By Xiaorui Liu (Yucheng)
Web Application Firewall (WAF) is commonly used as a north-south public network gateway for protecting against abnormal traffic. As the complexity of the internet environment increases, there is a growing demand for enhanced protection. The typical approach is to first route the traffic through the WAF security gateway for filtering and then forward it to the traffic gateway, which eventually reaches the microservice gateway. This multi-layer gateway architecture is illustrated in the following diagram:
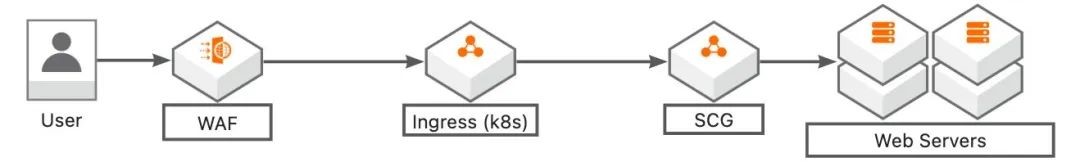
In this architecture, the WAF gateway provides security capabilities, the Ingress gateway handles cluster ingress gateway capabilities (Nginx may be deployed in non-Kubernetes scenarios), and SCG (Spring Cloud Gateway) serves as the microservice gateway. Under this architecture, it is crucial to evaluate the capacity of each gateway layer as each layer can potentially become a bottleneck and may require scaling out. However, this architecture comes with high resource and operational costs. Additionally, the introduction of each additional gateway layer increases the risk of affecting availability. In the event of availability issues, troubleshooting becomes more complex, resulting in a significant increase in mean time to recovery (MTTR).
The concept of cloud-native gateway proposes integrating security, traffic, and microservice gateway into a single entity. The architecture is as follows:
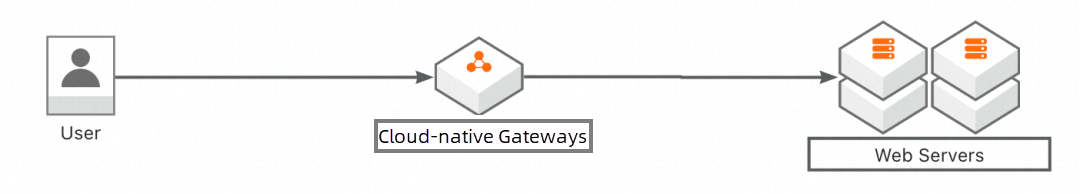
By adopting the three-in-one architecture of the cloud-native gateway, significant cost reduction and improvement in overall system availability can be achieved. This approach also aligns with the DevSecOps trend in microservice evolution. Microservice developers can focus more on security from the perspective of business interfaces, rather than implementing a one-size-fits-all WAF prevention mode for all routes.
The following figure shows the evolution of the cloud-native gateway technical architecture:
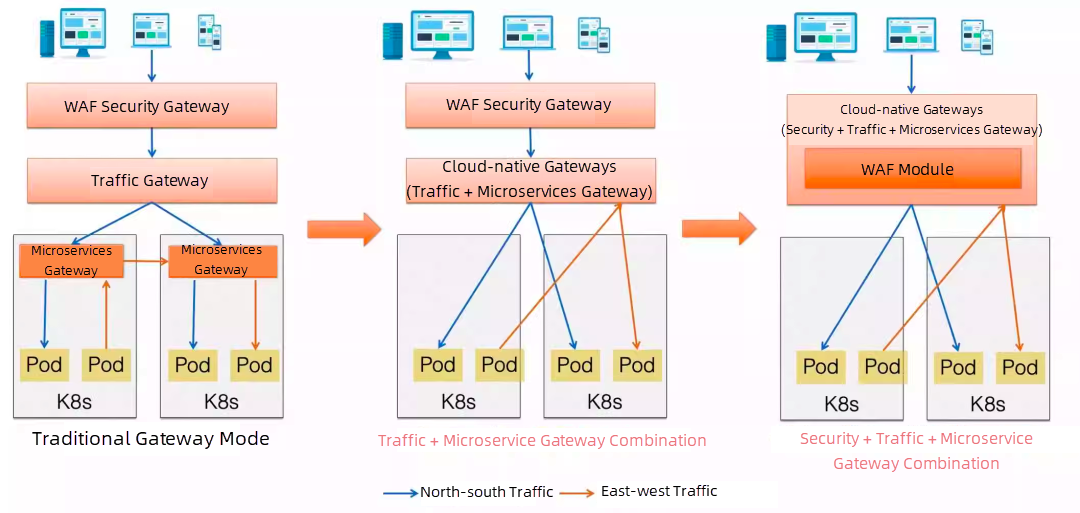
The evolution of technical architecture is accompanied by the evolution of organizational architecture, which is a key focus of microservice DevOps. The emphasis is on prioritizing developers to enhance the efficiency of microservice development. The transition to DevSecOps has no shortcuts. It requires collaboration between developers and operations personnel to break down the barriers between traditional development and operations. This collaboration is essential in forming a comprehensive and agile team that encompasses development, deployment, and security operations.
