By Alibaba Cloud Blockchain Service Team
On December 9th, the blockchain-based communication authorization service was officially released during the 118th issue of the Alibaba Cloud new product launch. Bo Yang, Senior Product Manager of Alibaba Cloud Communications, and Gong Yu, Product Expert of Ant Blockchain, discussed in detail about this service. They discussed the technical difficulties and implementation methods of communication authorization, and deeply explained the product features, workflow of the communication Authorization Service, the application of Ant blockchain authorization, and the technical value.
When enterprises promote their services by using message or voice, they may encounter the following issues:
To solve the preceding problems, the Alibaba Cloud Communication Authorization Service, built based on Ant blockchain technology, can implement the trusted certificate storage and authorization management during the user authorization process.
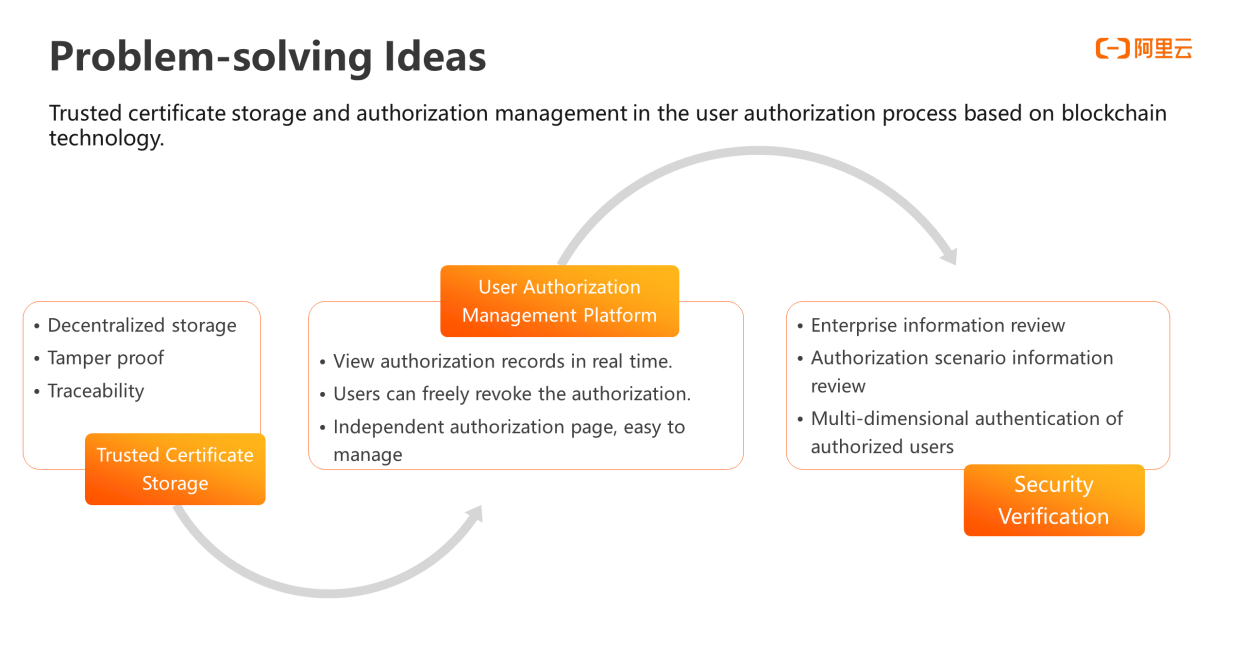
First, with a blockchain-based trusted data sharing system, the credit center participates interconnection of all parties and relies on the distributed ledger structure provided by the blockchain. This allows the data transaction flow records to be open, transparent, tamper-proof, and traceable, allowing every user-authorized notary to be trusted. Thereby solving the problems of unclear authorization process and untraceable information being tampered with.
The authorization management platform enables enterprise customers to view authorization records in real time. The enterprise customers also need to apply for authorization on the authorization scenario page on the platform. To obtain authorization from a user, a pop-up page will be needed and it should be manageable and controllable. In addition, for end user, the platform also provides Alipay channel so that users can view the details of their authorization in Alipay. Unless otherwise agreed in a contract, users can have independent choices of providing authorization or revoking authorization.
There is an information audit process for the newly applied enterprises, and enterprises are only qualified to use the communications authorization service after the enterprise information and authorization scenario information are approved. This ensures that the enterprise meets relevant requirements for promotion of its business. We also verify the identities of authorized users in multiple dimensions to avoid some unreal and fake users to authorize, and ensure the authenticity and validity of users.
The overall capability framework of the communication authorization service mainly includes four parts: enterprise application, business registration, notary blockchain, and forensic and query.
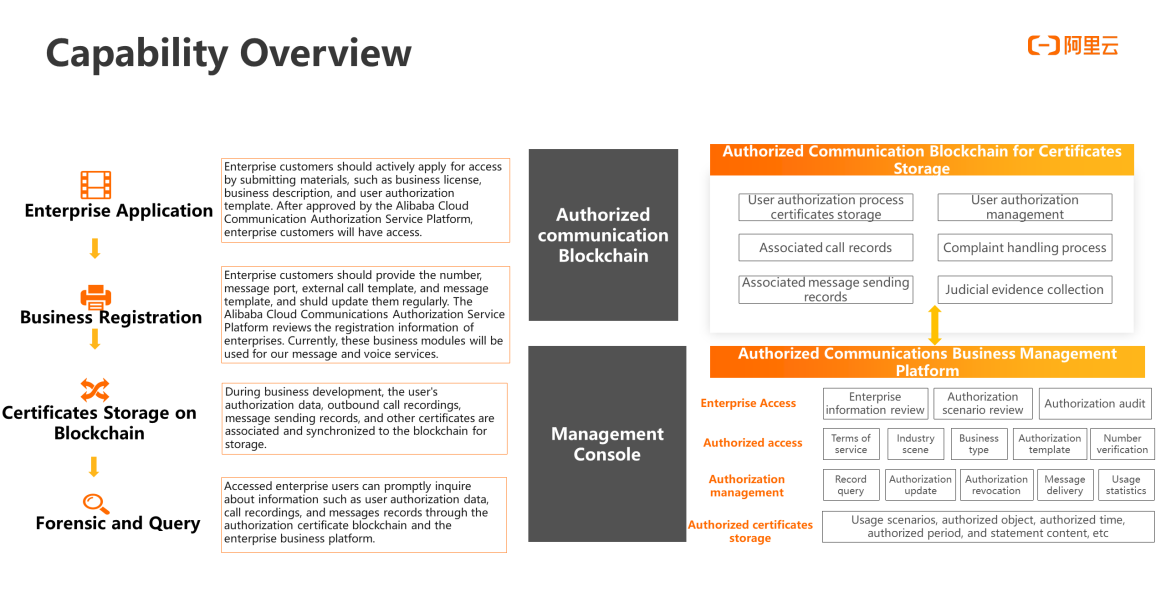
Enterprise Application: Enterprise customers should actively apply for access by submitting materials, such as business license, business description, and user authorization template. After approved by the Alibaba Cloud Communication Authorization Service Platform, enterprise customers will have access.
Business Registration: Enterprise customers should provide the number, message port, external call template, and message template, and should update them regularly. The Alibaba Cloud Communications Authorization Service Platform reviews the registration information of enterprises. Currently, these business modules will be used for our message and voice services.
Notary Blockchain: during business development, the user's authorization data, outbound call recordings, message sending records, and other notary information are associated and synchronized to the notary blockchain for storage.
Forensic and Query: Accessed enterprise users can promptly inquire about information such as user authorization data, call recordings, and messages records through the authorization certificate blockchain and the enterprise business platform.
These modules are implemented on the Alibaba Cloud Communication Authorization Platform (business management console). The underlying user authorization data storage is combined with the blockchain to ensure the user authorization data is traceable and unchangeable. In addition, for the complaint handling process and judicial disputes, the platform will also support the judicial evidence collection process.
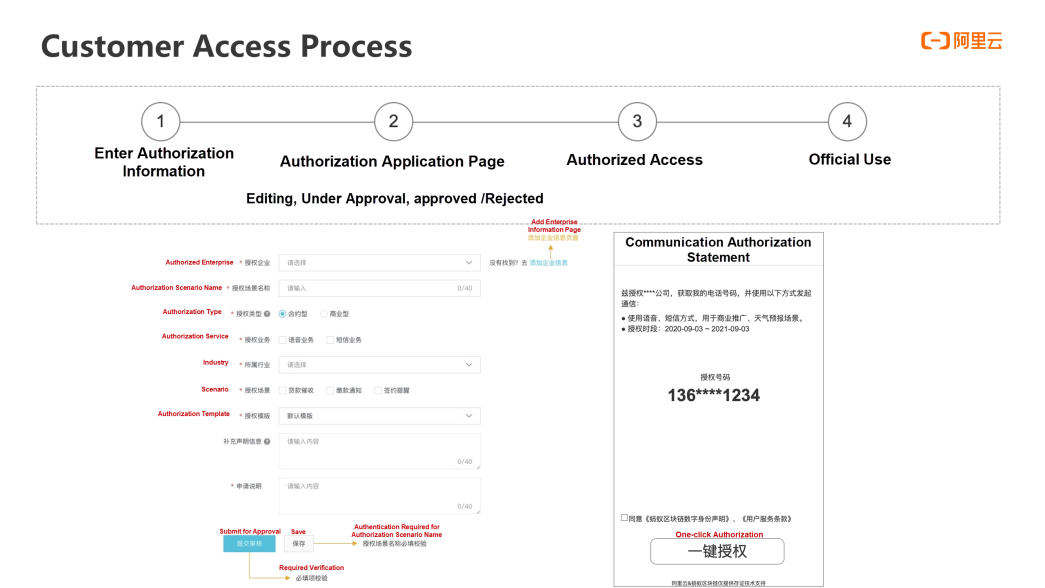
The Communication Authorization Service provides an independent authorization interactive page to ensure the credibility of authorization. A clear authorization page allows customers to select and confirm the authorization cycle, including the business type, industry scenario, authorization cycle, authorization number, and authorized enterprise. All the information will be displayed through the authorization page. The next step will not be taken until user authorization is explicitly specified.
To verify a user's identity, we use a multi-dimensional authentication mechanism at the back end to ensure the authenticity of the user. Specifically, we will verify whether the authorized number is the user's local number and whether it is consistent with the binding number of the Alipay account. Finally, the message verification code is used. There are multiple access modes supported by the Communication Authorization Service in the process of authorized access. You can directly encapsulate the link provided by the Communication Authorization Service or QR codes on the page to guide you, or directly integrate the SDK inside the APP to implement the authorization. The authorization process is real-time after one click. The specific content is submitted to the blockchain, including the authorization number, authorized enterprise, statement content, authorization cycle, industry scenario, and authorization time. The entire process is relatively fast.
