Manually managing SSL certificates for cloud servers is complex, error-prone, and repetitive. To address this, the Certificate Management Service offers automated deployment. This feature enables one-click deployment to Elastic Compute Service (ECS) instances and automatic updates for ECS and Simple Application Server, significantly improving efficiency and minimizing configuration risks.
Choose a deployment method
Select a method based on your server type and installation scenario.
Feature | Method 1: One-click deployment (for initial deployment) | Method 2: Manual deployment (for updating certificates) |
Core mechanism | Fully automated. The private key never leaves the instance and communicates with the hardware trusted module through a PKCS#11 interface, which ensures high security. | Semi-automated. Uploads the certificate file to a specified path on the server to overwrite the old file. |
Supported servers | Supports only specific truste ECS instances (7th/8th generation x86 architecture). Simple Application Server is not supported. | Supports all ECS and Simple Application Server instances. |
Supported operating systems | Alibaba Cloud Linux 3.x, Ubuntu 22.04 UEFI images. | All major Linux and Windows Server distributions. |
Supported web servers | Supports only specific versions of Nginx installed from | Supports all web servers, such as Nginx, Apache, and Tomcat. |
SSL certificate requirements | Single-domain SSL certificates that use the RSA algorithm. | All types of SSL certificates. |
Use cases | Initial deployment on eligible trusted ECS instances to enable fully automated renewals. | Updating an existing certificate on an ECS or Simple Application Server instance. |
If neither of the preceding methods meets your needs, see SSL certificate deployment solution selection to choose a different deployment solution.
Method 1: One-click deployment (for initial deployment to a trusted ECS instance)
This method integrates with the security module of an ECS trusted instance to achieve fully automated and highly secure deployment of certificates and private keys. If you purchase a multi-year certificate, the system automatically updates it after each renewal.
Usage notes
Instance types and specifications: 7th and 8th generation x86-based trusted ECS instances. For more information, see Create a trusted instance.
Operating system: Alibaba Cloud Linux 3.x, Ubuntu 22.04 UEFI images.
Web server: Specific versions of Nginx installed from
yumoraptsources.Alibaba Cloud Linux 3.x image: Nginx installed using yum, with a version from 1.18.0-2.1.al8 to 1.20.1-1.0.5.al8 (exclusive).
Ubuntu 22.04 UEFI image: Nginx installed using apt.
Certificate type and status: Single-domain SSL certificates that use the RSA algorithm. The certificate status must be Issued.
Server permissions: You need a
rootaccount or an account withsudoprivileges.Domain name resolution: The domain's DNS record is configured and resolves to the server's public IP address.
Step 1: Verify the Cloud Assistant status
Ensure Cloud Assistant is correctly installed on your ECS instance. Otherwise, the one-click deployment feature in the console is unavailable.
Select the resource group and region where the target resource is located.
On the ECS Instances tab, locate the target ECS server and check its status in the Cloud Assistant Status column.
NoteIf Cloud Assistant is not installed or its status is abnormal, see Check Cloud Assistant status and troubleshoot abnormal statuses.
Step 2: Configure the Nginx web application server on the ECS instance
For an initial deployment, you must modify the Nginx configuration file to allow it to call the private key from the trusted module through the PKCS#11 interface. This step is not required for subsequent updates.
Alibaba Cloud Linux 3.x images
This section uses Nginx 1.20.1 as an example. The default installation directory for Nginx installed via yum is /etc/nginx/. If you have changed this directory, adjust the configurations accordingly.
Confirm your Nginx version.
Only Nginx versions from 1.18.0-2.1.al8 to 1.20.1-1.0.5.al8 (exclusive) are supported.
ImportantIf Nginx is already installed on your ECS instance, check its version before using the one-click deployment feature. If not, you must downgrade it to a supported version or reinstall it.
Open the
/etc/nginx/nginx.confconfiguration file and addssl_engine pkcs11;afterpid /run/nginx.pid;to specify the use of the PKCS#11 encryption library. See the following example for the location and complete configuration:user nginx; worker_processes auto; error_log /var/log/nginx/error.log; pid /run/nginx.pid; # Specify the use of the PKCS#11 encryption library. ssl_engine pkcs11;Open the
/etc/nginx/nginx.confconfiguration file, uncomment the Settings for a TLS enabled server section, and addinclude "/etc/acm/ssl/nginx-acm.conf";to reference the SSL key configuration.Content to add:
include "/etc/acm/ssl/nginx-acm.conf";Location and complete example:
server { listen 443 ssl http2; listen [::]:443 ssl http2; # Specify the hostname or Common Name (CN). server_name example.com; root /usr/share/nginx/html; ssl_session_cache shared:SSL:1m; ssl_session_timeout 10m; ssl_prefer_server_ciphers on; # Reference the SSL key configuration. include "/etc/acm/ssl/nginx-acm.conf"; # Load configuration files for the default server block. include /etc/nginx/default.d/*.conf; error_page 404 /404.html; location = /40x.html { } error_page 500 502 503 504 /50x.html; location = /50x.html { } }
Open the
/usr/lib/systemd/system/nginx.servicefile and addP11_KIT_SERVER_ADDRESS=unix:path=/etc/acm/ssl/acm-p11-kit.sockandOPENSSL_CONF=/etc/acm/ssl/openssl-acm.cnfto configure communication with the SSL key service.Content to add:
Environment="P11_KIT_SERVER_ADDRESS=unix:path=/etc/acm/ssl/acm-p11-kit.sock" Environment="OPENSSL_CONF=/etc/acm/ssl/openssl-acm.cnf"Location and complete example:
[Unit] Description=A high performance web server and a reverse proxy server Documentation=man:nginx(8) After=network.target nss-lookup.target [Service] Type=forking PIDFile=/run/nginx.pid ExecStartPre=/usr/sbin/nginx -t -q -g 'daemon on; master_process on;' ExecStart=/usr/sbin/nginx -g 'daemon on; master_process on;' ExecReload=/usr/sbin/nginx -g 'daemon on; master_process on;' -s reload ExecStop=-/sbin/start-stop-daemon --quiet --stop --retry QUIT/5 --pidfile /run/nginx.pid TimeoutStopSec=5 KillMode=mixed # Configure communication with the SSL key service. Environment="P11_KIT_SERVER_ADDRESS=unix:path=/etc/acm/ssl/acm-p11-kit.sock" Environment="OPENSSL_CONF=/etc/acm/ssl/openssl-acm.cnf" [Install] WantedBy=multi-user.targetNoteIf you do not know the path to the Nginx systemd service configuration file, run
sudo find / -name "nginx.service"to find it.
Run the following command to reload the Nginx systemd service configuration.
systemctl daemon-reload
Ubuntu 22.04 image
This topic uses Nginx 1.18.0 as an example. /etc/nginx/ is the default installation directory for Nginx installed using apt. If you have changed this directory or installed Nginx using a different method, adjust the paths accordingly.
Open the
/etc/nginx/nginx.confconfiguration file and addssl_engine pkcs11;afterpid /run/nginx.pid;to specify the use of the SSL/TLS encryption library. The following code block shows the location and a complete example:user www-data; worker_processes auto; pid /run/nginx.pid; # Specify the use of the PKCS#11 encryption library. ssl_engine pkcs11; include /etc/nginx/modules-enabled/*.conf;Open the
/etc/nginx/sites-enabled/defaultfile, create a new server block in the default file, and addinclude "/etc/acm/ssl/nginx-acm.conf";.Content to add:
include "/etc/acm/ssl/nginx-acm.conf";Location and complete example:
server { listen 443 ssl; # Specify the hostname or Common Name (CN). server_name example.com; root /var/www/html; index index.html index.htm; access_log /var/log/nginx/access_6equj5.log; error_log /var/log/nginx/error_6equj5.log; ssl on; # Reference the SSL key configuration. include "/etc/acm/ssl/nginx-acm.conf"; location / { try_files $uri $uri/ =404; } }
Open the
/usr/lib/systemd/system/nginx.servicefile and addP11_KIT_SERVER_ADDRESS=unix:path=/etc/acm/ssl/acm-p11-kit.sockandOPENSSL_CONF=/etc/acm/ssl/openssl-acm.cnfto configure communication with the SSL key service.NoteIf you do not know the path to the Nginx systemd service configuration file, run
sudo find / -name "nginx.service"to find it.Content to add:
Environment="P11_KIT_SERVER_ADDRESS=unix:path=/etc/acm/ssl/acm-p11-kit.sock" Environment="OPENSSL_CONF=/etc/acm/ssl/openssl-acm.cnf"Location and complete example:
[Unit] Description=A high performance web server and a reverse proxy server Documentation=man:nginx(8) After=network.target nss-lookup.target [Service] Type=forking PIDFile=/run/nginx.pid ExecStartPre=/usr/sbin/nginx -t -q -g 'daemon on; master_process on;' ExecStart=/usr/sbin/nginx -g 'daemon on; master_process on;' ExecReload=/usr/sbin/nginx -g 'daemon on; master_process on;' -s reload ExecStop=-/sbin/start-stop-daemon --quiet --stop --retry QUIT/5 --pidfile /run/nginx.pid TimeoutStopSec=5 KillMode=mixed # Configure communication with the SSL key service. Environment="P11_KIT_SERVER_ADDRESS=unix:path=/etc/acm/ssl/acm-p11-kit.sock" Environment="OPENSSL_CONF=/etc/acm/ssl/openssl-acm.cnf" [Install] WantedBy=multi-user.target
Run the following command to reload the Nginx systemd service configuration.
systemctl daemon-reload
Step 3: Deploy the certificate from the Certificate Management Service console
Log on to the Certificate Management Service console.
In the left navigation pane, choose .
On the Deployment to Cloud Servers page, click Create Task and follow these steps to deploy the SSL certificate.
On the Configure Basic Information page, enter a custom task name and click Next.
On the Select Certificate page, select the certificate type and the SSL certificate associated with the cloud server, and then click Next.
Each deployment task can deploy only one certificate. To deploy multiple certificates, create multiple deployment tasks.
On the Select Resource page, select an ECS instance that supports one-click deployment and click Next.

The system automatically detects and retrieves all eligible ECS instances under your Alibaba Cloud account. If no resources are displayed, click Synchronize Cloud Resources in the Total Resources area in the upper-left corner. The synchronization time varies based on the number of your cloud resources.
If there are many instances in the list, you can select Quick Deployment/Manual Deployment from the All Types drop-down list to quickly filter the list for supported instances.
On the Quick Deployment tab, confirm that the deployment environment requirements are met. If they are, select Confirm that the preceding operations are complete. and click Continue to Deploy.
In the dialog box that appears, click OK.
WarningRestarting the web application server will affect your business. We recommend that you perform the deployment during off-peak hours.

Reference command to manually restart Nginx:
systemctl restart nginx.serviceAfter restarting, you can use the curl command to test the Nginx SSL connection. The command format is
curl -v https://<your_domain_name>.
Step 4: Check the deployment task status
On the Deployment to Cloud Servers page, find the task that you created. If the Task Status is Deployed, the certificate has been successfully deployed to the cloud server.

Step 5: Verify that the SSL certificate is effective
A successful deployment task does not guarantee that the certificate is working correctly. You must verify its status by accessing your domain name.
Access your domain over HTTPS in a web browser. For example,
https://yourdomain. Replaceyourdomainwith your actual domain.If a lock icon appears in the browser's address bar, the certificate is deployed successfully. If you encounter access errors or the lock icon does not appear, clear your browser cache or try again in incognito (privacy) mode.

Starting from version 117, the
 icon in the Chrome address bar has been replaced with a new
icon in the Chrome address bar has been replaced with a new  icon. Click this icon to view the lock information.
icon. Click this icon to view the lock information.
Method 2: Manual deployment (for certificate updates)
This method updates certificates on cloud servers (ECS or Simple Application Server) where a certificate is already configured. It works by overwriting old certificate files, simplifying renewals and replacements. It is not suitable for initial deployment.
Usage notes
Cloud server type: Alibaba Cloud servers only, (Simple Application Server and Elastic Compute Service (ECS)).
Web server: Only web servers that directly reference PEM or CRT format certificates, such as Nginx and Apache. IIS is not supported.
Server permissions: You need a
rootaccount or an account withsudoprivileges.
Step 1: Deploy the SSL certificate
Log on to the Certificate Management Service console.
In the left navigation pane, choose .
On the Deployment to Cloud Servers page, click Create Task.
On the Configure Basic Information page, enter a Task Name and click Next.
On the Select Certificate page, select a Certificate Type, select the Associated Certificates, and then click Next.
Certificates issued by the Private CA service are synchronized to the Manage Uploaded Certificates tab.
On the Select Resource page, select a cloud server type, select the target instance, and then click Next. When you open this page for the first time, the system automatically detects and retrieves all eligible cloud server instances under your Alibaba Cloud account that have a web application deployed.
NoteIf no resources are displayed, you can click Synchronize Cloud Resources in the Total Resources area to manually synchronize them. The time required for synchronization varies depending on the number of cloud product resources.

On the Deployment Configuration page, configure the parameters as described in the following table and click OK.
ImportantThe Certificate Path and Private Key Path must match the paths configured in your web application. Otherwise, the certificate will not take effect.
The following figure shows the certificate file configuration path for Nginx on a cloud server. The path is for reference only.

