By Kunshuo and Baiyu
As the Internet has become the de facto infrastructure of our daily lives, the risk of cyber security threats and infringements on enterprise applications and services have also become more prominent. The risks involved are not only confined to network security but also to the application itself.
In a traditional network architecture, applications are located in IDC and have clear boundaries. Application threats mostly originate from outside the boundaries and those within the boundaries are ignored. Traditionally, WAF (web application firewall) technology is used to intercept dangerous traffic, focusing on the north-south traffic at the entrance of the boundary.
However, with the development of microservices and containerized technologies, applications can be deployed in multiple environments such as IDC, container, public cloud, and private cloud. These applications are vulnerable not only to north-south threats, but also to horizontal threats from east-west. The increasing complexity of the network environment and the diversification of vulnerability attack methods have caused many production and research teams to spend more energy to fix these problems, thus wasting a lot of resources on research and development.
For most enterprises, the following depicts the typical security pain points at this stage:
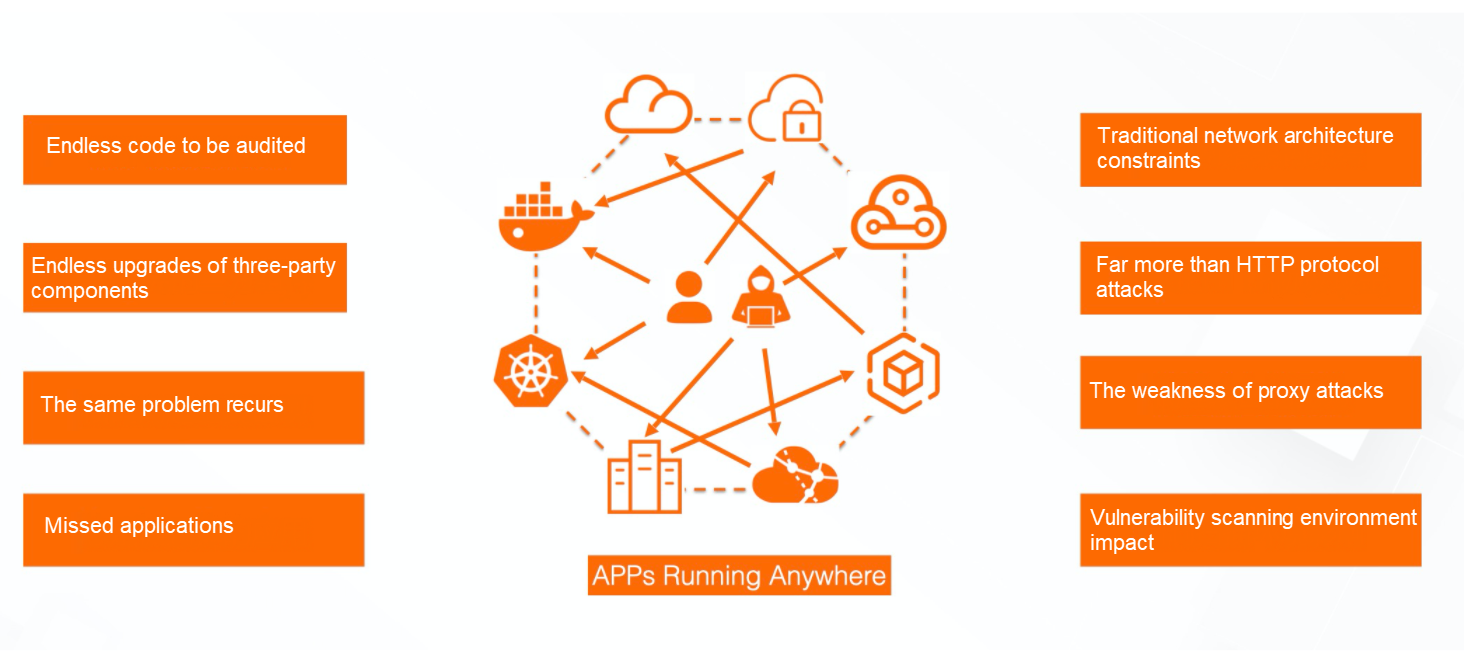
What if our application can be hardened without code security experts, additional code modifications, and complex configurations? In response, Alibaba Cloud Application Real-Time Monitoring Service (ARMS) launched the "application security" function based on RASP (Runtime Application Self-Protection), which allows applications to provide security protection in the upper limit and achieve endogenous security.
In 2014, Gartner listed "Runtime Application Self-Protection" (RASP) as the key trend of application security. As a security product that detects application attacks in run time and protects itself, RASP injects security programs into applications like vaccines, integrates with applications, detects and blocks security attacks in real-time, and enables applications to protect themselves. When applications encounter specific vulnerabilities and attacks, they can reconfigure to deal with new attacks without human intervention.