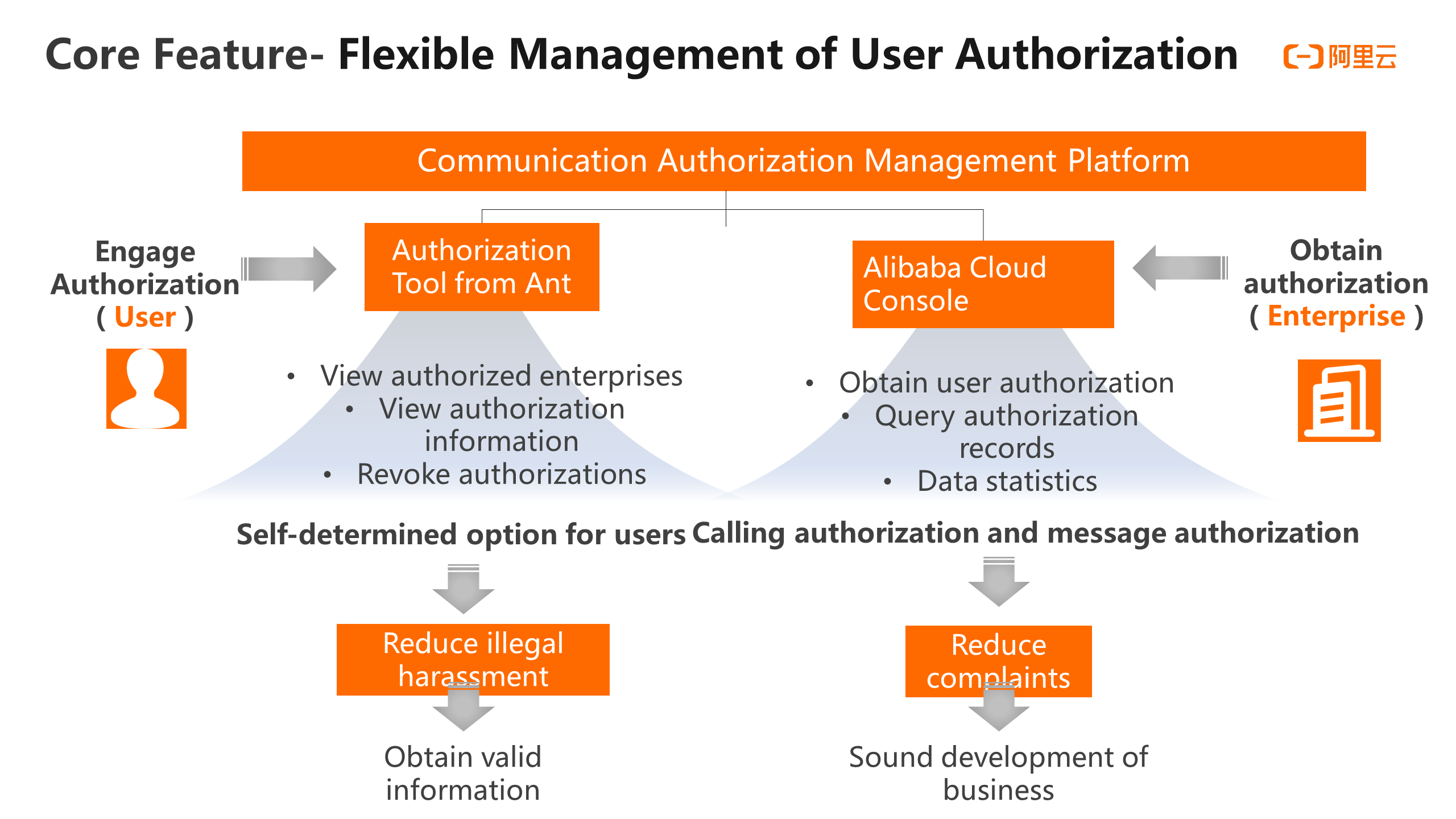
The management platform for the communication Authorization Service consists of the Customer- end Portal of Ant Shouquanbao and the Business- end Portal of the Alibaba Cloud Console. As the role for granting authorization, the user can search for the authorized enterprise in Alipay to manage the authorized enterprise, including viewing the details of the authorized enterprise and viewing the authorization information, such as the authorization cycle and purpose, and revoking the authorization in the authorized enterprise. One benefit of this method is that it can reduce some illegal harassment and obtain useful information more effectively.
Enterprises can obtain information such as user authorization scenarios in the Alibaba Cloud Communications Authorization Service Console to query specific users who have provided authorization or revoked authorization, and use the data statistics feature. This helps enterprises carry out their own authorized business services based on their needs. So as to reduce complaints and ensure the sound development of the business.
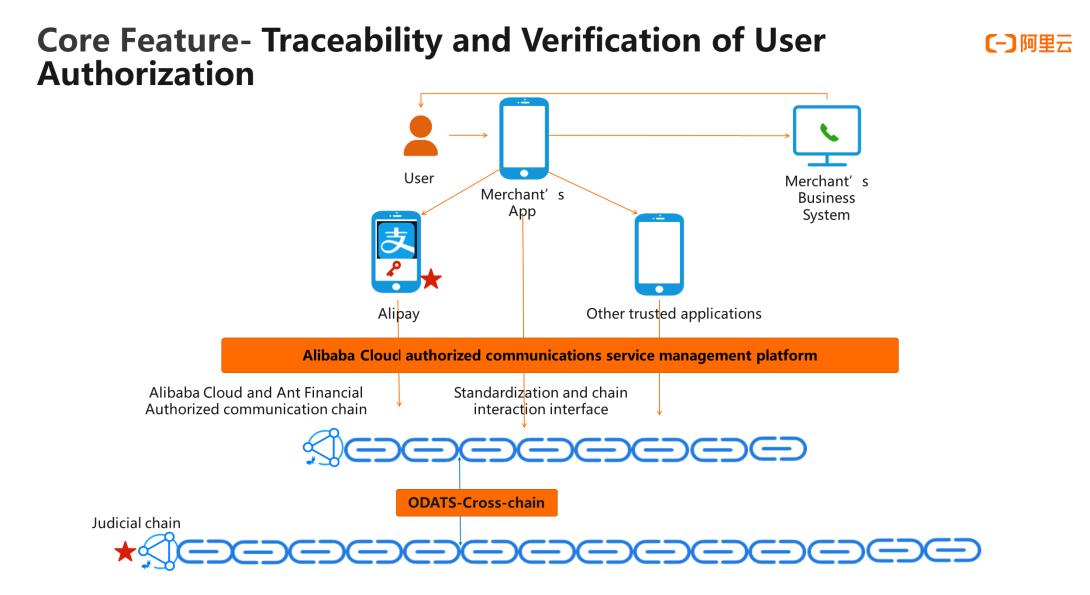
The third new feature of the Communications Authorization Service is that the user authorization information can be traced and used for forensic verification. Regardless of whether the user authorization is performed directly through the enterprise APP, or by the authorization page of Alipay, or subsequent authorization is performed through other trusted applications, it will be directly standardized through the business management platform of Alibaba Cloud Communications Authorization Service. And the authorization information will be notarized with the chain's interactive interface. In addition, Ant blockchain can be connected to the judicial chain by using the ODATS cross-chain technology. This enables forensic verification to be carried out quickly when legal disputes arise, greatly reducing the risk of enterprises falling into various legal disputes.
In a narrow sense, blockchain is a distributed and shared ledger technology. Based on smart contracts, blockchain can reach consensus on transactions among participants and make the history of transactions tamper-proof. In a broad sense, blockchain builds a distributed trust network among institutions, individuals, and machines. It is a new architecture and collaboration model to connect trusted data and achieve value flow.
Ant blockchain begins with blocks and links the industry. It has been applied to more than 50 business scenarios, such as government platforms, seal applications, national legal chains, financial transactions and chains, supply chain finance, overseas commodities, and agricultural product traceability. The daily chain volume reached 100 million level. The technology is leading, with more than 4000 patent applications worldwide. The communication authorization service released this time uses the authorized enterprise Ant blockchain, which is a Customer-end service based on distributed digital identity.
