Network transmission encryption
Network transmission encryption refers to secure authentication of the http network transmission protocol by businesses through the use of the https protocol to transmit data. It is recommended to encrypt the key business information provided to the public through the network transmission process.
Alibaba Cloud provides the ability to provide network transmission encryption by using the Alibaba Cloud SSL Certificate Service. The SSL Certificate Service provides a certificate application and deployment service on the Alibaba Cloud platform, which allows you to convert your service from HTTP to HTTPS at a lower cost. It achieves identity authentication and data encryption in transit for your website or mobile application.
Dynamic data encryption
Alibaba Cloud provides data dynamic encryption services. By integrating the Key Management Service (KMS) with user application systems, data dynamic encryption can be achieved, ensuring that data is encrypted before being written to or read from databases or storage. This provides more comprehensive protection for data security during dynamic transmission. Application data encryption using KMS requires integration of the KMS SDK or API to achieve application data encryption.
Select Data Encryption Keys
Alibaba Cloud Key Management Service provides different types of keys for cloud service encryption and application encryption scenarios. Please note that the default key provided by Alibaba Cloud Key Management Service can only be used for cloud service encryption and cannot be used for application encryption.
Key Categories | Key Specifications | Encryption Methods | Usage | Limitations | Costs |
Default Key | Aliyun_AES_256 | GCM | Only used for cloud service server encryption | Each Alibaba Cloud UID supports only one default key | Free |
Software Key |
| GCM, ECB, CBC RSAES_OAEP_SHA_256 ECIES_DH_SHA_1_XOR_HMAC | Used for cloud service server encryption and application client encryption | Refer to Billing | Refer to Billing |
Hardware Key |
| GCM, ECB, CBC RSAES_OAEP_SHA_256 ECIES_DH_SHA_1_XOR_HMAC SM2PKE | Used for cloud service server encryption and application client encryption Suitable for financial-level data encryption scenarios Supports national cryptographic algorithms | Refer to Billing | Refer to Billing |
Generally, it is recommended to choose software key encryption for application encryption scenarios.
For the software key category, check for the key types and specifications of symmetric keys and asymmetric keys.
Integration of Applications with KMS
Application systems can integrate with KMS through APIs or use pre-packaged KMS SDKs to connect to KMS and utilize encryption services.
Refer to access a KMS instance by using an AAP.
Choose to use a RAM role for API requests.
Choose to use a client key for data signature and authentication between KMS and application.
Providing Data Encryption In Transit
When providing data encryption for application systems, it is desirable to perform data encryption after the data is generated and before it is written to the database. Alibaba Cloud Key Management Service provides different encryption methods to support symmetric encryption and asymmetric encryption. The two methods are slightly different when using the KMS service.
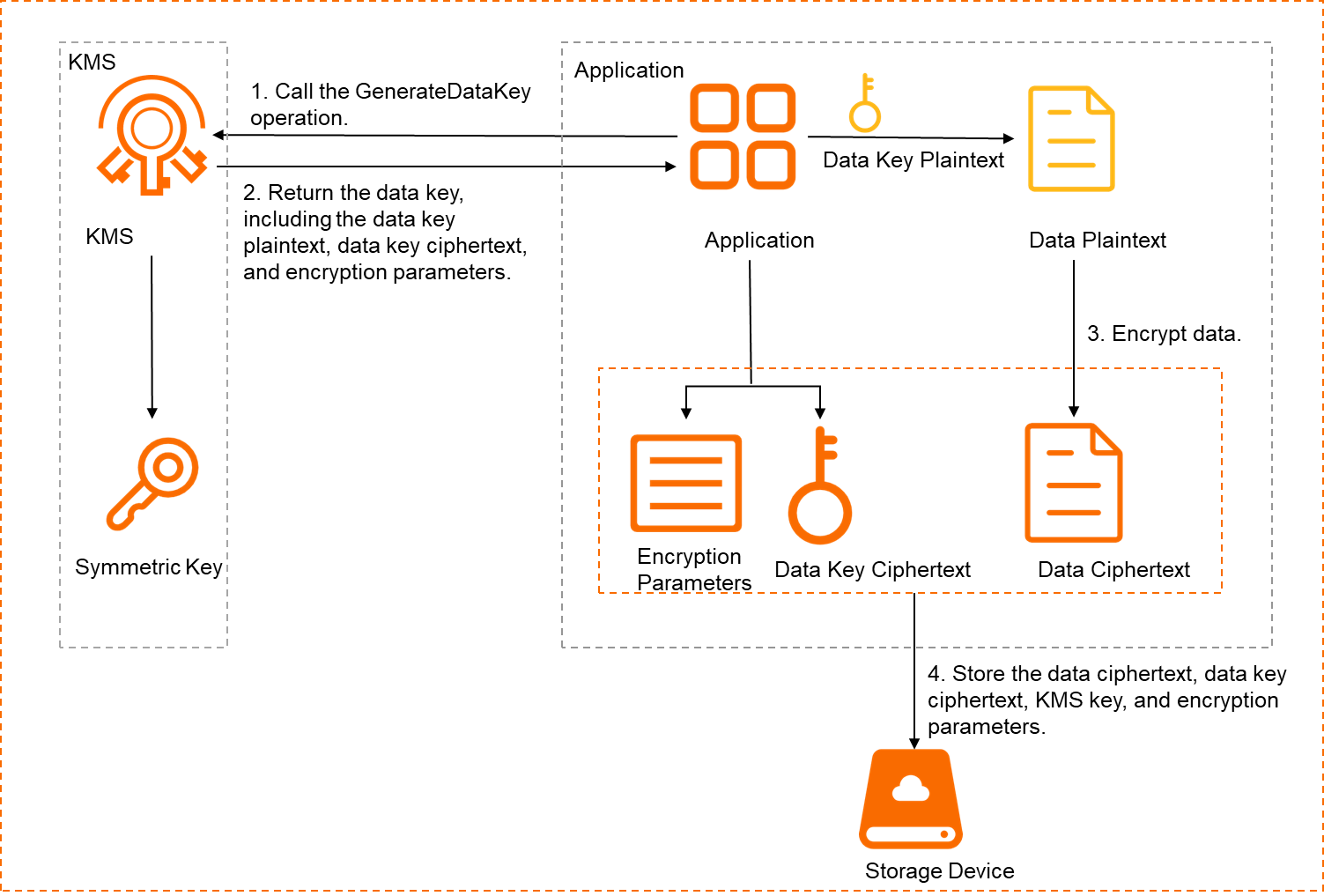
When using KMS symmetric encryption, the data encryption operation actually occurs on the KMS server, and a symmetric key is used for data encryption. Refer to Use a key to encrypt and decrypt data for details. The specific process is shown in the following image:
Providing Envelope Encryption for Data Keys
When using KMS asymmetric encryption (envelope encryption), the data encryption operation actually occurs locally (in the application environment). The application program interacts with KMS and performs local encryption operations on the data key (symmetric key) using the asymmetric encryption method. Refer to Use envelope encryption for details. The specific process is shown in the following image: