Data security
Hologres passed an independent third-party audit on compliance with the trusted services criteria for security, availability, and confidentiality established by the American Institute of Certified Public Accountants (AICPA). For more information about the audit report, see SOC 3 Report.
Hologres is certified by Payment Card Industry Data Security Standard (PCI DSS). PCI DSS is the most stringent financial data security standard that has the highest level in the world. If an enterprise is certified by PCI DSS, the enterprise meets the ability requirements in the field of payment system security protection and information security. The enterprise can provide secure and reliable system solutions and capabilities for customers. For more information about the certification report, see PCI DSS Certification Report.
Storage encryption
Hologres allows you to use Key Management Service (KMS) to encrypt static data for secure storage.
Overview of KMS
Key Management Service (KMS) is provided by Alibaba Cloud to encrypt application data in the cloud. KMS provides encryption and decryption services for your applications and helps you meet the requirements of cryptographic algorithms. This way, you can use keys with ease. Alibaba Cloud also provides Dedicated KMS that delivers high security. Dedicated KMS allows you to store your keys in exclusive hardware security module (HSM) clusters. For more information, see What is KMS?
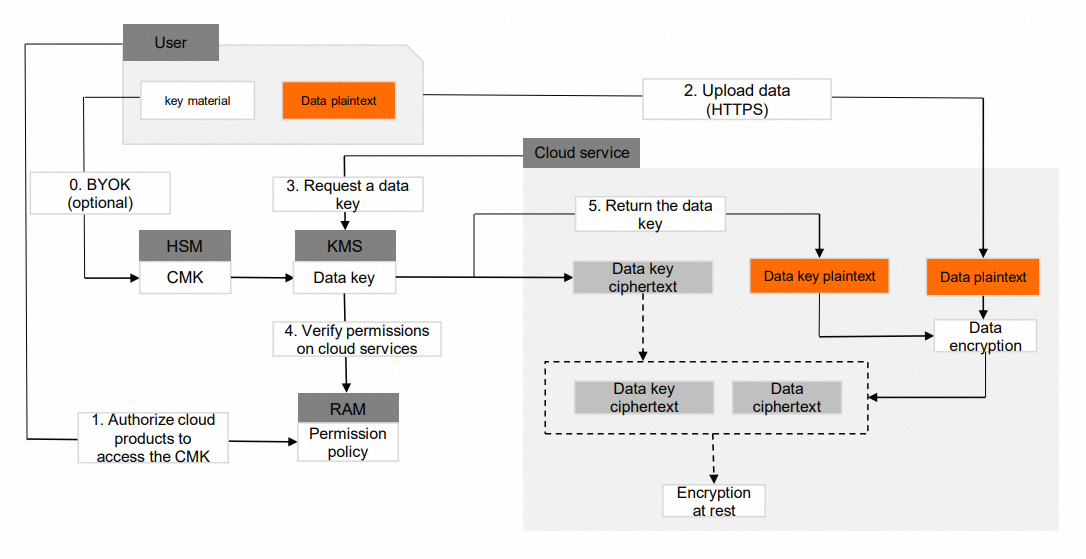
KMS provides HSMs that are tested and certified by the State Cryptography Administration (SCA) of China and has obtained the second-level certification of GM/T 0028.
KMS provides only Transport Layer Security (TLS)-based secure channels for access and uses only secure cipher suites for transmission. KMS complies with PCI DSS.
A random number generation algorithm is used to generate keys. The algorithm is secure and has high system entropy seeds. This protects keys from being decrypted by attackers.
Keys are protected by using secure hardware mechanisms. The plaintext of keys is used only inside HSMs for cryptographic operations to ensure security.
You can use ActionTrail to audit key usage and ensure that keys are correctly used. You can audit the keys for cloud services or user-owned applications when the keys are used by calling KMS API operations.
Hologres capabilities
Hologres supports only Bring Your Own Key (BYOK) encryption, which is a visible and controllable semi-managed encryption method. This is because high-value data that is stored in Hologres requires a high level of security. BYOK is an advanced security technology that is recognized in the industry. In BYOK encryption, keys that are generated by users offline are imported into an HSM that is hosted in KMS in the cloud. The keys cannot be exported from the HSM but can be deleted by users at any time. This way, users can re-import the same keys. For more information, see Encrypt data in Hologres.
Based on the key management feature provided by KMS and the encryption library capability provided by the security department, Hologres provides storage encryption that is based on algorithms such as AES-256, AES-128, RC4, and SM4.
Hologres allows you to configure a separate encryption rule for each table. You can use KMS to configure different keys for different tables.
When you read data from or write data to a table, Hologres calls KMS API operations to obtain key information. By default, key information is cached for 24 hours. You are charged KMS fees when you use the data encryption feature. For more information, see Billing of KMS.
After you enable the storage encryption feature, the data read and write performance may decrease by approximately 20% to 40% because of encryption and decryption operations. The performance loss varies based on the actual situation.
Encrypted data transmission
To improve the transmission security of Hologres, you can enable SSL-encrypted transmission. SSL encrypts network connections at the transport layer. This improves the security and integrity of transmitted data but increases the response time. For more information, see SSL-encrypted transmission (beta).
SSL is a protocol that is developed to ensure secure communication and protect data. Alibaba Cloud SSL certificates are trusted credentials that are issued by well-known certificate authorities (CAs). The CAs are certified by WebTrust. You can use SSL certificates to verify the identity of your website and encrypt data in transmission. HTTP cannot be used to encrypt data. During HTTP transmission, data leaks, data tampering, or phishing attacks may occur. After you install an SSL certificate on your web server, you can establish HTTPS-encrypted connections between your web server and website. This ensures the security of your website and data transmission and enables websites to meet the security requirements of app stores or application ecosystems. For more information, see What is an SSL certificate?
Data masking
Hologres provides the data masking feature. You can use the feature to mask data by column and configure data masking rules for specific users. After you enable this feature, sensitive information is masked in query results. This helps you protect sensitive and private data. Hologres supports multiple masking rules, such as IP address masking, email address masking, and hashing. For more information, see Mask data.
System security
Account
You must use an Alibaba Cloud account to purchase and use Hologres instances. You must create an Alibaba Cloud account and complete real-name verification before you can purchase a Hologres instance. You must create an AccessKey pair before you can access the Hologres instance.
Hologres supports Resource Access Management (RAM) authentication. RAM is a service provided by Alibaba Cloud and is used to manage permissions on resources. You can use your Alibaba Cloud account to create RAM users and grant the RAM users the permissions to access specific resources that are owned by your Alibaba Cloud account.
Authentication
You can create an AccessKey pair in the Alibaba Cloud console.
An AccessKey pair consists of an AccessKey ID and an AccessKey secret. The AccessKey ID is public and uniquely identifies a user. The AccessKey secret is private and is used to authenticate a user.
When you send a request to Hologres, a signature string in the specified format is generated for the request and your AccessKey secret is used to encrypt the signature string and generate a request signature. After Hologres receives the request, Hologres generates a signature for the signature string based on the AccessKey secret that corresponds to the AccessKey ID. If the signature is consistent with the request signature, Hologres considers the request valid. Otherwise, Hologres rejects the request and returns HTTP status code 403.
Authorization
You can access a Hologres instance by using an Alibaba Cloud account or as a RAM user. To implement flexible access control, you can create RAM users that have different permissions for your Alibaba Cloud account. Hologres uses permission-based authorization policies when you access a Hologres instance by using an Alibaba Cloud account or as a RAM user.
If you use an Alibaba Cloud account, Hologres checks whether the Alibaba Cloud account is the owner account of the Hologres instance. Only the owner can access the Hologres instance.
If you use a RAM user to access a Hologres instance, the RAM user permission policy is triggered. Hologres checks whether the Alibaba Cloud account that owns the Hologres instance grants the RAM user the permissions to access the Hologres instance.
The following table describes the three permission models that are supported by Hologres and are used to control the access permissions of RAM users. For more information about how to configure the permission models, see Overview.
Permission model
Scenario
Description
Standard PostgreSQL authorization model
This model is suitable for scenarios in which permissions are strictly managed. This model allows you to grant a RAM user the permissions on a specific table. For example, you can grant the zinan.tang user the read permissions on the table1 table.
In this model, permissions are granted in a fine-grained and flexible manner. Permissions on a specific table can be granted to users. You can run the
GRANT or REVOKEcommand to grant or revoke permissions on databases, schemas, tables, or views in an existing instance.Simple permission model (SPM)
This model allows you to manage database-level permissions. This model is suitable for scenarios in which permissions are managed in a coarse-grained manner.
In this model, specific permissions of each user group on databases cannot be changed. This model is suitable for most scenarios because the authorization operations are simple.
Schema-level permission model (SLPM)
This model allows you to manage schema-level permissions and is suitable for scenarios in which permissions are managed in a fine-grained manner and a simple authorization process is required.
In this model, specific permissions of each user group on schemas cannot be changed. The authorization operations are simple.
RAM authentication
Hologres supports RAM authentication. RAM is a resource access control service provided by Alibaba Cloud. You can create RAM users for your Alibaba Cloud account in RAM. The created RAM users are subordinate to the Alibaba Cloud account. All Hologres instances belong to the Alibaba Cloud account. The Alibaba Cloud account can grant access permissions on the Hologres instances to the RAM users.
