This topic helps you troubleshoot and resolve issues that occur after you manually deploy an SSL certificate, such as the certificate not taking effect or your website being marked as not secure.
Troubleshooting steps
Check if port 443 is open on the server.
If you use an Alibaba Cloud Elastic Compute Service (ECS) server, go to the Security Group page in the ECS console to check if port 443 is open. For more information about how to configure a security group, see Manage security groups.

If you use Web Application Firewall (WAF), check your server's firewall settings to ensure that they do not block external access to port 443.
Log on to the Web Application Firewall 3.0 console. From the top menu bar, select the resource group and region (Chinese Mainland or Outside Chinese Mainland) for the WAF instance.
In the left navigation pane, click Onboarding.
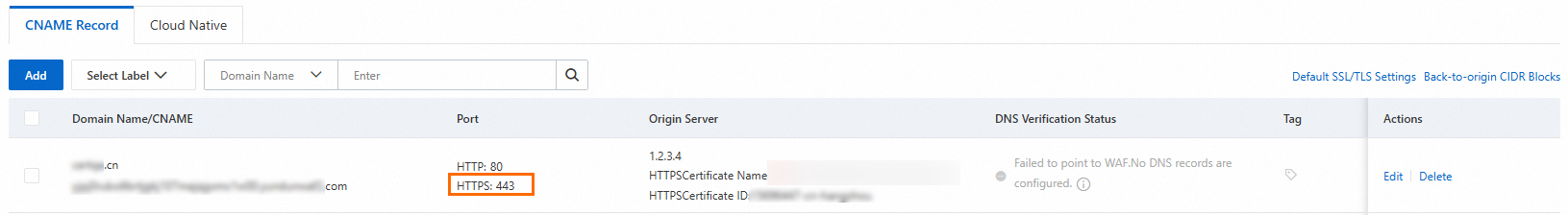
On the CNAME Record tab, check whether port 443 allows external access.
Check the web server configuration file.
Ensure that the certificate file name and path in the configuration file are correct. The certificate storage path and file name specified in the configuration file must exactly match the actual path and file name on the server. The following is a configuration example for Nginx:
server { # Port 443 is the default port for HTTPS listen 443 ssl; server_name example.com; # Replace the following paths with the paths to your SSL certificate and private key files ssl_certificate /etc/nginx/ssl/example.com.crt; ssl_certificate_key /etc/nginx/ssl/example.com.key; # Other configurations... }Ensure that the changes to the configuration file are saved.
Some web servers, such as Nginx and Apache, require a restart for the changes to the configuration file to take effect.
Restart the Nginx service.
sudo nginx -s reloadRestart the Apache service.
sudo systemctl restart httpd
Check the validity of the certificate.
Check if the certificate is within its validity period.
Log in to the Certificate Management Service console.
In the navigation pane on the left, choose Certificate Management > SSL Certificate Management.
On the SSL Certificate Management page, locate the deployed certificate and check if it is expired.
If the certificate has expired, renew it promptly. For more information about how to renew a paid certificate, see Renew an SSL certificate and manage an expiring certificate.
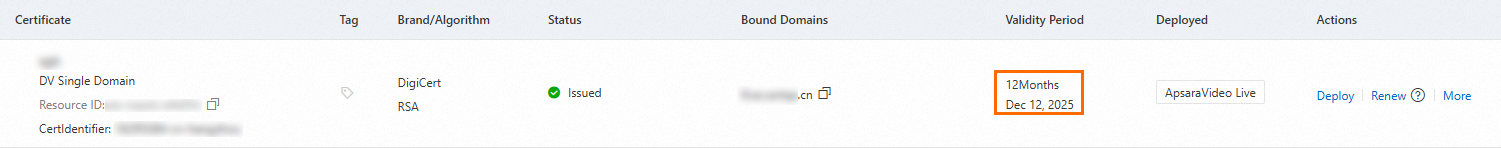
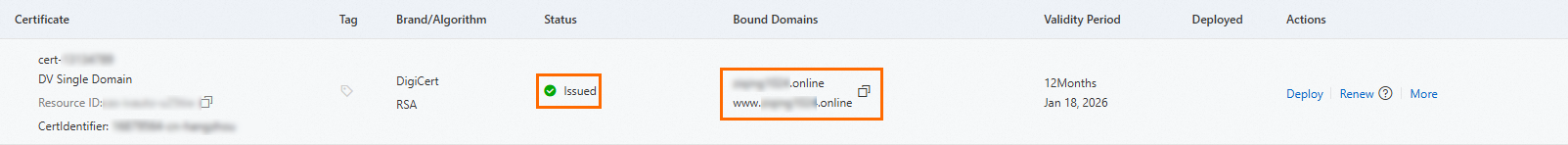
Verify that the Status of the certificate is Issued and that the Bound Domains are correct.
Ensure that the certificate is installed correctly. This includes placing the certificate file in the correct certificate folder and configuring the certificate section of the web server's configuration file, such as for Nginx or Apache, to apply the certificate.
If you use a self-signed certificate, confirm that your browser trusts it.
The following steps use Chrome as an example to show you how to confirm whether a browser trusts the certificate.
Open the website that uses the self-signed certificate in your browser.
Click the
 icon in the address bar. If the browser trusts the certificate, no warning icon appears to the left of the address bar. If it does not trust the certificate, a red
icon in the address bar. If the browser trusts the certificate, no warning icon appears to the left of the address bar. If it does not trust the certificate, a red  warning icon appears, as shown in the following figure.
warning icon appears, as shown in the following figure.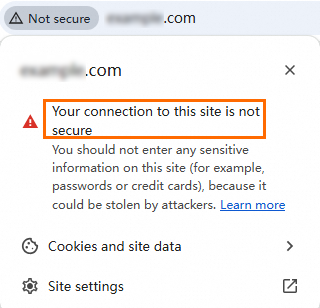
View the certificate details. If the browser does not trust the certificate, the certificate information window displays related warnings.
If you use a non-self-signed certificate, ensure that it is issued by a trusted certification authority (CA). Otherwise, the browser might block the connection because it does not trust the certificate.
The following steps use Chrome as an example to show you how to confirm whether a non-self-signed certificate is issued by a trusted CA.
View the certificate information:
Click the
 icon to the left of the address bar.
icon to the left of the address bar.Click Connection is secure to display the connection details.
Click Certificate is valid or a similar option. If the certificate is issued by a trusted CA, the browser shows that the certificate is valid and displays no warnings.

