When can I enable the lifecycle management feature?
If the files in a General-purpose NAS file system are accessed 1 to 3 times each month, configure a lifecycle policy to dump the files to the Infrequent Access (IA) storage class. You are charged based on the billable items of the IA storage class.
If the files in a General-purpose NAS file system are accessed once or twice each quarter, configure a lifecycle policy to dump the files to the Archive storage class. You are charged based on the billable items of the Archive storage class.
To further reduce storage costs, configure a lifecycle policy for both the IA storage class and the Archive storage class. If files meet the rules configured in the lifecycle policy, File Storage NAS (NAS) executes the lifecycle policy with the minimal overhead. For more information, see Lifecycle management.
Why am I unable to enable the lifecycle management feature for my file system?
The lifecycle management feature is unavailable for file systems for which the data encryption feature is enabled.
How do I configure lifecycle policies?
To configure lifecycle policies, use the NAS console or call the CreateLifecyclePolicy operation. For more information, see Manage a lifecycle policy and CreateLifecyclePolicy.
How do I disable the lifecycle management feature?
After you enable the lifecycle management feature for a General-purpose NAS file system, you can dump the cold data that has not been accessed for a long period of time to the IA or Archive storage class. The feature helps you reduce storage costs.
If you no longer want to use the lifecycle management feature, perform the following steps to disable the feature:
Log on to the NAS console.
In the left-side navigation pane, choose .
In the top navigation bar, select the resource group and region where your file system resides.

On the Lifecycle Policies page, find the lifecycle policy that you want to delete, and click Delete in the Actions column. In the message that appears, click OK.
After the lifecycle policy is deleted, the data that meets the lifecycle policy is no longer dumped to the IA or Archive storage class. If data has been dumped to the IA or Archive storage class before the policy is deleted, the data remains in the IA or Archive storage class. You are charged based on the storage usage of the IA or Archive storage class.
For more information about how to retrieve data from the IA or Archive storage class to the Standard storage class, see Create a data retrieval task.
Which files can be dumped to the IA or Archive storage class?
A file that meets the following conditions can be dumped to the IA or Archive storage class:
A lifecycle policy is configured for the directory in which the file is stored.
The size of the file is in the range of 64 KiB to 4.88 TiB.
The file is not accessed during the period of time that is specified in the lifecycle policy.
When you create a lifecycle policy, configure a rule to dump the files that are not accessed in the previous 14 days, 30 days, 60 days, or 90 days to the IA storage class. You can also configure a rule to dump the files that are not accessed in the previous 14 days, 30 days, 60 days, 90 days, or 180 days to the Archive storage class. The lifecycle management feature checks whether a file is infrequently accessed based on the atime parameter, which indicates the time when the file was last accessed.
The atime of a file is updated when you perform the following operations on the file:
Read data from the file.
Write data to the file.
The atime of a file is not updated when you perform the following operations on the file:
Rename the file.
Modify the user, group, mode, or other attributes of the file.
What happens if I configure multiple lifecycle policies for a single directory?
If the files in the directory meet a rule in one of the lifecycle policies, NAS executes the lifecycle policy with the minimal overhead.
What happens if I configure different lifecycle policies for a directory and its parent directory?
If the files in the directory meet a rule in one of the lifecycle policies, NAS executes the lifecycle policy with the minimal overhead.
For example, you configure the following lifecycle policy for a directory: Data that is not accessed in the previous 14 days is dumped to the IA storage class. You configure the following lifecycle policy for its parent directory: Data that is not accessed in the previous 60 days is dumped to the IA storage class. In this case, the files in the directory that are not accessed in the previous 14 days are dumped to the IA storage class. When the system checks for infrequently accessed files based on the lifecycle policy configured for the parent directory, the system skips the files that have already been dumped to the IA storage class.
Is a lifecycle policy valid for all data in the specified directory?
Yes, a lifecycle policy valid for all data in the specified directory. If the file data in the specified directory meets the lifecycle policy, the data is automatically dumped to the IA or Archive storage class.
How long does it take to dump a file that meets a lifecycle policy to the IA or Archive storage class?
The time that is required to dump a file to the IA or Archive storage class depends on the storage usage of the file system and the size of the file. After the lifecycle management feature is enabled, a file that meets a specified lifecycle policy is dumped to the IA or Archive storage class within 2 to 24 hours. Subsequent file dumps are performed at a specific point in time every week.
What happens if I rename a directory for which a lifecycle policy is configured?
If you rename a directory for which a lifecycle policy is configured, the lifecycle policy no longer takes effect on the files in the directory. Files that have been dumped to the IA or Archive storage class remain in the IA or Archive storage class.
If you reconfigure a lifecycle policy for the renamed directory, the lifecycle policy takes effect on the files in the directory. The files that meet the lifecycle policy are dumped to the IA or Archive storage class.
What happens if a lifecycle policy is deleted?
