Configuration data in Microservices Registry of Microservices Engine (MSE) is stored in plaintext. MSE is integrated with Key Management Service (KMS) to allow you to encrypt and decrypt configuration data, such as data sources, tokens, usernames, and passwords. This helps reduce the risk of sensitive data leaks.
Prerequisites
MSE is activated. For more information, see Activate MSE.
A Nacos engine that uses the Developer Edition, Professional Edition, or Serverless Edition is created. For more information, see Create an instance.
KMS is activated.
A KMS instance is purchased and enabled. The image version of the KMS instance is later than dkms-3.0.0. For more information, see Purchase and enable a KMS instance and Upgrade the image version of a KMS instance.
A key is created. For more information, see Getting started with key management
To ensure data security, MSE uses Alibaba Cloud KMS to encrypt and decrypt data. KMS includes Shared KMS and Dedicated KMS. Shared KMS is no longer available. For more information, see [Announcement] EOFS and EOS for the Shared KMS. If you use Shared KMS, we recommend that you upgrade Shared KMS to Dedicated KMS. If you activate KMS after March 31, 2022, you must purchase Dedicated KMS. For more information, see [Upgrade Announcement] KMS is upgraded to Dedicated KMS. For more information about KMS billing, see Billing of KMS 1.0.
Dedicated KMS instances are used in this topic. If you activated the Shared KMS before March 31, 2022, see FAQ.
Create encrypted configurations
To create encrypted configurations in the MSE console, perform the following steps:
Log on to the MSE console, and select a region in the top navigation bar.
In the left-side navigation pane, choose Microservices Registry > Instances.
On the Instances page, click the name of the instance.
In the left-side navigation pane, choose Configuration Management > Configurations.
In the upper-left corner of the Configurations page, select a namespace from the Namespace drop-down list, and click Add Configuration.
In the Create Configuration panel, set Data ID and Group, turn on Data Encryption, and then select KMS Key. If you have not created a KMS Key yet, click Create to create a KMS key in the Key Management Service console. After the KMS key is created, refresh the Create Configuration panel to view the created KMS key.
ImportantIf you activate Dedicated KMS after March 31, 2022, you must select the ID of a key that is used for encryption and associate the key with the MSE Nacos instance. This way, all subsequent configurations are encrypted by using the key.
If you activated KMS before March 31, 2022, a prompt to bind the key ID of the Dedicated KMS instance is not displayed and you can use the Shared KMS. The configuration methods for applications to access the Shared KMS are different.
For users who use Dedicated KMS, KMS AES-256 is displayed. For users who use Shared KMS, the three encryption methods are displayed in consideration of version compatibility. We recommend that you do not select KMS or KMS AES-128.
KMS AES-256: The envelope encryption and decryption method of KMS. This method uses the 256-bit key that has high encryption strength. The encrypted configuration content cannot exceed 50 KB. The configuration data in plaintext is not transmitted to KMS. We recommend that you select this option for higher security. Select an encryption method based on your business requirements.
KMS AES-128: The encryption method that uses the 128-bit key and has medium encryption strength. The encrypted configuration content cannot exceed 50 KB in size.
KMS: We recommend that you do not select this option. This is because special characters may result in compatibility issues. For example, an
ampersand (&)is escaped as\u0026. The encrypted configuration content cannot exceed 6 KB in size.
After the binding, you cannot change the key. If you delete the key, you cannot access encryption configurations.
In the Configuration Format section, select a data format, enter the configuration content in the Configuration Content editor on the right, and then click Release.
Use an encrypted configuration in the Nacos SDK for Java
Add the following dependencies to the pom.xml file in the project:
<dependency> <groupId>com.alibaba.nacos</groupId> <artifactId>nacos-client</artifactId> <version>{nacos-client-version}</version> </dependency> <dependency> <groupId>com.alibaba.nacos</groupId> <artifactId>nacos-client-mse-extension</artifactId> <version>{nacos-client-mse-extension-version}</version> </dependency>Version description
Nacos client major version
Nacos client version
Recommended plug-in version
1.x
V1.4.3 or later
V1.0.6 or later
2.x
V2.1.1 or later
V1.0.6 or later
ImportantStability issues may occur if the encryption and decryption plug-in version does not match the Nacos client version. We recommend that you use recommended versions.
Select the valid code that you want to configure based on the framework type that you use.
Use the Nacos client framework
If you use the Nacos client framework to obtain configurations, you must configure the following sample code.
try { Properties properties = new Properties(); // The address of your Nacos server. properties.put("serverAddr", "{serverAddr}"); // Configure the RAM role of the ECS instance as the access credential. properties.put("ramRoleName", "{ramRoleName}"); // The endpoint of the KMS instance. properties.put("kmsEndpoint", "{kmsEndpoint}"); ConfigService configService = NacosFactory.createConfigService(properties); System.out.println("content:::"+configService.getConfig("{dataId}", "{group}", 6000)); } catch (Exception e) { e.printStackTrace(); }kmsEndpoint indicates the endpoint of the KMS instance. If the access environment and the KMS instance are in the same VPC, the value of kmsEndpoint is the VPC endpoint of the instance. If you access the KMS instance over Internet, the value of kmsEndpoint is the public endpoint or VPC endpoint of the public gateway. For more information about how to obtain the endpoint, see How do I obtain the endpoint of a KMS instance?
If you use an AccessKey pair as a credential to access the KMS instance, replace the following configuration:
properties.put("ramRoleName", "{ramRoleName}");Use the following configuration:
properties.put("accessKey", "{accessKey}"); properties.put("secretKey", "{secretKey}");The Nacos SDK for Java can use encrypted configurations by using multiple access credentials, such as Security Token Service (STS) tokens and the Alibaba Cloud Resource Name (ARN) of a RAM role. For more information about the supported access credentials and client configuration methods, see Supported access credentials for configuration encryption of the Nacos SDK for Java.
If your KMS is activated after March 31, 2022, and you want to release encrypted configurations in the SDK, add the following code:
properties.put("keyId", "{keyId}");Replace the serverAddr, ramRoleName, accessKey, secretKey, kmsEndpoint, dataId, group, and keyId parameters in the code with the actual service parameters.
Use the Spring Cloud Nacos Config framework
NoteIf you use Spring Cloud Alibaba 2022.x or 2023.x, upgrade the version to 2023.0.1.2.
If you use Spring Cloud Alibaba 2021.x, upgrade the version to 2021.0.6.1.
If you use Spring Cloud Alibaba 2.x, upgrade the version to 2.2.10.
Make sure that the version mappings among Spring Cloud Alibaba, Spring Cloud, and Spring Boot are correct. For more information about the version mappings, see the release notes for the related version on the Spring Cloud Alibaba official website.
If you use the Spring Cloud Nacos Config framework to obtain configurations, you must add the following configurations:
spring.cloud.nacos.config.server-addr={serverAddr} spring.config.import=nacos:{dataId}?group={group}&refreshEnabled=true # Use the RAM role of an ECS instance as the access credential. spring.cloud.nacos.config.ramRoleName={ramRoleName} spring.cloud.nacos.config.kmsEndpoint={kmsEndpoint}kmsEndpoint indicates the endpoint of the KMS instance. If the access environment and the KMS instance are in the same VPC, the value of kmsEndpoint is the VPC endpoint of the instance. If you access the KMS instance over Internet, the value of kmsEndpoint is the public endpoint or VPC endpoint of the public gateway. For more information about how to obtain the endpoint, see How do I obtain the endpoint of a KMS instance?
If you use an AccessKey pair as a credential to access the KMS instance, replace the following configuration:
spring.cloud.nacos.config.ramRoleName={ramRoleName}Use the following configurations:
spring.cloud.nacos.config.accesskey={accessKey} spring.cloud.nacos.config.secretkey={secretKey} # If an AccessKey pair is used to access your Nacos instance, we recommend that you specify the AccessKey pair by using Java Virtual Machine (JVM) parameters or environment variables. # JVM parameters. -Dspring.cloud.nacos.config.accessKey={accessKey} -Dspring.cloud.nacos.config.secretKey={secretKey} # Environment variables. spring_cloud_nacos_config_accessKey={accessKey} spring_cloud_nacos_config_secretKey={secretKey}The Nacos SDK for Java can use encrypted configurations by using multiple access credentials, such as Security Token Service (STS) tokens and the Alibaba Cloud Resource Name (ARN) of a RAM role. For more information about the supported access credentials and client configuration methods, see Supported access credentials for configuration encryption of the Nacos SDK for Java.
