ログが異なるクラウドサービス、サードパーティツール、または自己管理アプリケーションに分散していると、統一された脅威検出やセキュリティ分析の実施が困難になります。Agentic SOC は、あらゆるソースからのログデータを一元的に収集、標準化、分析するための統合センターを提供します。これにより、技術環境全体に一貫した検出ルールを適用でき、包括的なセキュリティビューの提供と効率的な脅威レスポンスが可能になります。
仕組み
Agentic SOC は、モジュール式の構成システムを使用して、生ログの統合と標準化を自動化します。この中核となる原則は、以下の主要コンポーネントが連携して機能することに基づいています。
Data Source:Alibaba Cloud の Simple Log Service (SLS) におけるプロジェクトや Logstore など、生ログのストレージ場所を指定します。
説明Agentic SOC は、Agentic SOC Dedicated Collection Channel、User Log Service、および Security Center Log Serviceをサポートしています。詳細については、「データソースタイプの比較」をご参照ください。
Standardized Rule:
Standardization Method:ログが標準化された後の処理およびアクセスに関する技術的なパターンを指定します。
説明サポートされている方式はReal-time ConsumptionとScan Queryです。詳細については、「標準化方式の比較」をご参照ください。
Access Policy:ログ取り込みフローの中核となる構成です。Data Source、Standardization Method、およびStandardized Ruleの構成を関連付け、ログの読み取り、解析、処理方法を指定します。これにより、自動的なログの取り込みと標準化が可能になります。
Alibaba Cloud プロダクトの統合
このプロセスは、Web Application Firewall (WAF)、Cloud Firewall (CFW)、ActionTrail など、既にご利用の SLS Logstore にログを配信している Alibaba Cloud プロダクトに適用されます。
統合フローチャート
ステップ 1:プロダクトログ配信の有効化
ログを統合する前に、対象のクラウドプロダクトのログ監査機能を有効にし、そのログを SLS に配信する必要があります。これにより、Agentic SOC がデータを読み取れるようになります。
中央 Logstore にある Alibaba Cloud セキュリティプロダクトのアラートログの場合、データは自動的に Agentic SOC に配信されます。クラウドプロダクトのログサービスを有効にしなくても統合を完了できます。例として、WAF のアラートログや Cloud Firewall のアラートログが挙げられます。
WAF や CFW などのクラウドプロダクトのコンソールに移動し、[ログ管理] または [Simple Log Service] のエントリーポイントを見つけます。詳細については、「Alibaba Cloud プロダクトログを SLS に統合するための関連資料」をご参照ください。
プロダクトドキュメントに従ってログ配信を有効にします。この操作により、通常、SLS にプロジェクトと 1 つ以上のLogstoreが自動的に作成されます。
説明Simple Log Service コンソールにログインして、プロダクトから配信されたログのProjectとLogstoreを表示できます。たとえば、WAF ログのプロジェクト名は通常
wafnew-logstoreです。
ステップ 2:組み込みアクセスポリシーの有効化
一括での自動有効化
Agentic SOC は、Alibaba Cloud プロダクトからのログの一括統合をサポートしています。この機能により、アクセスポリシーの有効化とデータソースの検出を自動化できます。手順は以下の通りです。
コンソールへのログイン
Security Center コンソール - Agentic SOC - 統合センターに移動します。ページ左上で、アセットが所在するリージョンを選択します:Chinese MainlandまたはOutside Chinese Mainland。
一括統合の設定
Batch Associate Settingsをクリックし、指示に従って設定を完了します。
