When you distribute static resources, such as images, audio, video, and documents from Object Storage Service (OSS), configure ESA acceleration to improve access speed, reduce network latency, and lower traffic costs.
Use cases
A website uses Object Storage Service (OSS) to store static resources, such as images and videos, primarily for users outside the Chinese mainland. As the user base grows, users experience slower response times for file downloads and resource loading. Geographically distant users experience high latency. To address this issue, the website can use ESA to accelerate access to OSS. This solution provides fast resource access at a minimal cost and includes security protection features, such as Web Application Firewall (WAF) and Anti-DDoS, to enhance the overall user experience and website security.
Solution
Store static resources in a private OSS bucket and use ESA to accelerate access. When a client sends a request, ESA automatically selects the fastest point of presence (POP) based on the domain name. If the POP has the requested resource in its cache, it returns the resource directly to the user. Otherwise, the POP retrieves the resource from the origin server, returns it to the user, and caches it for subsequent requests.

Before you start
When you use this feature for the first time, enable the default access policy. After the policy is enabled, ESA obtains read-only access permissions to all OSS buckets under the same account. These permissions are granted using temporary tokens from the Security Token Service (STS) and do not allow write or delete operations, such as PUT.
If you choose to configure a permanent security token, you must restrict the token's permissions to prevent write or delete operations, such as PUT, on OSS buckets when you request the token. For more information about how to configure access permissions for a RAM user, see Mitigate risks of unauthorized access due to leaked credentials.
After you grant authorization and enable the private bucket origin fetch feature for an accelerated domain name, you can use that accelerated domain name to access all resources in the private bucket. If the content in the private bucket is not suitable for acceleration, do not authorize or enable this feature.
If your website is at risk of attacks, purchase an Anti-DDoS service and be cautious when you grant authorization or enable the private bucket origin fetch feature.
The ESA feature for origin fetch from a private OSS bucket conflicts with the default index page configuration for static website hosting on OSS. To use both features at the same time, see Resolve the 'You are forbidden to list buckets' error with private OSS bucket origin fetch.
After you enable the private bucket origin fetch feature, the ESA POP adds a header named "Authorization" to the origin request. The value of this header is the authentication signature for the private OSS bucket. Note that a single origin request to OSS cannot include signatures in both the header and the URL request parameters. Otherwise, OSS authentication fails.
Prerequisites
You have registered an Alibaba Cloud account and created an Alibaba Cloud account.
You have activated OSS and stored static resources in a private OSS bucket.
You have registered a domain name.
If the acceleration area includes the Chinese mainland, apply for an ICP filing for the domain name.
Connecting to ESA
After you add a site's primary domain name, such as example.com, to ESA, you can accelerate and manage the primary domain name and all its subdomains.
Step 1: Add a site
In the ESA console, choose Websites and click Add Website.
On the Enter Website page, enter the primary domain name of the site that you want to add, such as
example.com, and click Next.

For Location , select Global (Excluding the Chinese Mainland). For DNS Setup , select CNAME. Then, click Next.
Step 2: Verify domain name ownership
When you add a domain name to ESA for the first time, verify the ownership of the domain name.
On the Overview page, copy the Record Type , Hostname , and Record Value generated by ESA.

