To ensure the security and stability of your Tair (Redis OSS-compatible) instance, access from all IP addresses to Tair (and Redis Open-Source Edition) instances is denied by default. Before you can use a Tair (or Redis Open-Source Edition) instance, you must add the IP address or IP address range of the client to the instance's whitelist. A properly configured whitelist enhances the security of your instance. We recommend that you perform regular maintenance on your whitelists.
Whitelist configuration methods
Method | Description | Scenarios |
Add a whitelist | Manually add the IP address of a client to the instance's whitelist to grant access to the client. | |
Add a security group | A security group is a virtual firewall that controls the inbound and outbound traffic of ECS instances in the security group. To grant access to multiple ECS instances, you can bind their security group to the Tair instance. After the security group is bound, all ECS instances in the group can access the Tair instance without you having to manually enter their IP addresses. | Add the private and public IP addresses of multiple ECS instances using a security group |
You can configure whitelist groups and ECS security groups at the same time. In this case, the IP addresses in the whitelist groups and the ECS instances in the security groups can access the instance.
Add the private IP address of an ECS instance to a whitelist
If your ECS instance and Tair instance are in the same virtual private cloud (VPC), you can use the VPC for access.
If your ECS instance and Tair instance are not in the same VPC, you can change the VPC of the ECS instance. For more information, see Change the VPC of an ECS instance.
Log on to the console and go to the Instances page. In the top navigation bar, select the region in which the instance that you want to manage resides. Then, find the instance and click the instance ID.
In the left-side navigation pane, click Whitelist Settings.
Find the default whitelist and click Modify in the Actions column.
NoteYou can also click Add Whitelist to create a whitelist. The name of a whitelist must be 2 to 32 characters in length and can contain lowercase letters, digits, and underscores (_). It must start with a lowercase letter and end with a lowercase letter or digit.
Set Add Method to Import ECS Internal IP Address. The private IP addresses of the ECS instances that are in the same region as the Tair instance are displayed.
You can hover your mouse pointer over an IP address to view the ID and name of the ECS instance to which the IP address belongs.
Select the required IP addresses and move them to the right pane.
Click OK.
Optional: To remove all IP addresses from a whitelist group, click Delete on the right of the target whitelist group.
System-generated whitelist groups, such as default and hdm_security_ips, cannot be deleted.
Add a public IP address to a whitelist
If you want to remotely access an instance from an on-premises device, or if your ECS instance and Tair instance are not in the same VPC, you can follow these steps to add a public IP address to a whitelist.
Log on to the console and go to the Instances page. In the top navigation bar, select the region in which the instance that you want to manage resides. Then, find the instance and click the instance ID.
In the navigation pane on the left, click Whitelist Settings.
In the default security group, click Modify.
NoteYou can also click Add Whitelist to create a new group. The group name must be 2 to 32 characters in length and can contain lowercase letters, digits, and underscores (_). It must start with a lowercase letter and end with a lowercase letter or a digit.
Set Add Method to Add Manually.
In the Whitelist text box, enter an IP address or a CIDR block.
Separate multiple IP addresses with commas (,). The IP addresses cannot be the same. You can add up to 1,000 IP addresses. The following formats are supported:
A specific IP address, such as 10.23.12.24.
Classless Inter-Domain Routing (CIDR) block. For example, /24 indicates that the prefix is 24 bits in length. The prefix can be 1 to 32 bits in length. 10.23.12.0/24 indicates the IP address range from 10.23.12.0 to 10.23.12.255.
WarningAdding 0.0.0.0/0 to the whitelist allows access from all IP addresses. This poses high security risks. Configure this setting with caution.
Click OK.
Optional: To remove all IP addresses from a whitelist group, click Delete on the right of the target whitelist group.
System-generated whitelist groups, such as default and hdm_security_ips, cannot be deleted.
Add the private and public IP addresses of ECS instances in batches using a security group
If multiple ECS instances need to access a Tair instance, you can add a security group to the Tair whitelist. After you add the security group, the Tair instance allows all associated instances in the security group, such as ECS instances and Elastic Container Instances, to access it using their private and public IP addresses.
The IP access control takes effect only for instances, such as ECS instances, that are associated with the security group. It is not related to the custom CIDR blocks or IP addresses that are configured in the security group.
The Tair instance must be compatible with Redis 4.0 (latest minor version) or later. For more information about how to upgrade the major version, see Major version upgrade.
Log on to the console and go to the Instances page. In the top navigation bar, select the region in which the instance that you want to manage resides. Then, find the instance and click the instance ID.
In the navigation pane on the left, click Whitelist Settings.
Click the Security Groups tab.
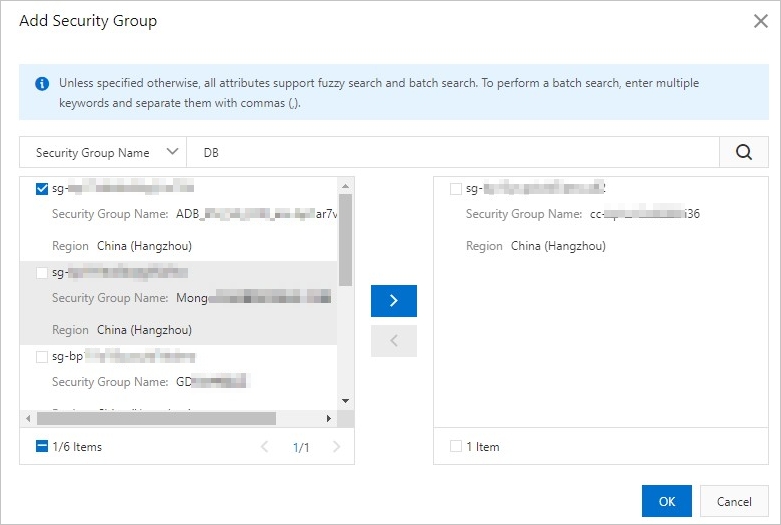
On the Security Groups tab, click Add Security Group.
In the dialog box that appears, select the security group that you want to add.
You can perform a fuzzy search by Security Group Name or Security Group ID.
Figure 3. Add a security group
 Note
NoteYou can add up to 10 security groups for each instance.
Click OK.
Optional: To remove all security groups, click Delete.
Related API operations
API operation | Description |
Queries the IP address whitelist of an instance. | |
Configures the IP address whitelist of an instance. | |
Queries the security groups that are configured in the whitelist of an instance. | |
Resets the security groups in the whitelist of an instance. |