By Shantanu Kaushik
DevOps and innovation are like _Corn and Peas_. I know this is supposed to be a tech article, but let's use an example that is a little diverse. They go very well together for some, but depending on your taste pallet, you might or might not be very enthusiastic about it. A lot depends on what your requirement is as well as acquired tastes.
Security with DevOps makes a great combination. It is like Corn and Peas for me, but it could be Steak and Potatoes for you. It all depends on what you are looking for and what your requirement is. Alibaba Cloud has done something very similar. The product range they have has been carefully tailored to suit different target audiences. These solutions have gone through years of growth.
Products like the Elastic Compute Service and the Simple Application Server have been tried and tested over the years. These seasoned products have made an impact on the technology industry practices. Following the same trend, when DevOps came into practice, there was a specific need for products like Terraform that is an Infrastructure as Code (IAC) product or the need for containers with Kubernetes (ACK).
Just like Corn and Peas_, one can think about introducing _mushrooms or cheese into the mix, right? This is what happened with Security in DevOps.
DevOps has agility and responsiveness built into its DNA, but with that, if you can integrate security, that will count for a full lifecycle with a secured solution altogether. Previously, security was a concern for the final stages of deployment. For projects that cover months in development and only reach the deployment stage after a considerable period of time, it works. However, with faster production and automation, product delivery cycles have accelerated considerably. On top of that, if you are using microservices or APIs, the development teams can reach a product delivery faster.
With rapid delivery cycles, security becomes a concern. An outdated security practice can jeopardize the most effective DevOps solutions. Now, with DevSecOps, security has been outlined as a shared responsibility of teams and has to be integrated from end-to-end. Hence, DevSecOps works with a built-in security system right into the DevOps solution.
Alongside everything else within the DevOps foundation, DevSecOps also focuses on infrastructure and application security from the foundation level. Automation is a primary checkpoint while implementing DevSecOps. It is mandatory for information security measures to be replaced with automated processes that are more scalable and maintainable.
The selection of proper automation tools and automating some of the security measures with DevOps is equally important. With automation at the Continuous Integration phase and proper tool section, you can have a good DevOps practice at your disposal.
It is of the utmost importance that you work with security from the ground level up. Security has to be given priority from the initial phase. That has to be outlined and defined as Built-in Security and not _Security as a perimeter or practice_. DevSecOps makes automation a necessity. If you wish to maintain QA, you need to replace the manual testing with an automated approach.
Alibaba Cloud Container Service for Kubernetes (ACK) adheres to the security standards set forth and has introduced DevSecOps without using the coined term. These security practices enhance the scalability and dynamic infrastructure that containers already provide.
DevSecOps introduced the end-to-end security concept that has to be followed throughout the software development lifecycle (SDLC.) These concepts are straightforward and point-out the need for integrated continuous security. DevSecOps introduces a new cultural change for organizations, just as DevOps did when it initially started its ascension. With Containers and Microservices, Alibaba Cloud provides organizations and businesses with tools and support to build agile DevOps solutions. When it comes to DevSecOps, Alibaba Cloud has the infrastructure and tools to support it, but it all depends on the developer to leverage these solutions to build a better and secure system.
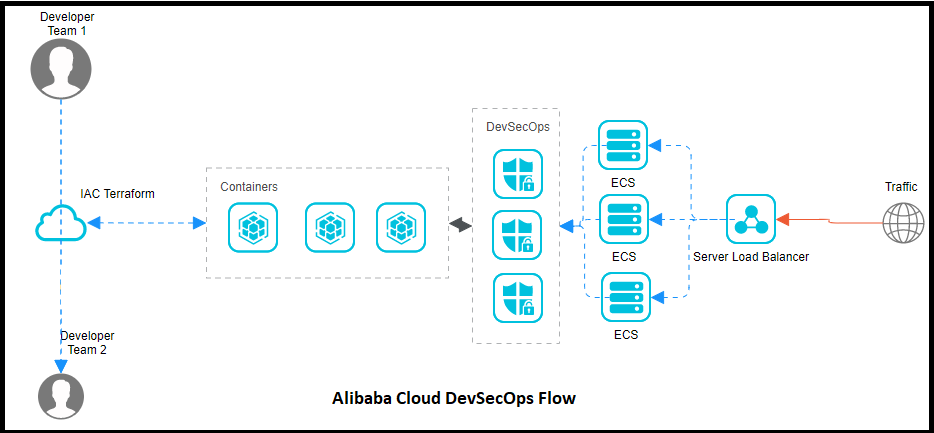
Protecting your environment is the first step. Make sure you have threat modeling exercises in place so you can discover any threats and/or vulnerabilities quickly with a patch or solution in works for a more secure and efficient system.
Automation with containers and microservices should be done with access management. Automate only where necessary, no less and no more. Less automation will slow down the system and excessive automation can plug the system with indeterminant issues.
Centralized access and identity management is a mandatory practice to secure microservices that manages them at different cycle points in your SDLC. Alibaba Cloud Resource Access Management (RAM) comes into play at this stage and increases the authorization standards at multiple-points in the system.
Alibaba Cloud API Gateway provides secure APIs and increases authentication standards. This increases security and decreases attacks.
Containers that are running microservices should be isolated. When a microservice isn't being used, it should not be connected to the network since attackers can leverage an idle connection and attack your service. Container orchestration and security integration along with security scanners are practices to be followed for attaining better authorization and security standards.
Whether it is the continuous integration stage, the release stage, or the deployment stage, every stage should be equipped with automated security testing capability. Along with that, configuration management capabilities should also be tested for any mismanagement issues.
DevOps on Alibaba Cloud presents developers with industry-based tools and practices, which ensures that your infrastructure or environment is based on current trends and practices. Security considerations play an important role in achieving stability and agility in your DevOps implementation. It is recommended to use an IAC product like Terraform and products like API Gateway. If you are implementing with Kubernetes, Alibaba Cloud's Container Service for Kubernetes (ACK) is an excellent option. These products are already in place and are backed by Alibaba Cloud. Leveraging their true potential will simplify the DevSecOps implementation and will ensure a more secure and efficient system. Make sure to choose wisely and evolve with the evolution of DevSecOps.
The views expressed herein are for reference only and don't necessarily represent the official views of Alibaba Cloud.
DevOps Implementation and Testing Strategy: Best Practices and Tools

2,593 posts | 793 followers
FollowAlibaba Clouder - December 31, 2020
Alibaba Clouder - October 1, 2020
Alibaba Clouder - July 24, 2018
Farruh - January 12, 2024
Neel_Shah - June 24, 2025
Alibaba Clouder - May 23, 2018

2,593 posts | 793 followers
Follow Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Robotic Process Automation (RPA)
Robotic Process Automation (RPA)
Robotic Process Automation (RPA) allows you to automate repetitive tasks and integrate business rules and decisions into processes.
Learn More Cloud-Native Applications Management Solution
Cloud-Native Applications Management Solution
Accelerate and secure the development, deployment, and management of containerized applications cost-effectively.
Learn MoreMore Posts by Alibaba Clouder