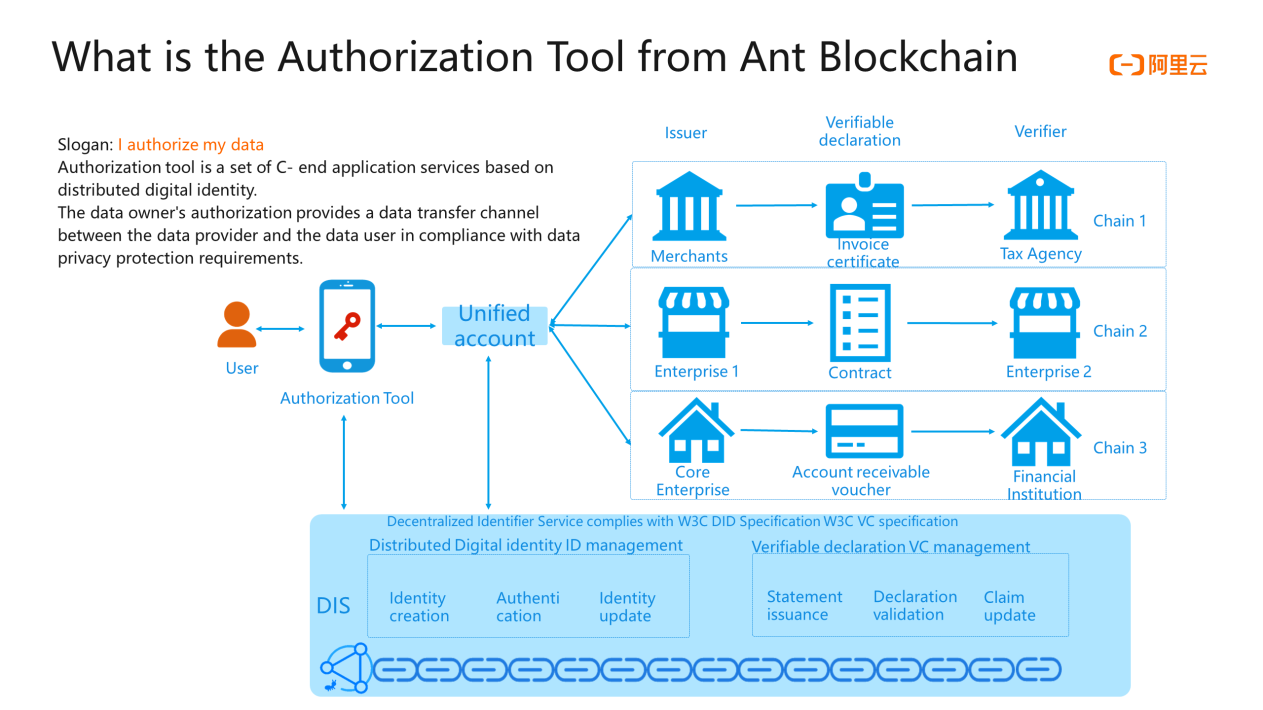
Ant blockchain uses the underlying service of distributed digital identities to map real identities to on-chain identities and implement data exchange between entities. To exchange data between merchant A and merchant B, you can configure account mapping and issue verification statements on blockchains. In addition, the use of a unified account allows information exchange among different chains. Based on that, the authorized enterprise links to the Customer-end user through the data owner's authorization, a data flow channel between the data provider and the data user is established, with privacy protection compliance.
An application model in the communication authorization scenario is to map participants to blockchain accounts and then notarize users' communication authorizations to guarantee the communication rights of users. First, the system will verify the information of the participants and customize the application scope authorized by the enterprise. When the user uses the enterprise application, the enterprise will apply for the user's communication right, and the user will independently evaluate whether to grant authorization based on the enterprise's authorization scope. After authorization, according to the agreement, users can choose to revoke or the authorization can be automatically revoked after the agreement is expired . In this process, documents can be marked on the blockchain and become tamper-proof. Only the relevant supervisors can verify the content of the certificate on the blockchain as needed, including the information of issuer,s registrant, and statement.
