Access Analyzer helps you identify and resolve excessive permissions by generating actionable remediation advice. This enables you to enforce the principle of least privilege and strengthen your security posture.
This feature is currently in beta and does not support all services. For a list of supported services, see Services that work with the permission audit feature. Always evaluate advice against your specific business requirements before applying any changes.
Overview
Granting an identity more permissions than it needs, known as over-privileged access, increases security risks such as unintended access, data breaches from compromised credentials, and compliance violations. Manually auditing and right-sizing permissions is often a time-consuming and error-prone process.
Access Analyzer automates this process by continuously analyzing access logs across your account or resource directory. It identifies RAM identities (users and roles) with unused permissions, including those with administrative, privileged, or inactive access. It then generates remediation advice, helping you efficiently right-size permissions and enforce the principle of least privilege. Access Analyzer can also be used to identify external access.Identify external access
Core concepts
Findings
A finding is a record of a potential security risk identified by Access Analyzer. Each finding includes the following key information:
Finding type: The category of the risk, such as:
Super user/role
Privileged user/role
Inactive user/role
Over-privileged user/role
Status: The current state of the finding: Active, Resolved, or Archived.
Resource information: The name, type, and owner of the resource.
Timestamps: When the finding was created, last analyzed, and last updated.
Finding ID: A unique identifier for the finding.
Remediation advice
Based on a finding, Access Analyzer generates advice to help you remediate the risk. Advice types include:
Policy replacement: Replace a broad policy with a more restrictive one. For example, you can replace the
AdministratorAccesspolicy (super administrator permission) with thePowerUserAccesspolicy (system administrator permission).Policy removal: Detach an unused policy from an identity.
Identity deactivation: Disable or delete an inactive identity.
Finding archival: Archive a finding if you determine that the reported permissions are intentional and approved for your use case.
Decision logic
Access Analyzer categorizes findings based on the following logic. If an identity meets the criteria for multiple finding types, it is categorized by the highest-priority type (1 = highest).
Priority | Finding type | Description |
1 | Super user/role | A RAM identity that has been granted full administrative permissions over all resources in the account through the |
2 | Privileged user/role | A RAM identity that has been granted high-risk permissions other than those defined in the |
3 | Inactive user/role | A RAM identity that has not accessed any resources or data within the specified idle period (default: 90 days) and does not meet higher-priority conditions. Note Identities with no policies attached are not flagged as inactive, even if they have never been used. |
4 | Over-privileged user/role | A RAM identity with service-level or action-level permissions that it has not used within the specified idle period and does not meet higher-priority conditions. Note The supported granularity varies for different services. For more information, see the "Supported granularity" paragraph in the "Limitations" section of this topic. |
Quick start: Right-size permissions for an inactive RAM user
This quick start guide walks you through using Access Analyzer to identify and disable an inactive RAM user.
Prerequisites
You have created an analyzer of the Over-privileged Access type in the RAM console.
The current RAM identity has the required permissions to perform remediation. This requires attaching both the
AliyunRAMAccessAnalyzerFullAccessandAliyunRAMFullAccesspolicies.
Procedure
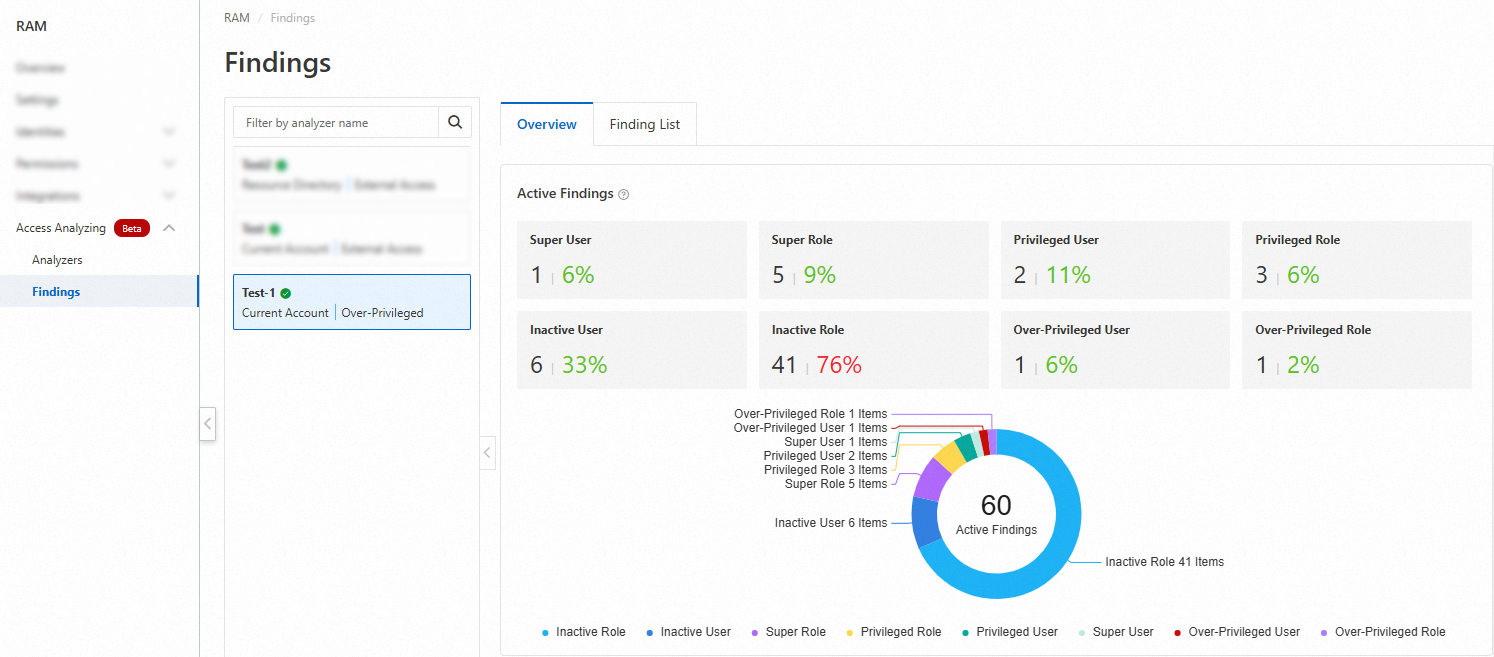
Review findings.
Log on to the RAM console.
In the left-side navigation pane, choose .
In the top navigation bar, select the region where the analyzer is located.
On the Overview tab, click Inactive User.
Apply the advice.
On the Findings page, find the RAM user that you no longer need and click the corresponding Finding ID.
On the details page of the finding, click the Advices tab. After a short wait, the system displays the Remove Unused Principals section. Click Go for Governance.