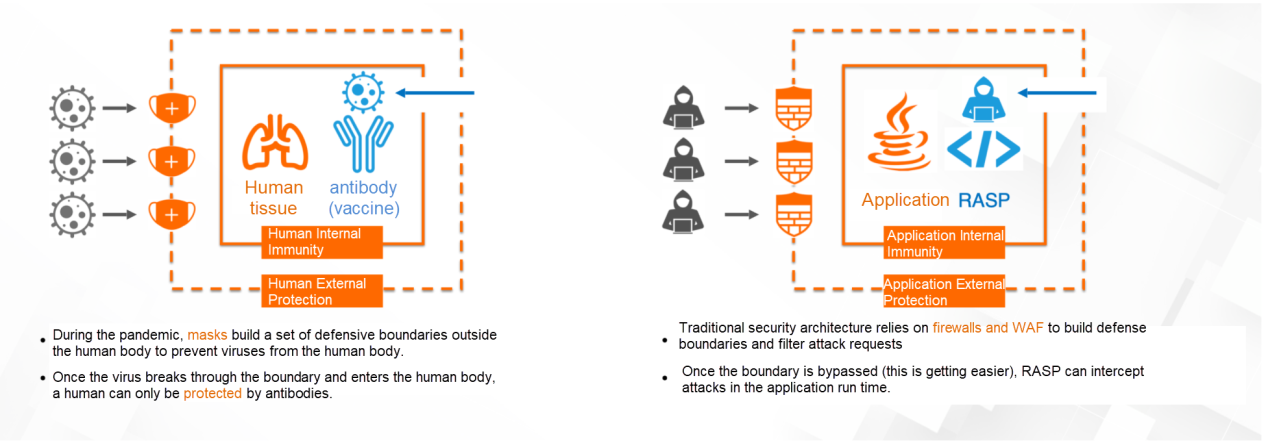
Take human virus protection as an example. Masks isolate external viruses from the body. Likewise, firewalls protect the system by analyzing and identifying dangerous external traffic. RASP technology is similar to human vaccine antibodies that do not need to care about the way the virus enters. It is deployed on the server terminal with the application startup and can identify and intercept attacks. RASP is designed to narrow the gaps left by application security testing and network boundary control. It penetrates the application's running environment and understands the flow of data and events in real-time to monitor or prevent new threats that fail to be foreseen during development.
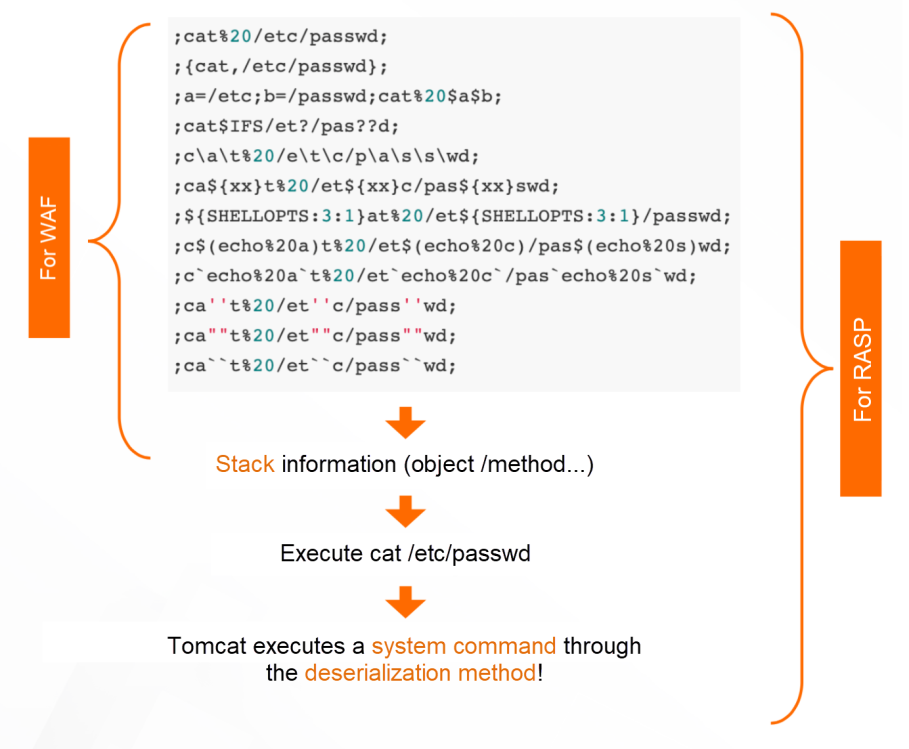
Generally, WAF can only see the traffic content at the entrance-user's original request. It is unable to notice how the application will execute this request. Therefore, some misinformation is generated. For example, users upload a SQL statement (misinformation) in online documents. Messages using PHP vulnerabilities are typed into the JAVA environment (misrepresentation). The application itself is precompiled, and there is no short command execution such as SQL injection points (misrepresentation) and ls, which is easy to be confused with normal input (misinformation).
