By Jessie Angelica and Sunny Jovita, Solution Architect
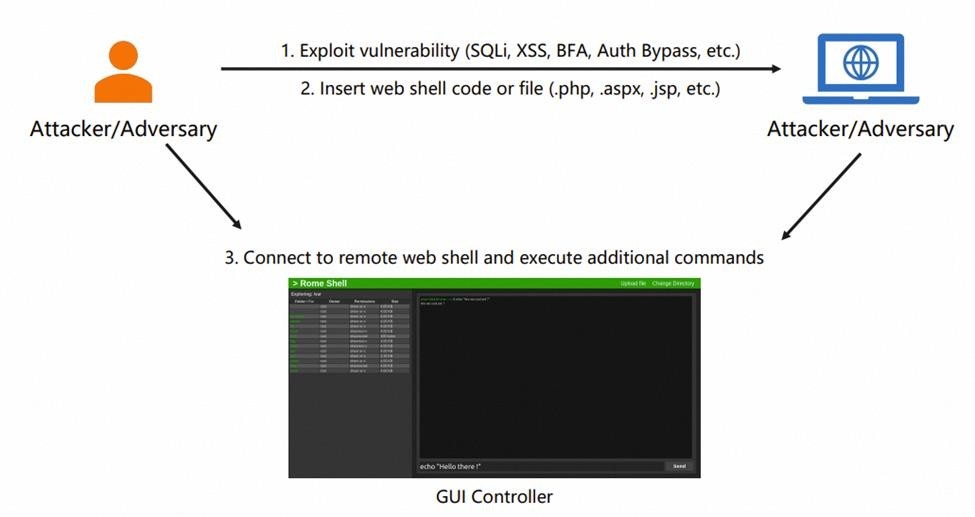
In a bypass attack, the attacker's primary goal is to acquire information and inject a file or web shell code into the targeted system. This malicious code can manifest in various forms, including PHP, ISP, or JS files. Once an attacker successfully injects this code, they can quickly establish remote connections to the server through a web shell GUI. Bypass attacks are common in website security. Examples of application attacks that malicious actors can deploy include SQL injection, application exploits (such as command injection, SQL injection, and brute force attacks), and the deployment of bots.
An illustrative example of a bot is when a website appears to be running normally but suddenly experiences erratic fluctuations in traffic. This situation poses a challenge because it becomes difficult to distinguish between genuine human users and automated bots. Furthermore, in the realm of cyber attacks, there are targeted assault strategies, such as social engineering, reverse engineering, and SYN flood attacks, commonly employed in Distributed Denial of Service (DDoS) attacks. SYN flood attacks involve inundating the target with a high volume of SYN/ACK (Synchronize/Acknowledge) requests, overwhelming the system's resources and rendering it inaccessible to legitimate users.
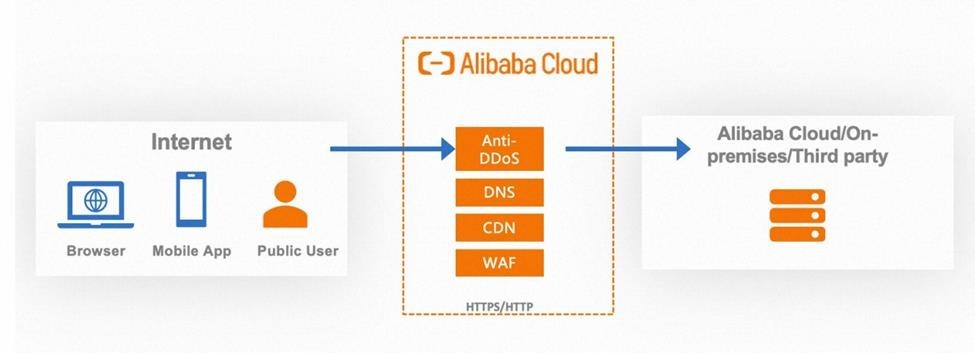
Implementing a Web Application Firewall (WAF) is crucial to mitigate all attacks. Positioned at Layer 7 of the application stack, a WAF effectively monitors HTTP/HTTPS traffic between the application and the internet. This versatile security system can be deployed or injected into various environments, including the cloud, different cloud providers, or on-premise solutions.
For instance, in the absence of a WAF, clients would input the domain name when they seek to access your website. A DNS server then resolves the IP address associated with that domain and directs the client to the corresponding server. However, when a WAF is implemented, users first interact with the DNS to obtain the DNS name of the website since WAFs operate as a redirect system. Instead of revealing the actual IP address, the DNS provides the WAF's name. Consequently, the actual IP address remains hidden from potential attackers, enhancing security. All user requests are seamlessly routed through the WAF before reaching the server. This initial routing through the WAF shields the server's IP address from public exposure.