Access Settings:
Increment Access:有効になっているすべてのアクセスポリシーを保持し、現在の構成からデータソースとポリシーのみを追加します。
Full Access:既存のすべてのアクセス設定を上書きして置き換えます。現在の構成で選択されていないポリシーは無効になります。
警告これは上書き操作であり、実行中のポリシーを誤って無効にし、データ統合の中断につながる可能性があります。注意して進めてください。
Accessible Account:現在のアカウントとそのメンバーアカウントを選択します。
Alibaba Cloud Services:接続するクラウドプロダクトと、それに対応するデータソースを選択します。
説明構成を簡素化するため、Agentic SOC には推奨アクセスポリシーが含まれています。Use Recommended Policyをクリックすると、システムはベストプラクティスに基づいて、選択されたクラウドプロダクトに対して最も分析価値の高いデータソースを自動的に選択します。これにより、データ分析を迅速に有効化できます。
Auto-Add New Data Sources:このオプションを有効にすると、システムは新しい Logstore を現在のデータソースの収集範囲に自動的に含めます。手動で追加する必要はありません。
データ統合の確認と開始
設定が完了したら、OK をクリックします。システムは自動的に以下の操作を実行します。
完全統合:選択されたアカウント内の、選択されたクラウドプロダクトデータソースに関連付けられているすべての有効な Logstore を SLS 内で自動的に統合します。
ポリシーのアクティベーション:選択されたデータソースに対応するアクセスポリシーを自動的に有効にします。
重要新しいアクセスポリシーのデプロイと初期化には時間がかかる場合があります。プロセスが完了するまでお待ちください。
有効化状態の確認
アクセスリストに戻り、アクセスするプロダクトを選択し、[操作] 列の アクセス設定をクリックします。
説明メンバーアカウントの場合、Multi-account Access Settingsの [アクセスポリシー] タブで、対象のデータソースの [操作] 列にある Multi-account Accessをクリックします。
[アクセスポリシー] リストページでアクセス状態を確認できます。状態が異常な場合は、データソースのステータスを確認してください。詳細については、「データソースの接続状態の確認」をご参照ください。
手動での有効化
データソースの設定
Agentic SOC には、主要な Alibaba Cloud プロダクト用のデータソースが事前設定されています。これらの設定を確認し、ご利用の Logstore 情報と一致していることを確認する必要があります。
クラウドプロダクトの検索
Security Center コンソールにログインし、[Agentic SOC] > [統合センター] に移動します。ページ左上で、アセットが所在するリージョンを選択します:Chinese MainlandまたはOutside Chinese Mainland。
プロダクトアクセスタブで、Service ProviderフィルターをAlibaba Cloudに設定し、統合するプロダクト (例:Web Application Firewall) を選択して、[操作] 列のアクセス設定をクリックします。
データソースのステータス確認
プロダクトに関連付けられているデータソースの名前をクリックします。ページがデータソースタブにリダイレクトされます。
データソースを見つけ、その接続状態を確認します。
正常:Agentic SOC が Logstore にアクセスできることを示します。次のステップに進むことができます。
異常:設定が正しくないことを示します。データソースのアクション列にある編集をクリックし、以下の情報を確認します。
インスタンス情報:ステップ 1 で記録したリージョン、プロジェクト、Logstoreが正確に一致しているか確認します。
ソースログサービス:SLS Logstore サービスが実行中であることを確認します。たとえば、プロジェクトが無効になっておらず、ログが引き続き書き込まれていることなどです。
未接続:データソースが設定されていないことを示します。
データソースのアクション列にある編集をクリックします。
Create Instanceをクリックし、ステップ 1 で自動的に作成された Logstore 情報 (Region ID、Project、Logstore) を選択します。