The page redirects to the user details page in the RAM console. You can then disable console access, disable AccessKey pairs, or delete the user as needed.
Verify the result. Return to the Findings page. You can manually archive the finding, or wait for the next analysis cycle, after which the finding will automatically be marked as Resolved.
Remediation playbooks
This section provides standard remediation workflows for each type of finding.
Replace the policy for super users/roles
This action replaces the over-permissive AdministratorAccess policy with the more restrictive PowerUserAccess policy.
On the Findings page, on the Overview or Findings tab, find the super user/role that you want to manage and click the finding ID.
On the details page of the finding, click the Advices tab.
Find the advice to replace the
AdministratorAccesspolicy with thePowerUserAccesspolicy.Follow the appropriate procedure based on whether the identity is in the current account or a different account:
Current account: Click Apply Recommendation. The system automatically attaches the
PowerUserAccesspolicy to the target RAM user and then detaches theAdministratorAccesspolicy.
Different account: One-click application is not supported for cross-account resources. Click Copy. Then, log on to the target account, access the URL, and manually replace the policy.

(Optional) If the analyzer does not provide a piece of remediation advice, see the "Why is there no remediation advice for my finding? " section in this topic.
This is a high-risk operation. Before proceeding, confirm that the PowerUserAccess policy is sufficient for the identity's operational needs. If you encounter any access issues after the change, immediately re-attach the AdministratorAccess policy to the identity in the RAM console to restore permissions.
Remove unused policies from super users/roles
If other unused system or custom policies are attached to the administrative identity, the system also suggests removing them. If multiple policies match the remediation advice, separate pieces of advice are generated for each policy.
On the Findings page, on the Overview or Findings tab, find the super user/role that you want to manage and click the Finding ID.
On the details page of the finding, click the Advices tab.
Find the advice to remove the policy.
Follow the appropriate procedure based on whether the identity is in the current account or a different account:
Current account: Click Apply Recommendation. The system automatically detaches the policy.

Different account: Click Copy. Then, log on to the target account, access the URL, and manually detach the policy.
(Optional) If the analyzer does not provide a piece of remediation advice, see the "Why is there no remediation advice for my finding? " section in this topic.
Confirm that the policy is no longer needed. If you delete it by mistake, go to the RAM console and re-attach the policy to the identity to restore permissions.
Remove unused policies from privileged users/roles
For a privileged user/role, Access Analyzer suggests removing unused policies that contain high-risk permissions. The procedure is the same as for removing unused policies from super users/roles.
Disable or delete inactive users/roles
For an identity that has not been used for a long time, the best practice is to disable or delete it to completely eliminate its security risks.
On the Findings page, on the Overview or Findings tab, find the inactive user/role that you want to manage and click the Finding ID.
On the details page of the finding, click the Advices tab.
Find the advice in the Remove Unused Principals section.
Follow the appropriate procedure based on whether the identity is in the current account or a different account:
Current account: Click Go for Governance. The page redirects to the corresponding user or role details page in the RAM console. As needed, you can disable console access by removing logon settings, disable or delete the AccessKey pairs, or delete the identity.

