After you add a website to Web Application Firewall (WAF), you can configure a whitelist for web intrusion prevention. If the requests that are destined for the website meet specific conditions, the Protection Rules Engine do not detect the requests. Web intrusion prevention may block normal access requests based on specific rules. You can use a whitelist to allow this type of requests.
Prerequisites
A WAF instance is purchased.
Your website is added to WAF. For more information, see Tutorial.
Background information
Web intrusion prevention protects your website against common web attacks and zero-day vulnerabilities. Web intrusion prevention provides the following protection features, see Protection Rules Engine.
After you enable the preceding protection features, normal access requests may be blocked. If normal access requests are blocked by the protection features, you can configure a whitelist. Then, the protection features do not detect the requests that meet specific conditions. We recommend that you configure a whitelist based on your business requirements.
Procedure
Log on to the WAF console.
In the top navigation bar, select the resource group and the region in which the WAF instance is deployed. You can select Chinese Mainland or Outside Chinese Mainland.
In the left-side navigation pane, choose .
In the upper part of the Website Protection page, select the domain name for which you want to configure protection from the Switch Domain Name drop-down list.
Click the Web Security tab, find the Web Intrusion Prevention section, and then click Settings.
Create a whitelist rule for web intrusion prevention.
On the Web Intrusion Prevention - Whitelisting page, click Create Rule.
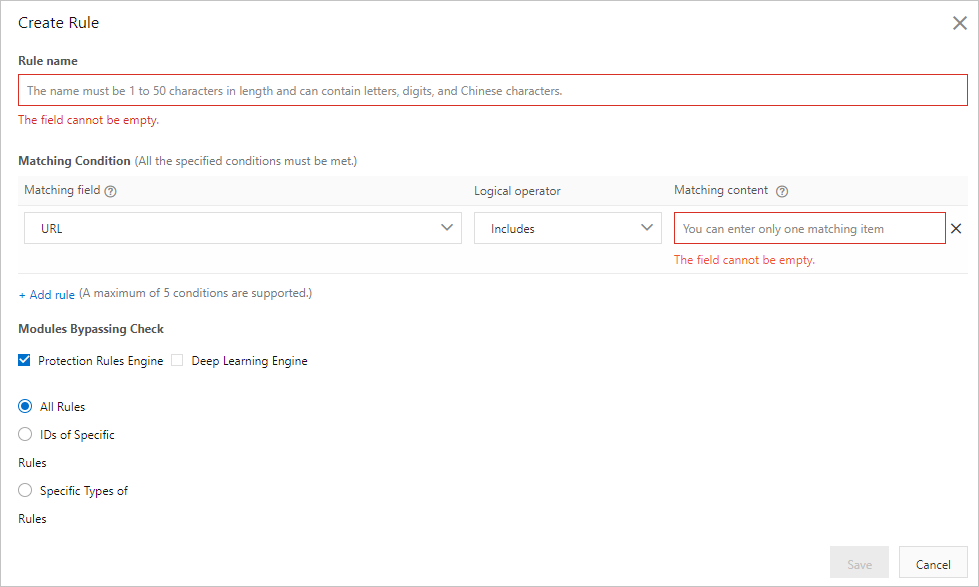
In the Create Rule dialog box, configure the following parameters.
Parameter
Description
Rule name
The name of the rule that you want to create.
The name must be 1 to 50 characters in length and can contain letters and digits.
Matching Condition
The condition based on which requests are allowed. Click Add rule to add more conditions. You can add a maximum of five conditions. If you specify multiple conditions, the rule is matched only if all the conditions are met.
For more information about conditions, see Fields in match conditions.
Bypassed Modules
The protection feature that does not detect requests if the requests meet the specified conditions. Valid values: Protection Rules Engine.
If you select Protection Rules Engine, All Rules is automatically selected. In this case, all rules in the protection rules engine are skipped for requests. You can specify the rules or rule types that you want to skip based on your business requirements. To specify the rules or rule types, perform the following steps:
Select Protection Rules Engine.
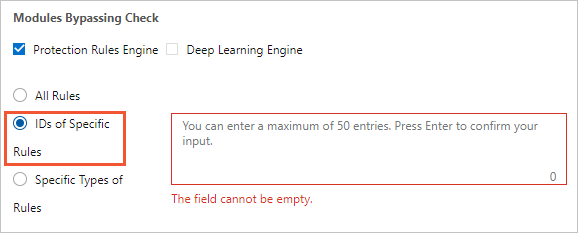
Optional:If you want to skip specific rules, select IDs of Specific Rules and enter the IDs of the rules.
To view the IDs of rules, you can click Create Rule Group on the Protection Rule Group page. The Create Rule Group page displays all protection rules that are included in WAF. For more information, see Customize protection rule groups.
Press Enter each time you enter a rule ID. You can enter a maximum of 50 rule IDs.
NoteYou can also create a whitelist rule on the Security Report page. On the Web Intrusion Prevention tab of the page, find the rule ID that you want to manage and click Ignore False Positives in the Actions column. After you click Ignore False Positives, WAF automatically generates a whitelist rule based on the characteristics of attack requests. You do not need to manually configure conditions or query rule IDs. For more information, see View security reports on the Web Security tab.
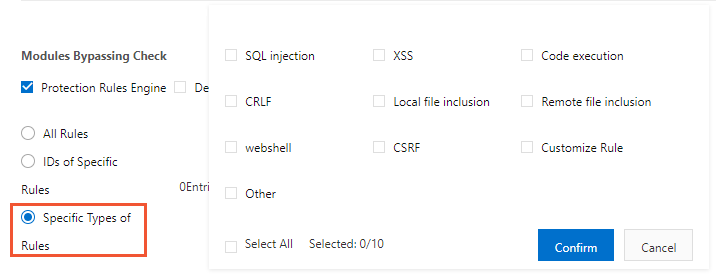
Optional:If you want to skip specific types of rules, select Specific Types of Rules, select the rule types, and then click Confirm.
Click Save.
After you create the whitelist rule, the whitelist rule is automatically enabled. You can view, disable, edit, or delete the rule in the rule list based on your business requirements.
ImportantBy default, a whitelist rule is permanently valid after you create it. If you no longer need a whitelist rule, you can disable or delete it.