You can also log on to Alibaba Cloud and access Hologres by using role-based single sign-on (SSO). In this case, the RAM role becomes a member of a Hologres instance. The user that assumes the RAM role has the same permissions as a member that is an Alibaba Cloud account or a RAM user. For more information, see RAM role authorization mode.
Auditing
ActionTrail
Hologres allows you to query the event logs of instances in the previous 90 days in the ActionTrail console, by calling API operations, or by using developer tools. This way, you can monitor events, configure alert rules for events, audit events in real time, and troubleshoot issues. For more information about how to query the event logs, see Query event logs. For more information about ActionTrail, see What is ActionTrail?
ActionTrail records operations that are performed on Alibaba Cloud services, including the operations that are triggered by users in the console, operations that are performed by calling API operations, and operations that are performed by using service roles. ActionTrail can track and record the operations in 10 minutes.
You can query operation records in the previous 90 days in the ActionTrail console or by calling API operations. The records include the following operation information: the person who initiated an operation, the time when an operation is performed, the object on which an operation is performed, the IP address from which an operation is initiated, whether an operation is performed in the Alibaba Cloud Management Console or by calling API operations, the result of an operation, and the cause of failure if an operation failed. You can download the operation records to Simple Log Service or Object Storage Service (OSS). Then, you can perform operations such as behavior analysis, security analysis, resource change tracking, and compliance audit.
ActionTrail allows you to deliver operation records to OSS or Simple Log Service. This provides extremely high availability and ensures the security of audit data by using encryption and access control. ActionTrail sends you a notification when an operation record is delivered.
You can create multiple trails to deliver operation records to different storage spaces. This helps you track different types of operations that are performed in different regions and back up various types of data for organization members based on their responsibilities.
Implementation principle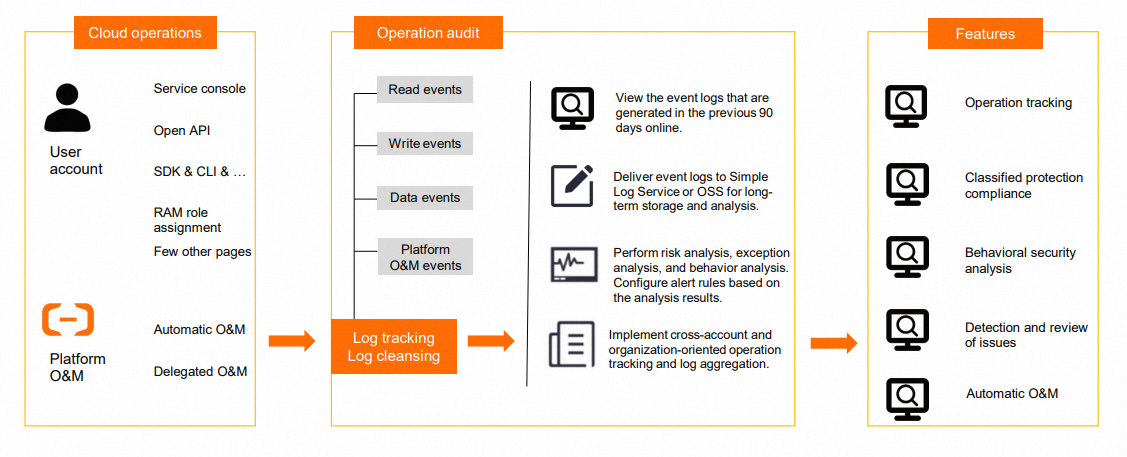
Hologres Query Log
Hologres records all DDL statements in the previous 30 days, and the DML and DQL statements that are executed for more than 100 ms in the previous 30 days. Hologres provides query logs that you can use to query detailed operation information about each user. For more information, see Query and analyze slow query logs.
Network security
Access isolation
As a one-stop real-time data warehouse engine developed by Alibaba Cloud, Hologres must meet the requirements of security isolation specifications. Take note of the following items:
The classic network, virtual private cloud (VPC), and Internet of each Hologres instance are isolated from each other. You can access the Hologres instance over a network by using the endpoint and virtual IP addresses (VIPs) that correspond to the network.
You can configure a specific VPC for a Hologres instance to ensure that the Hologres instance can be accessed only from the specified VPC.
IP address whitelist
Hologres supports multiple levels of access control to ensure security, such as the security authentication mechanism. Only users who have the authorized AccessKey ID and AccessKey secret can access data based on the granted permissions.
The IP address whitelist feature provides enhanced access control based on the preceding access authentication mechanisms. After an IP address whitelist is configured, you can access a Hologres instance only from IP addresses that are included in the whitelist. If you access a Hologres instance from an IP address that is not included in the whitelist, your access request is denied even if you have a valid AccessKey pair. For more information, see Configure an IP address whitelist.