If your KMS is activated after March 31, 2022, and you want to release encrypted configurations in the SDK, add the following code:
spring.cloud.nacos.config.keyId={keyId}Replace the serverAddr, ramRoleName, accessKey, secretKey, kmsEndpoint, dataId, group, and keyId parameters in the code with the actual service parameters.
Description
The following table describes the parameters. Make sure that the values you configure are valid.
Parameter
Description
serverAddr
The IP address of your MSE instance. Example:
mse-*****.nacos-ans.mse.aliyuncs.com.ramRoleName
The RAM role that is assigned to the ECS instance or ACK cluster.
accessKey and secretKey
The AccessKey ID and AccessKey secret of the current Alibaba Cloud account.
You must specify the accessKey and secretKey parameters. Otherwise, you must specify the ramRoleName parameter.
kmsEndpoint
The endpoint of the KMS instance. If the access environment and the KMS instance are in the same VPC, the value of kmsEndpoint is the VPC endpoint of the instance. If you access the KMS instance over Internet, the value of kmsEndpoint is the public endpoint or VPC endpoint of the public gateway. For more information about how to obtain the endpoint, see How do I obtain the endpoint of a KMS instance?
dataId
The data ID of the encrypted configuration. Example:
cipher-kms-aes-256-****.properties.group
The group name of the encrypted configuration.
keyId
The ID of the KMS key that is used to encrypt configurations. You can create and use a KMS key in the KMS console.
Example:
alia/***orkey-***.
Use an encrypted configuration in the Nacos SDK for Go
Run the
go getcommand to download dependencies in theNacos client SDK for Go.go get -u github.com/nacos-group/nacos-sdk-go/v2@v2.2.8Modify the initial configurations of the Nacos client.
In the Nacos SDK for Go, only an AccessKey pair can be used as the credential to access the KMS instance. Replace the serverAddr, accessKey, secretKey, and kmsEndpoint parameters in the code with the parameters used in your business and make sure that the
OpenKMSparameter is set to true for configuration encryption.sc := []constant.ServerConfig{ { IpAddr: "{serverAddr}", // Configure the IP address of your MSE Nacos instance. Port: 8848, }, } var accessKey = "{accessKey}" var secretKey = "{secretKey}" cc := constant.ClientConfig{ NamespaceId: "public", // Configure the ID of the namespace. OpenKMS: true, // Enable KMS-based encryption. AccessKey: accessKey, SecretKey: secretKey, KMSConfig: &constant.KMSConfig{Endpoint: "{kmsEndpoint}",}, TimeoutMs: 5000, NotLoadCacheAtStart: true, LogDir: "/tmp/nacos/log", CacheDir: "/tmp/nacos/cache", RotateTime: "1h", MaxAge: 3, }kmsEndpoint indicates the endpoint of the KMS instance. If the access environment and the KMS instance are in the same VPC, the value of kmsEndpoint is the VPC endpoint of the instance. If you access the KMS instance over Internet, the value of kmsEndpoint is the public endpoint or VPC endpoint of the public gateway. For more information about how to obtain the endpoint, see How do I obtain the endpoint of a KMS instance?
Publish encrypted configurations.
keyId: The ID of the KMS key that is used to encrypt configurations.configParam := vo.ConfigParam{ DataId: "{dataId}", Group: "{group}", Content: "content", KmsKeyId: "keyId", // The ID of the KMS key that is used to encrypt configurations. You can create and use a KMS key in the KMS console. } published, err := client.PublishConfig(configParam) if published && err == nil { fmt.Printf("successfully publish: group[%s], dataId[%s], data[%s]\n", configParam.Group, configParam.DataId, configParam.Content) } else { fmt.Printf("failed to publish: group[%s], dataId[%s], data[%s]\n with error: %s\n", configParam.Group, configParam.DataId, configParam.Content, err) }
Parameters
The following table describes the parameters. Make sure that the values you configure are valid.