The cloud-native gateway provides security capabilities through WAF plugins and implements a rules protection engine based on ModSecurity. It can block suspicious requests based on user-defined rules and supports OWASP CRS to offer fundamental protection functions for websites.
The plug-in is easy to use and supports fine-grained protection at the route level or domain name level. The configuration fields include:
| Service Name | Data types | Optional/Required | Default value | Description |
| useCRS | bool | Optional | false | Whether to enable OWASP CRS. For more information, see coruleset [1]. |
| secRules | array of string | Optional | - | User-defined WAF protection rules. For more information about syntax rules, see ModSecurity Chinese manual [2] |
Sample configuration:
1. Enable the default configuration for interception.
useCRS: true2. Enable the default configuration to observe but not intercept.
useCRS: true
secRules:
- "SecRuleEngine DetectionOnly"3. Customize protection rules.
useCRS: true
secRules:
- "SecRule REQUEST_URI \"@streq /admin\" \"id:101,phase:1,t:lowercase,deny\""
- "SecRule REQUEST_BODY \"@rx maliciouspayload\" \"id:102,phase:2,t:lowercase,deny\""Based on this configuration, the following requests will be blocked from access:
curl http://example.com/admin
curl http://example.com -d "maliciouspayload"4. Enable for a specific route or domain name.
useCRS: true
secRules:
- "SecRule REQUEST_URI \"@streq /admin\" \"id:101,phase:1,t:lowercase,deny\""
- "SecRule REQUEST_BODY \"@rx maliciouspayload\" \"id:102,phase:2,t:lowercase,deny\""
_rules_:
- _match_route_:
- "route-1"
secRules:
- "SecAction \"id:102,phase:1,deny\""
- _match_domain_:
- "*.example.com"
- test.com
secRules:
- "SecAction \"id:102,phase:1,pass\""In this example, route-1 specified in match_route is the route name entered when you create a gateway route. If these two routes are matched, this configuration is used. In this example, *.example.com and test.com specified in match_domain are used to match the requested domain name. If a domain name is matched, this configuration is used. The configured match takes effect in the order specified by rules under _rules_. The corresponding configuration takes effect after the first rule is matched. Subsequent rules will be ignored.
Select a gateway instance, click Plug-in Marketplace, search for WAF, and then click the plug-in configuration page.