Log on to the Alibaba Cloud DNS console. On the Public Zone page, find the target domain name, such as
example.com, and click Settings in the Actions column.Click Add Record. Enter the parameters based on the information that you copied in Step 1. Then, click OK.
Record Type :
TXTHostname :
_esaauthQuery Source : Default
Record Value :
verify_3***9e1TTL : 10 (Recommended)
Return to the ESA console. On the overview page of the target site, click Verify.
If the system displays Verification Successful , the verification is successful.
Add and resolve a domain name
To enable acceleration, add the accelerated domain name to ESA and then add a DNS record for the domain name on the Alibaba Cloud DNS platform. This topic uses the domain name images.example.com and the private OSS bucket endpoint bucket***aliyuncs.com as an example. You must replace the example domain name and bucket endpoint with your actual domain name and endpoint.
Step 1: Add a domain name in ESA
You can add a DNS record in the ESA console to configure information, such as the accelerated domain name and the private OSS bucket endpoint, and to obtain a CNAME value.
In the ESA console, choose Websites. In the Website column, click the target site.
In the navigation pane on the left, select DNS > Records. Click Add Record. Configure the record parameters as described below and click Next.
Record Type : CNAME.
Hostname :
images.Proxy Status : Turn on this switch to enable proxy acceleration.
Record Value : Select OSS.
Access Type : Select Private Access (Same-account).
Authorization : By default, access to private OSS buckets under the same account is automatically granted.
OSS Bucket : Select
bucket***aliyuncs.com.TTL : The default value is Auto.
Select Image/Video and click OK.
In the CNAME Configuration Guide , copy the Hostname and Record Value. Then, go to the Alibaba Cloud DNS console to add a CNAME record.
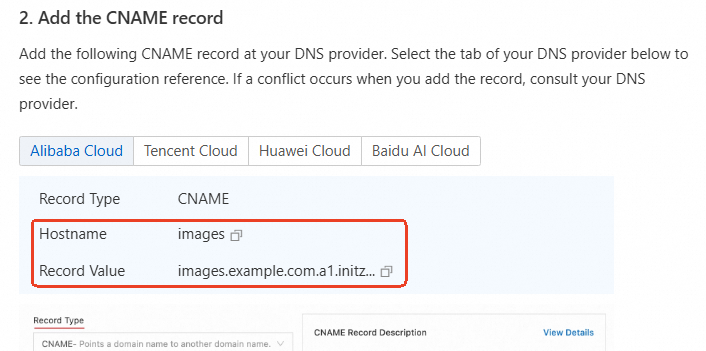
Step 2: Resolve the domain name
After you obtain the CNAME value in ESA, you must add a CNAME record in the Alibaba Cloud DNS console. When a user accesses the accelerated domain name, the request is resolved by Alibaba Cloud DNS to the CNAME of the ESA POP, which provides the acceleration service.
On the Public Zone page of the Alibaba Cloud DNS console, click Settings in the Actions column for the target domain name, such as
example.com.Click Add Record and configure the parameters using the Hostname and Record Value that you copied from ESA:
Record Type :
CNAMEHostname :
imagesQuery Source : Default
Record Value :
images.example.com.a1.initzz.comTTL : 10 (Recommended)
Wait for a few minutes and return to the ESA console to check whether the accelerated domain name has taken effect. If the CNAME Status is Configured , the acceleration is enabled.

Step 3: Verify the acceleration
You can access the same file using the ESA accelerated domain name and the bucket endpoint to verify the acceleration effect of ESA.
The results show that the loading time is 128 ms when the file is accessed using the accelerated domain name and 163 ms when the file is accessed using the bucket endpoint. The access speed is approximately 21% faster when you use the accelerated domain name.
The preceding data is for reference only. The actual acceleration effect may vary based on factors such as the network environment and geographical location. Typically, the acceleration effect is more significant if the user is closer to a POP or the network environment is better.
ESA accelerated domain name:
Access using the bucket endpoint:
Enable protection for the site
To improve the security of data in transit and the overall security of your website, you can configure multiple security features. These features include Anti-DDoS to defend against flood attacks, WAF to protect web applications from malicious attacks, and SSL Certificate management to ensure encryption of data in-transit. These features work together to help you build a more secure and reliable website environment.
Comprehensive website security
Protection features of ESA can effectively mitigate malicious attacks and ensure website stability and availability. ESA uses native WAF mitigation capabilities in combination with predefined and custom rules to intelligently filter client request traffic. This ensures that only legitimate and clean traffic can reach the server, thereby reducing potential security risks. You can also enable abuse prevention as needed to effectively prevent malicious resource abuse and to ensure service stability and security.

During service operation, ESA uses the Security Analytics and Event Analysis modules to collect and analyze client request data in real time and detect abnormal behavior. Using WAF custom rules, you can flexibly configure various protection measures, such as Block, JavaScript Challenge, and Redirection, to precisely respond to different types of attacks.
Additionally, ESA enables the DDoS Basic Protection feature by default to effectively defend against large-scale DDoS and CC attacks and ensure your website remains stable during high-traffic attacks.
With these multilayered protection measures, ESA not only helps you quickly detect and block abnormal access but also provides strong security protection against complex attacks, providing comprehensive protection for your website.
Secure communication between clients and servers
Encryption of data in-transit is a key measure to secure network communications and effectively prevents sensitive data from being stolen or tampered with during transmission. ESA provides a comprehensive security solution for data transmission between clients and your origin server, ensuring the security of data at every stage.

First, ESA enables the SSL/TLS encryption feature by default. The SSL/TLS protocol ensures the confidentiality and integrity of data during transmission by establishing an encrypted channel between the client and the server.
To further enhance security, you can request a free edge certificate. By deploying an edge certificate, clients communicate with ESA POPs over HTTPS. This ensures that data in transit is both encrypted and authenticated, which increases user trust in the website.
In addition, ESA supports enabling the edge TLS mutual authentication feature. This feature establishes a bi-directional identity verification mechanism between clients and ESA POPs to ensure that only authorized clients can access the server. This mutual authentication mechanism greatly improves the security of data transmission and effectively prevents unauthorized access and malicious attacks.
With the preceding multilayered security measures, you can ensure that your business data is protected from various network threats during transmission to safeguard your business.
Recommended configurations
ESA provides multiple optimization strategies to improve resource access performance, optimize network performance, and enhance the cache hit ratio. This ensures a faster, more stable, and more secure access experience.
Optimize resource access performance
By enabling and optimizing website settings, ESA significantly improves application performance. Specifically, ESA uses multiple advanced technologies to comprehensively optimize resources, including custom image transformation, resource minification, and transport protocol upgrades. These optimizations improve site access speed from multiple dimensions, allowing you to retrieve required resources faster and enhancing the overall user experience.
Custom image transformation: Automatically adjusts the size and format of images based on the user's device and screen size to reduce unnecessary data transmission.
Resource minification: Compresses and optimizes static resources, and removes redundant code and unnecessary data to reduce the size of resource files.
Transport protocol upgrades: Supports the latest transport protocols, such as HTTP/2 and HTTP/3, to improve data transmission efficiency and reduce latency.
Optimize network performance
To further improve network transmission speed, ESA provides four levels of network optimization configurations to enhance overall network performance, from protocol support to communication methods.
IPv6 protocol support: Fully compatible with the IPv6 protocol to improve the utilization of network address resources and optimize network connectivity efficiency.
Low-latency communication with WebSocket: Uses the WebSocket protocol for real-time communication to reduce data transmission latency and improve the response speed of real-time applications.
Efficient service interaction with gRPC: Provides low-latency, high-throughput service interaction based on the efficient communication mechanism of gRPC. This is suitable for scenarios with high performance requirements.
Intelligent traffic shaping to prevent overload: Uses intelligent traffic shaping and load balancing technologies to avoid network congestion and overload, which ensures stable network transmission speed even in high-concurrency scenarios.
Improve the cache hit ratio
To improve resource access speed, ESA lets you store frequently used resource files on POPs by configuring site cache policies or creating cache rules. When a user requests a file, the POP responds directly. This avoids long-distance origin requests and significantly reduces resource loading time.
Site cache policy: You can flexibly configure cache rules as needed to specify which resources to cache and maximize the cache hit ratio.
POP storage: Popular resources and static files are stored on globally distributed POPs. This ensures that users can access resources from nearby locations, which reduces network transmission distance and latency.