In contrast, RASP only reports effective attacks that can be exploited. In principle, RASP focuses on run time behavior, not the source and form of traffic. It does not need to modify the code. With the application startup in Agent mode, the underlying key functions and parameter contents of Hook applications are combined with request context, semantic analysis, baseline, and other means to determine whether the current application behavior is at risk. From a strategic point of view, since the application behavior is countless relative to the ever-changing attack characteristics, the defense effect of RASP against 0day and various deformation attack methods is better than that of WAF and other means that use "characteristics" as the detection object. In addition, encryption and other methods are deforming the input content to bypass feature-based detection. RASP will also ignore it, forming a dimension reduction attack.
Both RASP and WAF can detect traffic and content and terminate user sessions. What are their differences?
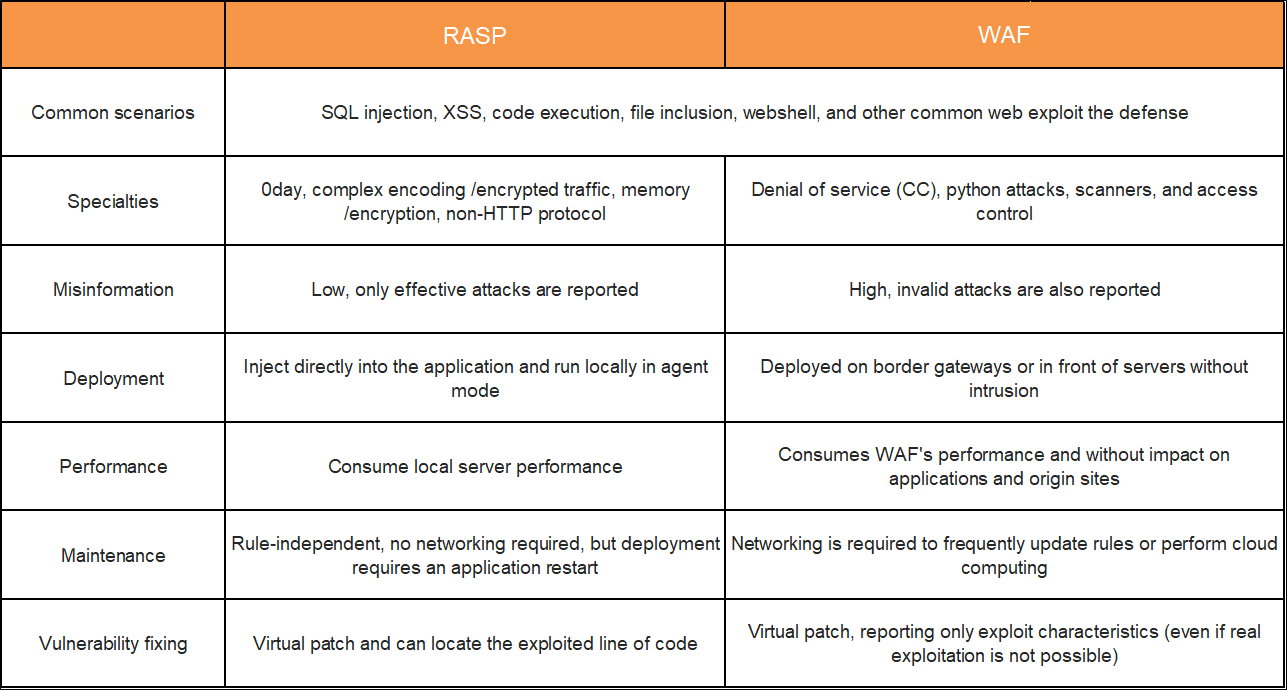
Next, we compare the differences between RASP and WAF from multiple perspectives such as scenarios, false reports, and maintainability. As can be seen from the preceding table, common WEB vulnerabilities such as SQL injection, XSS (cross-site scripting), code execution, and webshell have certain defense capabilities. As the ingress layer, WAF is better at the denial of service attacks, python attacks, scanners, and access control scenarios, while RASP runs with business processes and is better at scenarios such as 0day, complex encoding /encryption, memory /password addition, and non-HTTP protocols, and has the following features:
In conclusion, RASP is closer to cloud-native and can be used as a "distributed firewall" to break the limitation of WAF border protection and conform to the concept of zero-trust security. However, WAF is based on border security and has a wide range of protection. RASP fails to support the protection of Nginx, Apache, and other front servers.
Therefore, RASP and WAF have scenes that they are good at. They use their scenes to form a multi-layered defense in depth by complementing each other to achieve the best results.
Next, let's learn about the security protection methods provided by ARMS application security based on the Alibaba Cloud RASP and the function of using a deserialization vulnerability.
