When you use Alibaba Cloud SDKs, credential information, such as AccessKey pairs and Security Token Service (STS) tokens, is managed by the Credentials tool. This topic describes the credential types that the Credentials tool supports and how to configure them.
Prerequisites
The Credentials tool requires Java 8 or later. For more information, see Alibaba Cloud SDK Support Policy.
To use Alibaba Cloud SDK V2.0, see V2.0 SDK and V1.0 SDK.
Install the Credentials tool
Use the latest version of the Credentials dependency package to ensure that all features are supported.
<dependency>
<groupId>com.aliyun</groupId>
<artifactId>credentials-java</artifactId>
<version>latest-version</version>
</dependency>
<!-- If you use credentials-java alone, you must add the tea package. -->
<dependency>
<groupId>com.aliyun</groupId>
<artifactId>tea</artifactId>
<version>latest-version</version>
</dependency>For information about the latest version of the Credentials package, see GitHub or Maven Repository. For information about the latest version of the Tea package, see GitHub or Maven Repository.
Credential types supported by the Credentials tool and their configuration parameters
The credential types supported by the Credentials tool and their configuration parameters are defined in the com.aliyun.credentials.models.Config class. The credential type is specified by the type parameter, and the required configuration parameters differ for each credential type. The following table describes the valid values of the type parameter and the configuration parameters supported by each credential type. In the table, indicates a required parameter, - indicates an optional parameter, and indicates an unsupported parameter.
We recommend that you do not use credential types or parameters that are not listed in the following table.
type | |||||||
accessKeyId: The AccessKey ID. | |||||||
accessKeySecret: The AccessKey secret. | |||||||
securityToken: The STS token. | - | ||||||
roleArn: The Alibaba Cloud Resource Name (ARN) of the RAM role. | |||||||
roleSessionName: A custom session name. The default format is | - | - | |||||
roleName: The name of the RAM role. | - | ||||||
disableIMDSv1: Specifies whether to enforce the security hardening mode (IMDSv2). The default value is | - | ||||||
bearerToken: The bearer token. | |||||||
policy: A custom policy. | - | - | |||||
roleSessionExpiration: The validity period of the session. Default value: 3600. Unit: seconds. The minimum value is 900 seconds. The maximum value is the maximum session duration that is supported by the RAM role. | - | - | |||||
oidcProviderArn: The ARN of the OIDC IdP. | |||||||
oidcTokenFilePath: The path of the OIDC token file. | |||||||
externalId: the external ID of the role, which is used to prevent the confused deputy issue. For more information, see Use external IDs to prevent the confused deputy issue. | - | ||||||
credentialsURI: The URI of the external credential. | |||||||
STSEndpoint: The service endpoint for Security Token Service (STS), which supports VPC service endpoints and Internet service endpoints. For a list of valid values, see Endpoints. The default value is | - | - | |||||
timeout: The read timeout period for requests. Default value: 5000 milliseconds. | - | - | - | - | |||
connectTimeout: The connection timeout period for requests. Default value: 10000 milliseconds. | - | - | - | - |
Use the Credentials tool
The following sections provide code examples to demonstrate how to use the Credentials tool. You can select a method based on your requirements.
We recommend that you save the AccessKey pair in environment variables or configuration files.
We recommend that you use the singleton pattern when you use the Credentials tool. This practice enables the built-in credential caching feature. This prevents throttling issues caused by multiple API calls and avoids resource waste from creating multiple instances. For more information, see Auto-refresh mechanism for session credentials.
Method 1: Default credential provider chain
This is the default method used in the sample code on the OpenAPI Portal.
If you use the Credentials tool without passing any configuration parameters, the tool obtains credentials from the default credential provider chain and uses them as access credentials. When you use this method, you must ensure that a credential acquisition method supported by the default credential provider chain is configured in the application runtime environment.
import com.aliyun.credentials.Client;
import com.aliyun.credentials.models.CredentialModel;
public class DemoTest {
public static void main(String[] args) throws Exception {
// Do not specify configuration parameters. Credentials will be obtained from the default credential provider chain.
