This topic describes how to configure SSL encryption for an ApsaraDB RDS for PostgreSQL instance. SSL encryption is used to encrypt the connections from a database client to an RDS instance. This helps you protect the data that is transmitted over the connections. This topic also describes how to configure a cloud certificate to enable SSL encryption.
Background information
SSL is a protocol that is developed to ensure secure communication and protect data. From SSL 3.0 onwards, SSL is renamed as TLS.
ApsaraDB RDS for PostgreSQL supports TLS 1.0, TLS 1.1, and TLS 1.2.
The following table provides a comparison of the SSL encryption configurations and benefits among various certificates.
Item | |||
Purpose | The server (database) certificate, which is used by the client to authenticate the server. | The server (database) certificate, which is used by the client to authenticate the server. | The client certificate, which is used by the server (database) to authenticate the client. |
Method to obtain | Issued by Alibaba Cloud. | Issued by a certification authority (CA) or from a self-signed certificate. | Issued from a self-signed certificate. |
Validity period | 365 days. | Customized. | Customized. |
Number of protected endpoints | 1 | 1 or more. | Varies based on the cloud certificate or custom certificate that is used. The number of protected endpoints does not vary based on the CA certificate that is used. |
You must configure a cloud certificate or a custom certificate to enable SSL encryption and authenticate the server (database).
You can choose not to configure a client CA certificate, which is used by the server to authenticate the client.
Prerequisites
The RDS instance runs PostgreSQL 10 or later and uses cloud disks.
NoteServerless RDS instances are not supported.
The pgAdmin 4 client is downloaded. For more information, see pgAdmin 4.
Usage notes
A cloud certificate remains valid for one year. If a cloud certificate is about to expire, Alibaba Cloud notifies you by email and internal message and automatically renews the cloud certificate within a specific period of time. You can customize the time to renew the SSL certificate in the Schedule Event dialog box. For more information, see Manage scheduled events.
After SSL encryption is enabled, the CPU utilization and the read and write latencies increase.
After SSL encryption is enabled, you must close the existing connection and establish a new connection to make SSL encryption take effect.
When you configure a cloud certificate, change the endpoint that is protected by the configured cloud certificate, or disable SSL encryption, the RDS instance restarts. The restart process requires approximately 3 minutes. We recommend that you perform these operations during off-peak hours.
Step 1: Use a cloud certificate to enable SSL encryption
In this topic, cloud certificates are used to describe how to configure SSL encryption.
Go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance.
Log on to the ApsaraDB RDS console. Find the RDS instance and click the ID of the instance. In the left-side navigation pane of the page that appears, click . On the page that appears, click the SSL tab.
NoteIf the SSL tab does not appear, you must check whether the RDS instance meets the requirements in Prerequisites.
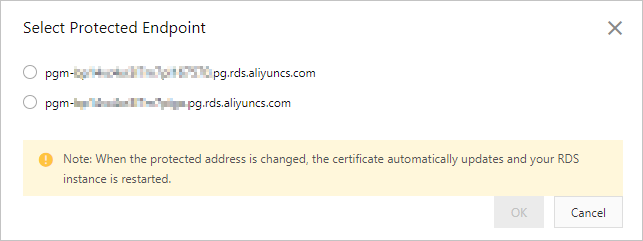
Select Cloud Certificate. Click Configuration next to Configure Database Certificate (to Prevent Database Disguise) and select the endpoint that you want to protect.
 Note
NoteIf you have not applied for a public endpoint, the Select Protected Endpoint dialog box displays only the internal endpoint of the RDS instance. If you have applied for a public endpoint, both the internal endpoint and the public endpoint of the RDS instance are displayed. However, each cloud certificate can protect only one endpoint. The internal endpoint is more secure than the public endpoint. Therefore, we recommend that you protect the public endpoint. For more information about how to view the internal endpoint and the public endpoint, see View and change the internal and public endpoints and port numbers of an ApsaraDB RDS for PostgreSQL instance.
For more information about how to protect the internal endpoint and the public endpoint at the same time, see Use a custom certificate to enable the SSL encryption feature.
After you configure a cloud certificate, the status of the RDS instance changes to Modifying SSL Settings. The RDS instance stays in the state for approximately 3 minutes. Wait until the RDS instance enters the Running state before you proceed with subsequent operations.
Step 2: Download the server CA certificate
After you configure the cloud certificate, you must download and save the server (database) CA certificate to your client. When you connect to the RDS instance from the client, you can use the server (database) CA certificate to authenticate the RDS instance.
Select Cloud Certificate. Then, click Download CA Certificate.
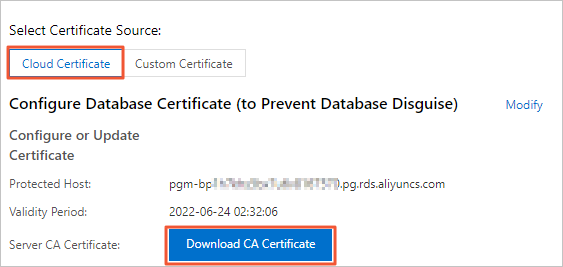
Decompress the file that you downloaded.