With the development of business container technology and serverless technology, the development cycle and function iteration frequency of business are getting faster, while the lag of security capabilities is becoming obvious. For example, it is difficult to upgrade old middleware with vulnerabilities. Insufficient evaluation of three-party components may introduce high-risk vulnerabilities. If there are security vulnerabilities in the code, you need to quickly locate and fix them. As an extension of DevOps, DevSecOps should pay more attention to security. Excellent DevSecOps tools should maximize security automation and reduce business intrusiveness. However, ARMS pays attention to the security of the application after its release and launch. It is friendly to DevSecOps and provides a complete security solution. It improves the security of the business 7x 24 hours without introducing additional burden to affect the business development. It changes the opposition between business and security.
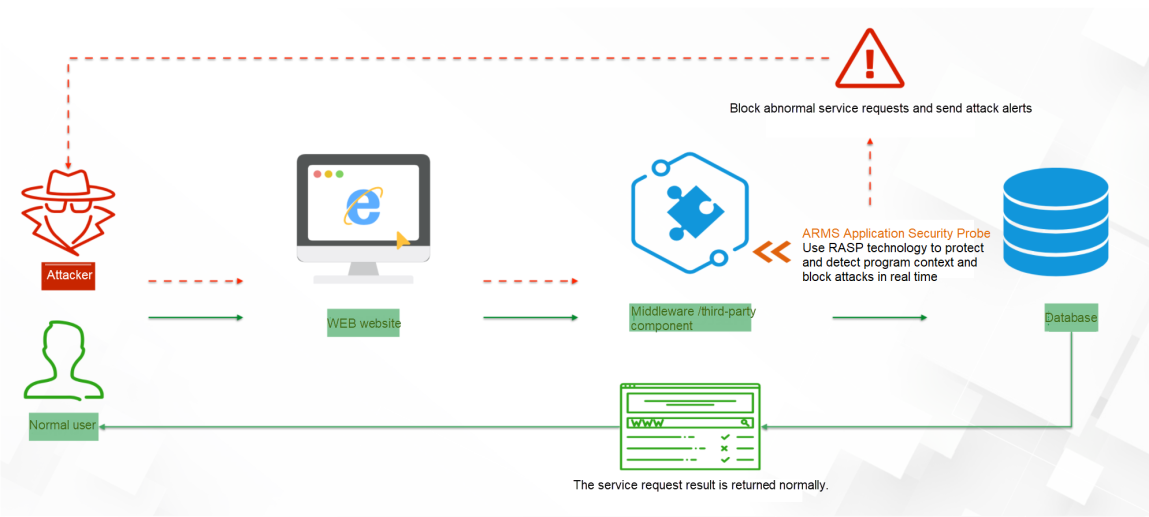
ARMS application monitoring probe integrates Alibaba Cloud security RASP technology and injects "security vaccine" into the application through tracking point technology. You only need to enable access to application security with one click, and you can identify dangerous attacks by hackers to intercept alerts without affecting normal customer requests. It is like an invisible security guard that guards the security of your application at all times. Next, let's take a detailed look at the attack protection statistics and the hazardous component detection function.
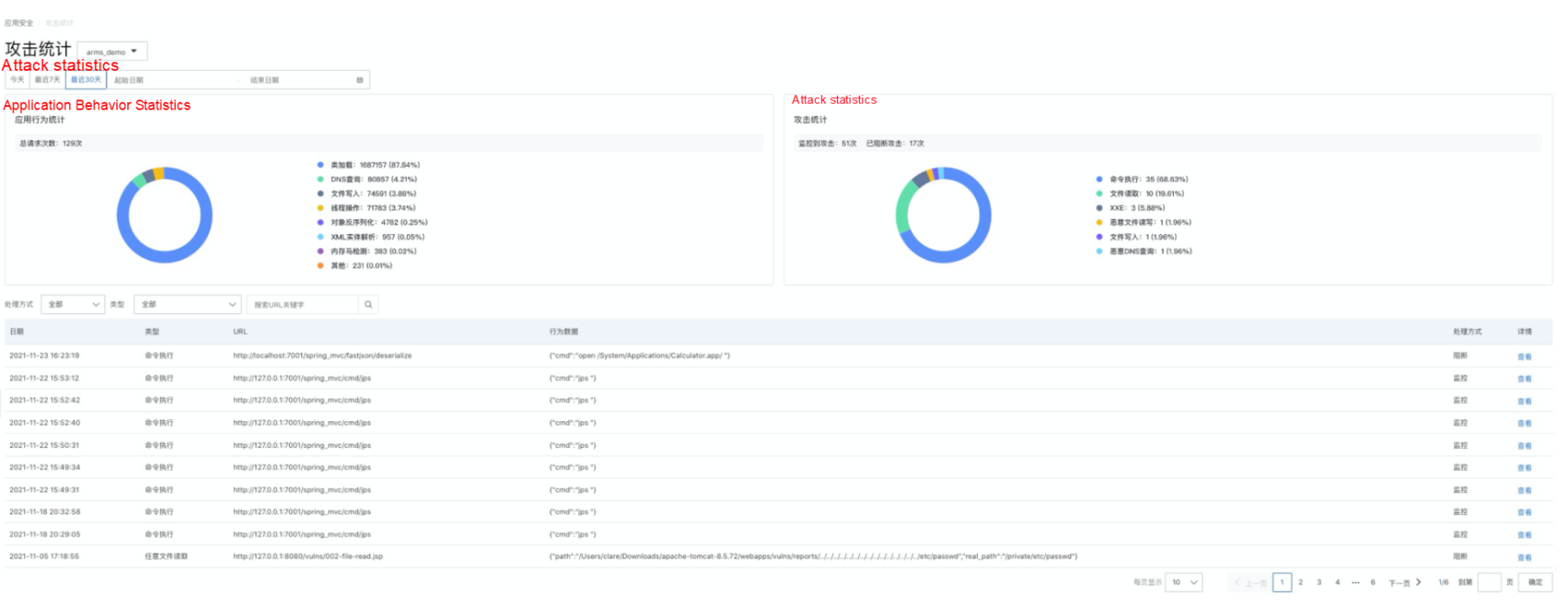
In many scenarios, after receiving security alerts at the traffic level, it is difficult to correlate with the actual vulnerability code location. ARMS security integrates the Alibaba Cloud security RASP technology in the application monitoring probe. After users enable security protection, they can receive attack alerts once a security attack occurs. Currently, it supports the detection of up to 15 types of attack scenarios, such as command execution vulnerabilities, file access vulnerabilities, network access vulnerabilities, memory horse bypass, JN injection, and malicious reflection calls.
