The protection rules engine feature uses built-in rules and automatically protects websites against common web attacks, such as SQL injection attacks, cross-site scripting (XSS) attacks, webshell uploads, command injection attacks, backdoor isolation, illegal file requests, path traversals, and exploitation of vulnerabilities.
Prerequisites
A WAF instance is purchased.
Your website is added to WAF. For more information, see Tutorial.
Background information
By default, the protection rules engine feature is enabled. After you add a website to WAF, the feature protects the website.
The Alibaba Cloud security team accumulates a large number of basic protection rules to defend against web attacks. WAF uses these rules to protect your websites against common web attacks. You can specify a group of protection rules that you want the protection rules engine feature to use based on your business requirements. WAF provides the following built-in protection rule groups based on the level of security strictness:
Medium rule group: By default, this rule group is selected.
Loose rule group: We recommend that you select this rule group to reduce false positives.
Strict rule group: We recommend that you select this rule group to enhance the accuracy of attack detection.
You can also configure a custom group. For more information, see Customize protection rule groups.
Intelligent rule hosting
By default, the intelligent rule hosting feature is enabled, which helps reduce false positives that are caused by the protection rules engine.
The feature automatically learns the pattern of historical traffic of your website by using intelligent algorithms and identifies the protection rules that are not suitable for specific services or interfaces based on Alibaba Cloud threat intelligence. These protection rules may cause false positives or false positive alerts for specific services or interfaces. Then, the feature adds the identified protection rules to the whitelist for web intrusion prevention to help reduce false positives and ensure protection performance. For more information about the whitelist for web intrusion prevention, see Configure a whitelist for web intrusion prevention. After the risk of false positives is eliminated, the protection rules engine feature automatically deletes the rules that are automatically added to the whitelist.
Procedure
Log on to the WAF console.
In the top navigation bar, select the resource group and the region in which the WAF instance is deployed. You can select Chinese Mainland or Outside Chinese Mainland.
In the left-side navigation pane, choose .
In the upper part of the Website Protection page, select the domain name for which you want to configure protection from the Switch Domain Name drop-down list.
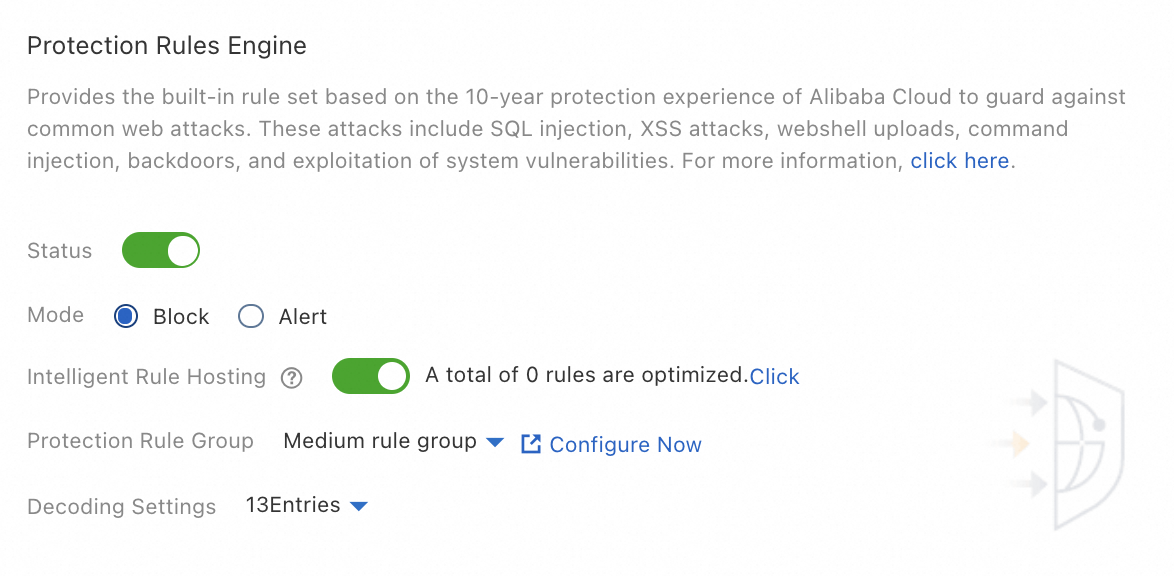
On the Web Security tab, configure the parameters in the Protection Rules Engine section. The following table describes the parameters.
Parameter
Description
Status
Specifies whether to enable the protection rules engine feature. By default, the protection rules engine feature is enabled. The feature protects the websites that are added to WAF against common web attacks.
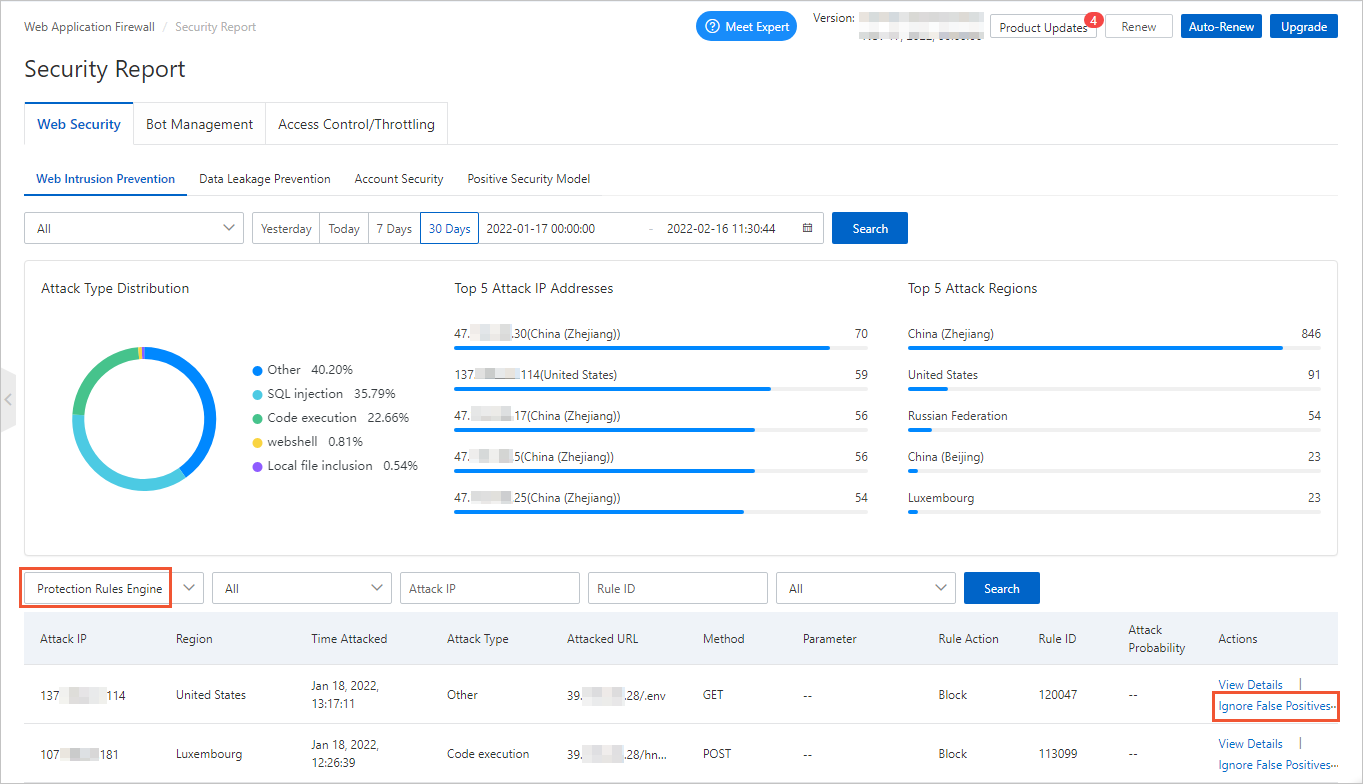
To view the attacks blocked by the protection rules engine feature, go to the Security Report page and choose . If a normal request is blocked by a rule, find the rule and click Ignore False Positives in the Actions column. For more information, see View security reports on the Web Security tab.