If a lifecycle policy is deleted, the files in the specified directory are no longer dumped to the IA or Archive storage class. Files that have been dumped to the IA or Archive storage class remain in the IA or Archive storage class.
Are the files in a directory repeatedly dumped if I delete the existing lifecycle policy and then reconfigure a lifecycle policy for the directory?
No, the files are not repeatedly dumped. After you reconfigure a lifecycle policy, the system checks for infrequently accessed files based on the lifecycle policy and skips the files that have already been dumped to the IA or Archive storage class. This ensures that files are not repeatedly dumped.
Can I read data from and write data to the files that are stored in the IA or Archive storage class?
Yes, you can read data from and write data to the files in the IA or Archive storage class the same way you read data from and write data to other files in a file system. For more information about the performance of different storage classes, see Storage classes of General-purpose NAS file systems.
Which files in my file system are stored in the IA or Archive storage class?
To query the files that are stored in the IA or Archive storage class, use the NAS console or call the ListDirectoriesAndFiles operation. For more information, see View the files stored in the IA or Archive storage class and ListDirectoriesAndFiles.
Is the latency of reading data from and writing data to a file in the IA storage class higher than the latency of reading data from and writing data to a file in the Standard storage class?
It depends. For a General-purpose NAS file system (Performance, Premium, or Capacity), when a file in the IA storage class is read for the first time, the latency may be higher than the latency of reading data from a file in the Standard storage class. When the file in the IA storage class is read later, the latency is almost the same as the latency of reading data from a file in the Standard storage class.
The latency of writing data to a file in the IA storage class is almost the same as the latency of writing data to a file in the Standard storage class. For more information about the performance of different storage classes, see Storage classes of General-purpose NAS file systems.
Is the latency of reading data from and writing data to a file in the Archive storage class higher than the latency of reading data from and writing data to a file in the Standard storage class?
It depends. For a General-purpose NAS file system (Performance, Premium, or Capacity), when a file in the Archive storage class is read for the first time, the latency may be higher than the latency of reading data from a file in the Standard storage class. When the file in the Archive storage class is read later, the latency is almost the same as the latency of reading data from a file in the Standard storage class.
The latency of writing data to a file in the Archive storage class is almost the same as the latency of writing data to a file in the Standard storage class. For more information about the performance of different storage classes, see Storage classes of General-purpose NAS file systems.
How am I charged if my files are dumped to the IA storage class?
If your files are dumped to the IA storage class, you are charged based on the billable items of the IA storage class. For more information, see Billing of General-purpose NAS file systems.
How am I charged if my files are dumped to the Archive storage class?
If your files are dumped to the Archive storage class, you are charged based on the billable items of the Archive storage class. The minimum storage duration required for the Archive storage class is 60 days. If a file is deleted, retrieved, or reduced in size before it is stored for 60 days (1,440 hours), a storage fee is incurred for the remaining storage duration (1440 - Actual storage duration) and the fee is calculated based on the original size of the archived file.
The minimum storage duration of a file starts from the latest one of the following timestamps: the time when the file is dumped and the time when the file is modified (mtime). The penalty fee is charged only once within 24 hours. If you modify a file, the storage duration of the file in the Archive storage class is reset. For more information, see Billing of General-purpose NAS file systems.
Is cold data in the IA storage class automatically converted to hot data after the cold data is accessed?
No, the cold data is not automatically converted to hot data after it is accessed. After data is dumped to the IA storage class, the data is persistently stored in the IA storage class. If you access cold data in the IA storage class, you are charged for the read and write traffic. For more information, see Billing of General-purpose NAS file systems.
If you need to frequently access data in the IA storage class, create a data retrieval task to retrieve data from specific files or directories to the Standard storage class. If you run the data retrieval task to read the required data, you are charged for the read traffic. For more information, see Create a data retrieval task.
How do I create a data retrieval task to retrieve files from the IA storage class?
To create a data retrieval task, use the NAS console or call the CreateLifecycleRetrieveJob operation. For more information, see Create a data retrieval task or CreateLifecycleRetrieveJob.
Is the read or write performance of a file system affected when a data retrieval task is running?
No, the read or write performance of a file system is not affected. You can read or write data as expected when a data retrieval task is running.
Am I charged for a data retrieval task?
Yes, you are charged for a data retrieval task. When you run a data retrieval task, the system reads data from the specified file. You are charged for reading the file from the IA or Archive storage class based on the file size and the storage class. After the data retrieval task is completed, the file is moved to the Standard storage class. You are charged for the storage space occupied by the file. For more information, see Billing of General-purpose NAS file systems.
How am I charged when I back up files that are stored in the IA or Archive storage class?
If you use Cloud Backup to back up files that are stored in the IA or Archive storage class of a General-purpose NAS file system, you are charged based on the billable items of Cloud Backup. For more information, see Billing methods and billable items.
To back up files from the IA or Archive storage class, Cloud Backup reads data from the files. Therefore, you are charged for the read traffic. The traffic fees are included into your NAS bills. For more information, see Billing of General-purpose NAS file systems.
How am I charged when I use a security service to scan files in the IA or Archive storage class?
When a security service, such as the anti-ransomware service of Security Center, scans files in the IA or Archive storage class of a General-purpose NAS file system, the service reads data from the files. File Storage NAS charges access traffic fees for the IA or Archive storage class. For more information, see Billing of General-purpose NAS file systems.
Why do I need to use RAM to grant the required permissions when I create a mount target in the classic network?
You must authorize NAS to authenticate the ECS instances that access your file systems. To ensure the data security of your file systems, NAS allows only the ECS instances of your Alibaba Cloud account to access your file systems using the classic network mount target. The file systems and ECS instances must belong to the same Alibaba Cloud account. To authenticate the ECS instances that access your file systems, you must use Resource Access Management (RAM) authorization to grant NAS the permissions to obtain a list of your ECS instances.
After you complete the authorization, NAS can call only the DescribeInstances operation. NAS uses the information about ECS instances only for authentication.
After you complete the authorization, do not delete or edit the AliyunNASDefaultRole role in RAM. Otherwise, exceptions such as mount failures or file system errors may occur.
Why am I unable to view a file system after I log on to the NAS console as a RAM user that has full control permissions on the file system?
Issue:
After you log on to the NAS console as a Resource Access Management (RAM) user who has full control permissions on a file system, an error message appears when you go to the File System List page.
Cause:
The RAM user has not been granted permissions on tags. You must also grant the
tag:ListTagKeyspermission.Solution:
In a custom policy, grant the RAM user permissions on the tags of the file system that you want to access. For more information, see Control access to NAS resources using RAM policies.
{ "Statement": [ { "Effect": "Allow", "Action": "nas:*", "Resource": "acs:nas:*:*:filesystem/0ddaf487b2" }, { "Effect": "Allow", "Action": "nas:CreateMountTarget", "Resource": "acs:vpc:*:*:vswitch/*" }, { "Effect": "Allow", "Action": "cms:Describe*", "Resource": "*" }, { "Effect": "Allow", "Action": "nas:DescribeFileSystems", "Resource": "*" }, { "Effect": "Allow", "Action": "tag:ListTagKeys", "Resource": "*" } ], "Version": "1" }
What do I do if it takes a long time to grant permissions on an SMB mount directory to a new user in a Windows AD domain?
When you grant permissions on an SMB mount directory to a new user, Windows traverses all files in the directory before it grants the required permissions. This issue may occur because of network latency. To resolve this issue, run a command-line script for concurrent execution, such as the icacls command or the PowerShell command Set-Acl. For more information, see icacls or Set-Acl.
How do I verify a keytab file?
Before you start, regenerate a keytab file and enable the -mapuser parameter.
After you enable the -mapuser option, existing mappings between other file system mount targets and the user become invalid. For example, the mapuser parameter maps the user someone to mount target 1 and then maps the user someone to mount target 2. In this case, the user someone can access only mount target 2. For this reason, when you perform the verification, use the mapuser parameter to map mount targets to different users.
Example
ktpass -princ cifs/file-system-id.region.nas.aliyuncs.com@EXAMPLE.com -ptype KRB5_NT_PRINCIPAL -mapuser alinas@example.com -crypto All -out c:\nas-mount-target.keytab -pass tHeP****d123example.com: the name of the AD domain that you want to build. Replace it with a lowercase domain name.
EXAMPLE.com: the name of the AD domain that you want to build. Replace it with an uppercase domain name.
Procedure
Log on to a Linux client on which the kinit tool is installed.
NoteThe client must be able to access the AD domain, or you must configure DNS as an AD server. For more information about how to configure a Linux client, see Mount and use an SMB file system on a Linux client as an AD domain user.
Add the following content to the /etc/krb5.conf file.
[realms] EXAMPLE.COM = { kdc = iZisovkei9i*****.example.com admin_server = iZisovkei9i****.example.com } [domain_realm] .example.com = EXAMPLE.COM example.com = EXAMPLE.COMIn the preceding content,
iZisovkei9i*****.exampleis an AD server. Replace it with the actual value.NoteIf your client runs CentOS, you must also add the following content.
default_tgs_enctypes = aes256-cts-hmac-sha1-96 rc4-hmac des-cbc-crc des-cbc-md5 default_tkt_enctypes = aes256-cts-hmac-sha1-96 rc4-hmac des-cbc-crc des-cbc-md5 permitted_enctypes = aes256-cts-hmac-sha1-96 rc4-hmac des-cbc-crc des-cbc-md5Verify that the client can connect to the AD server.
kinit aliyun.nas@example.comIf the command output contains the account information, the Kerberos configuration of the client is correct.