Client credentialClient = new Client();
CredentialModel credential = credentialClient.getCredential();
String accessKeyId = credential.getAccessKeyId();
String accessKeySecret = credential.getAccessKeySecret();
String securityToken = credential.getSecurityToken();
// If you use a V2.0 SDK of an Alibaba Cloud service, use com.aliyun.teaopenapi.models.Config to pass the credential.
com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config();
config.setCredential(credentialClient);
config.setEndpoint("<Endpoint>");
// The code for initializing the cloud service client using config is omitted.
}
}Method 2: AccessKey pair
The Credentials tool uses your AccessKey as access credentials.
An Alibaba Cloud account has full permissions on all resources. If the AccessKey pair of an Alibaba Cloud account is leaked, it poses a significant security threat to your system. We do not recommend using the AccessKey pair of an Alibaba Cloud account.
We recommend that you use the AccessKey pair of a RAM user that is granted the minimum required permissions.
import com.aliyun.credentials.Client;
import com.aliyun.credentials.models.Config;
import com.aliyun.credentials.models.CredentialModel;
public class DemoTest {
public static void main(String[] args) throws Exception {
Config credentialConfig = new Config();
credentialConfig.setType("access_key");
// Required. This example shows how to obtain the AccessKey ID from an environment variable.
credentialConfig.setAccessKeyId(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_ID"));
// Required. This example shows how to obtain the AccessKey secret from an environment variable.
credentialConfig.setAccessKeySecret(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_SECRET"));
Client credentialClient = new Client(credentialConfig);
CredentialModel credential = credentialClient.getCredential();
String accessKeyId = credential.getAccessKeyId();
String accessKeySecret = credential.getAccessKeySecret();
String securityToken = credential.getSecurityToken();
// If you use a V2.0 SDK of an Alibaba Cloud service, use com.aliyun.teaopenapi.models.Config to pass the credential.
com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config();
config.setCredential(credentialClient);
config.setEndpoint("<Endpoint>");
// The code for initializing the cloud service client using config is omitted.
}
}Method 3: STS token
The Credentials tool uses the static STS token that you provide as access credentials.
import com.aliyun.credentials.Client;
import com.aliyun.credentials.models.Config;
import com.aliyun.credentials.models.CredentialModel;
public class DemoTest {
public static void main(String[] args) {
Config credentialConfig = new Config();
credentialConfig.setType("sts");
// Required. This example shows how to obtain the AccessKey ID from an environment variable.
credentialConfig.setAccessKeyId(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_ID"));
// Required. This example shows how to obtain the AccessKey secret from an environment variable.
credentialConfig.setAccessKeySecret(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_SECRET"));
// Required. This example shows how to obtain the temporary security token from an environment variable.
credentialConfig.setSecurityToken(System.getenv("ALIBABA_CLOUD_SECURITY_TOKEN"));
Client credentialClient = new Client(credentialConfig);
CredentialModel credential = credentialClient.getCredential();
String accessKeyId = credential.getAccessKeyId();
String accessKeySecret = credential.getAccessKeySecret();
String securityToken = credential.getSecurityToken();
// If you use a V2.0 SDK of an Alibaba Cloud service, use com.aliyun.teaopenapi.models.Config to pass the credential.
com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config();
config.setCredential(credentialClient);
config.setEndpoint("<Endpoint>");
// The code for initializing the cloud service client using config is omitted.
}
}Method 4: AccessKey pair and RamRoleArn
The Credentials tool uses the AccessKey pair and RAM role ARN that you provide to call the AssumeRole operation to obtain an STS token. This token is then used as the access credential. Credentials obtained this way support auto-refresh. For more information, see Auto-refresh mechanism for session credentials.
import com.aliyun.credentials.Client;
import com.aliyun.credentials.models.Config;
import com.aliyun.credentials.models.CredentialModel;
public class DemoTest {
public static void main(String[] args) throws Exception {
Config credentialConfig = new Config();
credentialConfig.setType("ram_role_arn");
// Required. This example shows how to obtain the AccessKey ID from an environment variable.
credentialConfig.setAccessKeyId(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_ID"));
// Required. This example shows how to obtain the AccessKey secret from an environment variable.
credentialConfig.setAccessKeySecret(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_SECRET"));
// Optional. You can use a temporary credential to assume another RAM role.