組み込みアクセスポリシーの有効化
ログ処理パイプラインを開始して、Agentic SOC がプロダクトログを自動的に分析できるようにします。
プロダクトアクセスタブに戻り、再度プロダクトのアクセス設定ページに移動します。
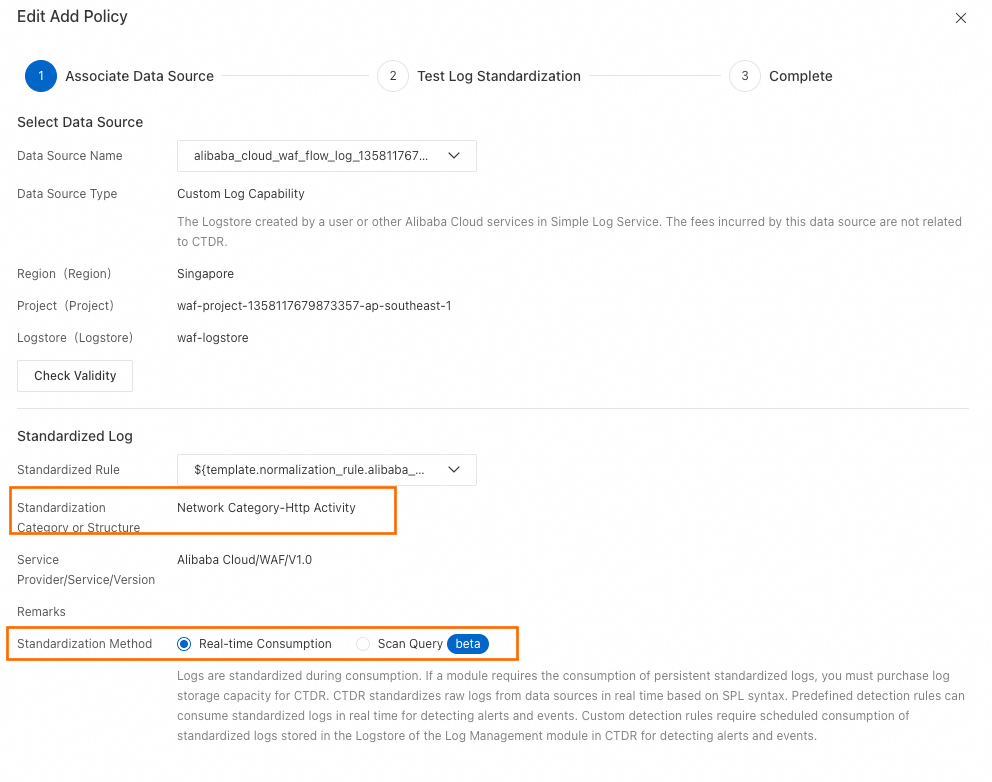
標準化方式の変更 (任意)
一部のプロダクトポリシーでは、編集ページでStandardization Methodを変更できます。サポートされている方式はReal-time ConsumptionとScan Queryです。詳細については、「標準化方式の比較」をご参照ください。
重要データソースタイプがSecurity Center Log Serviceまたはアラートログの場合、標準化方式はReal-time Consumptionとなり、変更できません。
Standardization Category or Structureに関連付けられたデータセット (StoreView) に、既に 5 つの「Scan Query」パターンのアクセスポリシーがアタッチされている場合、現在のポリシーには「Real-time Consumption」を選択する必要があります。そうしないと、アクセスポリシーを有効にできません。
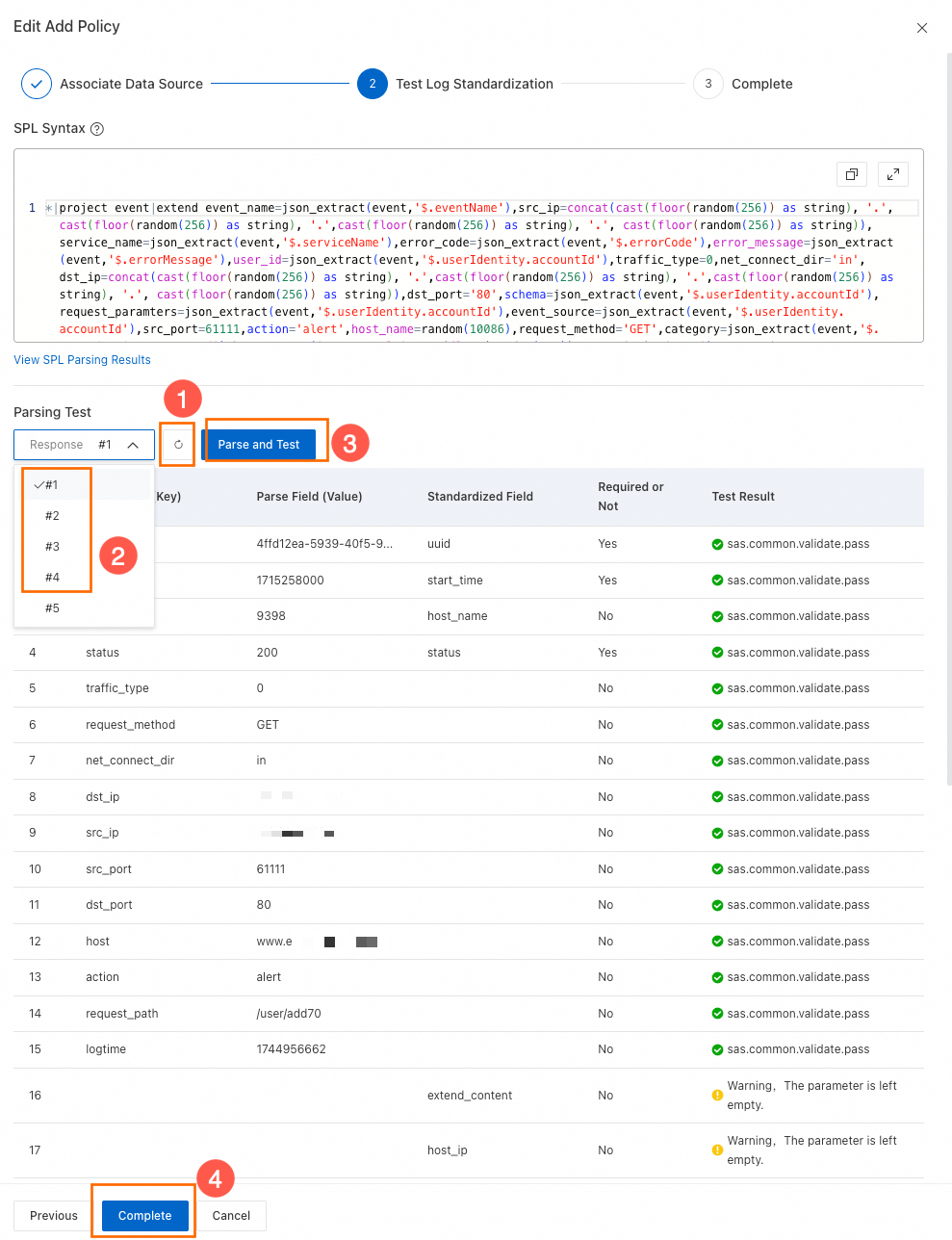
ログ標準化テスト
標準化方式を変更した場合は、ログ標準化テストを実行する必要があります。
警告Data SourceのLogstoreにデータが含まれていることを確認してください。Logstore が空の場合、ログ標準化テストは実行できません。
 ボタンをクリックします。システムは SPL 構文を使用してログデータを解析し、結果を返します。
ボタンをクリックします。システムは SPL 構文を使用してログデータを解析し、結果を返します。結果のドロップダウンリストから項目を選択してテストデータとして使用し、Parse and Testをクリックします。
テストに合格したら、完了をクリックします。
説明テストに失敗した場合は、「ログ標準化テストに失敗した場合やデータが解析できない場合はどうすればよいですか?」で解決策をご参照ください。
ポリシーの有効化
ポリシーのEnabling Status列のスイッチをオンにします。
重要Agentic SOC の購入時に推奨アクセスポリシーを有効にした場合、Security Center、WAF、Cloud Firewall、および ActionTrail の組み込みポリシーはデフォルトで有効になります。推奨アクセスポリシーを有効にするには、「サブスクリプションのアクセスポリシーを有効にする」および「従量課金のログアクセスポリシーを有効にする」をご参照ください。
ステップ 3:新しいアクセスポリシーの追加 (任意)
一部のプロダクトはカスタムアクセスポリシーをサポートしています。カスタムアクセスポリシーを追加する手順は以下の通りです。
アクセスポリシーリストで、Create Access Policyをクリックします。
説明Create Access Policyボタンが表示されない場合、そのプロダクトはこの機能をサポートしていません。
[アクセスポリシーの作成] ページで、Data Source、Standardized Rule、およびStandardization Methodを選択します。適切なデータソースや標準化ルールがない場合は、新しいデータソースとカスタム標準化ルールを作成できます。
重要現在のアカウントに属するデータソースのみ選択できます。メンバーアカウントのデータソースはサポートされていません。
Test Log Standardizationを完了し、ポリシーを有効にします。
サードパーティログの統合
Agentic SOC は、Fortinet、Chaitin、Microsoft、Sangfor、Tencent Cloud、HUAWEI CLOUD、Hillstone Networks、Knownsec、Microsoft Cloud などのサードパーティクラウドや、カスタムプロダクトアプリケーションからのログ統合をサポートしています。手順は以下の通りです。
サードパーティクラウドプロダクトからのログ統合
SLS にないログ
Tencent Cloud および HUAWEI CLOUD の WAF および CFW プロダクトについて、Agentic SOC はログ統合を支援するデータインポート機能を提供します。