Enter WAF protection rules in the console and start the WAF plug-in:
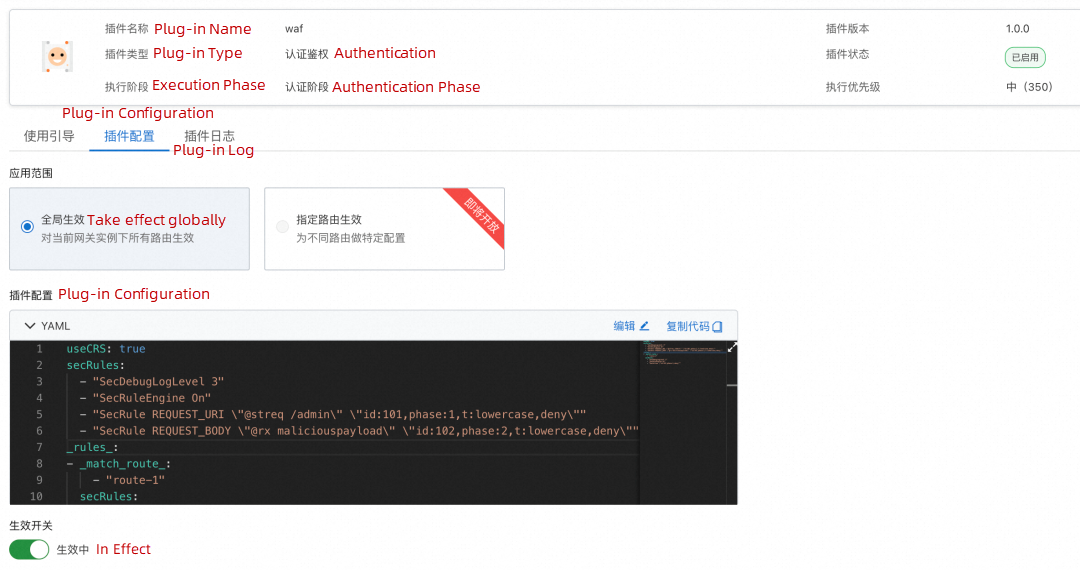
You can view the logs generated by the plug-in in the Plug-in Log section. The following figure shows the logs generated by the WAF plug-in during Shell injection attacks.
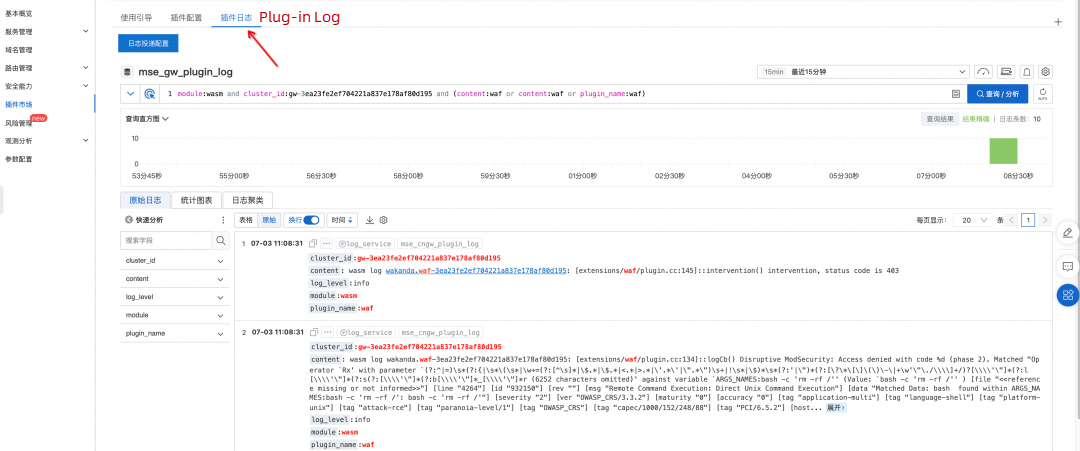
Send a simple web attack request to the gateway. Example:
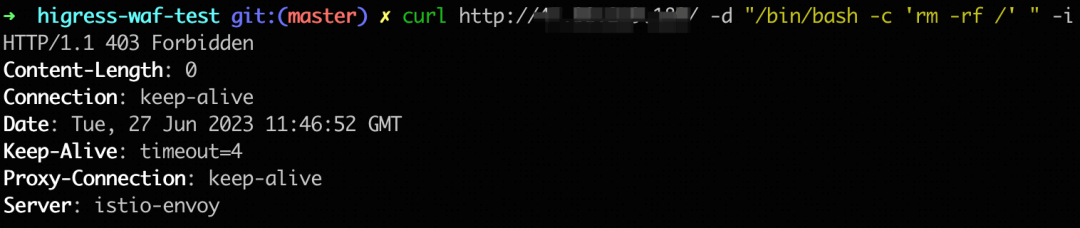
1. Example of Shell injection attack and defense
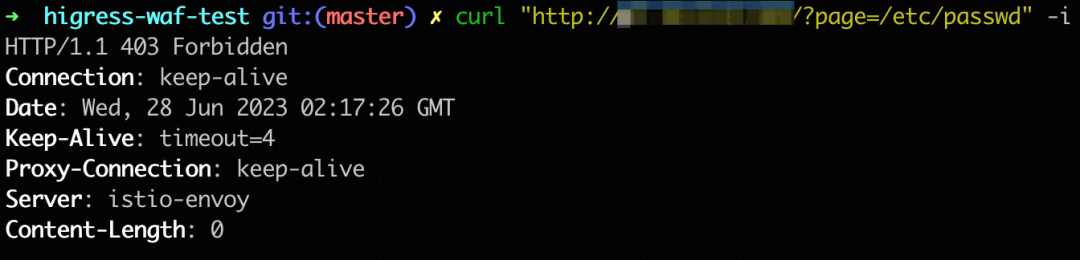
2. Example of SQL injection attack and defense

3. Example of remote files ( including RFI) attack and defense
4. Example of XSS attack and defense

5. Example of PHP injection attack and defense