credentialConfig.setSecurityToken(System.getenv("ALIBABA_CLOUD_SECURITY_TOKEN"));
// Required. The ARN of the RAM role to assume. Example: acs:ram::123456789012****:role/adminrole. You can set this parameter using the ALIBABA_CLOUD_ROLE_ARN environment variable.
credentialConfig.setRoleArn("<RoleArn>");
// Optional. The name of the role session. The default format is credentials-java-current timestamp. You can set this parameter using the ALIBABA_CLOUD_ROLE_SESSION_NAME environment variable.
credentialConfig.setRoleSessionName("<RoleSessionName>");
// Optional. Specify a more restrictive policy. Example: {"Statement": [{"Action": ["*"],"Effect": "Allow","Resource": ["*"]}],"Version":"1"}.
credentialConfig.setPolicy("<Policy>");
// Optional. The external ID of the role. This parameter is used to prevent the confused deputy problem.
credentialConfig.setExternalId("<ExternalId>");
// Optional. The validity period of the session. Default value: 3600 seconds.
credentialConfig.setRoleSessionExpiration(3600);
Client credentialClient = new Client(credentialConfig);
CredentialModel credential = credentialClient.getCredential();
String accessKeyId = credential.getAccessKeyId();
String accessKeySecret = credential.getAccessKeySecret();
String securityToken = credential.getSecurityToken();
// If you use a V2.0 SDK of an Alibaba Cloud service, use com.aliyun.teaopenapi.models.Config to pass the credential.
com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config();
config.setCredential(credentialClient);
config.setEndpoint("<Endpoint>");
// The code for initializing the cloud service client using config is omitted.
}
}Method 5: Instance RAM role
If your application runs on an ECS or ECI instance that is granted a RAM role, the Credentials tool can obtain the STS token for the RAM role from the instance metadata and use it as an access credential. When accessing the instance metadata, the application first retrieves the name of the RAM role that is granted to the current instance and then obtains the corresponding STS token based on that role. You can specify the RAM role name using the roleName parameter or the ALIBABA_CLOUD_ECS_METADATA environment variable to reduce the time required to obtain credentials and improve efficiency. Credentials obtained this way support auto-refresh. For more information, see Auto-refresh mechanism for session credentials.
By default, the Credentials tool uses the security-hardened mode (IMDSv2) to access instance metadata. If an exception occurs in security-hardened mode, you can use the disableIMDSv1 parameter or the ALIBABA_CLOUD_IMDSV1_DISABLED environment variable to control the exception handling logic:
If the value is
false(default), the system attempts to switch to NAT mode to continue obtaining credentials.If the value is
true, only the security-hardened mode can be used to obtain credentials. An exception is thrown if access in this mode fails.
Whether the server supports IMDSv2 depends on your server configuration.
In addition, you can disable credential access from instance metadata by setting the ALIBABA_CLOUD_ECS_METADATA_DISABLED=true environment variable.
For more information about instance metadata, see Instance metadata.
For more information about how to grant a RAM role to an ECS or ECI instance, see Create a RAM role and grant it to an ECS instance and Grant an instance RAM role to an ECI instance.
To obtain temporary credentials in security-hardened mode, you must use credentials-java 0.3.10 or later.
import com.aliyun.credentials.Client;
import com.aliyun.credentials.models.Config;
import com.aliyun.credentials.models.CredentialModel;
public class DemoTest {
public static void main(String[] args) throws Exception {
Config credentialConfig = new Config();
credentialConfig.setType("ecs_ram_role");
// Optional. The name of the RAM role granted to the ECS instance. If you do not set this parameter, the name is automatically obtained. We recommend that you set this parameter to reduce the number of requests. You can set this parameter using the ALIBABA_CLOUD_ECS_METADATA environment variable.
credentialConfig.setRoleName("<RoleName>");
// Optional. A value of true indicates that security-hardened mode is forcibly used. Default value: false. The system first attempts to obtain credentials in security-hardened mode. If the attempt fails, the system switches to normal mode.
credentialConfig.setDisableIMDSv1(false);
Client credentialClient = new Client(credentialConfig);
CredentialModel credential = credentialClient.getCredential();
String accessKeyId = credential.getAccessKeyId();
String accessKeySecret = credential.getAccessKeySecret();
String securityToken = credential.getSecurityToken();
// If you use a V2.0 SDK of an Alibaba Cloud service, use com.aliyun.teaopenapi.models.Config to pass the credential.
com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config();
config.setCredential(credentialClient);
config.setEndpoint("<Endpoint>");
// The code for initializing the cloud service client using config is omitted.
}
}Method 6: OIDCRoleArn
If you use the OIDC authentication protocol and have created a RAM role for an OIDC IdP, you can pass the OIDC IdP ARN, OIDC token, and RAM role ARN to the Credentials tool. The system then automatically calls the AssumeRoleWithOIDC operation to obtain the STS token for the RAM role and uses this token as the access credential. Credentials obtained this way support auto-refresh. For more information, see Auto-refresh mechanism for session credentials. For example, if your application runs in an ACK cluster where the RRSA feature is enabled, the Credentials tool reads the OIDC configuration information from the pod environment variables, calls the AssumeRoleWithOIDC operation to obtain the STS token for the service role, and uses this token to access related Alibaba Cloud services.
import com.aliyun.credentials.Client;
import com.aliyun.credentials.models.Config;
import com.aliyun.credentials.models.CredentialModel;
public class DemoTest {
public static void main(String[] args) throws Exception {
Config credentialConfig = new Config();
credentialConfig.setType("oidc_role_arn");
// Required. The ARN of the RAM role. You can set this parameter using the ALIBABA_CLOUD_ROLE_ARN environment variable.
credentialConfig.setRoleArn("<RoleArn>");
// Required. The ARN of the OIDC IdP. You can set this parameter using the ALIBABA_CLOUD_OIDC_PROVIDER_ARN environment variable.
credentialConfig.setOidcProviderArn("<OidcProviderArn>");
// Required. The path of the OIDC token file. You can set this parameter using the ALIBABA_CLOUD_OIDC_TOKEN_FILE environment variable.
credentialConfig.setOidcTokenFilePath("<OidcTokenFilePath>");
// Optional. The name of the role session. You can set this parameter using the ALIBABA_CLOUD_ROLE_SESSION_NAME environment variable.
credentialConfig.setRoleSessionName("<RoleSessionName>");
// Optional. Specify a more restrictive policy. Example: {"Statement": [{"Action": ["*"],"Effect": "Allow","Resource": ["*"]}],"Version":"1"}
credentialConfig.setPolicy("<Policy>");
// Optional. The validity period of the session. Default value: 3600 seconds.
credentialConfig.setRoleSessionExpiration(3600);
Client credentialClient = new Client(credentialConfig);
CredentialModel credential = credentialClient.getCredential();
String accessKeyId = credential.getAccessKeyId();
String accessKeySecret = credential.getAccessKeySecret();
String securityToken = credential.getSecurityToken();
// If you use a V2.0 SDK of an Alibaba Cloud service, use com.aliyun.teaopenapi.models.Config to pass the credential.
com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config();
config.setCredential(credentialClient);
config.setEndpoint("<Endpoint>");
// The code for initializing the cloud service client using config is omitted.
}
}Method 7: URI credential
By encapsulating the STS service and exposing its URI, external services can obtain an STS token through the URI. This reduces the risk of exposing sensitive information, such as AccessKey pairs. The Credentials tool obtains an STS token by accessing the URI that you provide and uses this token as an access credential. Credentials obtained this way support auto-refresh. For more information, see Auto-refresh mechanism for session credentials.
The URI must meet the following conditions:
It must support GET requests.
The response status code must be 2xx.
The response body must have the following structure:
{ "Code": "Success", "AccessKeySecret": "yourAccessKeySecret", "AccessKeyId": "STS.****************", "Expiration": "2021-09-26T03:46:38Z", "SecurityToken": "yourSecurityToken" }
import com.aliyun.credentials.Client;
import com.aliyun.credentials.models.Config;
import com.aliyun.credentials.models.CredentialModel;
public class DemoTest {
public static void main(String[] args) throws Exception {
Config credentialConfig = new Config();
credentialConfig.setType("credentials_uri");
// Required. The URI for obtaining external credentials. The format is http://local_or_remote_uri/. You can set this parameter using the ALIBABA_CLOUD_CREDENTIALS_URI environment variable.
credentialConfig.setCredentialsUri("<CredentialsUri>");
Client credentialClient = new Client(credentialConfig);
CredentialModel credential = credentialClient.getCredential();
String accessKeyId = credential.getAccessKeyId();
String accessKeySecret = credential.getAccessKeySecret();
String securityToken = credential.getSecurityToken();
// If you use a V2.0 SDK of an Alibaba Cloud service, use com.aliyun.teaopenapi.models.Config to pass the credential.
com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config();
config.setCredential(credentialClient);
config.setEndpoint("<Endpoint>");
// The code for initializing the cloud service client using config is omitted.
}
}Method 8: Bearer token
Currently, only Cloud Call Center (CCC) supports bearer tokens.
import com.aliyun.credentials.Client;
import com.aliyun.credentials.models.Config;
import com.aliyun.credentials.models.CredentialModel;
public class DemoTest {
public static void main(String[] args) throws Exception {
Config credentialConfig = new Config();
credentialConfig.setType("bearer");
// Required. Enter your bearer token.
credentialConfig.setBearerToken("<BearerToken>");
Client credentialClient = new Client(credentialConfig);
CredentialModel credential = credentialClient.getCredential();
String accessKeyId = credential.getAccessKeyId();
String accessKeySecret = credential.getAccessKeySecret();
String securityToken = credential.getSecurityToken();
// If you use the V2.0 SDK for CCC, use com.aliyun.teaopenapi.models.Config to pass the credential.
com.aliyun.teaopenapi.models.Config config = new com.aliyun.teaopenapi.models.Config();
config.setCredential(credentialClient);
config.setEndpoint("<Endpoint>");
// The code for initializing the cloud service client using config is omitted.
}
}Default credential provider chain
The default credential provider chain is a fallback strategy that searches for credentials in a predefined order. The tool proceeds through the chain until it finds credential information. If credential information cannot be obtained from any provider in the chain, a `CredentialException` is thrown. The search order is as follows:
1. System properties
The Credentials tool first attempts to obtain credential information from system properties.
If `alibabacloud.accessKeyId` and `alibabacloud.accessKeySecret` are defined in the system properties, an AccessKey pair is used as the default credential.
If `alibabacloud.accessKeyId`, `alibabacloud.accessKeySecret`, and `alibabacloud.sessionToken` are defined in the system properties, an STS token is used as the default credential.
You can add the following JVM parameters when you run a Java program to specify these values:
-Dalibabacloud.accessKeyId=your-access-key-id -Dalibabacloud.accessKeySecret=your-access-key-secret
2. Environment variables
If no credential information is found in the system properties, the Credentials tool checks the environment variables.
If the ALIBABA_CLOUD_ACCESS_KEY_ID and ALIBABA_CLOUD_ACCESS_KEY_SECRET environment variables exist and are not empty, an AccessKey pair is used as the default credential.
If the ALIBABA_CLOUD_ACCESS_KEY_ID, ALIBABA_CLOUD_ACCESS_KEY_SECRET, and ALIBABA_CLOUD_SECURITY_TOKEN environment variables are all set, an STS token is used as the default credential.
3. OIDC RAM role
If no credential information is found, the Credentials tool checks the following environment variables related to OIDC RAM roles:
ALIBABA_CLOUD_ROLE_ARN: The ARN of the RAM role.
ALIBABA_CLOUD_OIDC_PROVIDER_ARN: The ARN of the OIDC IdP.
ALIBABA_CLOUD_OIDC_TOKEN_FILE: The path of the OIDC token file.
If the preceding three environment variables exist and are not empty, the Credentials tool uses the values of these environment variables to call the AssumeRoleWithOIDC operation of STS and obtain an STS token as the default credential.
4. The config.json configuration file
This feature requires credentials-java 0.3.8 or later.
If credentials are still not found, the Credentials tool attempts to load the config.json file from the default path and use the specified credential as the default credential. The default file path is:
Linux/macOS:
~/.aliyun/config.jsonWindows:
C:\Users\USER_NAME\.aliyun\config.json
To configure credentials using this method, you can use the Cloud Assistant CLI or manually create a config.json configuration file in the corresponding path. The following code block shows an example of the content format:
{
"current": "<PROFILE_NAME>",
"profiles": [
{
"name": "<PROFILE_NAME>",
"mode": "AK",
"access_key_id": "<ALIBABA_CLOUD_ACCESS_KEY_ID>",
"access_key_secret": "<ALIBABA_CLOUD_ACCESS_KEY_SECRET>"
},
{
"name": "<PROFILE_NAME1>",
"mode": "StsToken",
"access_key_id": "<ALIBABA_CLOUD_ACCESS_KEY_ID>",
"access_key_secret": "<ALIBABA_CLOUD_ACCESS_KEY_SECRET>",
"sts_token": "<SECURITY_TOKEN>"
},
{
"name":"<PROFILE_NAME2>",
"mode":"RamRoleArn",
"access_key_id":"<ALIBABA_CLOUD_ACCESS_KEY_ID>",
"access_key_secret":"<ALIBABA_CLOUD_ACCESS_KEY_SECRET>",
"ram_role_arn":"<ROLE_ARN>",
"ram_session_name":"<ROLE_SESSION_NAME>",
"expired_seconds":3600
},
{
"name":"<PROFILE_NAME3>",
"mode":"EcsRamRole",
"ram_role_name":"<RAM_ROLE_ARN>"
},
{
"name":"<PROFILE_NAME4>",
"mode":"OIDC",
"oidc_provider_arn":"<OIDC_PROVIDER_ARN>",
"oidc_token_file":"<OIDC_TOKEN_FILE>",
"ram_role_arn":"<ROLE_ARN>",
"ram_session_name":"<ROLE_SESSION_NAME>",
"expired_seconds":3600
},
{
"name":"<PROFILE_NAME5>",
"mode":"ChainableRamRoleArn",
"source_profile":"<PROFILE_NAME>",
"ram_role_arn":"<ROLE_ARN>",
"ram_session_name":"<ROLE_SESSION_NAME>",
"expired_seconds":3600
}
]
}
Parameter | Description |
current | Specifies the name of the credential to use, which corresponds to the value of the |
profiles | A collection of credential information. Use the
|
5. Instance RAM role
If no credential information is found, the Credentials tool attempts to obtain the STS token of the RAM role that is granted to the instance from the instance metadata and use it as the default credential. When accessing instance metadata, the program first obtains the name of the RAM role that is attached to the current instance and then obtains the corresponding STS token based on that role. You can also specify the RAM role name using the ALIBABA_CLOUD_ECS_METADATA environment variable to reduce the time required to obtain credentials and improve efficiency.
By default, the Credentials tool accesses metadata in security-hardened mode (IMDSv2). If an exception occurs in security-hardened mode, you can use the ALIBABA_CLOUD_IMDSV1_DISABLED environment variable to control the exception handling logic:
If the value is
false(default), the system attempts to switch to NAT mode to continue obtaining credentials.If the value is
true, only the security-hardened mode is allowed for obtaining credentials. If access in security-hardened mode fails, an exception is thrown.
In addition, you can disable credential access from instance metadata by setting the ALIBABA_CLOUD_ECS_METADATA_DISABLED=true environment variable.
For more information about instance metadata, see Obtain instance metadata.
For more information about how to grant a RAM role to an ECS or ECI instance, see Create a RAM role and attach it to an ECS instance and Attach an instance RAM role to an ECI instance.
To obtain temporary credentials in security-hardened mode, you must use
credentials-java0.3.10 or later.
6. CredentialsURI
If no credential information is found, the Credentials tool checks the ALIBABA_CLOUD_CREDENTIALS_URI environment variable. If this variable exists and points to a valid URI, the Credentials tool accesses this URI to obtain an STS token as the default credential.
Auto-refresh mechanism for session credentials
Session credentials include ram_role_arn, ecs_ram_role, oidc_role_arn, and credentials_uri. This type of credential has a built-in auto-refresh mechanism in the Credentials tool. After a credential client obtains credentials for the first time, the Credentials tool saves the credential information to the cache. In subsequent requests, the same credential client instance automatically fetches the credentials from the cache. If the credentials in the cache are expired, the credential client instance re-obtains the credentials and updates the cache.
For `ecs_ram_role` credentials, the Credentials tool refreshes the cache 15 minutes before the credentials expire.
