In order to win this inevitable battle and fight against COVID-19, we must work together and share our experiences around the world. Join us in the fight against the outbreak through the Global MediXchange for Combating COVID-19 (GMCC) program. Apply now at https://covid-19.alibabacloud.com/
By Alibaba Cloud Security Team.
This year, the coronavirus outbreak has pushed many of us to working on the cloud and mobile office spaces. With this push, countless employers have begun to move their work online, with tens of thousands of people getting in touch through telecommuting and online conferencing. Cloud is the perfect solution to support this kind of temporary spike in the demand for bandwidth resources. This sudden change has also made everyone even more familiar with the need for mobile working, with many employees staying at home working on their mobile devices.
Traditional Remote Officing
Even before the epidemic, Identity as a Service (IDaaS) had focused on combating the increasing security challenges through different cryptographic techniques. Account passwords that use symmetric algorithms are vulnerable to credential stuffing attacks. Now, even short-term tokens generated by asymmetric techniques can face significant security challenges. Regardless of their byte lengths, your credentials can be stolen. To address this sort of problem, enterprises can enable more complex security policies, but doing so can often result in a worsened user experience.
Meanwhile, enterprises quickly found that it was impossible to verify the identity of users in a precise manner. In the future, by introducing artificial intelligence (AI) technologies to these systems, at Alibaba we will conduct comprehensive analysis and computing on all access attempts to our internal and external business systems, dynamically checking and updating existing security policies, and then automating the appropriate security control measures. We think that in the future it will be common to have the backend make decisions about whether to allow access to core systems. All these efforts will increase security protection and decrease the annoyance of users due to poorly designed solutions.
With the rapid development of new and upcoming AI technologies, we can ignore the embarrassing falls that some Boston Dynamics robots took and trust that AI will help us defend against cyber attacks in the near future. Already AI technologies are being used to quickly detect people with fevers at airports.

In ESG's annual research report, they identified that AI-based cybersecurity technology which uses AI and machine learning to detect threats as one of the top four key areas of security investment. The reason for this is simple. In the future, there will be a huge amount of data, whereas manual screening won't be able to keep up with the demand. So, with these technologies, we will be able to respond more quickly and to a large number of concerns.
Zero trust has been widely recognized in the industry since the zero-trust security architecture for identity authentication delivery emerged after Google's launch of BeyondCorp.
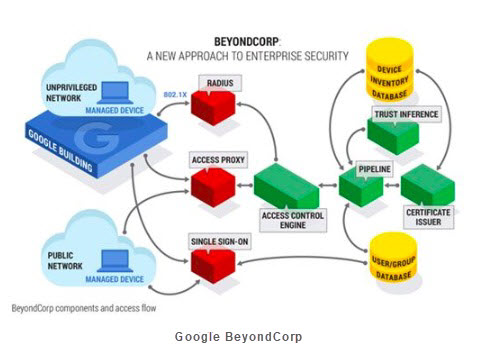
The greatest benefit of this model is that it raises previous IT best practices to the level of modern theory, with special emphasis on the mutual authentication of people and devices. With theory to guide practice, many problems, which have remained unresolved up to this point, should be able to find their answer. Consider this example. Forward and reverse proxies, or more specifically Identity Aware Proxy (IAP), indicated by Access Proxy in the preceding figure, have been widely used over the past twenty years. In today's environment, such proxies must interact with identity authentication and authorization. With such proxies, you can record all requests and responses, rather than just simple system logs. They can serve as the perception input of the Access Control Engine (ACE) in subsequent brain control centers and provide the data support necessary for machine learning.
This system is somewhat analogous to road checkpoints set up during the coronavirus outbreak. Only those allowed to pass along with the relevant personnel could enter a specified area after temperature screening and presenting necessary identification or documentation. In addition, often it's the case that anyone who enters or leaves the specified area must be also registered. This kind of collected information can provide a basis for further research and control.
In addition to Google, other major international vendors are also adopting this type of approach. In 2019, Cisco, a traditional network and enterprise security vendor, acquired Duo Security, a startup in the authentication field, for more than 2 billion US dollars. Through this acquisition, the identity authentication capabilities of Duo Security were integrated into Cisco's Smart Access Gateway (SAG), Cloud Access Security Broker (CASB), Mobile Device Management (MDM), and other hybrid cloud products.
In 2019, an increasing number of Chinese security providers switched to zero-trust security. Traditional virtual private network (VPN) vendors provide software-defined perimeter (SDP) products that are claimed to be able to reduce Internet exposure. It should be noted that zero-trust security solutions that are not based on identity capabilities are defective. Identity and perimeter control must be fully combined to provide complete zero-trust solutions.
