By Shantanu Kaushik
Hybrid Cloud adoption is growing day by day. Many enterprises are in the middle of making the shift if they haven't made the shift already. Like any other product or service that handles large amounts of data or is a connected resource based on an IT infrastructure, a Hybrid Cloud also needs to have good security practices associated with it.
As an IT administrator, one needs to think about a viable protection mechanism for the infrastructure, data, and applications that are running on the Hybrid Cloud setup. Cloud Bursting or workload portability being the primary feature of the hybrid cloud solution, securing the overall data flow across cloud environments, such as public and private clouds, becomes an essential practice.
Let’s start by looking at the security model implemented by Alibaba Cloud:
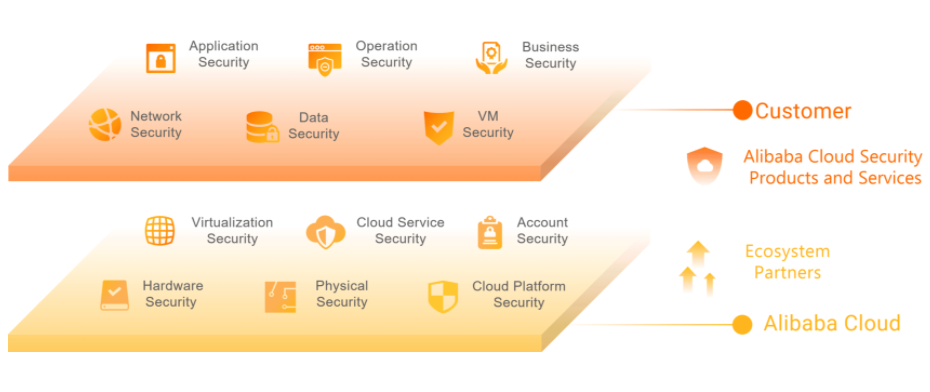
The Hybrid Cloud solution leverages the security of the private cloud and gives an option where the administrator can choose to not share any sensitive or critical data over the public cloud. With Alibaba Cloud Hybrid Cloud, you can make a management policy that enables you to choose how and where you wish your workload to be processed. It can be based on any policy, compliance, or security requirements.
The Hybrid Cloud is technically a group of different products and solutions that share functionality and environments to deliver a hybrid solution. These are separate entities, and when used separately, they have their own workflow, just like implementing containers or using DevOps. The Hybrid Cloud uses containers and APIs to interact and work with these entities. This enables the organizations to shift through the workload by assigning tasks to different resources based on the criticality of the workload and security associated with it.
Data protection is among the key concerns faced by any IT service that handles large amounts of data. The cloud is no different. Even though a private cloud is a physical resource located on-premise, it still is a cloud resource that could be vulnerable to attacks or issues.
The Hybrid Cloud solution leverages the benefits and functionalities of both public and private clouds. This enables it to take advantage of benefits like reduced security vulnerabilities, direct benefits of a private cloud setup. However, additional security measures must be in place based on an assessment of how secure and critical your data requirement is.
Let’s take a look at the data flow from an administrator using the Hybrid Cloud solution:
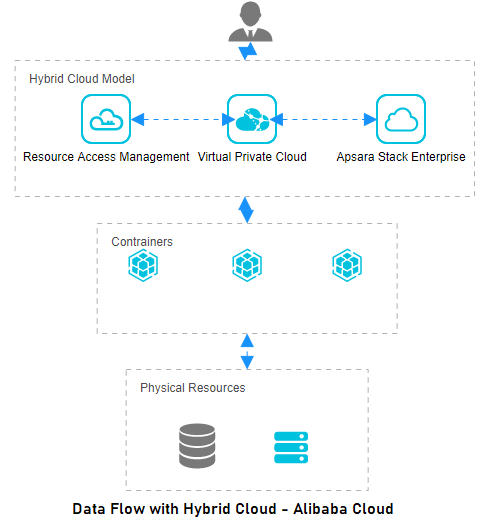
Data encryption at every stage. Be it and idle start or during transmission
Use of RAM (Resource Access Management) for Identity and Access Control.
Use of APIs
Security Updates and User Bulletins
Security vulnerabilities and patching practices are often defined as a race. Any network or cloud service may become vulnerable to threats and attacks at any point. With automation in monitoring, assessment, and patching of a lot of issues listed above can be reduced.
Monitoring your hybrid cloud solution to have regular assessment reports and threat analysis is among the top practices to implement. There are products within Alibaba Cloud’s product and service lineup that provide seamless threat analysis and solutions to counter them. There are also risks due to cloud service downtime. The Cloud Monitor helps you collect metrics related to your cloud practice to depict the true status of your cloud.
Let’s list some of the best practices for Monitoring and Risk Assessment:
Automation keeps you ahead of the game. Manual monitoring caps the possibility of a self-sustaining system. It reduces the overall productivity of the whole system as manual patching and configuration across teams needs to be a complete in-sync cycle. Automation responds to this challenge in a more hands-on and transparent manner.
An automation practice must include:
A hybrid cloud setup is location independent and may span across locations. It depends on where your private cloud is deployed. As an administrator, the best practice is to have good Service Level Agreements (SLAs). Choose your cloud resource provider based on the type of services and security they offer. Reliable service providers have reliable physical resources.
I have chosen Alibaba Cloud for all of my hybrid cloud requirements, based on their massive and secure infrastructure.
The views expressed herein are for reference only and don't necessarily represent the official views of Alibaba Cloud.

2,600 posts | 750 followers
FollowAlibaba Clouder - October 29, 2020
Alibaba Clouder - March 10, 2021
Alibaba Clouder - March 30, 2021
Hironobu Ohara - February 3, 2023
Alibaba Clouder - October 29, 2020
Alibaba Clouder - April 23, 2021

2,600 posts | 750 followers
Follow Robotic Process Automation (RPA)
Robotic Process Automation (RPA)
Robotic Process Automation (RPA) allows you to automate repetitive tasks and integrate business rules and decisions into processes.
Learn More Hybrid Cloud Solution
Hybrid Cloud Solution
Highly reliable and secure deployment solutions for enterprises to fully experience the unique benefits of the hybrid cloud
Learn More Hybrid Cloud Storage
Hybrid Cloud Storage
A cost-effective, efficient and easy-to-manage hybrid cloud storage solution.
Learn More Function Compute
Function Compute
Alibaba Cloud Function Compute is a fully-managed event-driven compute service. It allows you to focus on writing and uploading code without the need to manage infrastructure such as servers.
Learn MoreMore Posts by Alibaba Clouder