The following example creates a credential client in a singleton pattern. The client obtains credentials at different time points to verify the auto-refresh mechanism and calls an OpenAPI operation to ensure that the obtained credentials are valid.
import com.aliyun.credentials.models.CredentialModel;
import com.aliyun.ecs20140526.Client;
import com.aliyun.ecs20140526.models.DescribeRegionsRequest;
import com.aliyun.ecs20140526.models.DescribeRegionsResponse;
import com.aliyun.teaopenapi.models.Config;
import com.aliyun.teautil.models.RuntimeOptions;
import java.util.Date;
import java.util.concurrent.*;
public class Sample {
/**
* The Credential class is used to manage Alibaba Cloud credential instances in singleton pattern.
*/
private static class Credential {
private static volatile com.aliyun.credentials.Client instance;
private Credential() {
}
public static com.aliyun.credentials.Client getInstance() {
if (instance == null) {
synchronized (Credential.class) {
if (instance == null) {
try {
com.aliyun.credentials.models.Config config = new com.aliyun.credentials.models.Config();
config.setType("ram_role_arn");
config.setAccessKeyId(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_ID"));
config.setAccessKeySecret(System.getenv("ALIBABA_CLOUD_ACCESS_KEY_SECRET"));
config.setRoleArn(System.getenv("ALIBABA_CLOUD_ROLE_ARN"));
config.setRoleSessionName("RamRoleArnTest");
config.setRoleSessionExpiration(3600);
instance = new com.aliyun.credentials.Client(config);
} catch (Exception e) {
throw new RuntimeException("Credential initialization failed: " + e.getMessage(), e);
}
}
}
}
return instance;
}
}
/**
* The EcsClient class is used to manage the ECS client in singleton pattern.
*/
private static class EcsClient {
private static volatile Client instance;
private EcsClient() {
}
public static Client getInstance(com.aliyun.credentials.Client credentialClient) {
if (instance == null) {
synchronized (EcsClient.class) {
if (instance == null) {
try {
Config ecsConfig = new Config();
ecsConfig.setEndpoint("ecs.cn-hangzhou.aliyuncs.com");
ecsConfig.setCredential(credentialClient);
instance = new Client(ecsConfig);
} catch (Exception e) {
throw new RuntimeException("ECS client initialization failed: " + e.getMessage(), e);
}
}
}
}
return instance;
}
}
public static void main(String[] args) {
// Use ThreadPoolExecutor to create a scheduled thread pool.
ScheduledThreadPoolExecutor scheduler = new ScheduledThreadPoolExecutor(
1,
Executors.defaultThreadFactory(),
new ThreadPoolExecutor.AbortPolicy()
);
scheduler.setKeepAliveTime(0L, TimeUnit.SECONDS);
scheduler.allowCoreThreadTimeOut(false); // Do not allow core threads to time out.
// Define a Runnable task to execute the call logic.
Runnable task = () -> {
try {
com.aliyun.credentials.Client credentialClient = Credential.getInstance();
CredentialModel credential = credentialClient.getCredential();
System.out.println(new Date());
System.out.printf("AK ID:%s, AK Secret:%s, STS Token:%s%n", credential.accessKeyId, credential.accessKeySecret, credential.securityToken);
// This example calls an ECS API operation to verify whether the credential is available. You can modify it as needed.
Client ecsClient = EcsClient.getInstance(credentialClient);
DescribeRegionsRequest request = new DescribeRegionsRequest();
RuntimeOptions runtime = new RuntimeOptions();
DescribeRegionsResponse response = ecsClient.describeRegionsWithOptions(request, runtime);
System.out.printf("Invoke result:%s%n", response.statusCode);
} catch (Exception e) {
throw new RuntimeException("ECS client execution failed: " + e.getMessage(), e);
}
};
try {
// Execute the task for the first time (immediately).
scheduler.execute(task);
// Execute the task for the second time after a delay of 600 seconds.
scheduler.schedule(task, 600, TimeUnit.SECONDS);
// Execute the task for the third time, 4200 seconds after the start.
scheduler.schedule(task, 4200, TimeUnit.SECONDS);
// Execute the task for the fourth time, 4300 seconds after the start.
scheduler.schedule(task, 4300, TimeUnit.SECONDS);
} finally {
// Shut down the thread pool to ensure it is closed after all tasks are complete.