The current epidemic has exposed many problems. We all had to do our part, even though we were not always adequately prepared. Many enterprises are still using traditional VPNs for their remote office solutions. Such solutions can meet the needs of leaders and O&M personnel, but cannot support video conferences that involve tens of thousands of participants. A top bank in China has invested hundreds of millions of RMB in infrastructure every year. However, in the face of massive numbers of people working from home, its system still encountered massive jitters and a new solution was required to address this problem.
The current epidemic will have a far-reaching impact on the industry. Telecommuting and online education have become new hotspots where the relevant technology is much needed. In addition, IT professionals have become more enthusiastic about zero-trust networks centered on identity authentication and authorization. However, Rome was not built in a day. Google launched BeyondCorp 6 years after it started the project in 2013. It is impossible for enterprises to do away with their current systems and build zero-trust systems from scratch overnight. So, a more practical approach is to get started as soon as possible. Even if a simple model is used at the beginning, social events and security events can quickly force the industry to mature.
Zero trust is undoubtedly complex. It involves more than 10 different components, including the control center (ACE), access gateway (IAP), and authentication center (IDaaS). As the authentication center, IDaaS covers single sign-on (SSO), Radius access protocol, and user management (UD). It is the core of the entire solution.
The control center is the brain and backbone of the enterprise zero-trust system.
First, it is a brain that is capable of learning. Traditional firewall security policies adopt predefined rules, which are generally set by administrators based on their own experience. These policies are complicated and often don't perform well. For instance, the peak meeting sign-in time of enterprises is 9:00 in the morning on Monday. For an enterprise with 10,000 employees, it is important to know if the peak value is 10,000 or 1,000 sign-ins per second. Even if we are able to set an appropriate value based on observations, we would not know what volume to expect at 11:00. However, we can easily find the relevant patterns by performing machine learning on logs.
Second, the control center is a brain that can make informed judgments. Due to the introduction of IAP, it can implement real full-stack log audits. Every user request is recorded. By combining this information with the logs from switches, routers, firewalls, access systems, and other components, we can implement continuous adaptive risk and trust assessment. This allows us to better characterize and trace user behaviors.
Zero-trust systems can impose control at many points, and the authentication center is the best starting point.
Like society, networks are composed of complex entities with attributes that can tell us important things about them. Generally, an individual can be identified by an ID card. In current joint prevention and control efforts, more attributes can be attached to an identity. After all, it is easy to obtain more superficial attributes, such as body temperature, but more difficult to obtain deeper attributes, such as lung CT information or the presence of viral nucleic acid. Identity authentication has always been a key factor of security.
The access center is a gate that controls the flow of traffic.
Although the control center is a powerful brain, its judgments also depend on information from various organs. If the brain cannot receive any feedback, it is deaf and blind. Therefore, the linkage between the access center and the control center makes the system more intelligent. By using face masks as an example, a face mask that blocks 95% of particles of a certain size is good enough in our daily life. In situations with higher requirements, masks that block 99% of particles can be used. However, masks that block 100% of particles are extremely expensive. Likewise, the access center serves to better parse the TCP protocol. It can quickly detect web traffic, video traffic, or broadcast requests that carry a virus, and help the system respond promptly.
In summary, the control center, authentication center, and access center are the three core components required in a zero-trust security architecture.
With IDaaS at its core, Alibaba Cloud's security systems provide a complete zero-trust security solution, which is similar to the simplified version of Google's BeyondCorp. Through agent terminal management and control, the Service Provider Gateway (SPG) provides application access. Together with IDaaS, Alibaba Cloud security systems provide a flexible compound solution to meet the needs of enterprises.
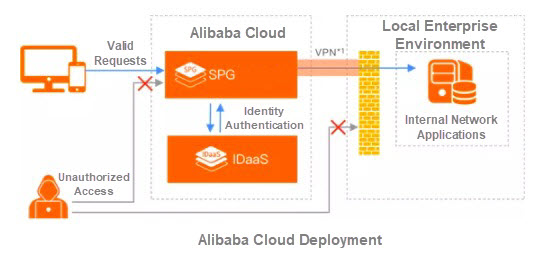
As shown above, the public IDaaS and SPG are deployed on Alibaba Cloud and can be connected to enterprises' internal networks through VPN tunnels. This means that, simply by configuring access control list rules for one inbound IP address of the SPG on the firewall, you can ensure that all traffic that is accessible to your enterprise's internal network is "sanitized" by Alibaba Cloud Web Application Firewall, IPS, besides other security services.
Alibaba Cloud security systems' IDaaS is mainly used to protect application and identity security.