If the error
KDC replay did not match expectations while getting initial credentialsis returned, replace all AD domain names in the /etc/krb5.conf file with uppercase domain names.
Optional:Confirm that the mount target in the keytab file is the mount target of your file system.
klist -k -t <keytab_file_name>.keytabYou can verify the keytab file.
kinit -k -t <keytab file name>.keytab cifs/file-system-id.region.nas.aliyuncs.com@EXAMPLE.COMIn the preceding command,
file-system-id.region.nas.aliyuncs.comis the mount target of the file system. Replace it with the actual value.EXAMPLE.COMis the AD domain. Replace it with the actual uppercase domain name.If no error occurs, the keytab file is correct.
How do I obtain an AccessKey pair?
Log on to the console using your Alibaba Cloud account.
Move the pointer over the profile icon in the upper-right corner and click AccessKey.
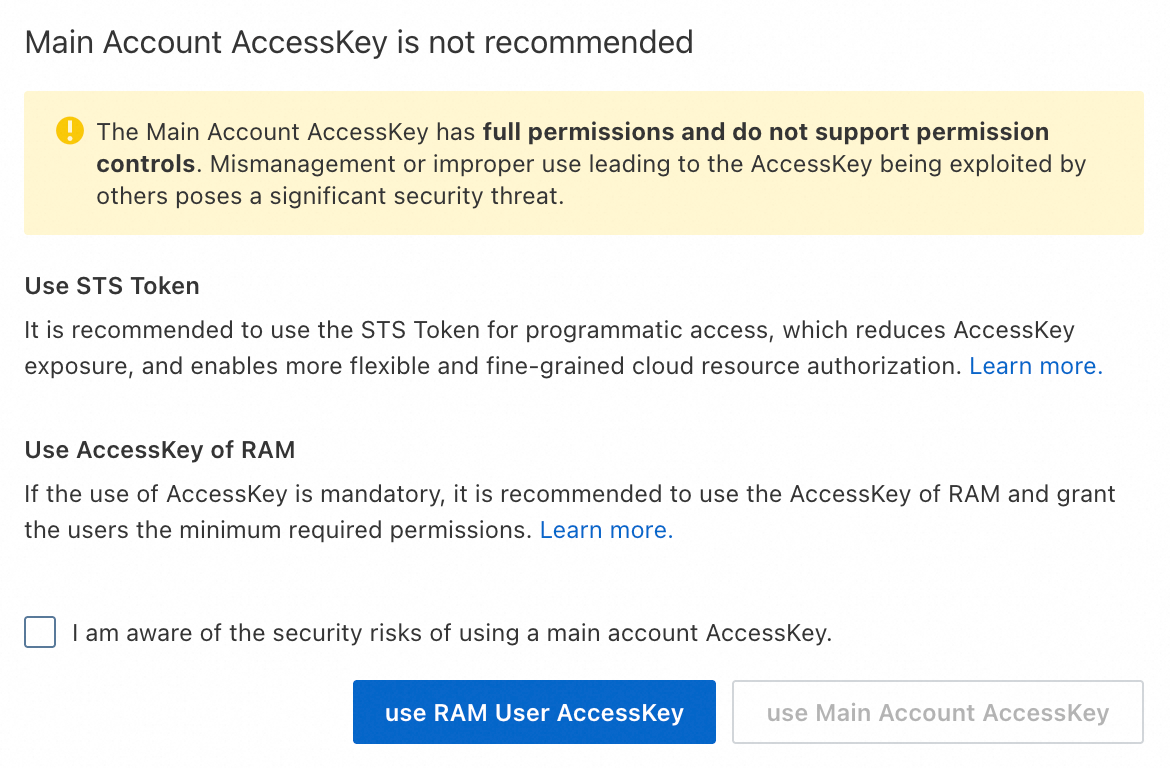
In the Main Account AccessKey is not recommended dialog box, select Use Main Account AccessKey or Use RAM User AccessKey.
Use the AccessKey pair of an Alibaba Cloud account
Select I am aware of the security risks of using a main account AccessKey, and then click Use Main Account AccessKey.
Click Create AccessKey.
In the Create Main Account AccessKey dialog box, review the security risks and limits again. To create the AccessKey pair, select I am aware of the security risks of using a main account AccessKey, and click Use Main Account AccessKey.

In the Create AccessKey dialog box, save the AccessKey ID and AccessKey secret, select I have saved the AccessKey Secret, and click OK.
(Optional) Configure AccessKey Network Access Control: You can restrict the source IP addresses for API requests that use the AccessKey pair. This improves security by restricting access to the AccessKey pair to trusted network environments. We recommend that you identify the network environment where the AccessKey pair is used, and click Go to Settings. For more information, see Configure an AccessKey-level network access restriction policy for a RAM user.
 Important
ImportantTo reduce the risk of leaks, the AccessKey secret of an Alibaba Cloud account is displayed only when you create it. You cannot retrieve it later. Make sure to store it securely.