scheduler.shutdown();
try {
if (!scheduler.awaitTermination(4500, TimeUnit.SECONDS)) {
scheduler.shutdownNow();
}
} catch (InterruptedException e) {
scheduler.shutdownNow();
Thread.currentThread().interrupt();
}
}
}
}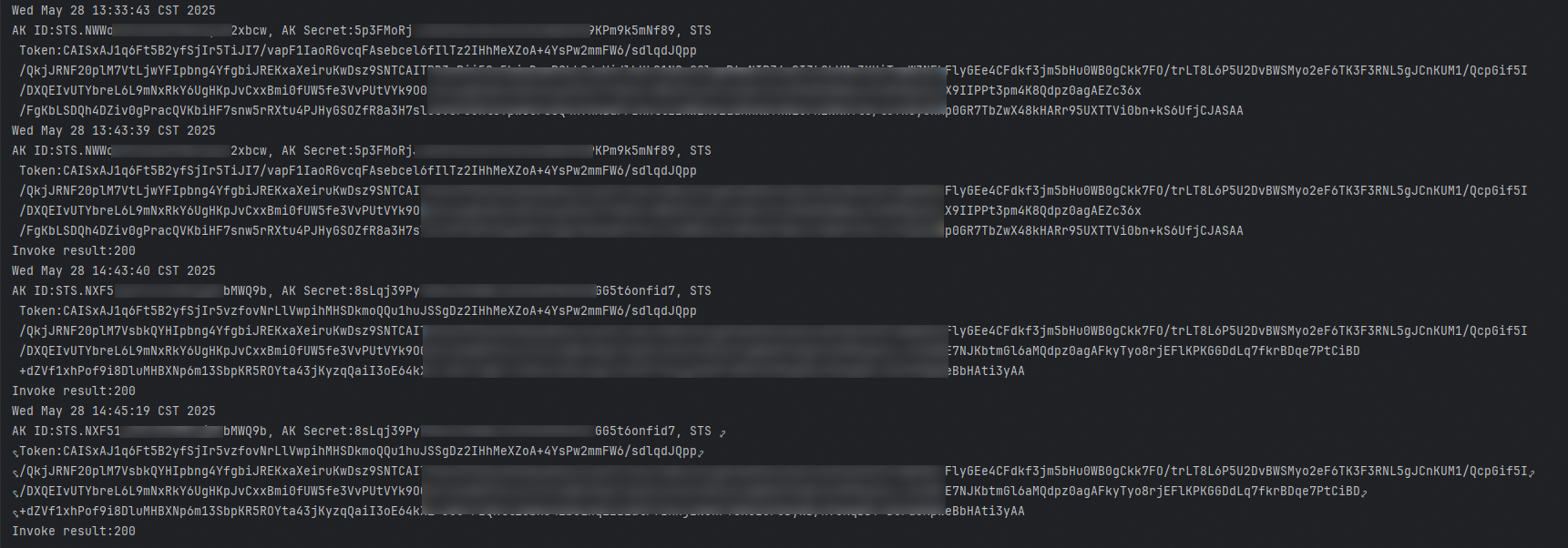
The following section analyzes the log results:
In the first call, no credential information is cached. Therefore, the system obtains the credentials based on the configuration. After the credentials are obtained, they are saved in the cache.
The credentials used in the second call are the same as the first one. This indicates that the credentials for the second call were retrieved from the cache.
In the third call, the credentials in the cache are expired. This is because the validity period of the credentials (`RoleSessionExpiration`) is set to 3,600 seconds, and the third call occurs 4,200 seconds after the first call. Therefore, the SDK re-obtains new credentials based on the auto-refresh mechanism and saves the new credentials to the cache.
The credentials used in the fourth call are the same as the new credentials obtained in the third call. This indicates that the credentials in the cache were updated after they expired.
References
For more information about RAM, see Terms.
For more information about how to create an AccessKey pair, see Create an AccessKey pair.
For more information about how to programmatically create a RAM user, an AccessKey pair, a RAM role, and an access policy and grant permissions, see RAM SDK Overview.
For more information about how to programmatically assume a role, see STS SDK overview.
For more information about RAM- and STS-related API operations, see API Reference.
Best practices for using an access credential to call API operations