Secure HTTPS and QUIC traffic by attaching SSL/TLS certificates to your Application Load Balancer (ALB) listeners. ALB supports one-way authentication and mutual TLS (mTLS) for client verification.
How it works
Authentication modes
Type | What it does | Required certificates | Use case |
One-way | Client verifies server identity | Server certificate | Web apps, APIs |
Mutual (mTLS) | Client and server verify each other | Server certificate + CA certificate | Finance, IoT, internal services |
One-way authentication handshake | Mutual authentication handshake |
 |  |
Supported configurations
Listener | Certificate type | One-way | Mutual |
HTTPS | RSA or ECC (single) | ✓ | ✓ |
RSA + ECC (dual) | ✓ | ✓ | |
QUIC | RSA or ECC (single) | ✓ | ✗ |
RSA + ECC (dual) | ✓ | ✗ | |
HTTP | — | ✗ | ✗ |
Note: Mutual authentication requires Standard or WAF-enabled edition. Basic Edition instances and QUIC listeners do not support mTLS.
Prerequisites
Prepare the required certificates based on your authentication mode:
Certificate type | Purpose | How to obtain |
Server certificate | Proves server identity to clients | |
CA certificate | Validates client certificates (mTLS only) |
Configure a certificate for one-way authentication
Console
When creating an HTTPS or QUIC listener, select your Server Certificate in the Configure SSL Certificate step. For HTTPS listeners, also choose a TLS Security Policy.
API
Call CreateListener with the following parameters:
ListenerProtocol:HTTPSorQUICCertificates.0.CertificateId: Server certificate IDSecurityPolicyId: TLS security policy ID (HTTPS only)
Configure a certificate for mutual authentication
Console
When creating an HTTPS listener, select your Server Certificate, toggle Enable Mutual Authentication on, and specify the CA certificate. Also choose a TLS Security Policy.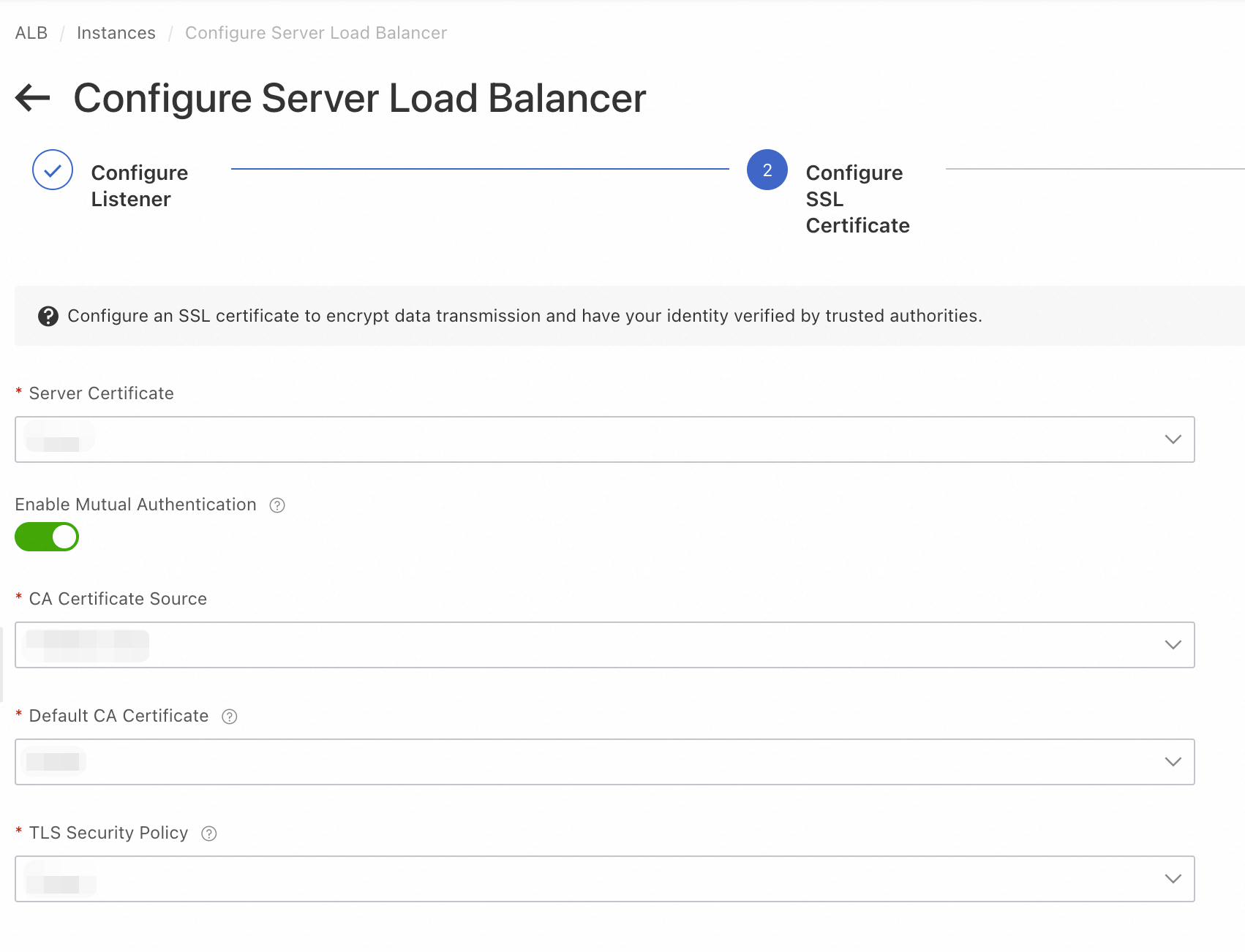
For a step-by-step tutorial, see Configure mutual authentication on an HTTPS listener.