Why is this important? When we overcome preliminary obstacles, we must then face more demanding challenges. Today, many cyberattacks hide themselves within normal traffic. When you detect that your system is under attack and then block the intrusive traffic, this is bound to mistakenly block normal traffic and affect normal services. This is why Adaptive Authentication is required additionally. Identity verification is the best way to identify camouflaged intrusive traffic and avoid false positives throughout the system. The most common approach is to have the AI module in IDaaS detect abnormal behaviors by checking IP addresses, locations, times, and other information. When it judges that a risk has occurred, it kills the existing session and displays an one-time password (OTP) secondary authentication page. The interaction can proceed only after the user passes secondary authentication. Otherwise, the access attempt is blocked.
IDaaS provides a zero-trust solution that combines the control center and the authentication center. Its user entity behavior analysis (UEBA) function is capable of AI-enabled identification and judgment. It can calculate average values based on user logon behavior on the same business day in the past month to produce a baseline. Then, it calculates a risk score for the user's authentication request. Based on the risk score, the system sends a DingTalk alert to the administrator, trigger two-factor authentication (2FA), or block the IP address by adding it to the blacklist.
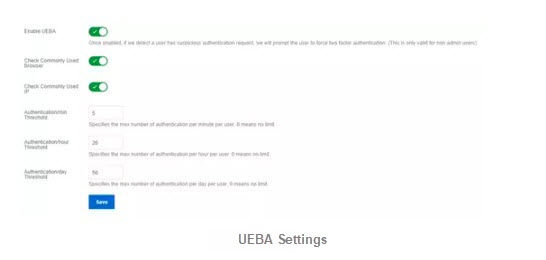
As mentioned at the beginning of this article, manual screening is not feasible when dealing with a massive amount of network throughput, which resembles opening every bag at airport security checkpoints. By leveraging the expertise Alibaba Cloud has accumulated over years along with the algorithms it has developed, UEBA is capable of quickly identifying risks.
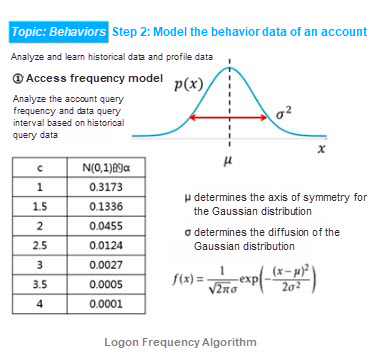
In addition, IDaaS also integrates Alibaba's business risk control capabilities, including user registration and logon, to ensure that users enjoy security and reliability from the very first time they use the system.
Application proxies address shortcomings such as insufficient VPN bandwidth and excessive exposure.
A major problem with traditional IPSec VPNs is that once attackers steal an identity and access the internal network, they can go on to horizontally access more vulnerable network devices and servers. This allows them to escalate their permissions in the system and achieve their ultimate objectives. This process occurs over and over again, resulting in information leaks and repeated network protection measures.
The SPG product serves as an IAP and intercepts and evaluates all web and TCP requests. In practice, systems with fewer open ports are more secure, and it is best to only open HTTPS port 443. Fortunately, many businesses have adopted browser/server (B/S) separation. Therefore, SPG can make businesses available without opening more ports, such as RDP port 3389. With the ability to process tens of thousands of concurrent requests per second, SPG can process all requests that flow in and out the firewall. Whether users are at work or at home, the process and user experience are the same.
In IDaaS, the terminal proxy IdpAgent ensures the security of access by mobile and PC terminals.
For example, during the epidemic, many people left their desktop computers in the office, so they could no longer work normally. To continue working, these people need to be able to use their PCs. However, the resulting terminal control problem presents a major challenge. Allowing home computers to access the enterprise network involves a high degree of risk. The enterprise cannot ensure that home computers are free from viruses and trojans.
By leveraging years of successful experience of using Alilang, our internal terminal proxy at Alibaba Cloud can check whether a device's vulnerability patches and anti-virus software meet baseline requirements during runtime, and only permits compliant devices to access. After passing Multi-factor Authentication identity authentication, you can automatically register your PC and mobile phone as trusted devices by binding user identities and device fingerprints. Next, you can download the client certificate instead of using a traditional account password to further reduce the chances of phishing and man-in-the-middle attacks.
In addition to terminal access, mobile terminal apps can also be used as tools for generating OTP tokens. In the future, VPN and DLP capabilities, and even conference calls, will be embedded in terminal control software.
In our efforts to fight the epidemic, DingTalk has played an important role as an application portal on terminals.