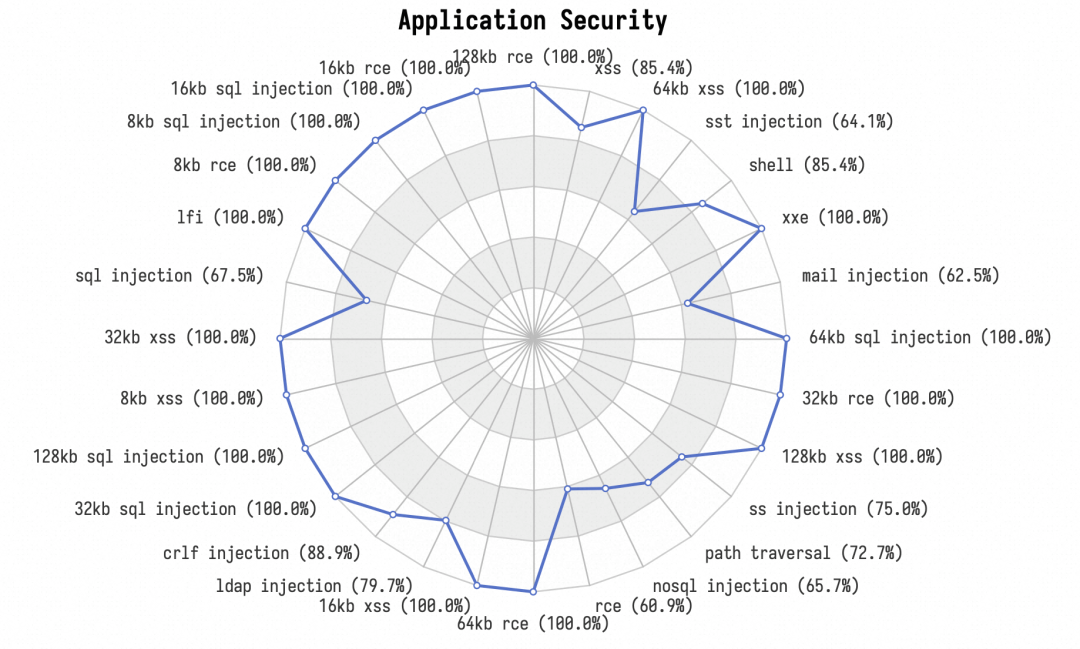
GoTestWAF [3] is an API and OWASP attack simulation tool that supports a wide range of API protocols, including REST, GraphQL, gRPC, WebSockets, SOAP, and XMLRPC. It was designed to evaluate web application security solutions, such as API security proxies, Web Application Firewalls (WAF), IPS, and API gateways. GoTestWAF generates malicious requests using encoded payloads placed in different parts of HTTP requests: its body, headers, URL parameters, etc., covering various common attack types. The following figure shows the test results of multiple attacks. The test results show that the WAF plug-in can effectively detect illegal requests of various attack types.