Use the AccessKey pair of a RAM user
Click Use RAM User AccessKey.
You are redirected to the Resource Access Management (RAM) console. On the Users page, find the RAM user for whom you want to obtain an AccessKey pair.
NoteIf no RAM user exists, create a RAM user. For more information, see Create a RAM user.
The AccessKey secret of a RAM user is displayed only when the AccessKey pair is created and cannot be retrieved later. Keep the AccessKey secret confidential.
If an AccessKey pair is leaked or lost, create a new one. You can create a maximum of two AccessKey pairs for each RAM user.
Click the logon name of the user.
In the AccessKey section of the Authentication tab, click Create AccessKey.
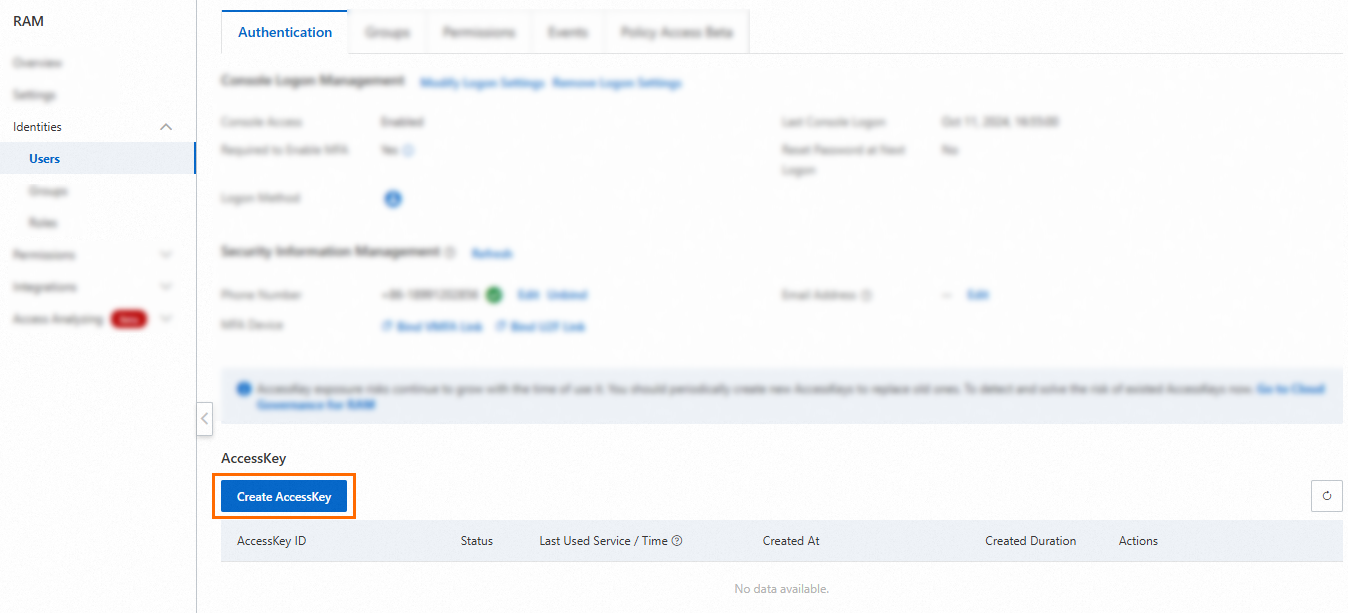
Read the suggestion for each scenario and select a credential solution based on your business requirements. If you must create an AccessKey pair, select a scenario, select I confirm that it is necessary to create an AccessKey, and then click Continue. The created AccessKey pair can be used in all scenarios.
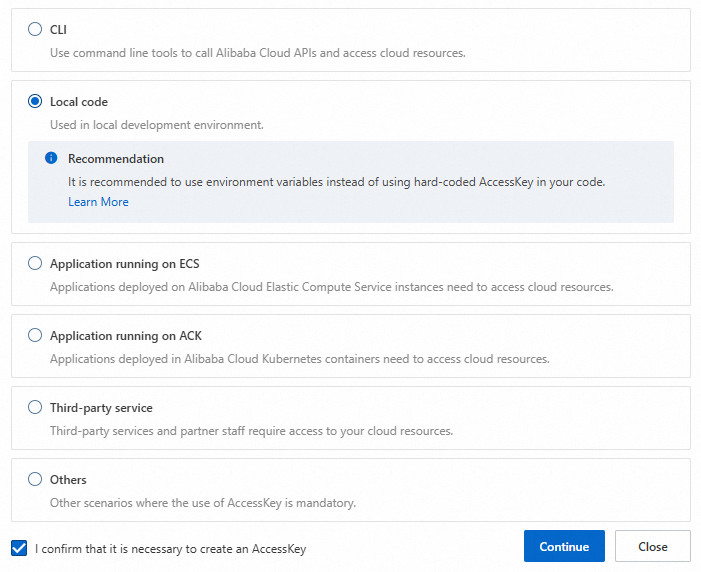
In the Create AccessKey dialog box, save the AccessKey ID and AccessKey secret, and click OK.