API
Call CreateListener with the following parameters:
ListenerProtocol:HTTPSSecurityPolicyId: TLS security policy IDCaEnabled:trueCertificates.0.CertificateId: Server certificate IDCaCertificates.0.CertificateId: CA certificate ID
Switch between authentication modes
For an existing HTTPS listener, you can enable or disable mutual authentication at any time.
Console
In the ALB console, click your instance ID and go to the Listener tab.
Find the target listener and click Manage Certificates in the Actions column.
On the CA Certificates tab, toggle Mutual Authentication on or off. If enabling, select a CA certificate.
API
Call UpdateListenerAttribute. Set CaEnabled to true or false, and specify CaCertificates.0.CertificateId when enabling.
Manage server certificates
Replace the default server certificate
The server certificate selected when creating a listener becomes its default certificate. Replace it before expiration or when business needs change.
Important: During replacement, new connections may be interrupted. Existing connections are not affected. Perform this operation during off-peak hours.
Console
In the ALB console, click your instance ID and go to the Listener tab.
Find the target listener and click Manage Certificates in the Actions column.
On the Server Certificates tab, click Replace next to the default certificate, select a new one, and click OK.
API
Call UpdateListenerAttribute with ListenerId and Certificates.0.CertificateId.
Add additional certificates for multi-domain support
If a listener serves multiple domains with different certificates, add additional certificates. ALB automatically matches certificates based on the requested domain name (SNI).
If a request matches an additional certificate's domain, that certificate is used.
If no match is found, the default certificate is used.
Console
In the ALB console, click your instance ID and go to the Listener tab.
Find the target listener and click Manage Certificates in the Actions column.
On the Server Certificates tab, Click Add EV Certificate, select the certificates for your domains, and click OK.
API
Call AssociateAdditionalCertificatesWithListener with ListenerId and Certificates.N.CertificateId.
Replace CA certificates
Console
In the ALB console, click your instance ID and go to the Listener tab.
Find the target listener and click Manage Certificates in the Actions column.
On the CA Certificates tab, Click Replace next to the current CA certificate, select a new one, and click OK.
API
Call UpdateListenerAttribute with ListenerId and CaCertificates.0.CertificateId.
Quotas
Quota name | Description | Default value | Maximum value | Adjustable |
alb_quota_loadbalancer_certificates_num_basic_edition | Maximum number of additional certificates that can be added to an ALB instance (excluding default certificates) | 10 | 150 | |
alb_quota_loadbalancer_certificates_num_standard_edition | 25 | 300 | ||
alb_quota_loadbalancer_certificates_num_standardwithwaf_edition |
Billing
Configuring certificates on a listener does not incur additional charges. However, you are billed for the certificates themselves. For more information, see Billing of SSL certificates and Billing for PCA.
Best practices for production
Certificate management
Centralized management: Use Certificate Management Service to view, renew, and deploy all certificates in one place.
Modern TLS policies: For public-facing applications, use
tls_cipher_policy_1_2or higher unless you have specific compatibility requirements.Automation: Use APIs or Terraform with Certificate Management Service to automate certificate renewal and deployment.
Risk prevention
End-to-end encryption: For sensitive services, enable end-to-end HTTPS to encrypt traffic from clients to ALB and from ALB to backend servers.
Proactive monitoring: Configure alert rules in CloudMonitor for certificate expiration. Set alerts for 30, 7, and 1 day before expiration.
Change management: Perform certificate replacements and TLS policy changes during off-peak hours. If issues occur, roll back immediately by updating the listener configuration.