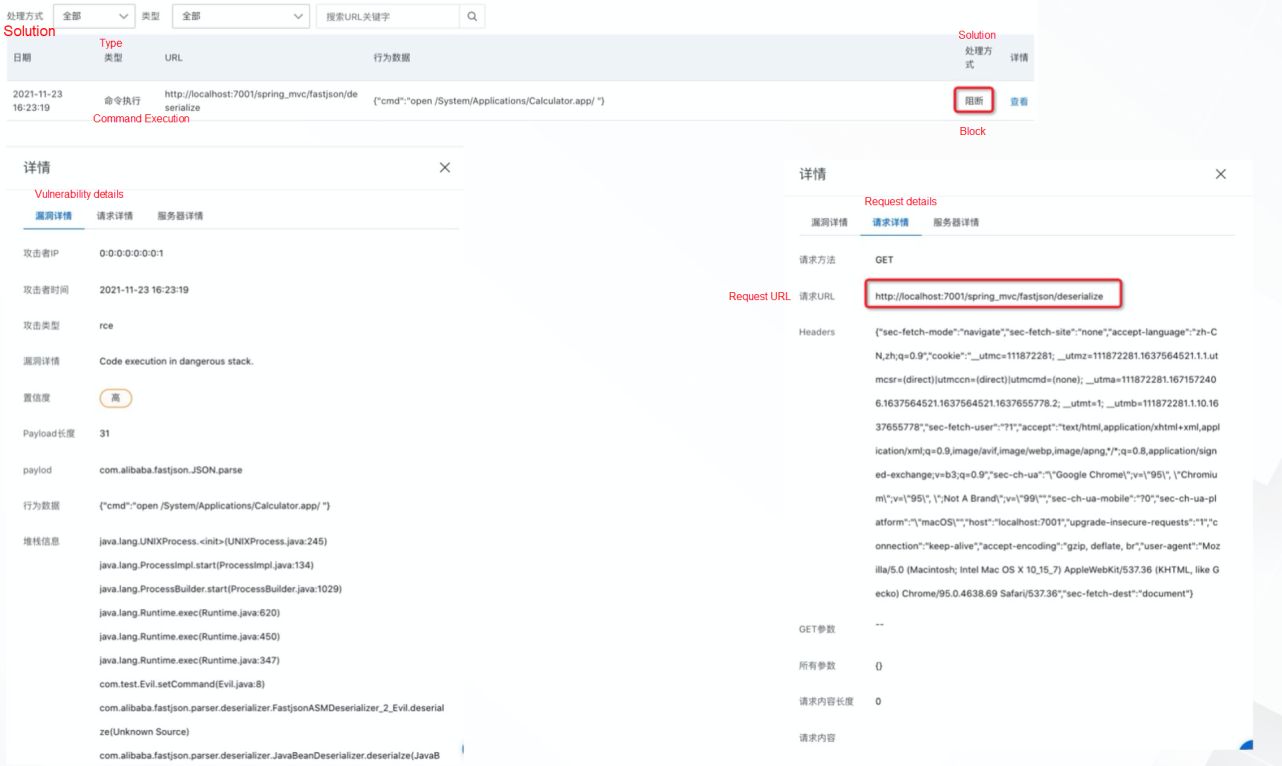
On the Attack Statistics page, ARMS provides statistics of normal behaviors and attack behaviors of applications. This allows you to learn whether attacks have occurred recently. If an attack is detected, you can also view the attack occurrence time, attack type, request URL, context data, and the result of the attack by page (monitoring or blocking depends on your protection settings). Click to view the attack source IP address, detailed parameters, machine, and other information, and further locate the code vulnerability location by analyzing the code stack for repair.
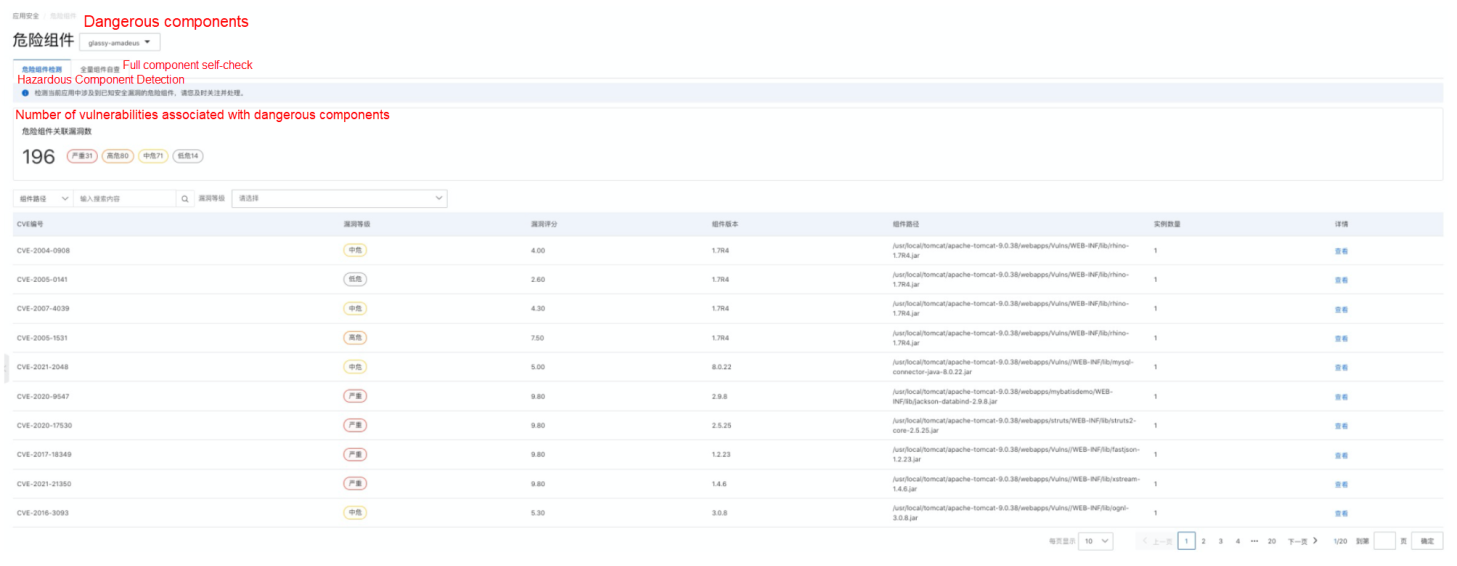
JAVA applications often rely on a large number of three-party open source components and various middleware frameworks. These components often have unknown vulnerabilities that are difficult to find and inventory, and applications are not clear about whether they may have high-risk vulnerabilities. The dangerous component detection feature provided by ARMS application security can help relieve this concern. Once an application is integrated with a probe and connected to application security, ARMS detects the three-party component dependencies, analyzes and associates authoritative CVE vulnerability libraries, and distinguishes different vulnerability risk levels. Customers can prioritize component upgrades to resolve high-risk vulnerabilities based on vulnerability fixing suggestions in the details.
For vulnerabilities that have not yet been included in CVE, when a new vulnerability is reported, clients can use the keyword search to check whether the component version they rely on is related to the security vulnerability through the "full component self-examination" function. Then clients can know and determine whether they need to deal with it.