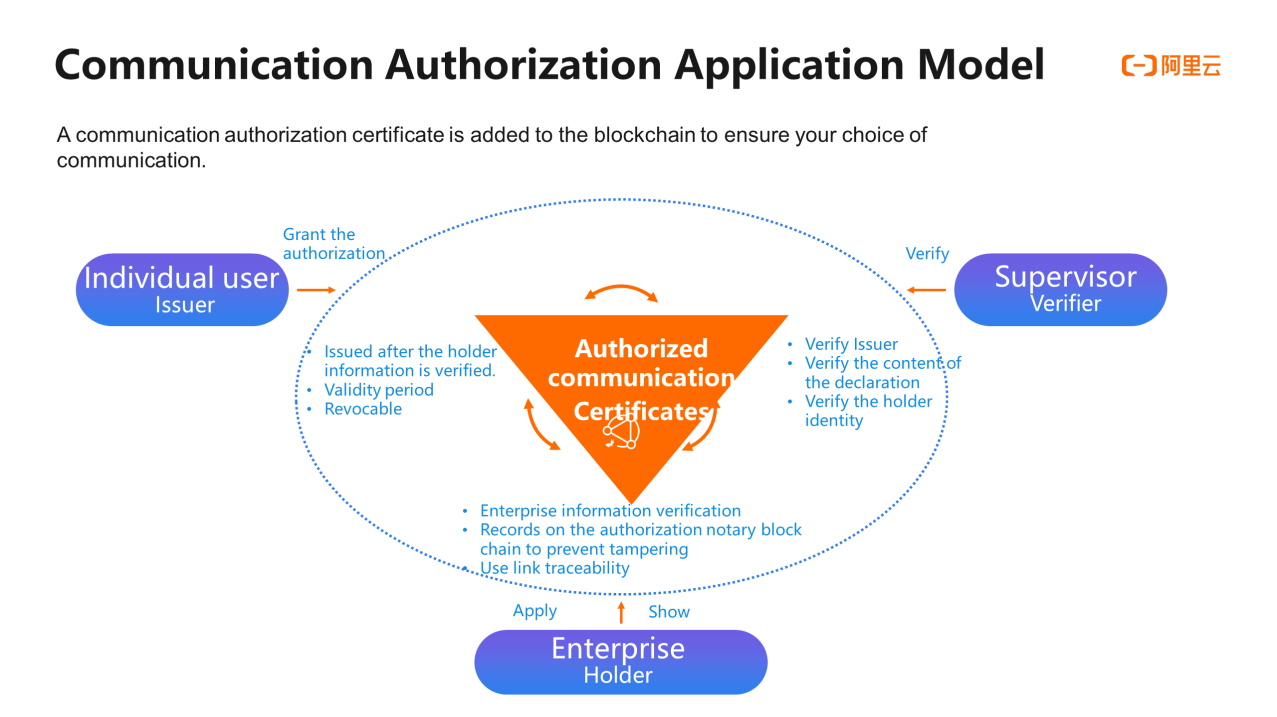
With the introduction of blockchain technology, the Communication Authorization Service provides users with one-click authorization and self-determined option, which allows users to decide which merchants can be authorized. The relevant records are notarized to prevent tampering and can be verified. In this way, the enterprise can contact the user within the scope of user authorization. When the authorization expires or the user revokes the authorization, the enterprise can no longer call the user.
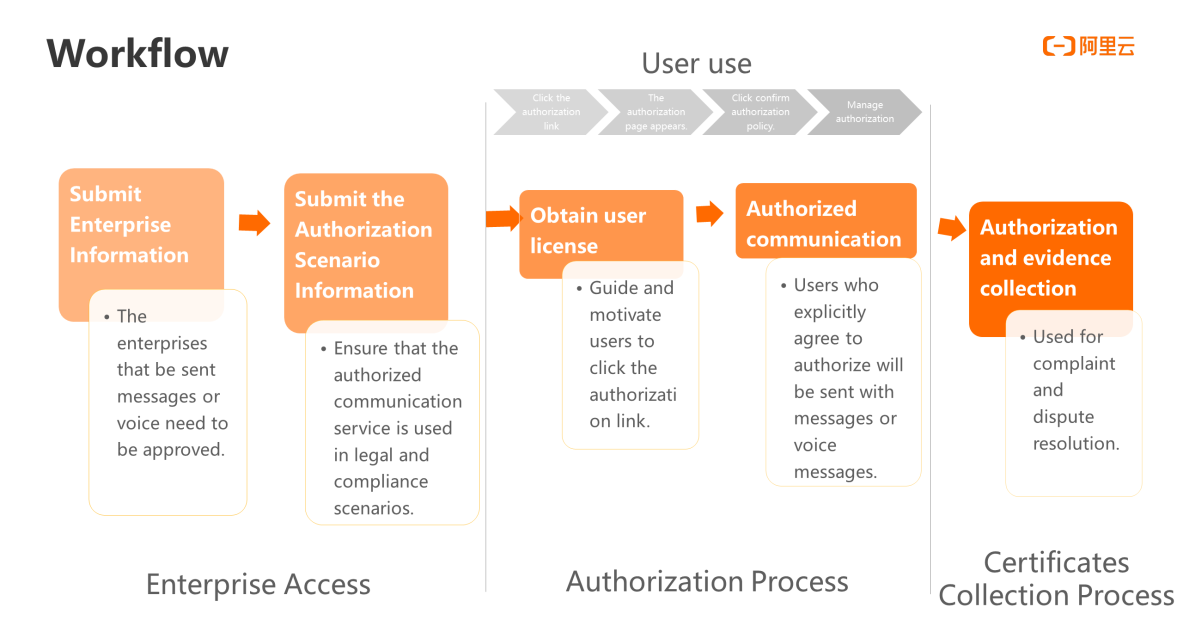
To authorize enterprises to access Alibaba Cloud verification, we set up two modules:enterprise information review and permission scenario review. This ensures that enterprises, that have passed the review and reached users by sending text messages and voice, can truly carry out services in legitimate and compliant scenarios.
The access authorization process is also the core process for an enterprise to obtain user authorization. For enterprise customers, it is to guide and motivate users to click the authorization link so that message or voice messages can be sent to users who have explicitly agreed to authorization. Between the enterprise customers and users, the process starts when you click the authorization link, and then the system displays a page with the authorization feature. After you click confirm authorization or directly close the page, the system manages the authorization. The authorization process can be directly verified by blockchain.
In the final stage of authorization and evidence collection, it is mainly used to resolve some complaints and disputes.
Typical Application Scenario 1: it is used for enterprises to obtain authorization before sending messages or voice calls to users. Users click the checkbox of the agreement and click the authorization button. Then, the back end automatically saves the user input information, authorization text, action process, and time to Ant blockchain. At the same time, after the notary is successful, it will return a notary number to facilitate the subsequent verification process.