適用範囲
クラウドプロバイダー | プロダクト | ログタイプ |
Tencent Cloud | Web Application Firewall (WAF) | 攻撃ログ、アクセスログ |
Cloud Firewall (CFW) | アラートログ | |
HUAWEI CLOUD | Web Application Firewall (WAF) | 攻撃ログ、アクセスログ |
Cloud Firewall (CFW) | アラートログ |
統合フローチャート
手順
データソースの作成
サードパーティのクラウドログデータ用に専用の Agentic SOC データソースを作成します。既に作成済みの場合は、このステップをスキップできます。
Security Center コンソール - 脅威分析とレスポンス - 統合センターに移動します。ページ左上で、保護したいアセットのリージョンを選択します:Chinese MainlandまたはOutside Chinese Mainland。
Data Sourceタブで、Tencent Cloud のログを受け取るためのデータソースを作成します。詳細については、「データソースの作成:SLS にないログ」をご参照ください。
Source Data Source Type:User Log ServiceまたはAgentic SOC Dedicated Collection Channelを選択します。詳細については、「データソースタイプの比較」をご参照ください。
インスタンス接続:データを分離するために、新しいLogstoreを作成することを推奨します。
データのインポート
HUAWEI CLOUD ログデータのインポートおよびTencent Cloud ログデータのインポートを参照し、ステップ 1 で作成したデータソースにサードパーティのクラウドデータをインポートします。
アクセスポリシーの設定
プロダクトアクセスタブに戻り、Service Providerフィルターを HUAWEI CLOUD などのサードパーティベンダーに設定します。
対象プロダクトの [操作] 列で、アクセス設定をクリックします。アクセスポリシーの詳細ページで、Create Access Policyをクリックします。
以下のようにデータソースを設定します。
Data Source Name:ステップ 1 で作成したデータソースを選択します。
Standardized Rule:HUAWEI CLOUD または Tencent Cloud と互換性のある、Agentic SOC が提供する組み込みの標準化ルールを選択することを推奨します。
説明また、「標準化ルールとデータセット」を参照して、カスタム標準化ルールを作成することもできます。
Standardization Method:Real-time Consumptionのみがサポートされています。Scan Queryはサポートされていません。
Test Log Standardizationページで、Parse and Testをクリックします。詳細については、「ログ標準化テスト」をご参照ください。
警告Data Sourceに対応するLogstoreにデータが含まれていることを確認してください。そうでない場合、ログ標準化テストは実行できません。
テストに合格したら、完了をクリックします。その後、ポリシーを有効にします。
SLS にあるログ
Logtail や Syslog-ng などの方法を使用して、Fortinet、Chaitin、Sangfor などのサードパーティプロダクトのログを既に SLS Logstore に収集している場合、取り込みフローは以下のようになります。SLS へのデータ取り込み方法については、「データ収集の概要」をご参照ください。
データソースの設定
統合プロダクトの検索
Security Center コンソール > Agentic SOC > 統合センターに移動します。ページ左上で、保護したいアセットが所在するリージョンを選択します:Chinese MainlandまたはOutside Chinese Mainland。
Service Providerフィルターをサードパーティベンダー (HUAWEI CLOUD など) に設定します。統合するプロダクト (Web Application Firewall など) を選択し、右側の [統合設定] をクリックします。
データソースの変更