Different account: Click Copy Resource URL. Log on to the target account and access the URL to disable or delete the identity.

(Optional) If the analyzer does not provide a piece of remediation advice, see the "Why is there no remediation advice for my finding? " section in this topic.
Remove unused policies from over-privileged users/roles
For an over-privileged user/role, Access Analyzer suggests removing unused policies. The procedure is the same as for removing unused policies from super users/roles.
Archive findings
You can archive a finding if you determine that it aligns with your business needs and requires no further action. Archiving a finding changes its status from Active to Archived.
Archive a single finding: On the Findings tab or the Advices tab, click Archive in the Actions column.
Automatically archive findings in batches: To automatically archive future findings that match specific criteria (for example, to ignore the inactive status of a specific role), click Save As Archive Rule. By defining rule conditions, you can ensure that all future findings matching the rule are archived automatically. For more information, see the "Automatically archive the findings" section in the Identify external access topic.
View and restore findings: By default, the system displays only active findings. To view or restore archived findings, on the Findings tab of the Findings page, set the Status filter to Archived to view all archived findings. For findings that need to be reprocessed, click Unarchive. The finding's status changes back to Active.

Limitations
Analyzer type: This feature supports only analyzers of the Over-privileged Access type. It does not support the External Access type.
Analysis granularity: The over-privileged access analyzer analyzes the permissions of all RAM identities in a resource directory or the current account. It does not analyze permissions for service-linked roles. The supported policy types, cloud services, and granularity are the same as those for permission auditing. For more information, see Services that work with the permission audit feature. If a policy contains permissions for unsupported services, the analyzer cannot provide remediation advice.
Policy replacement: Policy replacement advice for administrative roles are primarily based on the
AdministratorAccesspolicy. The feature does not support generating replacements for custom administrative policies.Policy content: Access Analyzer cannot generate removal advice for a policy that contains a
DenyorNotActionstatement.Authorization scope: If the authorization scope of an administrator permission is a resource group instead of an account, Access Analyzer does not identify the identity as a super administrator.
Authorization method: Access Analyzer can identify permissions granted directly to an identity or inherited through a user group. However, it does not provide one-click remediation for permissions inherited from a group. You must remediate these findings manually by adjusting the group's policies.
Data latency: Access Analyzer findings are updated periodically, and there can be a data latency of up to 24 hours. If you need to generate advice based on the most recent activity, navigate to the finding details page and click Rescan before viewing the advice.

FAQ
Can I apply advice in batches?
No, you must apply remediation advice individually. However, if you want to dismiss multiple findings of a specific type, you can create an archival rule to automatically archive them, which achieves a similar outcome to a batch ignore action.
How do I check the freshness of the data?
On the Findings page, the Updated At column shows when each finding was last updated. You can also view the analysis time and update time on the finding details page. All times are displayed in your local time zone.

Why is there no remediation advice for my finding?
On the finding details page, if no advice are displayed on the Advices tab, you must address the finding manually. For example, you can manually remove the policy or archive the finding.
Common reasons for empty advice include the following:
Policy replacement for super users/roles: If a RAM identity has recently used a permission that is exclusive to the
AdministratorAccesspolicy, Access Analyzer will not suggest replacing it with a more restrictive policy likePowerUserAccess.Remove unused policies: If a RAM identity has used any permission from a policy within the idle period, Access Analyzer will not suggest removing that policy.
Advice is not generated for permissions inherited from a user group or for policies containing services that are not fully supported by this feature. For more information, see the "Limitations" section in this topic.
How do I determine if a RAM identity's permissions are excessive?
When you review a finding, the details page provides information to help you decide whether the permissions are necessary. If they exceed requirements, you can right-size them using the suggestion or by manually optimizing the policy.
Accessed Services/Authorized Services:
Authorized Services: The total number of services the RAM identity is authorized to access via its attached policies. You can view the details about these services in the Access Records list.
Accessed Services: The number of services that Access Analyzer detected the identity actually accessed during the idle period. The Access Records list puts access services on the top and shows the last access time. You can also filter for all services accessed during the period.
Performed Actions/Authorized Actions:
Authorized Actions: The total number of actions that the RAM identity is authorized to perform for each authorized service.
Performed Actions: The number of actions that Access Analyzer detected the RAM identity performed during the idle period.
NoteAction-level analysis is not supported for all cloud services. For services without this support, the Performed Actions/Authorized Actions column will be empty. For a list of supported services, see Services that work with the permission audit feature.
Last Accessed At: Shows the last time each service or action was used.

For cloud services that support action-level permission auditing, you can click View Actions in the Actions column to see which specific actions were performed and their last performing times. Actions marked with a Privileged tag are high-risk and require careful review.