Typical Application Scenario 2: it is used for enterprises to query user information for evaluation in specified purpose scenarios, such as authorization data query. Generally, enterprises with this demand will be some bank payment enterprises. Through information self-proof, the recording time sequence is tamper-proof, the evidence chain can truly restore the actual query process, and users' data are authorized by them self. It is also a good way for enterprises to reduce costs and increase efficiency, for the evidence has no impact on the workflow. Nor does it change the users' habits.
In the future, Alibaba Cloud communications authorization service will continue to provide richer module functions, such as authorization hierarchical modules, more detailed authorization, richer authorization templates and forms, and full-process blockchain, by using its own technology, to continuously promote the healthy development of the call center market.
Alibaba Cloud Releases EventBridge to Support Cloud Native Architecture
Alibaba Cloud Big Data Solutions for Real-Time Analysis and Decision-Making for Enterprises

31 posts | 5 followers
FollowWei Kuo - August 30, 2019
Alibaba Clouder - September 17, 2019
Alibaba Clouder - December 21, 2018
Alibaba Cloud New Products - June 3, 2020
Alibaba Cloud Native Community - May 8, 2025
Alibaba Container Service - September 17, 2025

31 posts | 5 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Blockchain as a Service
Blockchain as a Service
BaaS provides an enterprise-level platform service based on leading blockchain technologies, which helps you build a trusted cloud infrastructure.
Learn More Data Security on the Cloud Solution
Data Security on the Cloud Solution
This solution helps you easily build a robust data security framework to safeguard your data assets throughout the data security lifecycle with ensured confidentiality, integrity, and availability of your data.
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn MoreMore Posts by Alibaba Cloud New Products