How do I use the server-side encryption feature of NAS?
When you create a file system, set the encryption method to NAS-managed key or Custom Key (KMS) as needed. For more information, see Create a General-purpose NAS file system in the console and Create an Extreme NAS file system in the console.
Can a file system use server-side encryption if it is not already enabled?
No. You can enable the server-side encryption feature only when you create a file system.
Can I disable the server-side encryption feature for a file system?
No. The server-side encryption feature takes effect immediately after it is enabled and cannot be disabled.
Can I change the key that is used to encrypt a file system?
No. The key used to encrypt a file system is bound during creation and cannot be changed.
How do I choose between NAS-managed keys and custom keys?
Both key management methods use Key Management Service (KMS) to host keys and use the envelope encryption mechanism to prevent unauthorized data access.
If you have specific security requirements to use Bring-Your-Own-Key (BYOK), select custom keys. For other scenarios, use NAS-managed keys.
If you use a custom key, the NAS file system that is encrypted using the key becomes inaccessible if the key is disabled or deleted.
Does the server-side encryption feature of NAS support the SM4 algorithm?
No, it does not. The server-side encryption feature of NAS uses the industry-standard AES-256 encryption algorithm to protect static data in file systems and uses the envelope encryption mechanism to prevent unauthorized data access. The server-side encryption keys are generated and managed by Key Management Service (KMS). KMS helps ensure the confidentiality, integrity, and availability of your keys. For more information about encryption, see Use envelope encryption to encrypt and decrypt data locally.
If a CMK is accidentally disabled or deleted, how can I restore access to the data in the NAS file system?
If a customer master key (CMK) is disabled, re-enable the CMK.
If you have scheduled a task to delete a key, cancel the key deletion request. For more information, see Schedule key deletion.
If the key material of a Bring-Your-Own-Key (BYOK) key is deleted, re-upload the original key material. For more information, see Import key material.
If a CMK is deleted, it cannot be restored, and the data in the file system becomes inaccessible.
After I enable the server-side encryption feature, does my application need to decrypt data for each access?
No, it does not. The data encryption and decryption processes are automatically handled by NAS. You do not need to modify your applications.
Does enabling server-side encryption affect file system performance?
After you enable server-side encryption, NAS encrypts data when it is written to the file system and automatically decrypts data when it is read from the file system. The read and write performance of a file system is mainly affected by the size of the read and write block in each read and write operation. Compared with a file system of the same specifications for which server-side encryption is disabled, the performance of a file system for which server-side encryption is enabled decreases by about 5% to 25%. For more information, see What factors affect the read and write performance of a file system?
If server-side encryption at rest is enabled for a file system, is the effective storage capacity reduced?
The effective capacity of the file system does not decrease. At-rest encryption uses Advanced Encryption Standard (AES), a block cipher that automatically pads data. This padding data is not counted toward the effective storage capacity of the file system instance.
Does File Storage NAS support inotify?
Using inotify with rsync is a common solution for real-time data backup and synchronization. However, because of the implementation mechanism of inotify, inotifywait does not work as expected on NAS file systems.
How inotifywait works
inotifywait is the user-mode interface implementation of the Linux kernel submodule inotify. inotify is implemented at the Virtual File System (VFS) layer. When a file operation reaches the VFS layer, the inotify module sends feedback on the operation type (such as create, delete, or property change) and the operation object (file name) to the user mode. The user-mode inotifywait can then output the operation information to the user.
Issues with using inotifywait on NAS
Because inotify is implemented at the VFS layer of the kernel, operations that a remote client performs on a Network File System (NFS) file system cannot be detected by the local kernel. Therefore, inotify cannot detect file modification operations from a remote client. For this reason, when you use inotifywait on NAS, for example, if you mount a NAS file system on Client A and Client B at the same time and start inotifywait on Client A to monitor the mount directory, the following phenomena occur:
Operations on files in the mount directory on Client A can be detected by inotifywait.
Operations on files in the mount directory on Client B cannot be detected by inotifywait.
Alternative solution
Use File Alteration Monitor (FAM) as an alternative solution. FAM is a library used to monitor changes to files or directories. It is implemented in user mode. The principle is to run a daemon in the background to periodically scan directories and retrieve file change information. However, using FAM has the following drawbacks:
You need to write a program on the client to call FAM interfaces to implement the feature.
For scenarios with many files, this solution has poor performance, may consume a large amount of resources, and cannot achieve good real-time performance.
If I cancel a file backup job, are the backed-up files retained?
When you cancel a running backup job, all files that have been backed up in the job are cleared and are not retained in the backup vault. To back up the files, run the backup job again.
Backed-up files in completed jobs are not affected.