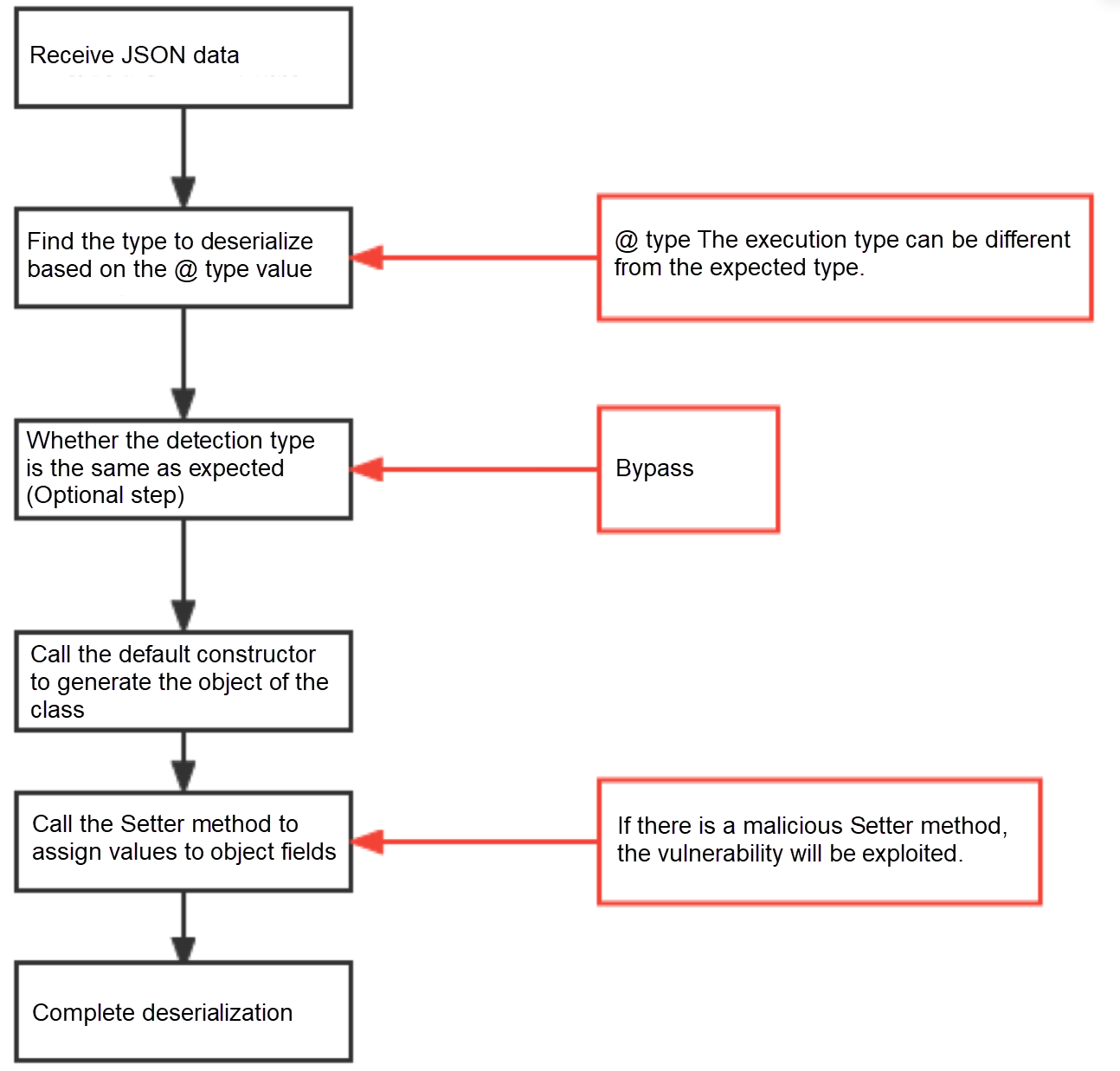
Next, we use the attack scenario of fastjson deserialization to demonstrate the actual protection effect of ARMS application security. The following is the deserialization process:
User:
package com.test;public class User { private String name; public void setName(String Name) { this.name = Name; } public String getName() { return name; }}Malicious:
package com.test;import java.io.IOException;public class Evil {
//Malicious Setter
public void setCommand(String command) throws IOException
{ Runtime.getRuntime().exec(command);
}
}Deserialized content:
{
"rand": {
"@type": "com.test.Evil",
"command": "open /System/Applications/Calculator.app/"
}
}Deserialized vulnerability code:
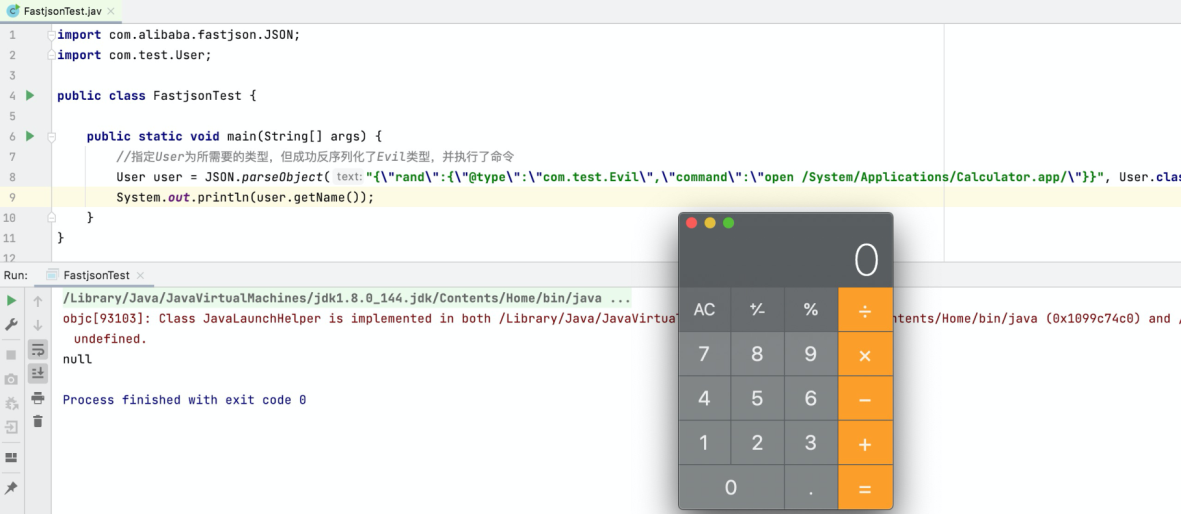
public static void main(String[] args) {
// Specify User as the required type, but deserialize the Evil type and executed the command
User user = JSON.parseObject("{\"rand\":{\"@type\":\"com.test.Evil\",\"command\":\"open /System/Applications/Calculator.app/\"}}", User.class);
}When the preceding code is executed, setting the User property during deserialization triggers command execution. In this article, an internal application will be open, which may cause greater harm by obtaining system configurations and accessing sensitive information in real attack scenarios.