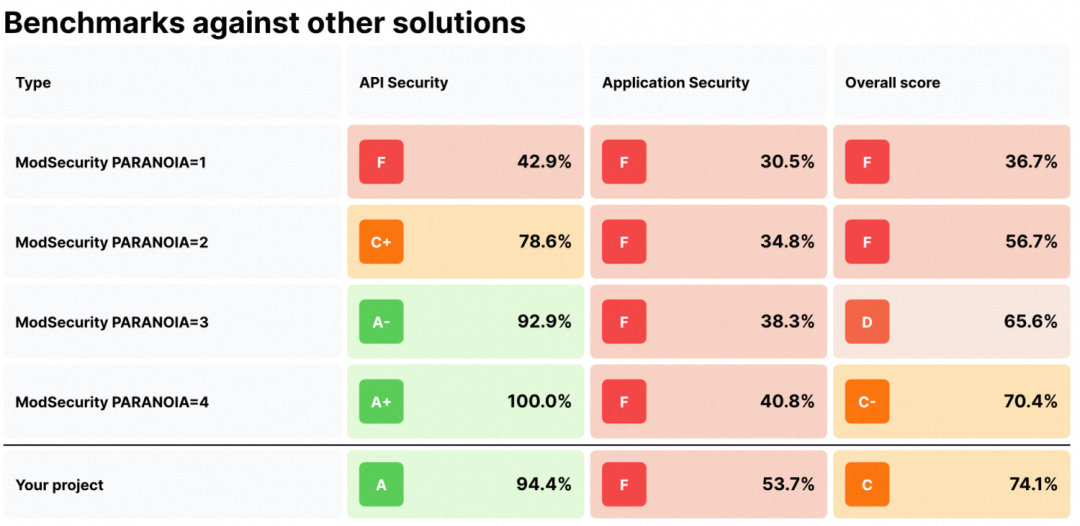
GoTestWAF provides four benchmarks based on ModSecurity. In the benchmark, paranoia indicates the protection level. The higher the value, the higher the protection level, and the higher the overall score. The overall score of the WAF plug-in is 74.1, which exceeds the benchmark with the highest protection level. This indicates that the plug-in has good protection capabilities.
The free WAF plugin offered by the cloud-native gateway only provides basic protection rules. If you have higher protection requirements, you can consider purchasing the Alibaba Cloud Web Application Firewall [4]. This option provides advanced protection capabilities, improved performance, and offers an additional layer of security for your application.
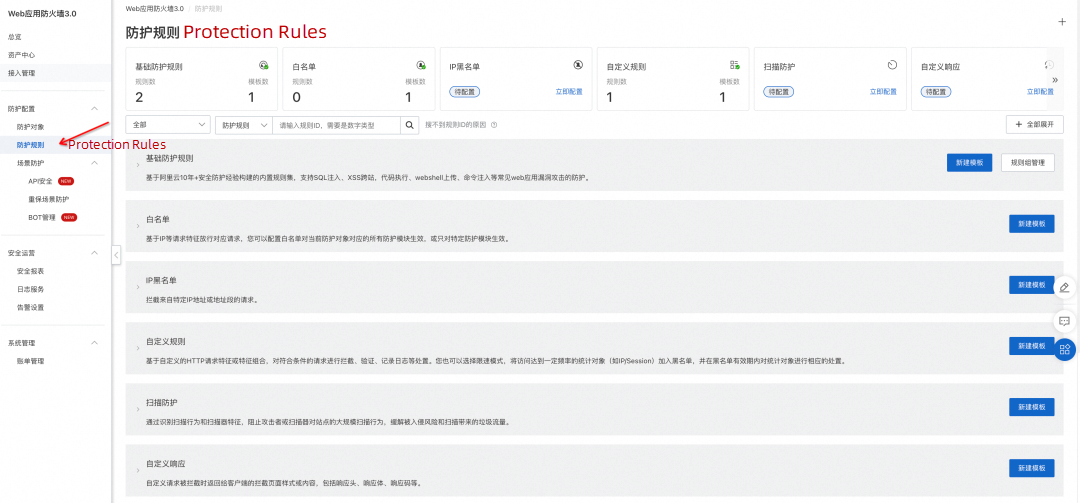
In the WAF console, you can [5] manage protection rules:
In the Access Management section, you can configure access to the gateway instance:
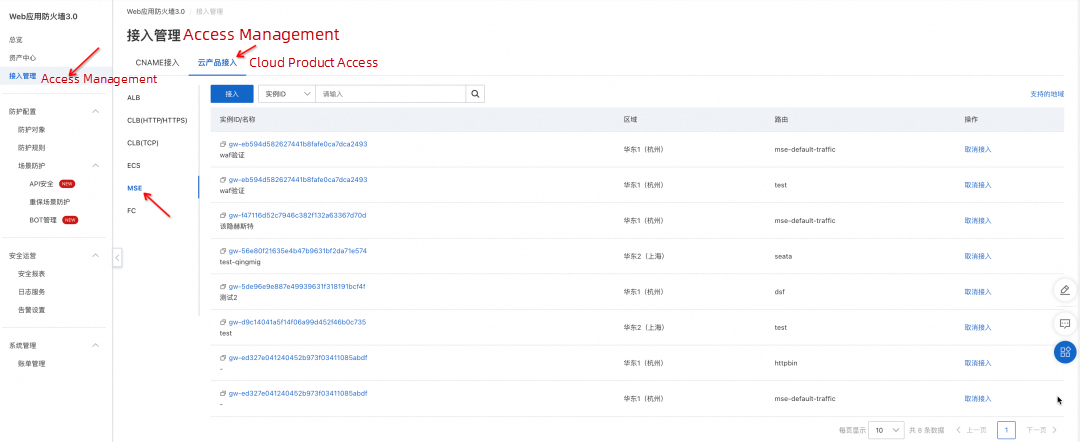
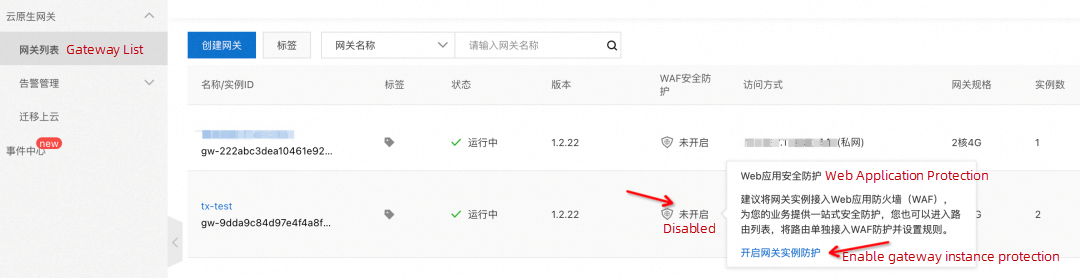
You can also configure access to WAF in the gateway instance section:
[1] coreruleset
https://github.com/coreruleset/coreruleset/tree/v3.3.2?spm=5176.mse-ops.0.0.ef3f142fSPw8XV&file=v3.3.2
[2] ModSecurity Document
https://www.alibabacloud.com/help/en/doc-detail/121053.html
[3] GoTestWAF
https://github.com/wallarm/gotestwaf