Parameter | Description |
serverAddr | The IP address of your MSE instance. Example: |
accessKey and secretKey | The AccessKey ID and AccessKey secret of the RAM user. |
kmsEndpoint | The endpoint of the KMS instance. If the access environment and the KMS instance are in the same VPC, the value of kmsEndpoint is the VPC endpoint of the instance. If you access the KMS instance over Internet, the value of kmsEndpoint is the public endpoint or VPC endpoint of the public gateway. For more information about how to obtain the endpoint, see How do I obtain the endpoint of a KMS instance? |
dataId | The data ID of the encrypted configuration. Example: |
group | The group name of the encrypted configuration. |
keyId | The ID of the KMS key that is used to encrypt configurations. You can create and use a KMS key in the KMS console. Example: |
Supported access credentials for configuration encryption of the Nacos SDK for Java
The Nacos SDK for Java supports multiple access credentials to encrypt configurations. You can select a method to initialize the credential provider based on the authentication and authorization requirements of your business scenario.
Supported access credentials:
For more information about how to configure access credentials on the client, see the "Configure access credentials on the client" section in Access authentication by the Nacos client. Select the following system policy to grant the related permission on the access credential. This way, a coarse-grained authorization operation is performed to grant the read and write permissions on all KMS instances.
Policy | Note |
AliyunKMSFullAccess | The permission that is required to manage KMS. You can use a RAM role to which this policy is attached to manage all features the same way you use an Alibaba Cloud account to manage KMS. |
FAQ
How do I configure parameters if the Shared KMS that was activated before March 31, 2022, is used?
If you activated the Shared KMS before March 31, 2022, you only need to replace the kmsEndpoint parameter with kmsRegionId. kmsRegionId indicates the region where the KMS instance resides, such as cn-hangzhou. Perform the following steps to modify the client configuration based on the framework that you use.
Use an encrypted configuration in the Nacos client SDK for Java
Replace the following configuration in the code:
properties.put("kmsEndpoint", "{kmsEndpoint}");Use the following configuration:
properties.put("kms_region_id", "{kmsRegionId}");Use an encrypted configuration by using the Spring Cloud Nacos Config framework in the Nacos SDK for Java
Replace the following configuration in the code:
spring.cloud.nacos.config.kmsEndpoint={kmsEndpoint}Use the following configurations:
spring.cloud.nacos.config.kms_region_id={kmsRegionId}Use an encrypted configuration in the Nacos SDK for Go
Add the RegionId parameter in ClientConfig. Replace the following configurations in the code:
cc := constant.ClientConfig{
NamespaceId: "public",
OpenKMS: true,
AccessKey: accessKey,
SecretKey: secretKey,
KMSConfig: &constant.KMSConfig{Endpoint: "{kmsEndpoint}",},
TimeoutMs: 5000,
NotLoadCacheAtStart: true,
LogDir: "/tmp/nacos/log",
CacheDir: "/tmp/nacos/cache",
RotateTime: "1h",
MaxAge: 3,
}Use the following configurations:
cc := constant.ClientConfig{
NamespaceId: "public",
OpenKMS: true,
AccessKey: accessKey,
SecretKey: secretKey,
TimeoutMs: 5000,
NotLoadCacheAtStart: true,
LogDir: "/tmp/nacos/log",
CacheDir: "/tmp/nacos/cache",
RotateTime: "1h",
MaxAge: 3,
RegionId: "{kmsRegionId}",
}How do I obtain the endpoint of a KMS instance?
If you access the KMS instance over a VPC, the value of kmsEndpoint is the instance VPC endpoint on the KMS instance details page.

If you access the KMS instance over the Internet, you must turn on the Internet Access Status switch on the KMS instance details page.