Mode
The action that you want to perform on attacks that are detected by WAF. Valid values:
Block: blocks attacks.
Warn: triggers alerts but does not block attacks.
Intelligent Rule Hosting
Specifies whether to enable Intelligent Rule Hosting. By default, the intelligent rule hosting feature is enabled. The feature dynamically manages the whitelist for web intrusion prevention to reduce false positives.
To view the number of rules that are automatically added to the whitelist, view A total of xxx rules are optimized in the Protection Rules Engine section. To view the rules, click Click to go to the Web Intrusion Prevention - Whitelist page and set the rule source to Intelligent Rule Hosting. You can modify or delete the rules that are automatically added to the whitelist.
After the risk is eliminated, the rules that are automatically added to the whitelist are deleted.
ImportantIf you modify a rule that is automatically added to the whitelist, the rule is automatically deleted after the risk is eliminated.
The rules that you manually add to the whitelist are not automatically deleted after the risk is eliminated.
Protection Rule Group
The protection rule group that you want to use. WAF allows you to create custom rule groups and provides the following built-in rule groups:
Medium rule group: detects common web application attacks based on the standard protection level. By default, this rule group is used.
Strict rule group: strictly detects web application attacks, such as path traversals, SQL injection attacks, and command injection attacks.
Loose rule group: loosely detects common web application attacks. If a high false positive rate exists when you apply the medium rule group or a large amount of uncontrollable user input, such as rich text editors and technical forums, is involved in your business, we recommend that you select the loose rule group.
You can click Configure Now to go to the Protection Rule Group page. On this page, you can create custom rule groups. Then, select rules based on your business requirements. For more information, see Customize protection rule groups.
Decoding Settings
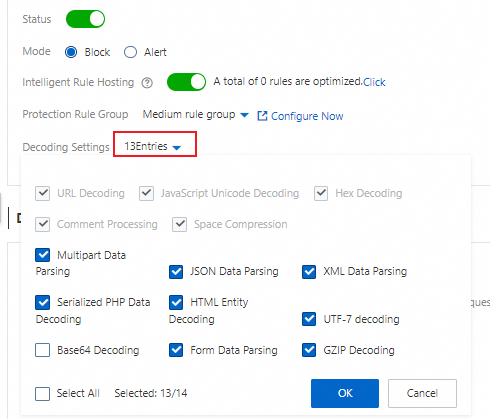
The data formats that you want the protection rules engine feature to decode and analyze.
By default, the protection rules engine feature decodes and analyzes the request data in all formats. This ensures protection performance. If the protection rules engine feature blocks normal requests that contain data in specific formats, you can clear the formats to reduce the false positive rate.
You can select the format that you want to decode or clear the format that you want to decode that you do not want to decode in the Decode Settings drop-down list.
ImportantYou cannot clear the following formats: URL Decoding, JavaScript Unicode Decoding, Hex Decoding, Comment Processing, and Space Compression.
By default, Base64 Decoding is not selected.
Query protection rules
You can use the following methods to query the latest protection rules that are added for the protection rules engine feature and query all protection rules that are included in the protection rules engine feature:
Query the latest protection rules
Log on to the WAF console. On the Overview page, click the items in the Urgent Vulnerability section to view the latest protection rules.
The Urgent Vulnerability section displays the updated protection rules of WAF to help you handle the most recent security vulnerabilities that are disclosed on the Internet.
You can click a rule to open the Details panel. The panel displays the domain names that are affected by the vulnerability, the details of the vulnerability, and information about the protection rules.
