This topic describes how to enable the backup encryption feature for an ApsaraDB RDS for MySQL instance. The backup files are encrypted by using the Percona XtraBackup utility. This utility eliminates the need to modify your application. If you want to use an encrypted backup file, you must download the backup file. Then, you can decrypt the backup file at decompression.
Prerequisites
Your RDS instance meets the following requirements:
The RDS instance runs MySQL 8.0, MySQL 5.7, or MySQL5.6.
The RDS instance runs RDS High-availability Edition.
The RDS instance uses Premium Local SSDs.
Key Management Service (KMS) is activated. For more information, see Purchase a dedicated KMS instance.
Background information
The key that is used for the backup encryption is created and managed by KMS. ApsaraDB RDS does not provide the key or certificates that are required for the backup encryption. You can use an automatically generated key or a custom key.
If you want to use a custom key, you must first create a service-linked role. ApsaraDB RDS uses the service-linked role to obtain keys and the attributes and aliases of the keys from KMS. Then, ApsaraDB RDS can display the keys in the ApsaraDB RDS console. After backup files are encrypted by using a custom key, ApsaraDB RDS can also display the related encryption information. For more information, see Service-linked roles.
When you enable the backup encryption feature, ApsaraDB RDS marks the key that you select. Then, ApsaraDB RDS uses the key to encrypt backup files based on the service-linked role.
Usage notes
After the backup encryption feature is enabled, it cannot be disabled.
After the backup encryption feature is enabled, the key cannot be changed.
After the backup encryption feature is enabled, only new backup files are encrypted. Existing backup files are not encrypted.
After the backup encryption feature is enabled, if you want to restore the data of your RDS instance to an on-premises database, you must decrypt the backup file of the RDS instance after you download the backup file. For more information, see Decrypt backup files.
NoteIf you directly restore the data of your RDS instance from a backup file by using the ApsaraDB RDS console, you do not need to decrypt the backup file. Before the backend performs the restoration, it automatically decrypts the backup file. For more information, see Restore full data.
If you use an existing custom key for the backup encryption, take note of the following items:
If you disable the key, configure a plan to delete the key, or delete the key material, the key becomes unavailable. In this case, if an O&M operation requires a backup file that is encrypted by using the unavailable key, the O&M operation fails. This may decrease the availability of your instance. If you restore data from a backup file that is encrypted by using the unavailable key, the data restoration also fails.
You must use your Alibaba Cloud account or a RAM user that has the following permissions:
{ "Version": "1", "Statement": [ { "Action": [ "ram:CreateServiceLinkedRole" ], "Resource": "*", "Effect": "Allow", "Condition": { "StringEquals": { "ram:ServiceName": "backupencryption.rds.aliyuncs.com" } } }, { "Action": [ "kms:ListResourceTags", "kms:TagResource" ], "Effect": "Allow", "Resource": [ "acs:kms:*:*:*" ] } ] }NoteYou can configure the permissions and grant the permissions to a RAM user by using the RAM console. For more information, see Authorize a RAM user to manage ApsaraDB RDS instances.
Enable the backup encryption feature
Go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance.
In the left-side navigation pane, click Backup and Restoration.
On the Backup and Restoration page, click the Backup Strategy tab.
Click Edit in the Backup Encryption Settings section to turn on Backup Encryption Status.
In the Backup Set Encryption Information dialog box, select a value for the Backup Master Key parameter and click OK.
Use Automatically Generated Key
If you select this option, Alibaba Cloud generates a key that can be used to encrypt backup files.
Use Existing Custom Key
If you select this option, the key that is created by using KMS is used. If the key does not exist, you can create a key by using KMS. For more information, see Create a CMK.
NoteIf this is the first time that you use KMS to create a custom key, you must follow the prompted instructions to obtain authorization.
After the backup encryption feature is enabled, the backup files of your RDS instance are encrypted. If you use these backup files on Alibaba Cloud, you do not need to manually decrypt these backup files. Before the backend performs operations such as data restoration, it automatically decrypts these backup files. If you download these backup files to your computer, you must manually decrypt these backup files. For more information about how to decrypt these backup files, see Decrypt backup files.