When ARMS application security is enabled and the preceding anti-sequence vulnerability occurs, ARMS application security recognizes the command execution behavior generated by the serialization vulnerability. You can block the deserialization action and send an alert notification. You can further analyze the attack source and vulnerability code location.
The core of fastjson deserialization is to find classes that can cause code execution. There are a large number of available classes in java's huge jdk class library and third-party class library. Traditional traffic products such as WAF often need to exhaust these classes that may be used in defense (omissions often occur). While ARMS application security is based on RASP's context analysis capability and behavior-based attack discovery method. All the code execution, malicious file upload, and sensitive file reading and writing caused by fastjson will be captured without the need to accurately match specific code implementation, so there is no possibility of being bypassed at all.
Based on the preceding cases, it can be seen that the overall product advantages of ARMS application security. ARMS application security supports 0day defense, attack alerts, and traceability. It supports dangerous component detection and provides vulnerability fix suggestions. It can be enabled with one click and there is no need to modify the code. It supports soft fuse escape to avoid affecting the application and Monitoring mode experience. According to the stress test, after the application security prevention mode is enabled, the average CPU overhead increases by less than 1%. The memory usage is less than 30M. The average RT takes milliseconds, and the impact on system performance is low. You can use the protection settings to select the observation or interception mode, customize the attack detection type, and customize the detection timeout period to further reduce the performance impact.
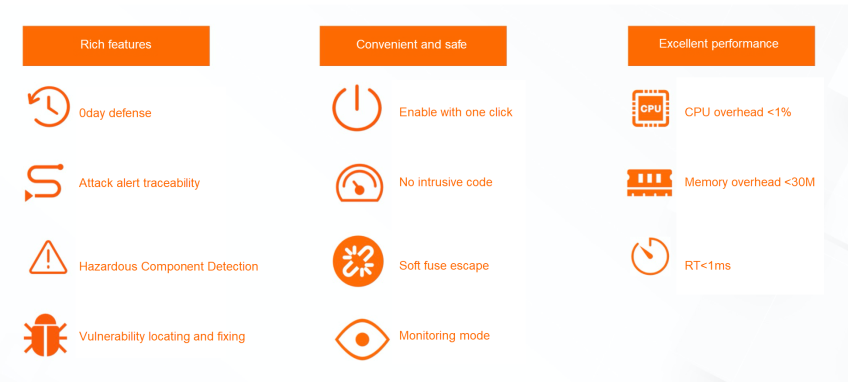
By integrating self-protection capabilities in ARMS application security run time, you can inject "vaccines" into your applications to implement application default security against daily OWASP attacks. By default, it defends against new vulnerabilities such as fastjson (0day), memory code, encryption code. It can detect high-risk vulnerabilities of three-party components and trace the attack behavior to locate and fix problems.
Check out the product page: Alibaba Cloud's Application Real-Time Monitoring Service (ARMS)
Alibaba Cloud ACK One and ACK Cloud-Native AI Suite Released
Cloud Forward: Cloud-Native Container Platform Episode 1 | ACK

212 posts | 13 followers
FollowAlibaba Cloud Native - August 14, 2024
Alibaba Cloud Community - March 4, 2022
Alibaba Clouder - July 10, 2020
Alibaba Clouder - February 7, 2018
Alibaba Clouder - November 7, 2017
Alibaba Clouder - January 28, 2021

212 posts | 13 followers
Follow Application Real-Time Monitoring Service
Application Real-Time Monitoring Service
Build business monitoring capabilities with real time response based on frontend monitoring, application monitoring, and custom business monitoring capabilities
Learn More WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More IT Services Solution
IT Services Solution
Alibaba Cloud helps you create better IT services and add more business value for your customers with our extensive portfolio of cloud computing products and services.
Learn More Enterprise IT Governance Solution
Enterprise IT Governance Solution
Alibaba Cloud‘s Enterprise IT Governance solution helps you govern your cloud IT resources based on a unified framework.
Learn MoreMore Posts by Alibaba Cloud Native