Query all protection rules
Log on to the WAF console. In the left-side navigation pane, choose .
On the Protection Rule Group page, you can use the following methods to view all protection rules that are included in the protection rules engine feature:
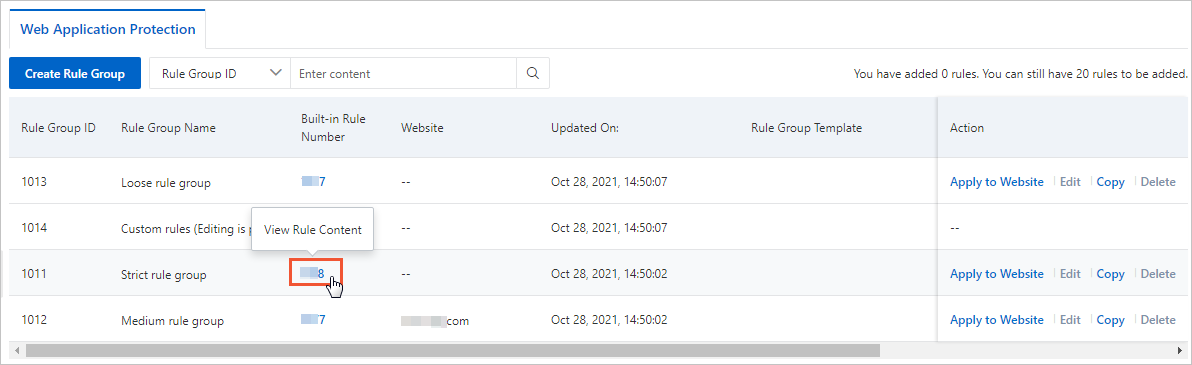
On the Web Intrusion Protection tab, find Strict rule group and click the number in the Built-in Rules column.
The strict rule group is a built-in rule group. The group contains all protection rules of the protection rules engine feature and cannot be modified.
NoteThe number of protection rules of the protection rules engine feature dynamically changes. The number of protection rules that are displayed in the WAF console may be different from the number shown in the following figure.
In the Built-in Rules panel, query the protection rules that you want to view.
You can configure Severity, Protection Type, and Application Type to filter protection rules. You can also use Rule ID or CVE ID to query a protection rule. You can obtain a rule ID on the Overview or Security Report page.
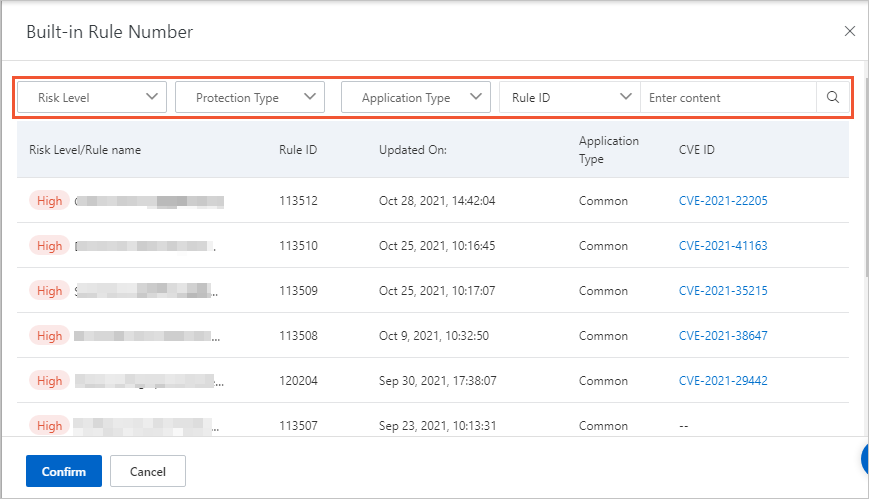
The rule list displays the following information: Severity/Rule Name, Rule ID, Updated On, Application Type, CVE ID, Protection Type, and Rule Description.
You can click a CVE ID to view the details of the vulnerability.