Access credential leaks cause severe security risks to your resources and services that are deployed on the cloud. This topic describes how to use an access credential to call API operations of Alibaba Cloud in a secure way in various scenarios.
What is an access credential?
An access credential is a set of information that is used for identity authentication. When you use a development tool such as an API, CLI, SDK, or Terraform to access Alibaba Cloud, you must provide a valid access credential to pass identity authentication. The following list describes common types of access credentials:
AccessKey pair: Each AccessKey pair consists of an AccessKey ID and an AccessKey secret. An AccessKey pair is a permanent access credential that Alibaba Cloud provides for Alibaba Cloud accounts and Resource Access Management (RAM) users. For more information, see Create an AccessKey pair.
Security Token Service (STS) token: An STS token is a temporary access credential that Alibaba Cloud provides for a RAM role. You can configure a custom validity period and access permissions for an STS token. For more information, see What is STS?
Common access credential leaks
Developers hardcode an AccessKey pair in business code. Developers who have the permissions to read the code repository can obtain the AccessKey pair. Some developers even upload the business code to open source communities or code hosting services. This causes even greater security risks.
Some developers include an AccessKey pair in the client code to allow the client to directly call API operations. Attackers can decompile the client code and obtain the AccessKey pair information.
The technical documentation or materials that are shared with others contain AccessKey pair information.
The sample code in product documentation contains AccessKey pair information.
The responses of API operations on which developers do not have management permissions contain AccessKey pair information.
Secure methods to use access credentials
Secure methods to use an access credential mainly focus on reducing the exposure time and scope of access credentials. The following table lists the secure methods to use access credentials in common scenarios.
Method | Scenario |
Assume a RAM role by using an application that is deployed in an ACK cluster | If your applications are deployed in a Container Service for Kubernetes (ACK) cluster, you can enable the RAM Roles for Service Accounts (RRSA) feature for the ACK cluster. This way, each application that is deployed in the ACK cluster can assume a different RAM role to call API operations of Alibaba Cloud. |
If your application is deployed on an Elastic Compute Service (ECS) instance, you can attach an instance RAM role that has specific permissions to the ECS instance. This way, the application that is deployed on the ECS instance can call API operations of Alibaba Cloud. | |
If the R&D, O&M, and product personnel of an enterprise want to use an AccessKey pair for O&M, management, and debugging, we recommend that you implement role-based single sign on (SSO). This way, users of your enterprise can assume a corresponding RAM role and obtain the STS token to perform the required operations. | |
If your application deployed on Function Compute needs to access other Alibaba Cloud resources, you can associate functions with Function Compute RAM roles. This way, your application can use STS tokens to access cloud resources. This prevents security risks that may be caused by permanent access credentials. | |
If the preceding solutions are not applicable, we recommend that you configure system environment variables to call API operations of Alibaba Cloud. |
Assume a RAM role by using an application that is deployed in an ACK cluster
Prerequisites
An Alibaba Cloud service that works with RAM is used. For more information, see Services that work with RAM.
The RRSA feature supports only ACK clusters that run Kubernetes 1.22 and later. ACK clusters that support the RRSA feature include ACK Basic clusters, ACK Pro clusters, ACK Serverless Basic clusters, ACK Serverless Pro clusters, and ACK Edge Pro clusters.
Alibaba Cloud SDK V2.0 is installed.
The self-developed SDKs of services that use self-managed gateways are not installed.
Working principles
You can use the RRSA feature to allow different applications in an ACK cluster to assume different RAM roles. Applications can obtain STS tokens, use the tokens to assume specific RAM roles, and then access relevant cloud services. This enforces the principle of least privilege and allows applications to call API operations without the need to use AccessKey pairs, which prevents AccessKey pair leaks.
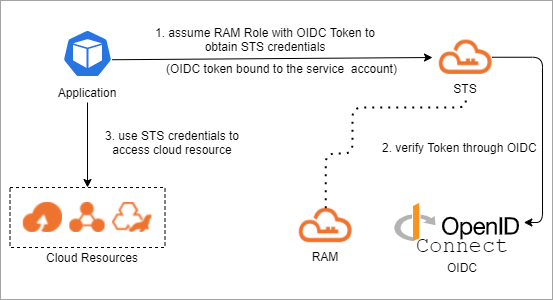
The following steps show how an application accesses a cloud resource when RRSA is used to enforce access control:
The tenant deploys a pod for which the feature of service account token volume projection is enabled.