Decrypt backup files
This section uses Ubuntu 16.04 as an example to show how to decrypt backup files.
Prerequisites
Percona XtraBackup is installed. If you do not install Percona XtraBackup, install Percona XtraBackup by following the instructions described in Installing Percona XtraBackup 2.4 or Install Percona XtraBackup 8.0 overview.
The qpress decompression tool is installed. If you do not install the tool, run the following commands:
wget "http://docs-aliyun.cn-hangzhou.oss.aliyun-inc.com/assets/attach/183466/cn_zh/1608011575185/qpress-11-linux-x64.tar" tar xvf qpress-11-linux-x64.tar chmod 775 qpress cp qpress /usr/binPython 3 is installed.
Procedure
Obtain the ciphertext and the algorithm that is used to encrypt the backup files.
Go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance.
In the left-side navigation pane of the page that appears, click Backup and Restoration.
On the page that appears, click the Base Backups tab and then the Data Backup tab.
Click the
 icon in the Actions column of the backup set and click View Encryption Information to obtain the ciphertext and encryption algorithm.
icon in the Actions column of the backup set and click View Encryption Information to obtain the ciphertext and encryption algorithm.
Call the Decrypt operation and set the CiphertextBlob parameter to the ciphertext obtained in Step 1 to obtain the value of the Plaintext parameter. The value is a Base64-encoded binary string.
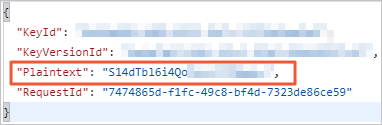
Decode the value of the Plaintext parameter by using Base64 and convert each binary value in the binary string into a hexadecimal value. Then, you can obtain the password. This section uses Python 3 code to implement this operation.
Open the vi editor by running the
vi decrypt.pycommand in the CLI.Press the
ikey on the keyboard to enable the editing mode, enter the following content, press theESCkey, and then enter:wqto save the changes and disable the editing mode.import base64 import binascii plaintext = 'S14dTbl6i4Qo**********' # Enter the value of the Plaintext parameter that is obtained in the previous step in single quotation marks (''). password = binascii.b2a_hex(base64.b64decode(plaintext)) # Obtain the password for the decryption and set the password parameter to the obtained value. print(str(password, 'utf-8')) # Print the password as a string on the screen.Run the
python decrypt.pycommand in the CLI, and the password for the decryption is printed on the screen. Example:4b5e1d4db97a********************
Download the encrypted backup data and decrypt the data.
Download the backup data to your computer. For more information, see Restore the data of an ApsaraDB RDS for MySQL instance from a physical backup file to a self-managed MySQL database.
Run the following command in the CLI to create a directory, such as
/home/mysql/data, to store backup data:mkdir /home/mysql/dataDecompress the physical backup package. The command that is used to decompress the physical backup package varies based on the extension of the package name.
Backup file type
Command used for decompression
.tar.gz
tar -izxvf test1.tar.gz -C /home/mysql/data.xb.gz
gzip -d -c test1.xb.gz | xbstream -x -v -C /home/mysql/data_qp.xb
## Decompress the physical backup file. cat test1_qp.xb | xbstream -x -v -C /home/mysql/data ## Decompress the physical backup file. ### If the RDS instance runs MySQL 5.6 or MySQL 5.7, run the following command: innobackupex --decompress --remove-original /home/mysql/data ### If the RDS instance runs MySQL 8.0, run the following command: xtrabackup --decompress --remove-original --target-dir=/home/mysql/data_xb.qp
qpress -do test1_xb.qp | xbstream -x -v -C /home/mysql/dataAfter the decompression, all data is suffixed with
.xbcrypt. The suffix indicates that the data is encrypted.
Run the following command to decrypt data:
xtrabackup --decompress --remove-original --decrypt=AES256 --encrypt-key=4b5e1d4db97a******************** --target-dir=/home/mysql/dataNoteThe following lists describe the crucial parameters in the preceding command:
After you run the preceding command, the
.xbcryptsuffix of the backup file disappears and the backup file is decrypted.