and hybrid cloud setup. You can connect Alibaba Cloud to provide identity management services to other cloud platforms and private environments with IDaaS.
IDaaS utilizes one-account-access-all, which enables a centralized identity management solution that removes multiple ID-based silos decrease complexities make the process easier. Enterprise-grade security based on identity management helps you drastically improve management efficiency.
Alibaba Cloud IDaaS supports single sign-on (SSO) protocols that allow organizations to connect their services using one account. The password system is eliminated after using SSO, eliminating various security risks related to passwords.
1. Data Initialization
This step includes migrating your identity data to the Alibaba Cloud IDaaS service. IDaaS supports data imports from Excel, SCIM, and AD/LDAP.
2. Application Integration
This step includes connecting your current applications to the IDaaS service and starting with the single sign-on (SSO) integration process.
3. Provisioning
This step includes provisioning from and to the IDaaS service, including support for some third-party SaaS applications.
4. Permission Setup
This step involves defining the roles and permissions set up for these roles within IDaaS.
5. Authentication Integration
This step includes the integration of authentication methods to IDaaS. These methods may include biometrics, SMS auth, social logins, AD credentials, and other external authentication mediums.
Identity management is the first step of a journey towards implementing the cloud in your business scenario. Alibaba Cloud IDaaS solves some of the biggest woes of cloud-based identity services and provides a unified platform for centralized management and one-stop identification integration.
As a close relative of Alibaba Cloud RAM, IDaaS also showcases some fascinating integration scenarios with RAM.
In the next article of this two-part series, we will explain all of the use case scenarios associated with Alibaba Cloud IDaaS and the integration scenarios between IDaaS and RAM.
Securing Environments with IDaaS – Part 2: Industry-Based Use Cases and Integration

2,593 posts | 793 followers
FollowAlibaba Clouder - January 29, 2021
Alibaba Clouder - April 2, 2021
CloudSecurity - December 9, 2025
5544031433091282 - April 8, 2025
Alibaba Cloud Community - September 27, 2021
Alibaba Clouder - March 26, 2020

2,593 posts | 793 followers
Follow Bastionhost
Bastionhost
A unified, efficient, and secure platform that provides cloud-based O&M, access control, and operation audit.
Learn More Managed Service for Grafana
Managed Service for Grafana
Managed Service for Grafana displays a large amount of data in real time to provide an overview of business and O&M monitoring.
Learn More Hybrid Cloud Solution
Hybrid Cloud Solution
Highly reliable and secure deployment solutions for enterprises to fully experience the unique benefits of the hybrid cloud
Learn More Networking Overview
Networking Overview
Connect your business globally with our stable network anytime anywhere.
Learn MoreMore Posts by Alibaba Clouder