When I use the file backup feature, if I cancel a file restore job, are the restored files retained?
When you cancel a file restore job, the files that have been restored in the job are saved in the specified directory. Other files in the job are not restored.
How is the free trial period for NAS File Backup calculated?
For any NAS file system, you can try the file backup feature for free within 30 days after you create the first backup plan.
For example, on May 1, 2021, you create a backup plan named backup01 for File System A. You can try the file backup feature for free until May 30, 2021. After the trial period expires, you can switch to the paid mode to continue using the backup plan or delete the backup plan. For more information, see Billing of Cloud Backup.
Are all my deleted files temporarily stored in the recycle bin?
After you enable the recycle bin, deleted files or directories are temporarily stored in the recycle bin. This includes but is not limited to the following:
Files in NAS that you manually delete on compute nodes such as ECS instances and containers. For example, if you manually run the
rm -f test01.textcommand to delete the test01.text file, the test01.text file is moved to the recycle bin.Files or directories in NAS that are automatically deleted by applications on compute nodes. For example, if Python uses
os.remove("test02.text")to delete the test02.text file, the test02.text file is moved to the recycle bin.Files or directories that are deleted by a POSIX rename operation. For example, if the files test_a.txt and test_b.txt exist in the same directory and you run
mv test_a.txt test_b.txt, the test_b.txt file is moved to the recycle bin.Temporary files generated by applications that use NAS files. For example, when you run the vim command to edit a file, the generated
.swpand.swpxfiles are moved to the recycle bin.Log files that are automatically rotated by applications. For example, if you use Nginx to configure automatic log rotation and retain a maximum of 20 log files, when the log file test.log.19 is rotated to the log file test.log.20, the original log file test.log.20 is moved to the recycle bin.
If you only overwrite the content of a file without deleting it, the file is not moved to the recycle bin. For example, if you call the open() function to open and write to a file in w+ mode, the original file is not moved to the recycle bin.
If a file system directory name has been changed, can a file recovery operation from the recycle bin restore the file to the original directory?
Yes, it can. When you restore files from the recycle bin to their original directory, the restore operation uses the FileId of the original directory as an identifier. The original directory is correctly identified even after it is renamed, and the file is restored to the new path. For example, assume that you enable the recycle bin feature, delete the file file1.txt from the directory dir1, and then rename the directory dir1 to dir2. In the recycle bin of the NAS console, you can find that the file file1.txt is in the directory dir2. After you perform the file restore task, you can find on the compute node that the file file1.txt is in the directory dir2.
Which method is faster for restoring files: from the recycle bin or from Cloud Backup?
Restoring files from the recycle bin is faster. When you restore files from the recycle bin, File Storage NAS only needs to migrate the file metadata, not copy the data. Therefore, restoring files from the recycle bin is significantly faster than restoring files from Cloud Backup.
Am I charged for using the recycle bin?
The recycle bin feature is free of charge, but you are charged for the storage of files temporarily stored in the recycle bin based on their original storage class. For example, if you delete a file from a storage-optimized file system, you are charged for the file based on the unit price of storage-optimized capacity. If you delete a file from the IA storage class, you are charged for the file based on the unit price of IA storage capacity. For more information, see Billing of General-purpose NAS file systems.
How do I query files in the recycle bin?
Use the NAS console to query information about files temporarily stored in the recycle bin, such as the time they were deleted. For more information, see Query files in the recycle bin.
Can I read from or write to files in the recycle bin?
No. You can only query deleted files or directories. When the recycle bin feature is enabled, deleted files are temporarily stored in the recycle bin. To read from or write to files in the recycle bin, you must perform a file restore operation. You can read from and write to the files after they are restored. For more information, see Restore files from the recycle bin.
After a file in a General-purpose NAS file system is deleted, does it still occupy the file count or capacity of the NAS file system while in the recycle bin, causing the NAS limits to be reached sooner?
No, it does not. Files temporarily stored in the recycle bin do not count towards the NAS file count or occupy capacity. They also do not cause your instance to reach the storage capacity or file count limits of the NAS file system instance sooner. For more information about the storage capacity and file count supported by each NAS storage class, see Limits.
Files temporarily stored in the recycle bin are charged based on their original storage class. For more information, see Billing of General-purpose NAS file systems.
Why does an error occur when I use the CloudMonitor API to view NAS monitoring data?
An error may occur because the MetricName parameter you set is incorrect. NAS supports real-time monitoring of file system instance performance and capacity through the CloudMonitor service. The supported metrics are listed in the following table. For information about how to view NAS monitoring data using the CloudMonitor API, see View monitoring data using the CloudMonitor API.
Capacity monitoring
File system type
MetricName
Metric
Unit
Description
General-purpose NAS file system
AlignedSize
Data volume of a General-purpose NAS file system (excluding the IA storage class)
bytes
The volume of the data that is stored in a file system within a specified period of time. The value does not include the volume of the data that is stored in the IA storage class.