View the issuer information. In the certificate information window that appears, find the Issuer field. Check the common name (CN), organization (O), and other related information to see if it includes the name of a well-known CA.

Verify that the domain name resolves correctly.
Verify that the DNS record points to the correct IP address, especially if you recently changed your host or IP address.
Log on to the Alibaba Cloud DNS console.
On the Authoritative DNS Resolution page, on the Authoritative Domain Names tab, click the target domain name to open the Settings page.

On the Settings page, click the Add Record button. Verify that the Record Value matches your IP address. If it does not match, click the Modify button to correct it.

If you recently changed your domain name resolution settings, there might be a delay before the changes take effect. You can try clearing the local DNS cache and retrying, or wait for the changes to propagate.
The following sections describe how to clear the local DNS cache on different operating systems:
Windows
Open the command prompt. Press
Win + R, entercmd, and then press Enter.In the command prompt, enter the following command and press Enter:
ipconfig /flushdnsThe message "Successfully flushed the DNS Resolver Cache" indicates that the local DNS cache has been cleared.
macOS
Open the Terminal.
Press
Command + Spaceto open Spotlight Search, then enter "Terminal" to find it.In the Terminal, enter the following command to clear the DNS cache in macOS, and then press Enter:
# dscacheutil is a command line interface used to interact with the system's cache service. sudo dscacheutil -flushcacheNext, enter the following command in the Terminal to restart the
mDNSResponderprocess by sending a HUP signal, and then press Enter:# mDNSResponder is the background process responsible for the DNS service. Restarting it ensures the cache is completely purged. sudo killall -HUP mDNSResponderIf no error message appears, the command was executed successfully.
NoteYou may be prompted to enter your administrator password during the process. Enter the password and press Enter.
Linux
On Linux systems, the method for clearing the local DNS cache depends on the DNS caching service that the system uses. The following sections describe how to clear the cache for several common DNS caching services:
systemd-resolvedIf your Linux system uses
systemd-resolvedto manage the DNS cache, you can run the following command to clear the cache:sudo systemd-resolve --flush-cachesnscd(Name Service Cache Daemon)If your Linux system uses
nscdto manage the DNS cache, you can clear the cache by restarting thenscdservice:sudo service nscd restartOr:
sudo systemctl restart nscddnsmasqIf your Linux system uses
dnsmasqto manage the DNS cache, you can clear the cache by restarting thednsmasqservice:sudo service dnsmasq restartOr:
sudo systemctl restart dnsmasqBINDIf your Linux system uses
BIND(Berkeley Internet Name Domain) to manage the DNS cache, you can clear the cache with the following command:sudo rndc flushNetworkManagerSome Linux distributions use
NetworkManagerto manage network settings, including the DNS cache. You can clear the cache by restarting theNetworkManagerservice:sudo service network-manager restartOr:
sudo systemctl restart NetworkManager
NoteChoose the appropriate command based on the DNS caching service that your system uses. Executing these commands typically requires administrative permission, so you may need to add
sudobefore the command. After you clear the DNS cache, the system retrieves the latest domain name resolution information from the DNS server. This can help resolve network access issues.
Clear the browser cache.
The browser might cache old SSL certificate information. Try clearing the browser cache and then re-accessing your website.
Try to access your website in incognito or private mode. The operation for Chrome is shown in the following figure. If you are using Edge, you need to click New InPrivate window.

Verify that the certificate chain is complete.
Ensure that the entire certificate chain is complete, including the intermediate certificate and the root certificate. Browsers must verify the complete certificate chain, from the root certificate to the server certificate. If the chain is incomplete, the browser may not trust the certificate.
NoteA root certificate is the starting point of the certificate trust chain and is used to verify the authenticity of all subordinate certificates issued by that CA. For SSL certificates issued by a trusted CA, their root certificates are pre-installed in major web browsers (such as Google Chrome, Mozilla Firefox, and Microsoft Edge) or operating systems (such as Windows, macOS, Android, and iOS). However, for clients where the root certificate is not pre-installed (such as apps, Java clients, older browsers, and IoT devices), you need to manually download the root certificate that matches your server certificate type and install it on the corresponding client. This ensures that the client can establish a secure HTTPS connection with the server. To manually download a root certificate that matches your SSL certificate type, see Download and install a root certificate.
An intermediate certificate is located between a root certificate and a user entity certificate (such as an SSL certificate) and is issued by a higher-level CA to a lower-level CA. In Alibaba Cloud Certificate Management Service, the downloaded PEM file contains the server certificate and the intermediate certificate. The private key (KEY file) is paired with the server certificate to ensure secure HTTPS communication. Using an intermediate certificate helps reduce the risk of a root certificate directly signing an SSL certificate. If a root certificate needs to be revoked, all directly signed certificates will lose trust. Signing a user's SSL certificate with the private key of an intermediate certificate can effectively reduce this risk. To download an intermediate certificate, see Download an SSL certificate.
A missing certificate chain is a common cause of SSL certificate validation failures. Most desktop browsers can retrieve the intermediate certificate using the Authority Information Access (AIA) URL. However, some mobile browsers, especially on Android, do not support this feature. This can cause the certificate to be marked as untrusted. To resolve this, you must merge the server certificate and the full certificate chain into a single file and then deploy it on your server. When a browser connects, the server sends the complete chain, which allows the browser to trust the certificate. The SSL certificate chain structure is as follows:
-----BEGIN CERTIFICATE----- Website certificate -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- CA intermediate certificate authority -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- CA root certificate authority -----END CERTIFICATE-----NoteThe SSL certificate chain structure generally consists of Website certificate > CA intermediate certificate authority > CA root certificate authority. The intermediate certificate may also have a multilayer structure.
How to view the SSL certificate chain
This section uses the Chrome browser as an example.
In the browser address bar, click the
 icon and in the information card that appears, click Connection is secure.
icon and in the information card that appears, click Connection is secure.In the Connection is secure window that appears, click Certificate is valid.
Click Details and view the Certification Path to see the SSL certificate chain. The following figure shows an example.

How to complete the SSL certificate chain
If the certificate was requested through Alibaba Cloud, you can directly re-download the certificate file, which already contains the complete certificate chain.
On Windows, manually open the certificate, find the intermediate certificate, and export it in Base64 format. Then, copy the exported content into the original certificate.
Confirm that the private key is correct.
Ensure that the certificate and private key uploaded to the web server match and are in the correct format.
A private key is created when you generate a Certificate Signing Request (CSR). This private key must be paired with the corresponding certificate. The following steps show you how to verify that the private key matches the certificate on a Linux system:
Log on to the ECS server backend and use the following command to go to the certificate installation folder:
# / is the root folder. The ssl path is an example. Use the actual installation path of your certificate. cd /sslUse the following command to view the public key information of the certificate and obtain its MD5 hash:
# Replace your_certificate.pem with the PEM file in your ECS server's certificate folder. sudo openssl x509 -in your_certificate.pem -noout -pubkey | openssl md5Use the following command to view the public key information in the private key file and obtain its MD5 hash:
# Replace your_private_key.key with the private key file in your ECS server's certificate folder. sudo openssl rsa -in your_private_key.key -pubout | openssl md5Compare the MD5 hashes from the two commands. If they are the same, the private key matches the certificate.

If the private key is lost or corrupted, you must generate a new private key and request a new certificate.
Check browser compatibility.
Ensure that your certificate format and cipher suites are compatible with major browsers.
Ensuring that the certificate format and cipher suites on your server are compatible with major browsers is an important step in securing your website. The following are some methods to ensure compatibility:
Use a trusted certification authority (CA)
Choose a trusted CA to issue your SSL/TLS certificate. Major browsers automatically trust certificates issued by these CAs.
Use the correct certificate format
Ensure your certificate is in X.509 format, which is the standard format for SSL/TLS certificates.
To check if your certificate is in X.509 format, you can inspect the content and format of the certificate file using the following method.
Use the
opensslcommand line interface to view the certificate content# Replace /ssl/cert.pem with the actual installation path of your certificate file. sudo openssl x509 -in /ssl/cert.pem -text -nooutIf the certificate is in X.509 format, this command will output detailed information about the certificate, including the version, serial number, signature algorithm, issuer, validity period, and public key information.
Example output:
Certificate: Data: Version: 3 (0x2) Serial Number: 01:23:45:67:89:ab:cd:ef:01:23:45:67:89:ab:cd:ef Signature Algorithm: sha256WithRSAEncryption Issuer: C = US, O = DigiCert Inc Validity Not Before: Jan 17 00:00:00 2025 GMT Not After : Jan 17 23:59:59 2026 GMT Subject: CN = example.com Subject Public Key Info: Public Key Algorithm: rsaEncryption RSA Public-Key: (2048 bit) ......If this command runs successfully and displays detailed information about the certificate, your certificate is in X.509 format.
Use PEM format (usually
.crtor.pemfiles) to save the certificate and intermediate certificate chain.
Use modern cipher suites
Configure the server to use modern cipher suites, such as TLS 1.2 or TLS 1.3. These versions provide better security and compatibility.
Disable insecure protocols and encryption algorithms, such as SSL 2.0, SSL 3.0, TLS 1.0, TLS 1.1, RC4, and 3DES.
Test the connection on different browsers and devices.
Ensure the folder containing the certificate files has the correct read permissions.
Ensure that the web server has read permissions for the folder that contains the certificate files.
The following steps show you how to confirm that the folder for certificate files has the appropriate read permissions in Linux.
Use the
ls -ldcommand to view the folder permissions.# Replace the example path /ssl with the actual installation path of your certificate files. sudo ls -ld /sslThis will output information similar to the following:
 Note
NoteThe meaning of the permission field (such as
drwxr-xr-x):The first character
dindicates that this is a folder.The next three characters
rwxrepresent the owner's permissions: read (r), write (w), and execute (x).The middle three characters
r-xrepresent the permissions for users in the same group: read (r) and execute (x).The last three characters
r-xrepresent the permissions for other users: read (r) and execute (x).
Confirm that the permissions are appropriate.
Read permission: Ensure the relevant user or service has read (r) permission for the folder.
Execute permission: For a folder, execute (x) permission allows a user to enter the folder, that is, to use the
cdcommand to switch to that folder.
(Optional) Modify the permissions.
To change the permissions, you can use the
chmodcommand to do so:# Replace the example path /ssl with the actual installation path of your certificate files. sudo chmod 750 /sslNoteThe
750permission means:The owner has read, write, and execute permissions.
Users in the same group have read and execute permissions.
Other users have no permissions.
By following these steps, you can confirm and adjust the read permissions of a folder on your Linux server to ensure security and functionality.
Implementation logic can vary by website. Review the log files of your web server and applications for any SSL-related error messages to find specific clues about the issue. If the issue persists, contact your account manager for assistance.