プロダクトに関連付けられているデータソースの名前をクリックします。データソースタブにリダイレクトされます。次に、データソースのアクション列にある編集をクリックします。
Create Instanceをクリックし、サードパーティプロダクトのログが保存されているRegion ID、Project、およびLogstoreを選択します。
説明Simple Log Service コンソールにログインして、クラウドプロダクトの Logstore 情報を表示できます。
組み込みアクセスポリシーの有効化
プロダクトアクセスタブに戻り、再度プロダクトのアクセス設定ページに移動します。
対象の組み込みアクセスポリシーの [操作] 列にある編集ボタンをクリックします。Test Log Standardizationページで、Parse and Testをクリックします。詳細については、「ログ標準化テスト」をご参照ください。
テストに合格したら、完了をクリックします。その後、ポリシーを有効にします。
カスタムプロダクトアプリケーションからのログ統合
統合フローチャート
プロダクトの追加
Security Center コンソール - Agentic SOC - 統合センターに移動します。ページ左上で、アセットが所在するリージョンを選択します:Chinese MainlandまたはOutside Chinese Mainland。
プロダクトアクセスタブのMulti-cloud Service Accessエリアで、Add Serviceをクリックし、Vendor NameとService Nameを入力します。
データソースの追加
Data Sourceタブで、Add Data Sourceをクリックします。詳細については、「データソース」をご参照ください。以下のパラメーターを設定します。
プロダクトログが既に SLS に収集されている場合、Data Source TypeをUser Log Serviceに設定し、対応する Logstore を選択します。
説明Simple Log Service コンソールにログインして、プロダクトの Logstore 情報を表示できます。
プロダクトログが SLS に収集されていない場合:
Data Source TypeをAgentic SOC Dedicated Data Collection Channelに設定すると、Agentic SOC は SLS に専用のプロジェクト (aliyun-cloudsiem-channel-AlibabaCloudUID-cn-RegionID) と専用の Logstore を作成します。
Agentic SOC は SLS に専用のプロジェクト (aliyun-cloudsiem-channel-AlibabaCloudUID-cn-RegionID) と専用の Logstore を作成します。
Data Source TypeをUser Log Serviceに設定した場合、まずSimple Log Service コンソールに移動し、対応する Logstore を作成する必要があります。
重要データソースが設定された後、「データ収集の概要」を参照するか、SLS ヘルプデスクに連絡してプロダクトログを収集し、対応する SLS Logstore に送信してください。
標準化ルールの追加
Standardized Ruleタブで、Create Custom Ruleをクリックします。詳細については、「カスタム標準化ルールの作成」をご参照ください。
説明ベンダーとプロダクトが、ステップ 1 で追加したプロダクトと一致していることを確認してください。
アクセスポリシーの追加と有効化
プロダクトアクセスタブに戻り、ステップ 1 で追加したプロダクトを見つけ、[操作] 列のアクセス設定をクリックします。
[取り込み設定] ページで、Create Access Policyをクリックします。[取り込みポリシーの作成] ページで、Data SourceとStandardized Logの以下のパラメーターを設定します。
Data Source:ステップ 2 で設定したデータソースを選択します。
Standardized Rule:ステップ 3 で設定したルールを選択します。
Standardization Method:サポートされている方式はReal-time ConsumptionとScan Queryです。詳細については、「標準化方式の比較」をご参照ください。