Many IT personnel were not psychologically prepared for the high demands posed by so many people who work from home. Over a two-day period, DingTalk had expanded by over 10,000 servers a day, showing the high demand for its services. At first, DingTalk applications were relatively basic, mainly consisting of live video conferences. In the future, as DingTalk becomes a mobile office portal, the opening of internal network applications to DingTalk will pose greater security challenges.
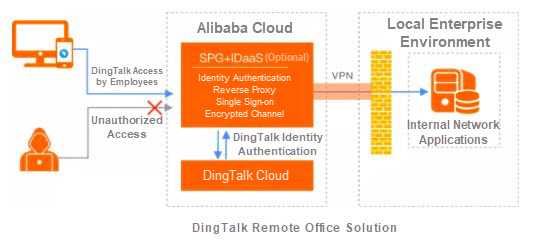
One simple solution is to integrate IDaaS, SPG, and DingTalk to flexibly adapt to more application scenarios. For example, if you use the DingTalk built-in browser to open an office application, you can use one of two methods:
id_token and then use this token to satisfy the SPG verification requirements.In the latter solution, IDaaS is an optional component. This means that an enterprise only needs to provide a valid user identity, which can be the DingTalk identity or the original 4A system identity.
In addition to the public DingTalk service, Alibaba also provides a dedicated DingTalk service to ensure that important files can be stored locally. The solutions for other exclusive DingTalk scenarios are similar and will not be described here.
In addition to being deployed in Alibaba Cloud, IDaaS also can be deployed in Alibaba Cloud's Apsara Stack, Alibaba's Database management system product line, which can run on customers' agile Platform-as-a-Service (PaaS) products. The Apsara Stack Security IDaaS and SPG can be deployed behind the enterprise firewall to better meet the regulatory requirements of users in industries such as finance.
For users who use both public and private clouds, Alibaba Cloud provides a hybrid cloud deployment mode to meet the needs of local cloud users.
As we continue to fight the novel coronavirus epidemic, we at Alibaba Group, adhering to our business-oriented approach, will not only continue to provide global procurement and logistics services, but also provide even powerful technical capabilities that can help us all get through this difficult time together.
A true zero-trust security system requires end-to-end protection from terminal devices to the cloud. Terminals, access, AI, and cloud native capabilities are all strengths of Alibaba Cloud. The core advantage of cloud0native is that cloud-based architectures can build a trusted chain from the bottom up, covering IaaS, PaaS, and SaaS scenarios. This removes the need to introduce third-party security vendors.
In addition to IDaaS, Alibaba Cloud security systems also provide Anti-DDoS, WAF, SDDP, risk control, real-person authentication, and SSL certificate services, while Alibaba Group provides Alilang, DingTalk, RAM, VPN, SAG, DAMO Academy's AI, and other products and services. In the future, we will integrate a wider range of security solutions to keep our users protected.
Finally, we see zero-trust security with identity authentication at boundaries as an inevitable trend in the current market.
As the current epidemic has increased the demand for cloud and mobile solutions, we must work to extend our security defenses. Mobile terminal devices and public cloud servers are located outside the traditional enterprise security firewall, breaking open the security perimeter that enterprises could erect in the past. 20 years ago, enterprises set up ACLs and firewalls, including NGFWs. Then, 10 years ago, Web 2.0 saw the development of web application firewalls (WAFs). Going forward, zero trust will be demanded to meet increased security requirements such as IDaaS and other identity authentication measures at the new perimeters of enterprise networks. This sort of market trend will be driven by governments and financial businesses that are most sensitive to security concerns. So, let's see where it takes us.
While continuing to wage war against the worldwide outbreak, Alibaba Cloud will play its part and will do all it can to help others in their battles with the coronavirus. Learn how we can support your business continuity at https://www.alibabacloud.com/campaign/supports-your-business-anytime
What Would You Do If Your App Crashes during Coronavirus Outbreak?
Ant Financial Unveils SaaS Version of Its Database Solution Oceanbase

2,593 posts | 791 followers
FollowAlibaba Clouder - April 8, 2020
Alibaba Clouder - March 26, 2020
Alibaba Clouder - April 24, 2020
Iain Ferguson - May 9, 2022
Alibaba Clouder - March 12, 2020
Alibaba Clouder - November 3, 2020

2,593 posts | 791 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More ApsaraDB RDS for MySQL
ApsaraDB RDS for MySQL
An on-demand database hosting service for MySQL with automated monitoring, backup and disaster recovery capabilities
Learn More ApsaraDB RDS for PostgreSQL
ApsaraDB RDS for PostgreSQL
An on-demand database hosting service for PostgreSQL with automated monitoring, backup and disaster recovery capabilities
Learn MoreMore Posts by Alibaba Clouder