TLS versions include TLS v1.0 (disabled), TLS v1.1, TLS v1.2, and TLS v1.3. A higher TLS version improves the security of HTTPS communication. However, higher TLS versions have lower browser compatibility than lower versions. You can set a suitable TLS version on the web server or Alibaba Cloud product where the certificate is installed, based on your requirements.
Certificate deployed on an Alibaba Cloud product
If your certificate is deployed on one of the following Alibaba Cloud products, follow the corresponding procedure to set the TLS version. The following sections provide brief steps. For complete information, see the linked documentation.
Anti-DDoS Proxy
Procedure
Log on to the Anti-DDoS Proxy console.
In the top navigation bar, select the region of your instance.
Anti-DDoS Proxy (Chinese Mainland): Choose the Chinese Mainland region.
Anti-DDoS Proxy (Outside Chinese Mainland): Choose the Outside Chinese Mainland region.
In the left-side navigation pane, choose .
On the Website Config page, find the target domain name and click Edit in the Actions column.
On the Modify Website Configurations tab, modify the TLS Security Settings. For more information, see Customize the TLS security policy for an HTTPS server certificate.
Web Application Firewall
Procedure
Log on to the WAF 3.0 console. In the top navigation bar, select the resource group and region of the WAF instance. You can select Chinese Mainland or Outside Chinese Mainland.
In the left-side navigation pane, click Onboarding.
On the CNAME Record tab, click Default SSL/TLS Settings above the list.

In the Default SSL/TLS Settings dialog box, set the default TLS version for WAF and click OK.
Parameter
Description
HTTPS Upload Type
Upload an SSL Certificate. The procedure is the same as uploading a domain name certificate. For more information, see Upload a certificate.
TLS Version
Select the TLS versions to enable. Options:
(Default) TLS 1.0 and Later (Best Compatibility and Low Security)
TLS 1.1 and Later (High Compatibility and High Security)
TLS 1.2 and Later (High Compatibility and Best Security)
To enable TLS 1.3, select Support TLS 1.3.
HTTPS Cipher Suite
Select the cipher suites to enable. Options:
(Default) All Cipher Suites (High Compatibility and Low Security)
Custom Cipher Suite (Select It based on protocol version. Proceed with caution.)
For information about supported custom cipher suites, see Cipher suites supported by WAF.
For more information, see Add a website to WAF using a CNAME.
Server Load Balancer (SLB)
Procedure
When you create or configure an HTTPS listener for a high-performance Classic Load Balancer (CLB) instance, you can select a TLS security policy. When you add or configure an HTTPS listener, on the Certificate Management Service wizard page, click Advanced Settings and then click Modify to select a TLS security policy from the expanded section. The following example describes how to configure the TLS protocol versions for a CLB instance.
The Server Load Balancer (SLB) product family includes Application Load Balancer (ALB), Network Load Balancer (NLB), and Classic Load Balancer (CLB). You can select an SLB product based on your requirements.
Log on to the Classic Load Balancer (CLB) console.
In the top menu bar, select the region where the instance is deployed.
On the Instances page, find the target instance and click Configure Listener in the Actions column.
On the Protocol & Listener wizard page, set Select Listener Protocol to HTTPS. Configure the other parameters and click Next. For information about how to configure the other parameters, see Add an HTTPS listener.
On the Certificate Management Service configuration wizard, select an uploaded server certificate. Alternatively, in the Server Certificate section, click Create Server Certificate to upload a server certificate. You can also purchase a certificate. For more information about certificates, see Create a Certificate.
Click Modify next to Advanced Settings and select a TLS Security Policy.
NoteOnly guaranteed-performance instances support TLS security policies.
A TLS security policy includes optional TLS versions for HTTPS and their corresponding cipher suites. For more information, see TLS security policies.
Complete the configurations on the subsequent wizard pages and click Submit. For more information about the wizard configurations, see Add an HTTPS listener for a CLB instance.
For more information, see Add an HTTPS listener.
CDN
Procedure
Before you begin, make sure that you have configured an HTTPS certificate. For more information, see Configure an HTTPS certificate.
TLS v1.0, TLS v1.1, TLS v1.2, and TLS v1.3 are enabled by default.
Log on to the CDN console.
In the left navigation pane, click Domain Names.
On the Domain Names page, find the target domain name and click Manage in the Actions column.
In the domain's navigation pane, click HTTPS.
In the Configure TLS Cipher Suite and Version section, configure the cipher suite and versions based on your business requirements.
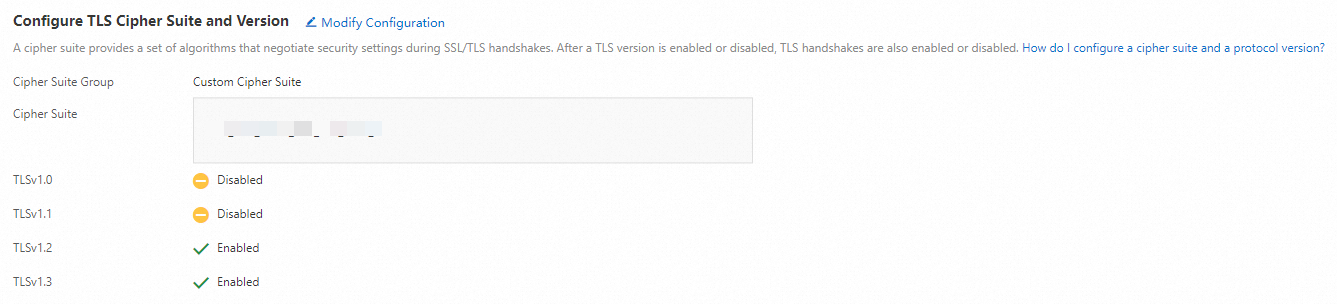
The following cipher suites are supported. Select a cipher suite based on your business requirements:
All Cipher Suite Groups (Default): Provides low security and high compatibility. For information about supported encryption algorithms, see Default TLS encryption algorithmsDefault TLS encryption algorithms.
Enhanced Cipher Suite: Provides high security and low compatibility. Supported encryption algorithms:
TLS_AES_256_GCM_SHA384
TLS_AES_128_GCM_SHA256
TLS_CHACHA20_POLY1305_SHA256
ECDHE-ECDSA-CHACHA20-POLY1305
ECDHE-RSA-CHACHA20-POLY1305
ECDHE-ECDSA-AES128-GCM-SHA256
ECDHE-RSA-AES128-GCM-SHA256
ECDHE-ECDSA-AES128-CCM8
ECDHE-ECDSA-AES128-CCM
ECDHE-ECDSA-AES256-GCM-SHA384
ECDHE-RSA-AES256-GCM-SHA384
ECDHE-ECDSA-AES256-CCM8
ECDHE-ECDSA-AES256-CCM
ECDHE-ECDSA-ARIA256-GCM-SHA384
ECDHE-ARIA256-GCM-SHA384
ECDHE-ECDSA-ARIA128-GCM-SHA256
ECDHE-ARIA128-GCM-SHA256
Custom Cipher Suite: Select a cipher suite based on your business requirements.
For more information about TLS versions, see Background information.
For more information, see Configure TLS versions and cipher suites.
DCDN
Procedure
Before you begin, make sure that you have configured an HTTPS certificate. For more information, see Configure an HTTPS certificate.
By default, TLS 1.0, TLS 1.1, TLS 1.2, and TLS 1.3 are enabled.
Log on to the DCDN console.
In the left-side navigation pane, click Domain Names.
On the Domain Names page, find the domain name that you want to manage and click Configure.
In the left-side navigation tree of the domain name, click HTTPS Settings.
In the Configure TLS Cipher Suite and Version section, select cipher suites and enable TLS versions based on your requirements.
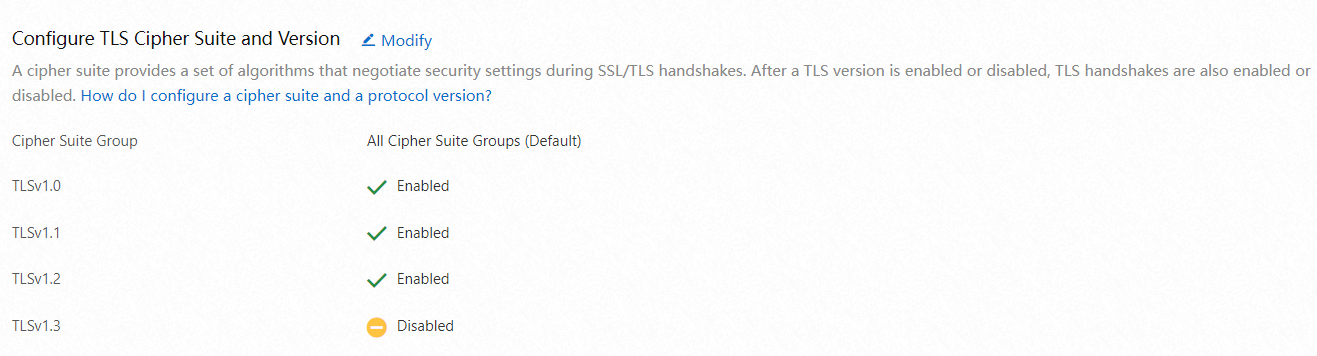
The following cipher suites are supported. Select a cipher suite based on your business requirements:
All Cipher Suite Groups (Default): Provides low security and high compatibility. For more information about the supported encryption algorithms, see Default TLS encryption algorithms supported by DCDN.
Enhanced Cipher Suite: Provides high security and low compatibility. The supported encryption algorithms are:
TLS_AES_256_GCM_SHA384
TLS_AES_128_GCM_SHA256
TLS_CHACHA20_POLY1305_SHA256
ECDHE-ECDSA-CHACHA20-POLY1305
ECDHE-RSA-CHACHA20-POLY1305
ECDHE-ECDSA-AES128-GCM-SHA256
ECDHE-RSA-AES128-GCM-SHA256
ECDHE-ECDSA-AES128-CCM8
ECDHE-ECDSA-AES128-CCM
ECDHE-ECDSA-AES256-GCM-SHA384
ECDHE-RSA-AES256-GCM-SHA384
ECDHE-ECDSA-AES256-CCM8
ECDHE-ECDSA-AES256-CCM
ECDHE-ECDSA-ARIA256-GCM-SHA384
ECDHE-ARIA256-GCM-SHA384
ECDHE-ECDSA-ARIA128-GCM-SHA256
ECDHE-ARIA128-GCM-SHA256
Custom Cipher Suite: Allows you to select custom cipher suites based on your requirements.
For more information, see Configure TLS versions and cipher suites.
If you have questions during the configuration, contact your account manager for the product.
Certificate deployed on a web server that is not an Alibaba Cloud product
To ensure the security and compatibility of your web server, you can adjust the ssl_protocols parameter in the server's certificate configuration file. This lets you enable or disable specific TLS versions based on your requirements. For example, if your environment supports only TLS v1.1 and TLS v1.2, set the ssl_protocols parameter to TLSv1.1 TLSv1.2. If you also need to enable TLS v1.3, set the ssl_protocols parameter to TLSv1.1 TLSv1.2 TLSv1.3.
The following procedure uses Nginx as an example to show how to modify the TLS versions that Nginx supports.
Step 1: Open the Nginx configuration file
Run the following command to open the Nginx configuration file for editing. This file is usually located at /etc/nginx/nginx.conf or in a .conf file within the /etc/nginx/conf.d/ directory.
sudo nano /etc/nginx/nginx.confIf you have a separate site configuration file, the path may be similar to the following:
sudo nano /etc/nginx/sites-available/defaultStep 2: Modify SSL settings in the server block
Find the server block related to HTTPS. Add or modify the ssl_protocols line to specify the supported TLS versions. The following example shows how to enable TLS 1.2 and TLS 1.3 in the configuration file. Make sure that your clients support the configured TLS versions. Otherwise, connection failures may occur.
server {
listen 443 ssl;
server_name yourdomain.com;
# Paths to the SSL certificate and key
ssl_certificate /path/to/your_certificate.crt;
ssl_certificate_key /path/to/your_private.key;
# Set the supported SSL/TLS versions
ssl_protocols TLSv1.2 TLSv1.3;
# Optional: Set more secure cipher suites
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
location / {
root /var/www/html;
index index.html index.htm;
}
}Step 3: Restart the Nginx service
After you save the changes, run the following command to restart the Nginx service for the configuration to take effect:
sudo systemctl reload nginxOr:
sudo service nginx restartThese steps modify the TLS versions on the Nginx server.
Step 4: Verify that the TLS versions are set successfully
Run the following command to test the server's TLS configuration:
# Replace "your_ip" with your actual IP address. sudo openssl s_client -connect your_ip:443Check the protocol version and certificate information in the output to confirm that the TLS configuration has taken effect. If the output includes information about the specified TLS versions, the configuration is successful.

New security standards may emerge over time, and old standards may become deprecated. Regularly review and update your encryption standards to keep your website secure.