The ACK cluster creates a service account OpenID Connect (OIDC) token file and mounts the token file to the pod.
The application in the pod uses the OIDC token file to call the AssumeRoleWithOIDC API operation of STS and obtain the STS token that is used to assume a RAM role.
NoteTo enable the application to perform these operations, you must first create an OIDC identity provider and allow the service account used by the pod to assume the specified RAM role. For more information, see AssumeRoleWithOIDC.
The OIDC token in the OIDC token file is a temporary token. We recommend that you configure the application to read the latest token from the OIDC token file. The cluster renews the token in the OIDC token file before the token expires.
The application in the pod uses the STS token to assume the specified RAM role and then calls the API of the relevant cloud service.
Configuration methods
Enable the RRSA feature for an ACK cluster. For more information, see Enable RRSA.
Use the RRSA feature in an ACK cluster. For more information, see Work with RRSA.
Sample code
Alibaba Cloud SDK V2.0 supports OIDC token authentication of RRSA. By default, all cloud service SDKs that support STS token authentication and are developed based on Alibaba Cloud SDK V2.0 support RRSA OIDC token authentication. The following table describes the supported SDK versions and demos.
Programming language | Supported SDK version | Demo |
Go | Alibaba Cloud Credentials for Go 1.2.6 and later. For more information, see Method 6: Use the RAM role of an OIDC IdP. | |
Java | Alibaba Cloud Credentials for Java 0.2.10 and later. For more information, see Method 6: Use the RAM role of an OIDC IdP. | |
Python 3 | Alibaba Cloud Credentials for Python 0.3.1 and later. For more information, see Method 6: Use the RAM role of an OIDC IdP. | |
Node.js and TypeScript | Alibaba Cloud Credentials for TypeScript/Node.js 2.2.6 and later. For more information, see Method 6: Use the RAM role of an OIDC IdP. |
Assume an instance RAM role in ECS
Prerequisites
An Alibaba Cloud service that works with RAM is used. For more information, see Services that work with RAM.
Alibaba Cloud SDK V2.0 is installed.
The self-developed SDKs of services that use self-managed gateways are not installed.
Working principles
You can attach an instance Resource Access Management (RAM) role to an Elastic Compute Service (ECS) instance. Then, the ECS instance can use the Security Token Service (STS) temporary credential of the instance RAM role to access the APIs of other Alibaba Cloud services. The STS temporary credential is updated on a periodic basis. This ensures the security of your AccessKey pair and implements fine-grained access control and permissions management by using RAM.
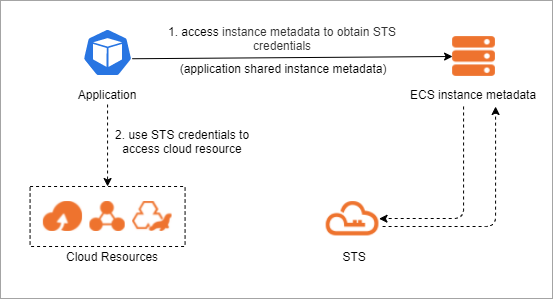
The following list describes the process:
An application accesses ECS instance metadata to obtain an STS token. For more information, see Overview of ECS instance metadata.
The application uses the STS token to access cloud resources. For more information, see What is STS?
Configuration method
Attach an instance RAM role to an ECS instance. For more information, see Instance RAM roles.
Sample code
Alibaba Cloud Credentials is a credential management tool provided by Alibaba Cloud for developers. You can use Alibaba Cloud Credentials to attach an instance RAM role to an ECS instance in a convenient manner. The following sample code provides an example on how to call the DescribeRegions operation of ECS.
Programming language | References |
Go | |
Java | |
Python | |
PHP | |
Node.js | |
.NET |
Use an STS token for development and debugging
Scenario
If the R&D, O&M, and product personnel of an enterprise want to use an AccessKey pair for O&M, management, and debugging, we recommend that you implement role-based SSO. This way, users of your enterprise can assume a corresponding RAM role and obtain the STS token to perform the required operations.