重要データソースタイプがAgentic SOC Dedicated Data Collection Channelの場合、Real-time Consumptionを選択します。
Test Log Standardizationページで、Parse and Testをクリックします。詳細については、「ログ標準化テスト」をご参照ください。
警告ご利用のData Sourceに対応するLogstoreにデータがあることを確認してください。Logstore が空の場合、ログ標準化テストは実行できません。
テストに合格したら、完了をクリックします。その後、ポリシーを有効にします。
統合データの分析
プロダクトログが統合された後、ログを分析し、アラートとセキュリティイベントを生成し、クラウドセキュリティリスクへの対応と処理を支援するために、脅威検出ルールを設定する必要があります。詳細については、「脅威検出ルールの設定」をご参照ください。
クォータと制限
スキャンクエリモードの制限:データセット (Standardized Ruleに関連付け) は、「Scan Query」モードで最大 5 つのアクセスポリシーにアタッチできます。
複数アカウント統合の制限:
メンバーアカウントからのログは、Real-time Consumptionモードでのみ取り込むことができます。Scan Queryはサポートされていません。詳細については、「複数アカウント管理機能」をご参照ください。
メンバーアカウントに属するデータソースに対して、カスタムアクセスポリシーを追加することはできません。
標準化方式の制限:データソースタイプがAgentic SOC Dedicated Collection Channelであるか、取り込まれるログタイプが「アラートログ」である場合、Real-time Consumptionのみがサポートされます。
課金情報
Agentic SOC を使用してログを統合すると、選択したデータソースタイプに応じて、以下の料金が発生する場合があります。
データソースタイプ | Agentic SOC 課金項目 | SLS 課金項目 | 注 |
Agentic SOC Dedicated Collection Channel |
説明 これらの項目はログアクセストラフィックを消費します。 | ログストレージと書き込み以外のサービス料金 (インターネットトラフィックなど)。 | Agentic SOC が SLS リソースを作成および管理するため、Logstore のストレージおよび書き込み料金は Agentic SOC によって課金されます。 |
User Log Service | ログの取り込みには料金が発生し、ログアクセストラフィックを消費します。 | ストレージ、書き込み、データ転送を含む、ログに関するすべてのコスト。 | SLS がすべてのログリソースを管理します。SLS はこれらのリソースに関するすべての料金を請求します。 |
Security Center Log Service | ログの取り込みはログアクセストラフィックを消費します。 | なし | これは Security Center の内部ログです。SLS 料金は適用されません。 |
関連資料
Standardization Methodの比較
比較ディメンション | Real-time Consumption | Scan Query |
仕組み | 書き込み時の標準化:Agentic SOC はデータソースからログを消費し、ログを標準化してから Agentic SOC のログスペースに保存します。 | 読み取り時のスキーマ適用 (Schema-on-read):レプリカを保存せずに、データソースインスタンスから直接ログを読み取ります。 |
主な利点 | 高いクエリパフォーマンスと高速な分析。 | 軽量なデプロイメントと低コスト。 |
ログストレージと料金 | Log Storage Capacity を購入すると、標準化されたログは自動的に Agentic SOC のログ管理に配信されます。この配信は、ご利用の Agentic SOC のLog Storage Capacity を消費し、無効にすることはできません。 | ログのレプリカは保存されません。ソース (SLS など) が生ログのストレージ料金を請求します。 |
適用可能なデータソースタイプ |
| User Log Service (アラートログを除く) |
パフォーマンスとクォータ | アクセスポリシーの数に制限はありません。 |
|
複数アカウントアクセス | サポートされています。 | サポートされていません。 |
