After you enable Secure Sockets Layer (SSL) encryption, clients can still connect without SSL using the PGSSLMODE=disable parameter if client access control is not configured. To force clients to use SSL connections, follow the steps described in this topic.
Prerequisites
SSL encryption is enabled for your RDS instance. This applies if you want your client to connect to the RDS instance only over SSL connections. For more information, see Configure SSL encryption or Configure a custom certificate.
A client CA certificate is configured. This applies if you want to verify the client certificate when the client connects to the RDS instance over SSL connections. For more information, see Configure a client CA certificate.
Procedure
You can use one of the following methods to forcefully enable the client to connect to the RDS instance over SSL connections:
Method 1: Configure a client ACL
After a client CA certificate is configured, you can configure an ACL on the RDS instance. Then, the client can connect to the RDS instance only after the RDS instance validates the client based on the SSL mode that you specify. The RDS instance validates the client using the client certificate and the private key of the client certificate.
When you configure an ACL, no operations can be performed on the RDS instance. This configuration process requires approximately 1 minute.
If client access control is not configured for an RDS for PostgreSQL instance, the default authentication method is
prefer. In this case, a client can use thePGSSLMODE=disableparameter to connect without SSL. To block non-SSL connections, enable SSL encryption and then configure the ACL to use an authentication method other thanprefer.
Click Modify to the right of Configure ACL and select an appropriate authentication method.
You can use one of the following authentication methods to forcefully enable the client to connect to the RDS instance over SSL connections:
cert: A client certificate rather than a password is used to validate the client. An SSL connection is established. In addition, the system validates the client certificate and checks whether the Common Name (CN) specified in the client certificate is consistent with the username that is used to connect to the RDS instance.
verify-ca: An SSL connection is established, and the system validates the client certificate.
verify-full: An SSL connection is established. The system validates the client certificate and checks whether the CN specified in the client certificate is consistent with the username that is used to connect to the RDS instance. This SSL mode is supported for PostgreSQL 12 or later.
Method 2: Configure the pg_hba.cnf file
After you configure SSL encryption, you can use the AD Domain Service Configuration feature of RDS for PostgreSQL to modify the pg_hba.cnf file. This forces clients to use SSL to connect to the database.
Go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance.
In the navigation pane on the left, click Accounts and then click the AD Domain Services tab.
In the first record, change the value in the TYPE column to
hostssl.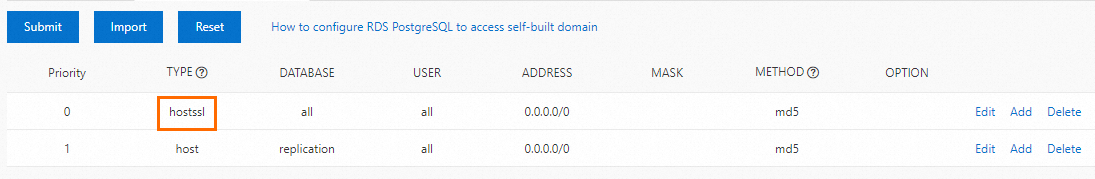
Click Submit.
NoteAfter you click Submit, the status of your RDS instance changes to Maintaining Instance for approximately 1 minute. The new configurations take effect only for new connections. You must close the existing connections and re-establish these connections for the new configurations to take effect.