Security Center provides integrated security for your containers. It detects and defends against vulnerabilities, configuration risks, attacks, and intrusions in real time. After you connect your container assets to Security Center, you can manage them from a centralized location. This topic describes how to view the security risks of your container assets.
Edition requirements
Subscription service: Ultimate (If your current version is unsupported, you must upgrade).
NoteThe server's protection edition must be set to Ultimate. For more information, see Attach a protection edition to a server.
Pay-as-you-go service: The pay-as-you-go service is enabled for Host and Container Security. If not, see Purchase.
NoteYou must set the server protection level to Host and Container Protection. For more information, see Attach a server protection level.
Prerequisites
Connect your container assets to Security Center. For more information, see Add image repositories and Connect a self-managed K8s cluster.
To view alerts for container cluster anomalies, you must enable K8s threat detection. For more information, see K8s threat detection for containers.
Synchronize latest assets
Before you view container asset information, you must synchronize the latest asset data. This ensures that newly added container assets are displayed in the asset list.
Log on to the Security Center console.
In the navigation pane on the left, choose . In the upper-left corner of the console, select the region where your assets are located: Chinese Mainland or Outside Chinese Mainland.
On the Container page, on the Cluster or Image tab, click Synchronize Assets.
(Optional) In the upper-right corner of the Container page, click Task Management. In the Task Management panel, on the Container Asset Synchronization and Synchronize Image Asset tabs, you can view the progress, status, and details of the asset synchronization.
Cluster management
Supported cluster types
Managed and dedicated clusters that are created in Alibaba Cloud Container Service for Kubernetes (ACK).
Every morning, Security Center automatically performs a full synchronization of assets of this type in your Alibaba Cloud account. This eliminates the need to add assets manually. If you create new clusters, you can manually sync the latest asset information on the Cluster tab.
View cluster information
Log on to the Security Center console.
In the navigation pane on the left, choose . In the upper-left corner of the console, select the region where your assets are located: Chinese Mainland or Outside Chinese Mainland.
On the Container page, on the Cluster tab, you can view the number of connected clusters, the number of at-risk clusters, and a list of connected clusters.
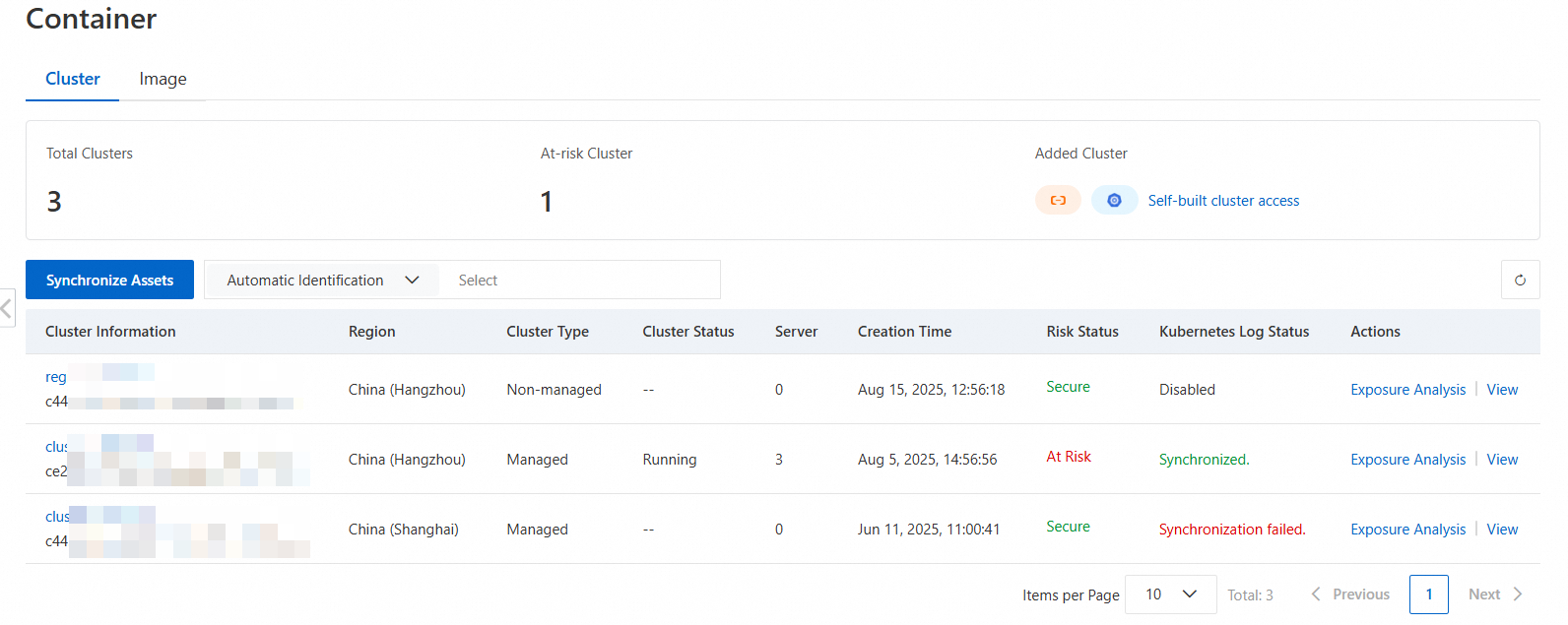
Search for a target cluster
You can use the search component above the cluster list to search for a cluster by its ID, type, or other information.
View risk details of a target cluster
Click the name of the target cluster or View in the Actions column to open its risk details page. On this page, you can view statistics and lists of security alerts, vulnerabilities, configuration risks (K8s configuration risks and baseline risks), and container firewall alerts.

Enable K8s log threat detection
After you enable K8s log threat detection for a cluster, Security Center can retrieve the cluster's log data to provide more comprehensive security risk detection, such as identifying high-risk operations and attack behaviors.
ACK managed and dedicated clusters
In the Container Service console, enable the log audit feature. For more information, see Use the cluster API server audit feature.
Log on to the Container Service Management console. In the navigation pane on the left, choose Clusters.
On the Clusters page, click the name of the target cluster. In the navigation pane on the left, choose .
Follow the on-screen instructions to select an SLS project and enable the feature.
In the Security Center console, enable K8s threat detection for containers.

Self-managed K8s clusters
For more information, see Enable log threat detection.
After this feature is enabled, go to the Container page in the Security Center console. On the Clusters tab, you can check the K8s Log Status column for the target cluster to verify that K8s log threat detection is enabled.
Cluster exposure analysis
Exposing a container port to the internet can expose your business to security risks, such as network attacks and data breaches. To prevent these risks, Security Center provides a port exposure analysis feature for container clusters that detects public port information.
Currently, the exposure analysis feature supports only ACK managed and dedicated clusters.
Perform an exposure analysis.
You can perform an exposure analysis on a cluster automatically or manually:
Automatic exposure analysis: After you connect a K8s cluster, Security Center automatically performs a full synchronization of cluster information and runs an exposure analysis on all connected clusters early every morning.
Manual exposure analysis: On the Cluster tab of the Container page, click Exposure Analysis in the Actions column for the target cluster.
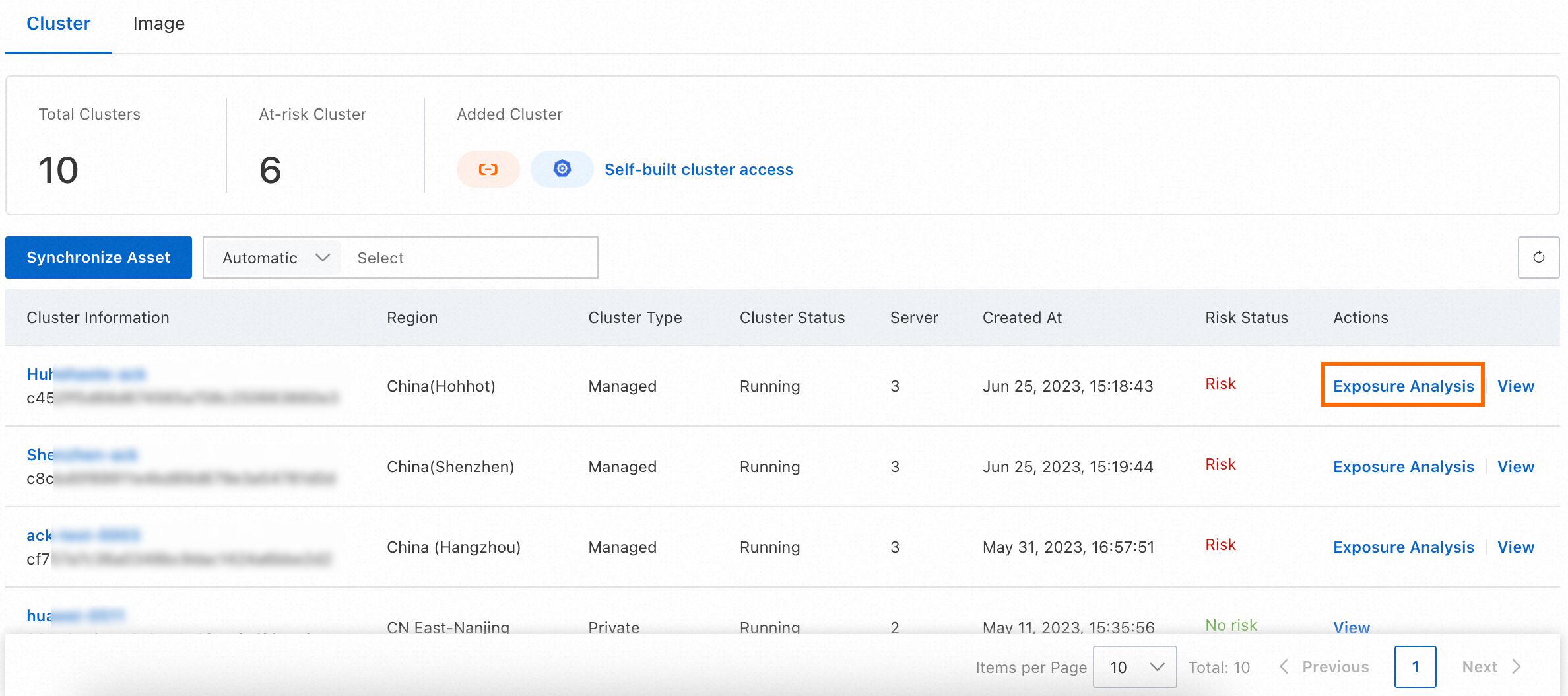
(Optional) In the upper-right corner of the Container page, click Task Management. On the Container Exposure tab of the Task Management panel, you can view the progress and details of the cluster exposure analysis task.
View the results of the cluster exposure analysis.
On the Container page, click the name of the target cluster.
On the cluster details page, click the Container tab and set the Exposed filter to Yes.
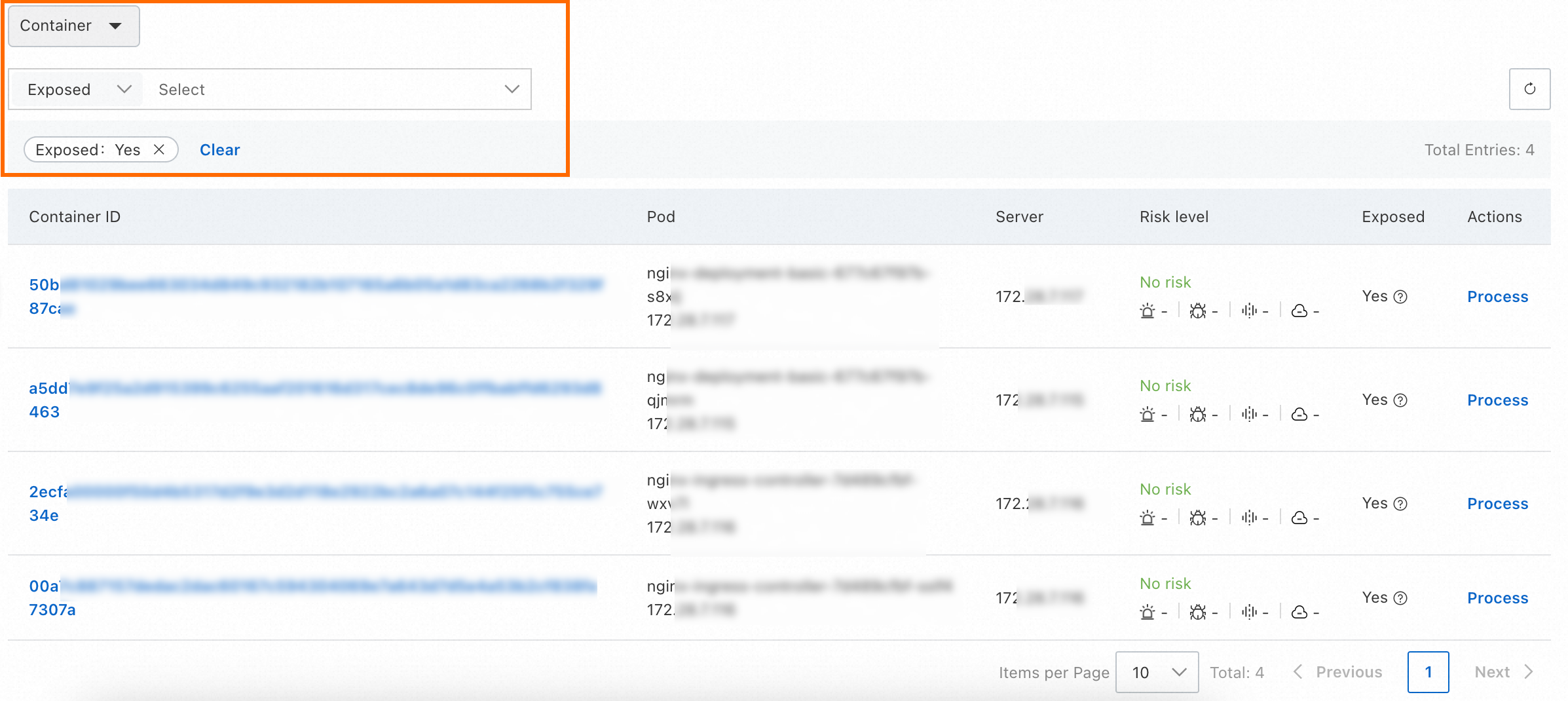
Move the pointer over the
 icon in the Exposed column to view the exposed port information of the container.
icon in the Exposed column to view the exposed port information of the container.If a port is exposed to the internet but is not in use, close it promptly to reduce security risks.
Image management
View image information
Log on to the Security Center console.
In the navigation pane on the left, choose . In the upper-left corner of the console, select the region where your assets are located: Chinese Mainland or Outside Chinese Mainland.
On the Image tab of the Container page, you can view the image information.

View overview information
The Overview section displays information such as the number of at-risk images and the Remaining Quota for image security scans.
In the Remaining Quota section, click Increase Quota to increase your container image security scan quota. For more information, see Upgrade and downgrade.
You can click Add in the Add Third-party Image Repository section to register private image repositories. For more information, see Add an image repository.
View the list of image repositories
The image repository list displays all repositories that are connected to Asset Center. You can view the repository name, region, type, and risk status.
Search for a target image repository
You can use the search component above the list to search for an image repository by its instance ID, namespace, or other information.
View a target image repository
Click the name of the target image repository or click View in the Actions column. On the repository's details page, you can view information for each image, including its name, version, size, and risk status. The Created At/Updated At column shows the time of the first and most recent syncs by Security Center, not the local creation and update times of the image repository.
On the image repository details page, find the target image repository version and click Handle in the Actions column to view or export its threat and vulnerability information.
View image repositories of Platform for AI (PAI)
You can view a list of image repositories for PAI by selecting from the search filter.
Synchronize ACR assets
Click Synchronize in the Actions column of an image repository to enable automatic synchronization of assets from a Container Registry Enterprise Edition instance. Once enabled, assets added to the instance are automatically synchronized to the image list in Security Center.
Scan container images
The image scan feature in Security Center detects image vulnerabilities, baseline risks, malicious samples, and sensitive files to help you ensure a secure image runtime environment.
Log on to the Security Center console.
In the navigation pane on the left, choose . In the upper-left corner of the console, select the region where your assets are located: Chinese Mainland or Outside Chinese Mainland.
On the Image tab of the Container page, click Scan Now in the Container Image Scan section.

In the Quick Scan dialog box, select an image type, configure the scan scope as required, and then click OK.
For more information about how to configure the scan scope, see Perform image security scans.
(Optional) In the upper-right corner of the Container page, click Task Management. In the Task Management panel, on the Image Scan, Image Risk Fixing, and Container Runtime Image Scan tabs, you can view information about image scans and repairs.
References
The Container Asset Overview feature provides security visualization and management capabilities for your assets, such as clusters, containers, images, and applications. It also displays the network topology of your container assets in the cloud. This feature helps you efficiently manage the security of your container assets. For more information, see Container Asset Overview.
Security Center provides container security capabilities, such as K8s threat detection for containers and container escape prevention. You can enable these features to protect your container runtime environment. For more information, see Container protection settings.
Container signing lets you sign container images to ensure that only trusted images are deployed. This feature prevents unauthorized images from being launched and improves your asset security. For more information, see Container signing.
Security Center detects system vulnerabilities, application vulnerabilities, baseline risks, and malicious samples in your image assets, and then categorizes and displays the results. You can view the details of the security risks and fix them. For more information, see View and fix detected image risks.
The security monitoring feature of Security Center provides monitoring and alerting capabilities. It detects major attack behaviors on containers, such as malicious image startups, viruses and malware, intrusions into containers, container escapes, and high-risk operations. For more information, see Use security monitoring.