In this use case, a user inputs a query to locate the city of Tokyo. However, the attacker exploits a vulnerability by injecting a semicolon command into the SQL query and attempting to execute other susceptible queries. When security measures are low, the system becomes vulnerable to the deception caused by the semicolon command. Consequently, the attacker can easily blend query, leading to data loss in the Tokyo table.
In the context of scripting vulnerabilities, if a website's URL or overall security is low, users or potential attackers can take advantage of this weakness. They can autonomously modify the website's scripting by inserting their scripts. These injected scripts redirect users to content that may involve gambling or pornography, causing users visiting the legitimate website to become uncertain about whether the site has been compromised or is intentionally directing them to such content.
WAFs prove particularly valuable in affiliate scenarios, such as ticketing platforms. In these instances, numerous bots or web crawlers may place ticket orders without completing payments, resulting in all tickets being held. This scenario harms customers and the company as revenue dwindles when fake users occupy ticket slots.
The significance of WAFs extends to e-commerce platforms and real estate sector, where traffic volumes can be substantial, vulnerabilities in website scripting can lead to fraudulent activities. For example, attackers may manipulate the contact information of sellers or real estate agents, making fraud a simple endeavor. These use cases exemplify the critical role of WAFs in protecting against a diverse range of threats across various industries.
Web Application Firewalls (WAFs) are robust security measures that offer several key capabilities:
1) Coverage of Common Vulnerabilities: WAFs can effectively address ten common vulnerability attacks identified by OWASP, making them versatile safeguards against various threats.
2) DDoS Protection: WAFs extend their protective capabilities to mitigate Distributed Denial of Service (DDoS) attacks, offering a layer of defense against large-scale assaults.
3) IP Blocking and Region Filtering: Administrators can employ WAFs to block specific IP addresses and regions identified as threats through the WAF's report console.
4) Traffic Monitoring and Rule Templates.
5) Port Management: You can open or enable specific ports on your servers, tailoring security configurations to meet your needs.
6) IP Whitelisting and Blacklisting: WAFs enable the management of IP addresses by allowing administrators to whitelist trusted IPs while blacklisting suspicious or malicious ones.
7) Subdomain Flexibility: WAFs offer the capability to protect any subdomain. For example, you can configure a subdomain like "website.development.co.id" and associate it with Alibaba WAF for enhanced security.
Regarding speed, the WAF system is designed to secure HTTP and HTTPS traffic without compromising access speed. However, to enhance user experience further and reduce server load, you can implement Content Delivery Networks (CDNs). CDNs frequently accessed content, allowing users to retrieve requests quickly from the store, minimizing the need to interact with the origin server. This, in turn, can significantly improve overall website performance while maintaining robust security through the WAF. When a server stores requests, new users seeking the same request and can retrieve it directly from the cache. However, if the requested content hasn't been cached, the request must proceed to the origin server for retrieval. Content Delivery Networks (CDNs) are designed with a caching system that alleviates the need to access the origin server constantly. This is particularly beneficial when the origin server is located in a different region, as CDNs significantly reduce access times due to their caching mechanisms.
WAF can protect against DDOS attack but if you want to protect DDOS, it's advisable to implement additional Anti- DDoS measures. DDoS attacks can occur at Layer 4 (network layer, involving TCP and UDP) or Layer 7 (application layer, involving HTTP and HTTPS). The security group feature is available in Elastic Compute Service (ECS) environments. For instance, to prevent DDoS attacks at Layer 4, you can configure the security group to allow traffic only on application ports like 80 or 443. If an attack occurs at Layer 7, the WAF is equipped to provide protection. However, it's recommended to augment security with anti-DDOS measures for further mitigation. When uncertain about the scale of an attack, starting with WAF is a prudent approach since monitoring incoming requests is crucial. For example, if the query rate exceeds 100,000 per second, implementing Anti-DDoS can provide an additional layer of security.
In conclusion, safeguard your web applications, protect your data, and elevate your cybersecurity posture by embracing the cutting-edge security solutions offered by Alibaba Cloud WAF. Join us in the journey towards a more secure and resilient online world.
115 posts | 21 followers
FollowAlibaba Cloud Community - October 13, 2023
Alibaba Clouder - January 28, 2021
Alibaba Clouder - December 25, 2020
Neel_Shah - November 14, 2025
Dikky Ryan Pratama - May 5, 2023
Alibaba Clouder - January 14, 2021
115 posts | 21 followers
Follow WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn More Web App Service
Web App Service
Web App Service allows you to deploy, scale, adjust, and monitor applications in an easy, efficient, secure, and flexible manner.
Learn MoreMore Posts by Alibaba Cloud Indonesia