Parameter
Description
Example (for reference only, use your actual paths)
Certificate Path
The absolute path where the certificate file is stored on the cloud server.
Linux:
/ssl/cert.pemWindows:
c:\ssl\cert.pem
Private Key Path
The absolute path where the private key file of the certificate is stored on the cloud server.
Linux:
/ssl/cert.keyWindows:
c:\ssl\cert.key
Certificate Chain Path
The absolute path where the certificate chain file is stored on the cloud server.
NoteIf a certificate chain file is configured in the web application, enter the path here.
Linux:
/ssl/cert.cerWindows:
c:\ssl\cert.cer
Reload Command
If a restart command is configured, it will be executed after certificate deployment to restart the web application or reload its configuration, making the certificate take effect.
ImportantIf the web application fails to restart, log on to the corresponding cloud server to handle it.
To reload Nginx configuration:
sudo nginx -s reload.To restart the Apache service:
sudo systemctl restart httpd.
In the dialog box that appears, click OK.
If you did not configure a restart command, the following prompt appears. Click OK, then log on to the cloud server and manually restart the web service to ensure the certificate takes effect immediately.
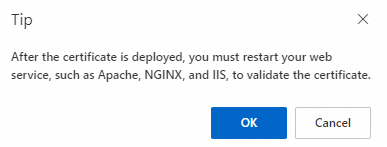
If you configured a restart command, the following prompt appears. Confirm the risks and click OK. The restart command will be executed after the deployment task finishes to ensure the certificate takes effect immediately.

Step 2: Check the deployment task status
On the Deployment to Cloud Servers page, find the task that you created. If the Task Status is Deployed, the certificate has been successfully updated on the cloud server.

Step 3: Verify that the SSL certificate is effective
Access your domain over HTTPS in a web browser. For example,
https://yourdomain. Replaceyourdomainwith your actual domain.If a lock icon appears in the browser's address bar, the certificate is deployed successfully. If you encounter access errors or the lock icon does not appear, clear your browser cache or try again in incognito (privacy) mode.

Starting from version 117, the
 icon in the Chrome address bar has been replaced with a new
icon in the Chrome address bar has been replaced with a new  icon. Click this icon to view the lock information.
icon. Click this icon to view the lock information.
If the issue persists, see FAQ for troubleshooting.
Quotas and limits
Deployment fees:
Deploying official certificates: Free, does not consume deployment quotas.
Deploying self-uploaded certificates: Consumes deployment quota. You must purchase deployment package at a cost of USD 5 per deployment. If a deployment fails, the quota will be refunded.
Quota limits:
Each deployment task supports deploying one certificate to one cloud server instance. To deploy to multiple instances, create multiple tasks.
Going live
Service interruption risk: Both deployment methods may require restarting the web service (such as Nginx or Apache), which will cause a brief service interruption. We strongly recommend performing deployment operations during off-peak hours.
Graceful reload: For web servers that support graceful reloads (such as Nginx), it is recommended to use
nginx -s reloadorsystemctl reload nginxinstead ofrestartin the Reload Command of Method 2 to minimize the impact on existing connections.Monitoring and alerts: After deploying the certificate, we recommend enabling domain monitoring. Alibaba Cloud will automatically check the certificate's validity and send reminders before expiration, helping you renew in time to avoid service interruptions. For details, see Purchase and enable public domain name monitoring.
FAQ
Why is my SSL certificate not working or HTTPS inaccessible after deployment?
This issue is typically caused by a misconfiguration in your environment or deployment settings. Check the following common causes:
Port 443 is blocked: Ensure that port 443 is open in your server's security group rules and any host-based firewalls (such as
firewalldor Windows Firewall).Domain mismatch: Verify that the domain you are accessing via HTTPS is explicitly listed as a Common Name (CN) or Subject Alternative Name (SAN) in the certificate details.
Deployment task failed: Go to the task details page, check the Task Status. Click View Failure Cause to diagnose the problem, correct your configuration, and run the task again.
For further troubleshooting, see Resolve certificate deployment issues based on browser error messages and SSL certificate deployment troubleshooting guide.
What do I do if I get the error "the cloud Assistant not install or run" during deployment?

Cause: Cloud Assistant is not installed on the ECS instance, or its status is abnormal.
Solution 1:
Find the target server and check the Cloud Assistant status.
If it is not installed, you can click Install to install it automatically.
If the status is abnormal, see Troubleshoot abnormal Cloud Assistant statuses for solutions.
After the Cloud Assistant status returns to normal, create a cloud server deployment task again in the Certificate Management Service console.
Solution 2:
See Install an SSL certificate on an Nginx or Tengine server (Linux) to manually install the certificate on an ECS server.