[4] Alibaba Cloud Web Application Firewall
https://www.alibabacloud.com/help/en/doc-detail/446889.html
[5] WAF Console
https://account.aliyun.com/login/login.htm?oauth_callback=https%3A%2F%2Fyundun.console.aliyun.com%2F%3Fp%3Dwafnew
How Does Spring Cloud Introduce Cloud-native Gateway and Innovate Microservice Architecture
Kruise-Game: Best Practice for Session-Based Games (PvP Room)

664 posts | 55 followers
FollowAlibaba Cloud Native Community - November 28, 2022
Alibaba Cloud Native Community - February 18, 2025
Alibaba Cloud Native - December 10, 2024
Alibaba Cloud Native Community - July 24, 2025
Alibaba Cloud Native Community - October 20, 2025
Alibaba Cloud Native Community - November 15, 2023

664 posts | 55 followers
Follow WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Web Hosting Solution
Web Hosting Solution
Explore Web Hosting solutions that can power your personal website or empower your online business.
Learn More Microservices Engine (MSE)
Microservices Engine (MSE)
MSE provides a fully managed registration and configuration center, and gateway and microservices governance capabilities.
Learn More Web App Service
Web App Service
Web App Service allows you to deploy, scale, adjust, and monitor applications in an easy, efficient, secure, and flexible manner.
Learn MoreMore Posts by Alibaba Cloud Native Community