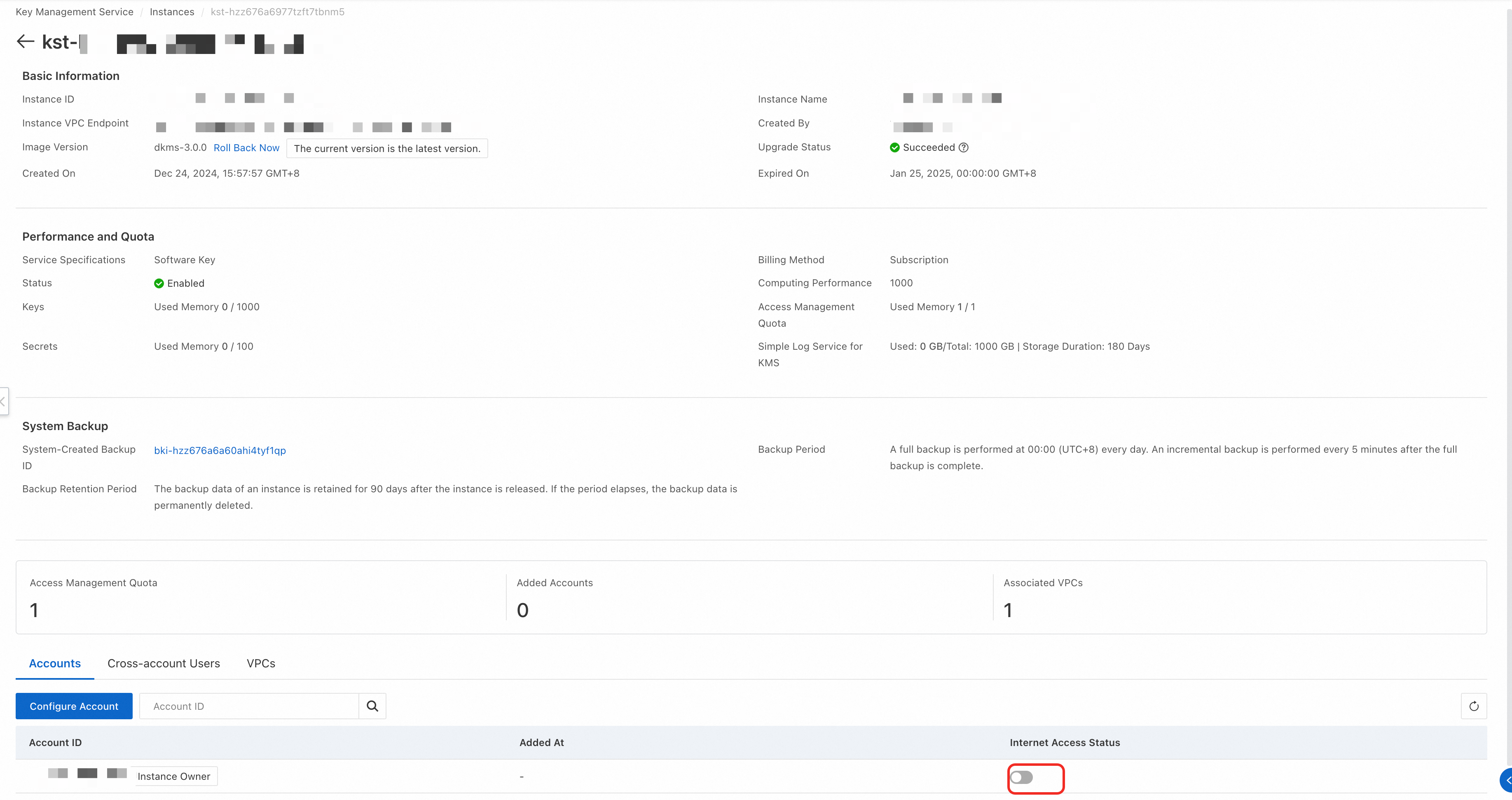
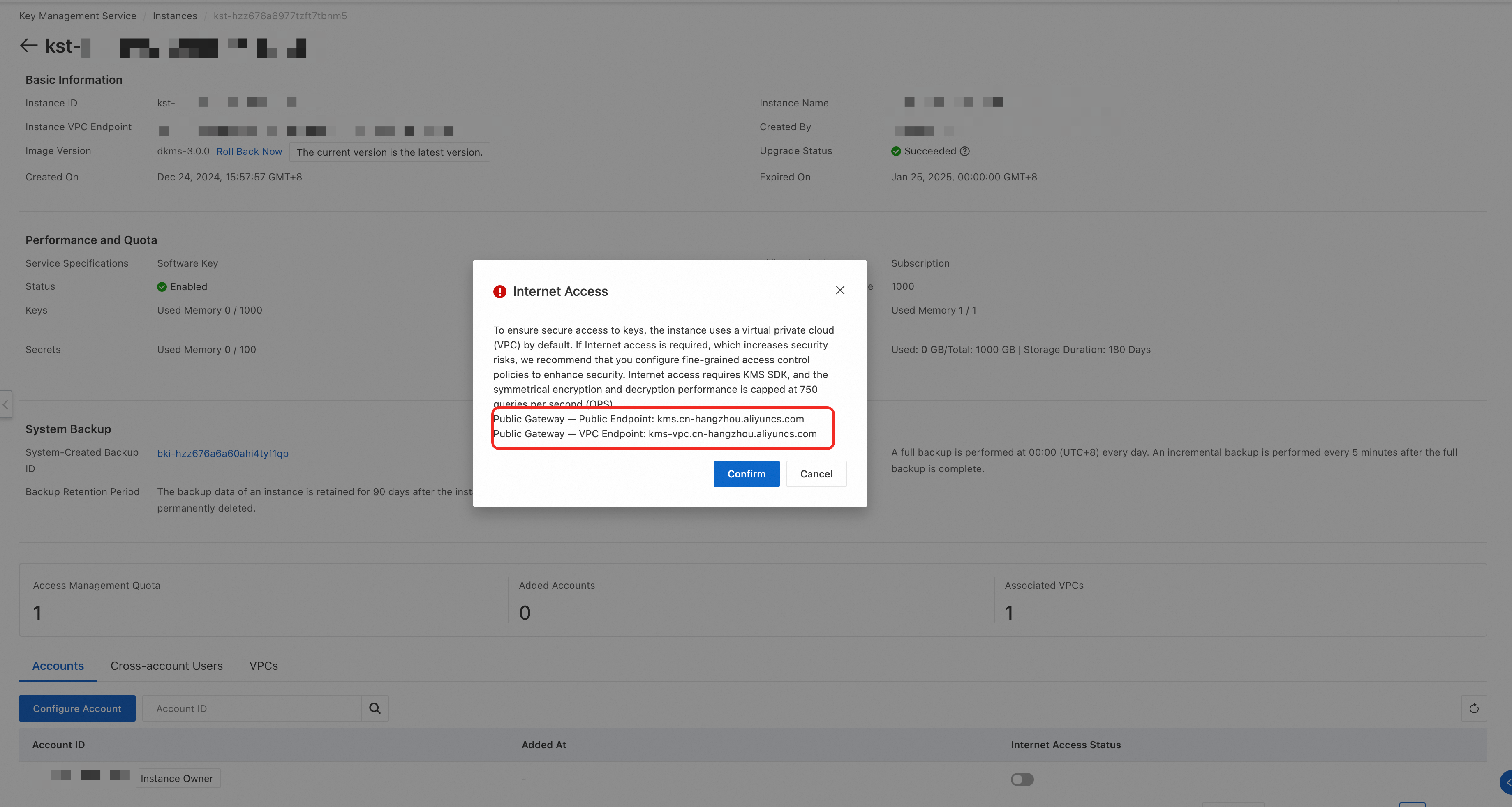
If you access the KMS instance over a VPC, the value of kmsEndpoint is the VPC endpoint of the public gateway.
FAQ
Troubleshooting of common errors
Perform the following steps:
Check whether the application runtime environment can connect to the VPC in which the MSE instance resides and the VPC in which the KMS instance resides.
NoteYou do not need to ensure the connectivity between the MSE instance and KMS instance.
Check whether KMS
V1.0orV3.0is used. If KMS V1.0 is used, you must make sure that KMS was activated before March 31, 2022.NoteIf you activate KMS after March 31, 2022, you must purchase Dedicated KMS. The encryption feature of KMS V1.0 is no longer available for new users.
Check whether the Nacos client version matches the version of the encryption and decryption plug-in. For more information, see version descriptions in this topic.
Troubleshooting of Nacos SDK for Java issues
Keywords of exception stacks in Nacos logs | Causes |
| The initialization parameter |
| The key ID specified by the initialization parameter |
| The initialization parameter |
| The endpoint specified by the initialization parameter |
| The initialization parameter |
| The value of the initialization parameter |
| The initialization parameter |
|
|
| The initialization parameter |
| The file that is specified by the initialization parameter |