The file that you downloaded is a package that contains the following files:
PEM file: suitable for most scenarios.
JKS file: In most cases, the PEM-formatted certification authority (CA) certificate file must be imported to a truststore for the conversion into a JKS file for use in Java applications. The password is apsaradb.
P7B file: suitable for a small number of Windows applications that require PKCS#7-formatted certificate files.
Step 3: Connect to the RDS instance from the database client
In this example, pgAdmin is used to describe how to connect to the RDS instance over SSL.
You can connect to an RDS instance by using multiple methods, such as the psql command-line client and Java Database Connectivity (JDBC). For more information, see Connect to an ApsaraDB RDS for PostgreSQL instance over SSL connections.
Before you connect to the RDS instance, make sure that IP address whitelists are configured and accounts are created on the instance. For more information, see Configure an IP address whitelist and Create a database and an account on an ApsaraDB RDS for PostgreSQL instance.
This section uses
pgAdmin 4 V6.2.0as an example. If the screenshots differ from your client, you can configure SSL-related parameters based on this section by following instructions in Official documentation.
Start pgAdmin 4.
NoteIf this is the first time you log on to pgAdmin of a later version, you must specify a master password that is used to protect saved passwords and other credentials.
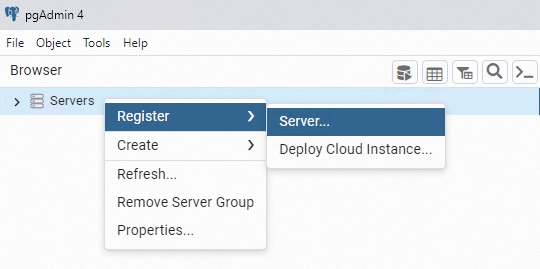
Right-click Servers and choose .
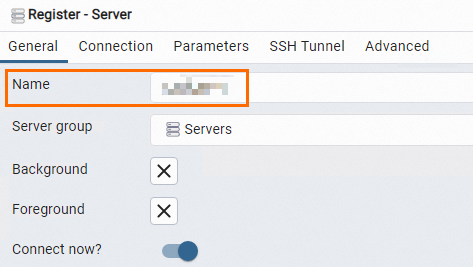
On the General tab of the Register - Server dialog box, enter the name of the server on which pgAdmin is installed.
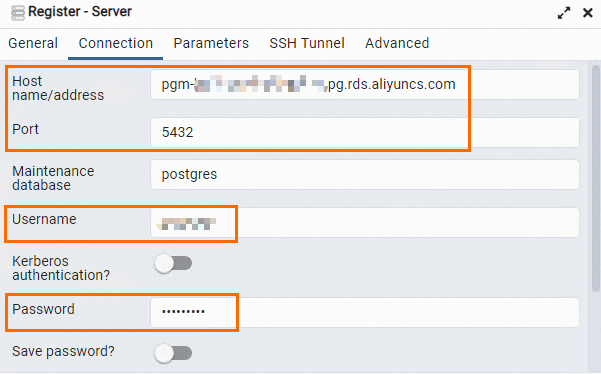
Click the Connection tab and enter the information that is used to connect to the RDS instance.
Parameter
Description
Host name/address
The endpoint and port that are used to connect to the RDS instance.
If you want to connect to the RDS instance over an internal network, enter the internal endpoint and internal port of the RDS instance.
If you want to connect to the RDS instance over the Internet, enter the public endpoint and public port of the RDS instance.
You can view the preceding information on the Database Connection page of the RDS instance.
For more information, see View and change the endpoints and port numbers of an ApsaraDB RDS for PostgreSQL instance.
Port
Username
The username and password that are used to log on to the RDS instance.
For more information about how to create an account on an RDS instance, see Create a database and an account.
Password
On the Parameters tab, configure the parameters related to the SSL authentication mode and configure the certificate.
Parameter
Description
SSL mode
For security purposes, we recommend that you set this parameter to Require, Verify-CA, or Verify-Full. The following list provides the meanings of the different values of the SSL mode parameter:
Require: The database client encrypts the SSL connections that are used to transmit data. However, the database client does not validate the RDS instance.
Verify-CA: The database client encrypts the SSL connections that are used to transmit data and validates the RDS instance.
Verify-Full: The database client encrypts the SSL connections that are used to transmit data, validates the RDS instance, and checks whether the CN or Domain Name System (DNS) specified in the server CA certificate is consistent with the value of the Host name/address parameter that you set at connection establishments.
Root certificate
If you set the SSL mode parameter to Verify-CA or Verify-Full, you must set the Root certificate parameter to the save path of the file that contains the server CA certificate.
NoteIn this example, the file that contains the server CA certificate is downloaded from the SSL tab and then is decompressed to the D:\CA\aliyunCA\ path on your computer. You can change the path based on your business requirements.
In pgAdmin, the file that contains the server CA certificate is in the PEM format.
Click Save.
If the information that you enter is correct, the page that is shown in the following figure appears, which indicates that the connection to the RDS instance is successful.
 Important
ImportantThe postgres database is the default system database. Do not perform operations on the postgres database.