As a Kubernetes application deployment tool, Kruise Rollouts provides a variety of canary release policies such as canary release and blue-green deployment. You can use Kruise Rollouts together with Microservices Engine (MSE) Microservices Governance to implement smooth canary releases for new versions of applications during the service call process. This ensures the stability of new versions.
Introduction to end-to-end canary releases
The traditional canary release mode cannot meet the complex delivery requirements in scenarios where the microservices architecture is used. The end-to-end canary release feature is introduced to route canary traffic to canary environments or groups for each microservice application. Developers expect that traffic flows from an upstream canary environment to a downstream canary environment. This way, a request remains within canary environments, and a traffic lane is generated. In a traffic lane, even if some microservice applications involved in the call process do not have their respective canary environments, requests for these microservice applications can still be routed to downstream canary environments. In this case, you can release changes to multiple services at the same time to ensure the system stability. The following figure shows the process of an end-to-end canary release.
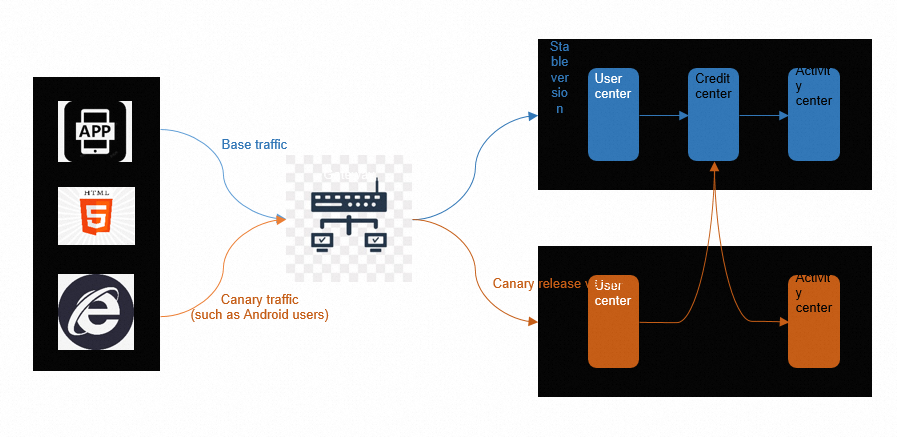
Introduction to Kruise Rollouts
Kruise Rollouts is an open source progressive rollout framework provided by OpenKruise. For more information, see Kruise Rollouts. You can use Kruise Rollouts to perform canary releases, blue-green deployments, and A/B testing. You can also use Kruise Rollouts to control the canary traffic and pods. The release process can be automated in batches and paused based on the metrics of Managed Service for Prometheus. Kruise Rollouts also provides imperceptible connection of bypasses and is compatible with various workloads such as Deployments, CloneSets, and StatefulSets. For more information, see Kruise Rollouts.
Kruise Rollouts is a bypass component. You need to only create a Rollouts resource in your Container Service for Kubernetes (ACK) cluster to automate application releases and updates. Kruise Rollouts supports seamless integration with Helm and PaaS platforms at low costs. The following figure shows the architecture of a canary release by using Kruise Rollouts.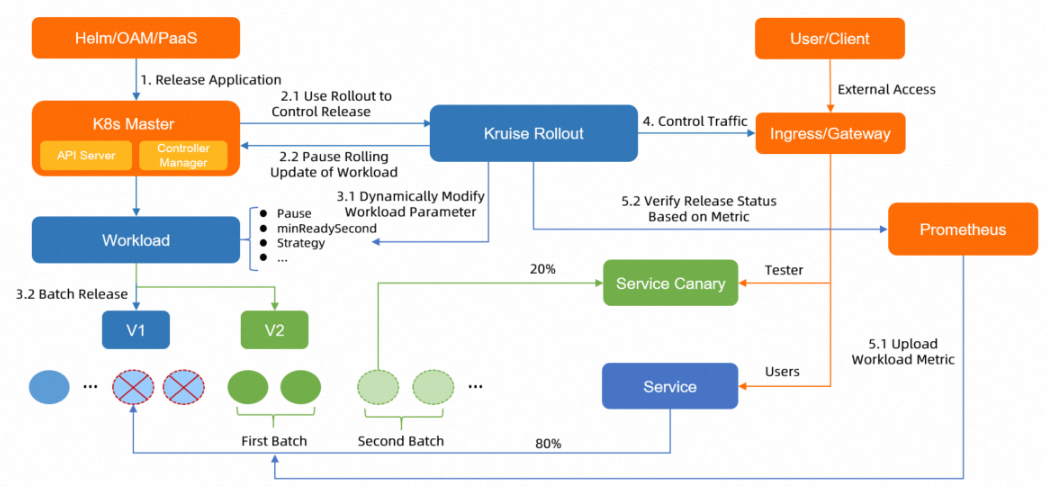
Prerequisites
An ACK cluster of V1.19 or later is created. For more information, see Create an ACK managed cluster.
kubectl-kruise is installed. For more information, see kubectl-kruise.
Microservices Governance is activated. For more information, see Activate Microservices Governance.
Step 1: Make preparations
Install the Kruise Rollouts component.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side navigation pane, choose .
On the Manage Components page, click the Manage Applications tab.
Find the ack-kruise card and click Install.
In the message that appears, click OK.
Install the MSE Ingress Controller component. Create an MseIngressConfig and an IngressClass resource. For more information, see Use MSE Ingresses to access applications in ACK clusters.
Enable Microservices Governance for applications. For more information, see Enable Microservices Governance for microservice applications in an ACK cluster.
Step 2: Deploy demo applications
Create a deployment, a service, and an Ingress resource.
Create a file named mse-demo.yaml and copy the following content to the file.
Run the following command to deploy the business application:
kubectl apply -f mse-demo.yamlCreate a file named mse-ingress.yaml and copy the following content to the file.
Run the following command to create an Ingress rule:
kubectl apply -f mse-ingress.yamlRun the following command to query the public IP address:
kubectl get ingressExpected output:
NAME CLASS HOSTS ADDRESS PORTS AGE spring-cloud-a <none> * EXTERNAL_IP 80 12mRun the following command to check the route status. Replace <EXTERNAL_IP> with the IP address that you obtained in the preceding step.
curl http://<EXTERNAL_IP>/aExpected output:
A[192.168.42.115][config=base] -> B[192.168.42.118] -> C[192.168.42.101]
Step 3: Implement an automated end-to-end canary release by using Kruise Rollouts
Define the canary release rules of Kruise Rollouts.
NoteIn this example, the canary release is performed in three batches:
A/B testing is performed. Requests that contain header[User-Agent]=xiaoming are forwarded to the canary version. Other requests are forwarded to the base version.
Half of the pods run the canary version, and half of requests are forwarded to the canary version.
All the pods run the canary version, and all the requests are forwarded to the canary version.
Create a file named rollout.yaml and copy the following content to the file:
Run the following command to deploy the Rollouts resource in your ACK cluster:
kubectl apply -f rollout.yamlRun the following command to query the status of the Rollouts resource:
kubectl get rolloutIf STATUS=Healthy is returned as expected, the Rollouts resource is working properly.
Update the application.
Kruise Rollouts is a common configuration and only needs to be distributed to your cluster. To release new application versions, you need to only update the deployment. You do not need to configure Kruise Rollouts again. For example, you can directly update the image versions of spring-cloud-a and spring-cloud-c to mse-2.0.1 and then run the
kubectl apply -f mse-demo.yamlcommand to deploy the deployments to your cluster. In addition to kubectl, you can use Helm or Vela to deploy the deployments to your cluster.Modify the mse-demo.yaml file to update the image versions of spring-cloud-a and spring-cloud-c to mse-2.0.1.
Run the following commands to query the status of the Rollouts resources:
kubectl get rollouts rollout-a -n default kubectl get rollouts rollout-c -n defaultExpected output:
NAME STATUS CANARY_STEP CANARY_STATE MESSAGE AGE rollouts-a Progressing 1 StepPaused Rollout is in step(1/1), and you need manually confirm to enter the next step 41m rollouts-c Progressing 1 StepPaused Rollout is in step(1/1), and you need manually confirm to enter the next step 41mYou can check the STATUS, and CANARY_STATE columns to view the status of the Rollouts resources and the release stages.
If STATUS=Progressing is returned, the canary release stage is in progress.
If CANARY_STATE=StepPaused is returned, the current batch is released. Manual configuration is required for releasing the next batch.
You can release the remaining batches after you verify that the canary version runs as expected.
The preceding steps release only some applications of the canary version and forward a proportion of requests to the canary version. After you verify that the canary version runs as expected based on application logs and metric data, you can run the
rollout.rollouts.kruise.io/<rollouts-demo> approvedcommand to release the remaining applications of the canary version. <rollouts-demo> indicates the name of the Rollouts resource.Optional. If the new application version does not run as expected, roll back the application version.
If the canary version does not run as expected during the release process, modify the deployment configurations and then run the
kubectl apply -f mse-demo.yamlcommand to roll back the application version. You do not need to perform modification operations on the Rollouts resources.
The end-to-end canary release feature of Microservices Governance provides lanes, which greatly facilitate verification during testing and release. You can use Microservices Governance together with Kruise Rollouts to significantly improve the stability of online applications in a DevOps process.