シナリオの制限 | データソースが Agentic SOC 専用データ収集チャネルであるか、ログタイプがアラートログである場合、このパターンを選択する必要があります。 | なし |
Data Sourceタイプの比較
比較ディメンション | User Log Service | Agentic SOC Dedicated Collection Channel | Security Center Log Service |
ログのストレージと管理 | お客様自身で SLS プロジェクトと Logstore を管理します。 | Agentic SOC が専用の SLS プロジェクトと Logstore を自動的に作成・管理します。 | Security Center は、その内部ログをお客様の SLS に保存しません。 |
サポートされている標準化方式 | Real-time Consumption、Scan Query (アラートログを除く) | Real-time Consumption | Real-time Consumption |
ユースケース |
|
| Security Center の内部ログを分析します。 |
Alibaba Cloud プロダクトログを SLS に統合するための関連資料
Web Application Firewall (WAF):WAF 3.0 ログ。
Cloud Firewall (CFW):Cloud Firewall ログ。
Bastionhost:監査ログを Simple Log Service にアーカイブする。
ActionTrail:プラットフォーム操作ログ。
Anti-DDoS:完全なログ分析の開始。
API Gateway:API Gateway アクセスログ。
Container Service for Kubernetes (ACK):ログ管理。
PolarDB:ログ分析。
ApsaraDB for MongoDB:MongoDB ログ。
Server Load Balancer (SLB):ALB アクセスログ、アクセスログ、Classic Load Balancer (CLB) のレイヤー 7 アクセスログ、およびClassic Load Balancer (CLB) の秒単位のレイヤー 4 監視メトリック。
Object Storage Service (OSS):OSS アクセスログ。
File Storage NAS:SLS に基づくログ分析。
CloudConfig:設定監査ログ。
よくある質問
データソースの接続状態が「異常」または「未接続」と表示されるのはなぜですか?
以下の項目を順に確認してください。
RAM 権限:Agentic SOC のサービスリンクロール
AliyunServiceRoleForSasが SLS Logstore へのアクセス権限 (少なくともAliyunLogReadOnlyAccess) を持っているか確認します。これが最も一般的な原因です。設定情報:Agentic SOC のデータソース編集ページで、SLS のリージョン、プロジェクト、Logstore名が正しいか確認します。スペルミスや余分なスペースがないことを確認してください。
ソース Logstore の状態:SLS コンソールにログインし、プロジェクトが無効になっておらず、新しいデータが Logstore に書き込まれていることを確認します。
アクセスポリシーが有効にならないのはなぜですか?
単一のデータセット StoreView (Standardized RuleのStandardization Category or Structureによって決定) には、「スキャンクエリ」モードで最大 5 つのアクセスポリシーしかアタッチできません。この制限を超えると、アクセスポリシーは有効になりません。解決策については、「アクセスポリシーが有効にならない」をご参照ください。
ログ標準化テストに失敗した場合やデータが解析できない場合はどうすればよいですか?
ソース Logstore にデータが含まれているか確認する:新しいログが SLS Logstore に書き込まれていること、できれば過去 1 時間以内に書き込まれていることを確認してください。Logstore が空の場合、テストは続行できません。
標準化ルールが一致しているか確認する:カスタムルールを使用している場合、SPL 文が生ログのフォーマットを正しく解析できることを確認してください。SLS コンソールのクエリおよび分析ページで SPL 文をデバッグできます。