SecondaryAlignedSize
Data volume of the IA storage class
bytes
The volume of the data that is stored in the IA storage class within a specified period of time after the lifecycle management feature is enabled for a file system.
FileCount
Number of files
N/A
The number of files in a file system within a specified period of time, excluding directories.
OfflineReadQuantity
Read traffic of the IA storage class
bytes
The read traffic that is generated when you access data in the IA storage class after the lifecycle management feature is enabled.
OfflineWriteQuantity
Write traffic of the IA storage class
bytes
The write traffic that is generated when you access data in the IA storage class after the lifecycle management feature is enabled.
ArReadQuantity
Read traffic of the Archive storage class
bytes
The read traffic that is generated when you access data in the Archive storage class after the lifecycle management feature is enabled.
ArWriteQuantity
Write traffic of the Archive storage class
bytes
The write traffic that is generated when you access data in the Archive storage class after the lifecycle management feature is enabled.
ArDeletePenaltyOpCount
Number of delete operations on archived files that trigger penalty
N/A
The number of times that files stored in the Archive storage class for less than 60 days are deleted. After the lifecycle management feature is enabled, if a file is stored in the Archive storage class for less than 60 days, you are charged for the remaining storage duration.
ArTruncatePenaltyOpCount
Number of truncate operations on archived files that trigger penalty
N/A
The number of times that files stored in the Archive storage class for less than 60 days are truncated. After the lifecycle management feature is enabled, if a file is stored in the Archive storage class for less than 60 days, you are charged for the remaining storage duration.
ArRetrievePenaltyOpCount
Number of retrieve operations on archived files that trigger penalty
N/A
The number of times that files stored in the Archive storage class for less than 60 days are retrieved. After the lifecycle management feature is enabled, if a file is stored in the Archive storage class for less than 60 days, you are charged for the remaining storage duration.
Extreme NAS file system
ExtremeCapacity
Total storage space of an Extreme NAS file system
bytes
The total capacity of an Extreme NAS file system within a specified period of time.
ExtremeCapacityUsed
Data volume of an Extreme NAS file system
bytes
The volume of data that is stored in an Extreme NAS file system within a specified period of time.
ExtremeInodeLimit
Maximum number of files in an Extreme NAS file system
N/A
The maximum number of files that can be created in an Extreme NAS file system within a specified period of time.
ExtremeInodeUsed
Number of used files in an Extreme NAS file system
N/A
The number of files that have been created in an Extreme NAS file system within a specified period of time.
Performance monitoring
MetricName
Metric
Unit
Description
IopsRead
Read IOPS
requests/s
The average read IOPS of a file system within a specified period of time.
IopsWrite
Write IOPS
requests/s
The average write IOPS of a file system within a specified period of time.
ThruputRead
Read throughput
bytes/s
The average read throughput per second of a file system within a specified period of time.
ThruputWrite
Write throughput
bytes/s
The average write throughput per second of a file system within a specified period of time.
LatencyRead
Read latency
ms
The average read latency per millisecond of a file system within a specified period of time.
LatencyWrite
Write latency
ms
The average write latency per millisecond of a file system within a specified period of time.
QpsMeta
Metadata QPS
requests/s
The average number of times that a file system requests metadata per second within a specified period of time.
What is the relationship between access point policies and the system policies AliyunNASFullAccess and AliyunNASReadOnlyAccess?
Policy | Description |
Access point policy | An access point policy is an authorization policy provided by Alibaba Cloud NAS for access point clients. It can be directly granted to different RAM users or RAM roles without requiring the AliyunNASReadOnlyAccess and AliyunNASFullAccess system policies. It can meet your fine-grained requirements to a greater extent, enabling more flexible permission management. Access permissions supported by access point clients:
|
AliyunNASReadOnlyAccess | A system policy that grants read-only access to NAS file systems. A RAM user or RAM role with this permission can only view file system information and has no execution permissions or access permissions for the access point client. |
AliyunNASFullAccess | A system policy that grants full management permissions for NAS file systems. This permission carries a high risk and is not recommended for use. A RAM user or RAM role with this permission can perform operations such as deleting, modifying, and enabling the recycle bin for NAS file system instance resources. Additionally, after an access point policy is enabled, the RAM user or RAM role has access permissions to the access point client by default. |
How do I resolve the issue where Java/Tomcat cannot access NAS SMB?
Cause:
By default, Windows services such as Tomcat start with the Local System account. This account cannot access the NAS SMB network path mounted by the current user, which causes the application access to fail.
Solution:
Open the Services Manager as an administrator.
In the list of services, find your Tomcat service (the name may be Apache Tomcat or a custom name).
Right-click the service and select Properties.
Switch to the Log On tab.
Select the This Account option and enter the current administrator account.
Click Apply, and then click OK.
In the list of services, right-click the Tomcat service and select Restart to apply the new identity.