Configuration methods
If a single Alibaba Cloud account is used, we recommend that you assign RAM roles to users by job responsibility. For more information, see Overview. The users can use the CLI tool saml2alibabacloud to obtain the STS token after authentication on the identity provider (IdP) side. For more information, see saml2alibabacloud.
If multiple Alibaba Cloud accounts are used, we recommend that you use CloudSSO to configure SSO for the accounts. For more information, see Configure SSO. After the configuration is complete, users can use CLI to log on to CloudSSO and access Alibaba Cloud resources. For more information, see Use Alibaba Cloud CLI to access CloudSSO and Alibaba Cloud resources.
Use an STS token in Function Compute
Scenario
If your application deployed on Function Compute needs to access other Alibaba Cloud resources and you hardcode the AccessKey pair of a RAM user in related functions, AccessKey pair leaks may occur, and O&M is difficult. In this case, you can attach RAM roles to the functions. This way, the application can use STS tokens to access cloud resources, and security risks from permanent access credentials are prevented.
Solution architecture
In the solution, function RAM roles in Function Compute are used to obtain and use temporary access credentials. The solution allows you to dynamically manage and temporarily grant access permissions. This prevents risks that are caused by long-term AccessKey pair exposure, and makes the system more secure and flexible. The administrator only needs to configure roles for functions and grant permissions to the roles one time. In subsequent operations, functions can dynamically obtain and use temporary access credentials in runtime. This simplifies O&M management.
The administrator creates a RAM role whose trusted entity is Function Compute and grants permissions to the RAM role. The permissions include the permissions that are required to access a specific cloud resource of a cloud service. Then, the administrator associates the created RAM role with a function in Function Compute. When your application attempts to obtain the temporary access credential from the function context, Function Compute calls the AssumeRole operation as a trusted Alibaba Cloud service to obtain the STS token from RAM or STS. Then, your application can use the obtained STS token to call an API operation of the cloud service. After the cloud service processes the request and returns the result, your application receives the result and performs subsequent operations.
Configuration method
For more information, see Grant Function Compute permissions to access other Alibaba Cloud services.
Configure system environment variables
Configuration method
Configure the ALIBABA_CLOUD_ACCESS_KEY_ID and ALIBABA_CLOUD_ACCESS_KEY_SECRET environment variables.
Linux and macOS
Run the following commands:
export ALIBABA_CLOUD_ACCESS_KEY_ID=<access_key_id> export ALIBABA_CLOUD_ACCESS_KEY_SECRET=<access_key_secret>Replace
<access_key_id>with your AccessKey ID and<access_key_secret>with your AccessKey secret.Windows
Create an environment variable file, add the
ALIBABA_CLOUD_ACCESS_KEY_IDandALIBABA_CLOUD_ACCESS_KEY_SECRETenvironment variables to the file, and then specify your AccessKey ID for ALIBABA_CLOUD_ACCESS_KEY_ID and your AccessKey secret for ALIBABA_CLOUD_ACCESS_KEY_SECRET.Restart the Windows operating system.
Sample code of Alibaba Cloud SDKs
Alibaba Cloud SDKs allow you to configure the ALIBABA_CLOUD_ACCESS_KEY_ID and ALIBABA_CLOUD_ACCESS_KEY_SECRET environment variables to create a default access credential. When you call an API operation, the system reads the AccessKey pair from the default access credential and uses the AccessKey pair to complete authentication. The following sample code provides an example on how to call the DescribeRegions operation of ECS.
Programming language | References |
Go | |
Java | |
Python | |
PHP | |
Node.js | |
.NET |
Common sample code
For self-developed SDKs of services that use self-managed gateways, the following sample code provides an example on how to load environment variables by using Java:
import com.aliyun.credentials.Client;
import com.aliyun.credentials.models.Config;
public class DemoTest {
public static void main(String[] args) throws Exception{
Config config = new Config();
// Which type of credential you want
config.setType("access_key");
// AccessKeyId of your ram user
config.setAccessKeyId(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_ID"));
// AccessKeySecret of your ram user
config.setAccessKeySecret(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_SECRET"));
Client client = new Client(config);
}
}Solutions to access credential leaks
AccessKey pair leak: For more information, see Solutions to AccessKey pair leaks.
STS token leak: For more information, see What do I do if STS tokens are disclosed?
References
For more information about best practices for cloud security, see the following topics: